Biggest Healthcare Industry Attacks (2023 – 2024)
The healthcare industry has become an increasingly favored target for cybercriminals, with the financial impact of breaches being particularly severe. The industry’s vulnerability is further exacerbated by the critical nature of its operations, where disruptions can directly jeopardize patient safety.

An illustration of “Healthcare Cybersecurity” by DALL-E
According to IBM’s 2024 report, healthcare incurs the highest costs associated with data breaches, averaging USD 9.77 million per incident, despite a 10.6% decrease in overall breach costs. This significant cost is driven by the sensitive data managed by healthcare organizations, and their frequent reliance on legacy systems. Medical records, often containing personal information such as names, dates of birth, and social security numbers, are especially valuable to threat actors for identity theft and other fraudulent activities.
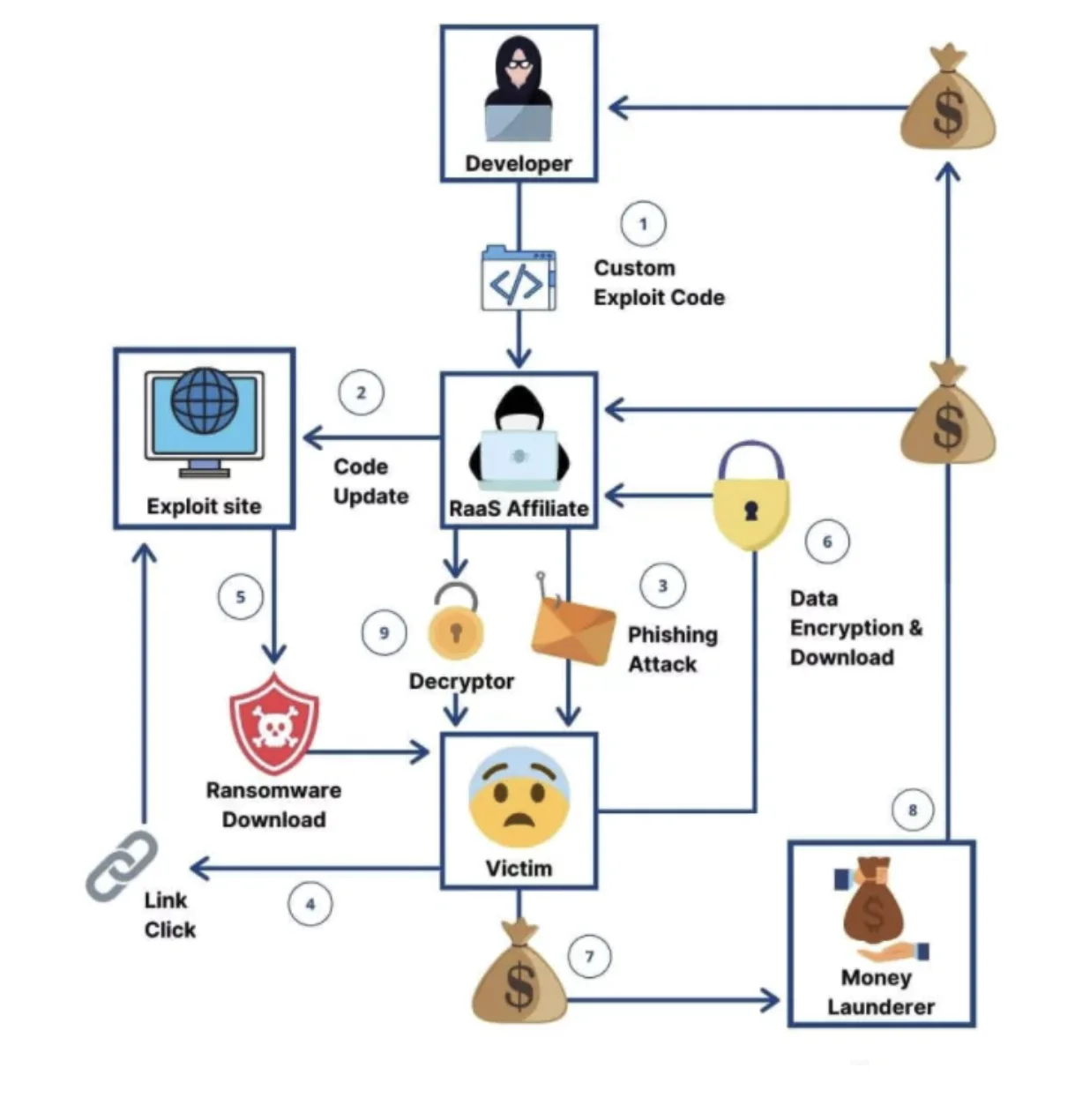
Adding to these challenges is the rise of Ransomware-as-a-Service (RaaS) operations, which have made it easier for affiliates to deploy ransomware and manage payments, significantly increasing the risk to healthcare organizations. The sector also faces growing threats from supply chain disruptions, and the outpacing IoT landscape.
To help visualize the growing impact on healthcare in 2024, consider that in 2023, the number of large security breaches hit a record high with 725 incidents reported to the Department of Health and Human Services (HHS), surpassing 2022’s record of 720 breaches.
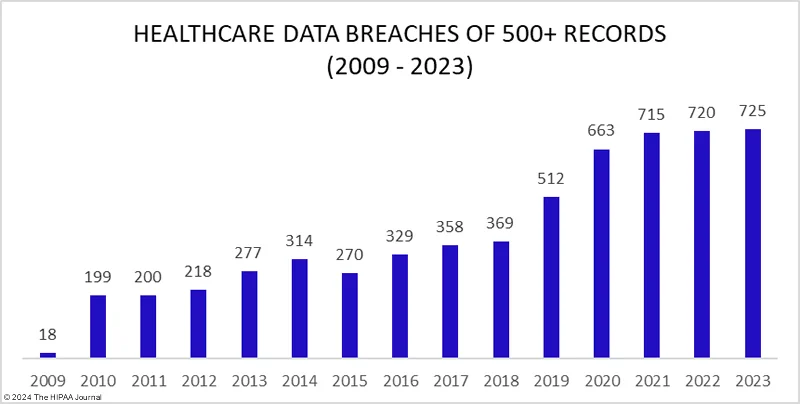
Healthcare Data Breaches of 500+ Records, 2009 – 2023 (The HIPAA Journal)
The graph above shows the steady rise in significant healthcare data breaches since 2009, highlighting the increasing attention from threat actors on the healthcare sector.
Common Cyber Attack Types in the Healthcare Industry
Following our discussion on the rising number of attacks on the healthcare industry, it’s crucial to understand the most prevalent cyber threats targeting this sector. The healthcare industry faces a variety of cyberattacks, each with potentially devastating consequences.
Below, we outline some of the most common attack vectors.
1. Ransomware Attacks and the Impact of RaaS
Ransomware attacks have become particularly notorious in healthcare due to the critical nature of the data involved. With the rise of Ransomware-as-a-Service (RaaS), even low-skilled attackers can now execute sophisticated ransomware campaigns.
The stakes are high in case of a ransomware attack on a healthcare organization, as delays in accessing critical patient data can lead to dire outcomes.
To proactively detect and mitigate these threats, healthcare organizations can leverage SOCRadar’s Dark Web Monitoring, which provides real-time alerts on potential ransomware plots and data leaks before they can cause damage.
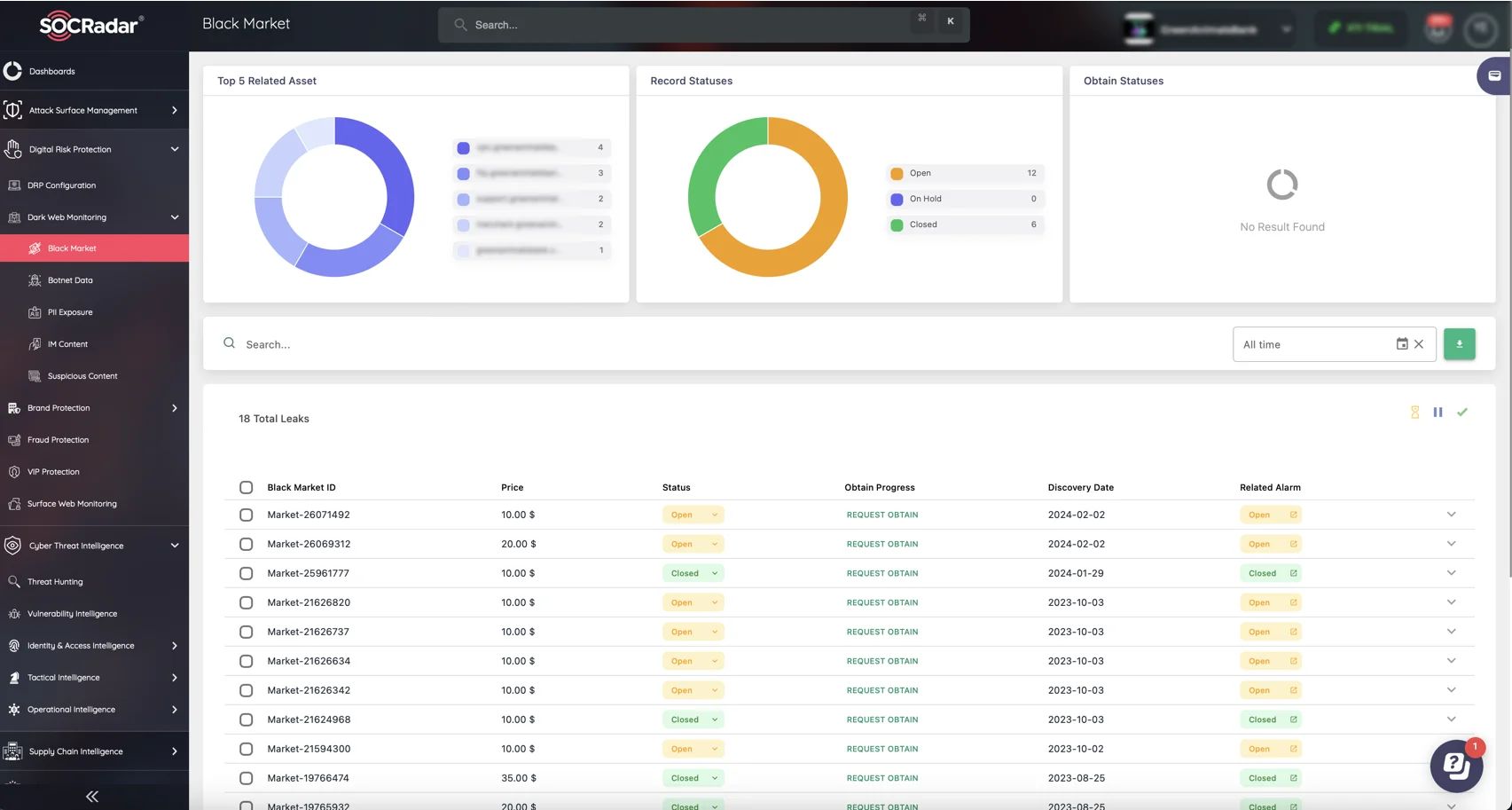
SOCRadar’s Dark Web Monitoring module – Monitor Black Markets, PII Exposure, Suspicious Content, and more
2. Phishing and Insider Threats
Phishing remains a persistent threat in the healthcare industry, exploiting the urgency and fast-paced environment typical of medical settings. Attackers craft deceptive emails to trick employees into revealing sensitive information or clicking on malicious links, leading to data breaches or malware installation.
The success of phishing attacks often stems from the high-pressure conditions under which healthcare workers operate and the occasional lack of awareness about cybersecurity threats.
These phishing schemes are closely linked to the broader issue of insider threats, which pose significant risks to healthcare organizations. Whether through negligence or malicious intent, employees with access to sensitive data may unintentionally aid cyberattacks by failing to follow security protocols or falling victim to phishing, even potentially exposing their credentials. Notably, a 2024 healthcare report by Kroll highlights that credential access is now the top concern for cybersecurity professionals in the industry – ranking even higher than threats like ransomware, BEC, and phishing itself.
3. Healthcare Supply Chain Attacks
Supply chain issues pose a significant threat in healthcare, where organizations rely heavily on numerous third-party vendors for essential services. Attackers often exploit vulnerabilities in these less secure elements to disrupt or gain access to broader healthcare systems.
An example of this is the February 2024 BlackCat ransomware attack on Change Healthcare, which disrupted payment processes across U.S. healthcare providers. This incident affected the entire healthcare supply chain, highlighting how ransomware can have far-reaching effects even without directly targeting every link in the chain.
Similarly, the July 2024 ransomware attack on OneBlood, a major non-profit blood donation service, crippled critical software systems, forcing a shift to manual operations.
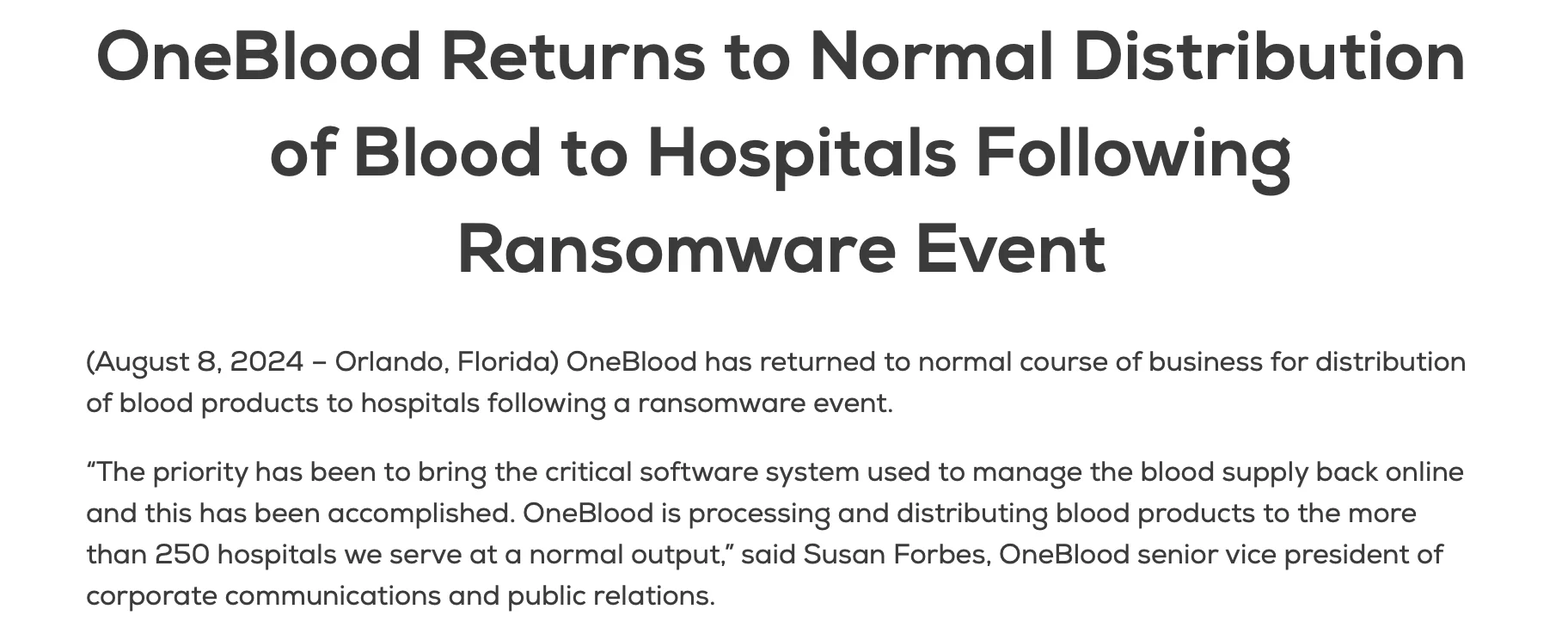
OneBlood’s statement about its recovery – August 8, 2024
This disruption severely impacted the availability of blood products, leading over 250 hospitals to activate critical blood shortage protocols.
Healthcare organizations can strengthen their defenses against supply chain attacks by utilizing SOCRadar’s Supply Chain Intelligence, which maps security statuses across the entire vendor network and provides actionable insights to prevent disruptions.
SOCRadar’s Supply Chain Intelligence module, 3rd Party Companies
4. IoT Vulnerabilities
The integration of Internet of Things (IoT) devices in healthcare has revolutionized patient care but has also introduced significant security risks. From health monitoring gadgets to advanced surgical robots, IoT devices often lack robust security measures, making them vulnerable to cyberattacks.
Cybercriminals exploit this expanded IoT attack surface to carry out data breaches, ransomware attacks, and even pose physical threats if devices like pacemakers or insulin pumps are compromised. The 2023 Healthcare Threat Landscape Report by SOCRadar highlights these risks, revealing vulnerabilities in IoT devices and an increase in phishing attacks targeting healthcare entities.
Moving forward, it is important to note that hacking remains the leading cause of data breaches in the healthcare industry, a trend highlighted by The HIPAA Journal.
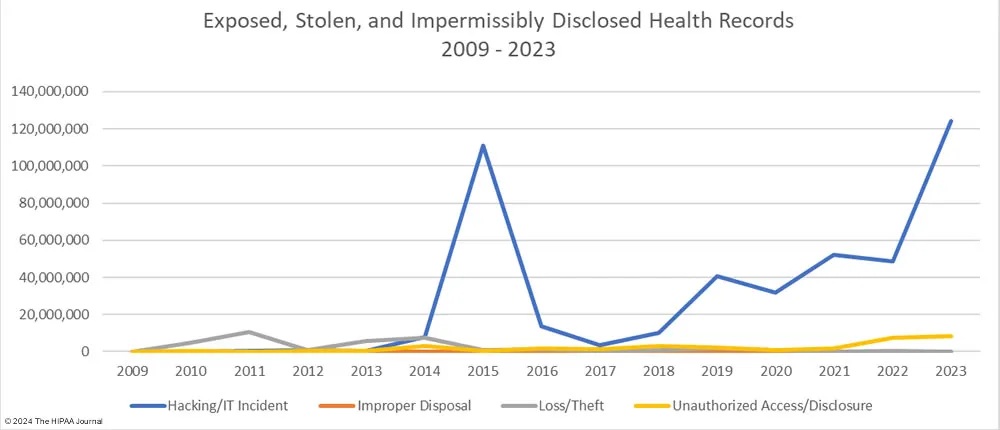
Cause of healthcare data breaches, 2009 – 2023 (The HIPAA Journal)
Further statistics show that the scale of compromised records has reached alarming levels, with over 124 million healthcare records breached in 2023 alone, representing a staggering 93.5% of all records compromised across various sectors.
The Clop ransomware group is said to have played a significant role in these large-scale breaches. In 2023, the ransomware operation exploited zero-day vulnerabilities in Fortra’s GoAnywhere MFT and Progress Software’s MOVEit Transfer, impacting nearly 2,600 organizations. These organizations included numerous healthcare providers.
SOCRadar’s dark web analysts have also reported a 58.3% global increase in ransomware attacks targeting the healthcare sector, with the U.S. experiencing an even higher surge of 64.8%. Despite a decrease in the profitability of ransomware – evidenced by the decline in ransom payments from 85% in early 2019 to 29% in Q4 2023 – the volume of attacks has grown as threat actors seek to maintain their revenue streams.
The Top Healthcare Cyber Attacks Through 2023-2024
The healthcare sector has witnessed some of the most devastating cyberattacks in recent history, with 2023-2024 marking a particularly turbulent period. Below are some of the top healthcare cyberattacks that made headlines in 2023 and thus far in 2024.
1. HCA Healthcare
Affected Patients: 11 million
HCA Healthcare, a major hospital and clinic operator in the U.S., suffered a significant data breach affecting at least 11 million patients across 20 states, including California, Florida, Georgia, and Texas.
The breach exposed sensitive information such as patient names, contact details, dates of birth, and upcoming appointment information. The data theft was traced to an external storage location used exclusively for automating email formatting, which the company swiftly disabled to contain the breach.
The hacker, who initially posted a sample of the stolen data online on July 5, 2023 attempted to extort HCA Healthcare by selling the data. In January 2024, the stolen data resurfaced on a dark web forum, underscoring the ongoing threat to the healthcare sector.
The hacker forum post from January 2024 (SOCRadar Dark Web News)
The HCA Healthcare breach is one of the largest in healthcare history; the incident, alongside other cyberattacks occurring around the same time, pointed to an escalating threat landscape targeting the US healthcare industry.
2. Perry Johnson & Associates
Affected Individuals: 9 million
Perry Johnson & Associates (PJ&A), a medical transcription service provider, suffered a major data breach compromising the personal and health information of 9 million individuals in the US.
This breach, the second largest US healthcare-related data breach in 2023, occurred between March 27 and May 2, with hackers accessing sensitive data, including patients’ names, dates of birth, addresses, medical record numbers, and diagnosis information. The breach also exposed Social Security numbers (SSNs), insurance details, and clinical information from medical transcription files.
PJ&A began notifying affected individuals on October 31, 2023, and later reported the incident to the Department of Health and Human Services, revealing the full scope of the breach. The company assured that no credit card or bank account information was compromised and that there was no evidence of data misuse for fraud or identity theft. However, the breach affected several healthcare providers, including Northwell Health and Cook County Health, prompting them to sever ties with PJ&A.
3. Welltok Inc
Affected Individuals: 8.5 million
Healthcare Software-as-a-Service (SaaS) provider Welltok Inc. reported a significant data breach in 2023, affecting 8.5 million individuals. The breach was part of the widespread exploitation of the MOVEit Transfer vulnerability by Cl0p, first disclosed and patched on May 31, 2023.
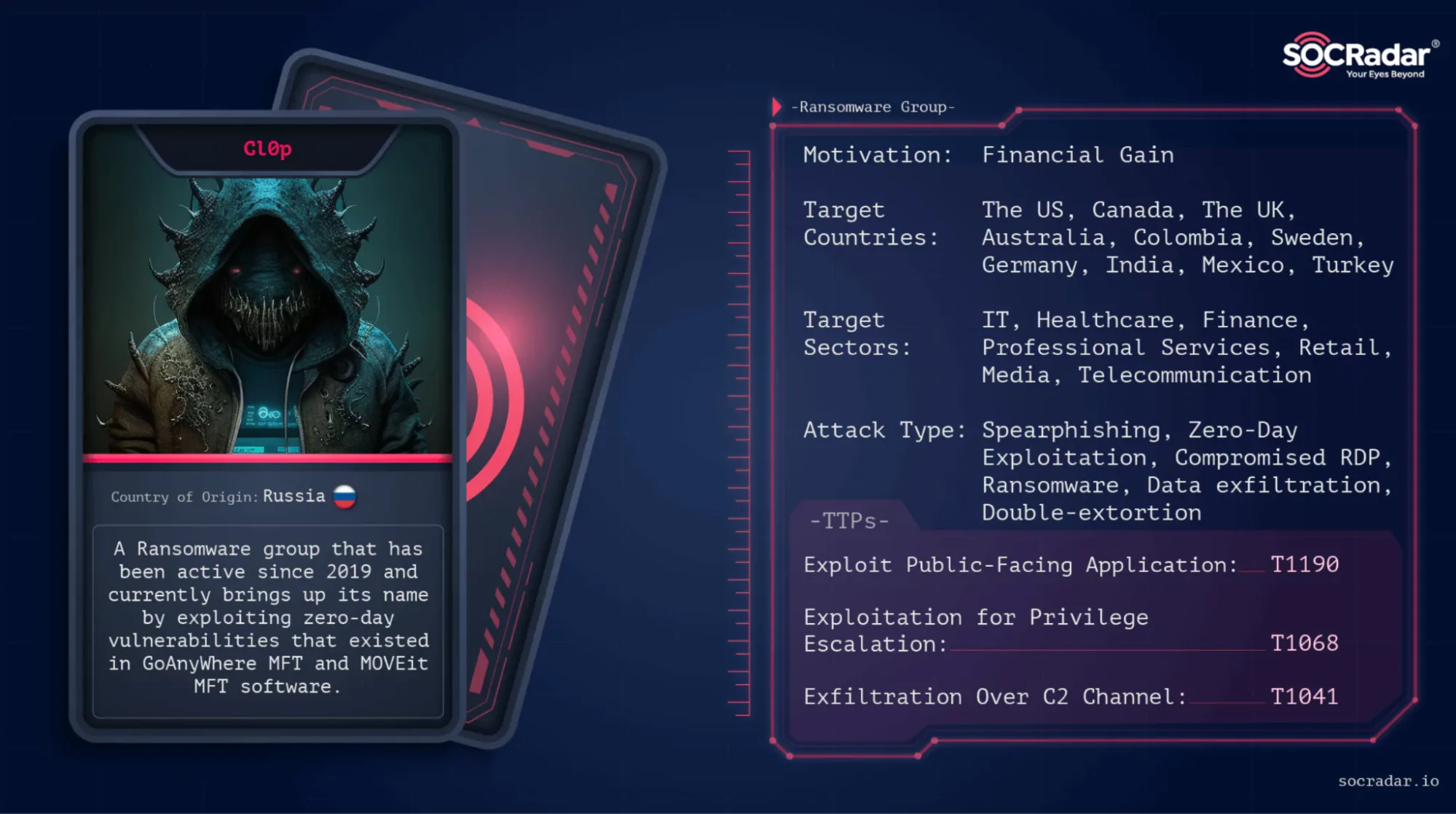
Learn more about Cl0p’s tactics and operations on SOCRadar’s Dark Web Profile
Despite promptly applying all available security patches, Welltok later discovered that unauthorized actors had exploited the vulnerability, leading to the exfiltration of data from their MOVEit Transfer server. The compromised data included names, addresses, email addresses, phone numbers, and, in some cases, Social Security numbers, health insurance information, and Medicare/Medicaid ID numbers.
The breach impacted individuals across 20 healthcare providers and plans, including major entities like Sutter Health, Mass General Brigham Health Plan, and several Blue Cross and Blue Shield organizations.
4. PharMerica Corp
Affected Individuals: 5.8 million
PharMerica Corp, a leading pharmacy services provider across 50 US states, experienced a significant data breach in March 2023, affecting over 5.8 million patients.
The breach exposed highly sensitive data, including full names, addresses, dates of birth, Social Security numbers (SSNs), medications, and health insurance information. The breach, which occurred on March 12, was discovered two days later, with PharMerica confirming the theft of client data by March 21. However, affected individuals were not notified until May 12, 2023.
The Money Message ransomware gang claimed responsibility for the attack, stating they had stolen 4.7 TB of data, which included at least 1.6 million unique records of personal information. On April 9, 2023, after their extortion deadline passed, the group published all the stolen data on their extortion site. This data was later reposted on a clearnet hacking forum, making it widely accessible.
5. Change Healthcare
Affected Organizations: Numerous/Undetermined
In early 2024, Change Healthcare, a critical player in the US healthcare infrastructure, was struck by a ransomware attack from the ALPHV (BlackCat) group. This attack caused significant disruption, particularly in prescription drug distribution, affecting pharmacies and hospitals nationwide for over ten days.
Following the attack, posts surfaced on the RAMP forum, suggesting that UnitedHealth Group might have paid a $22 million ransom to regain access to their systems. However, neither UnitedHealth nor the hackers confirmed this payment.
Complicating matters, an ALPHV affiliate known as “notchy” alleged that the ransomware group kept the entire ransom, violating their agreement to share profits. This affiliate also claimed to have accessed data from other healthcare firms partnered with Change Healthcare, raising concerns about further potential data breaches.
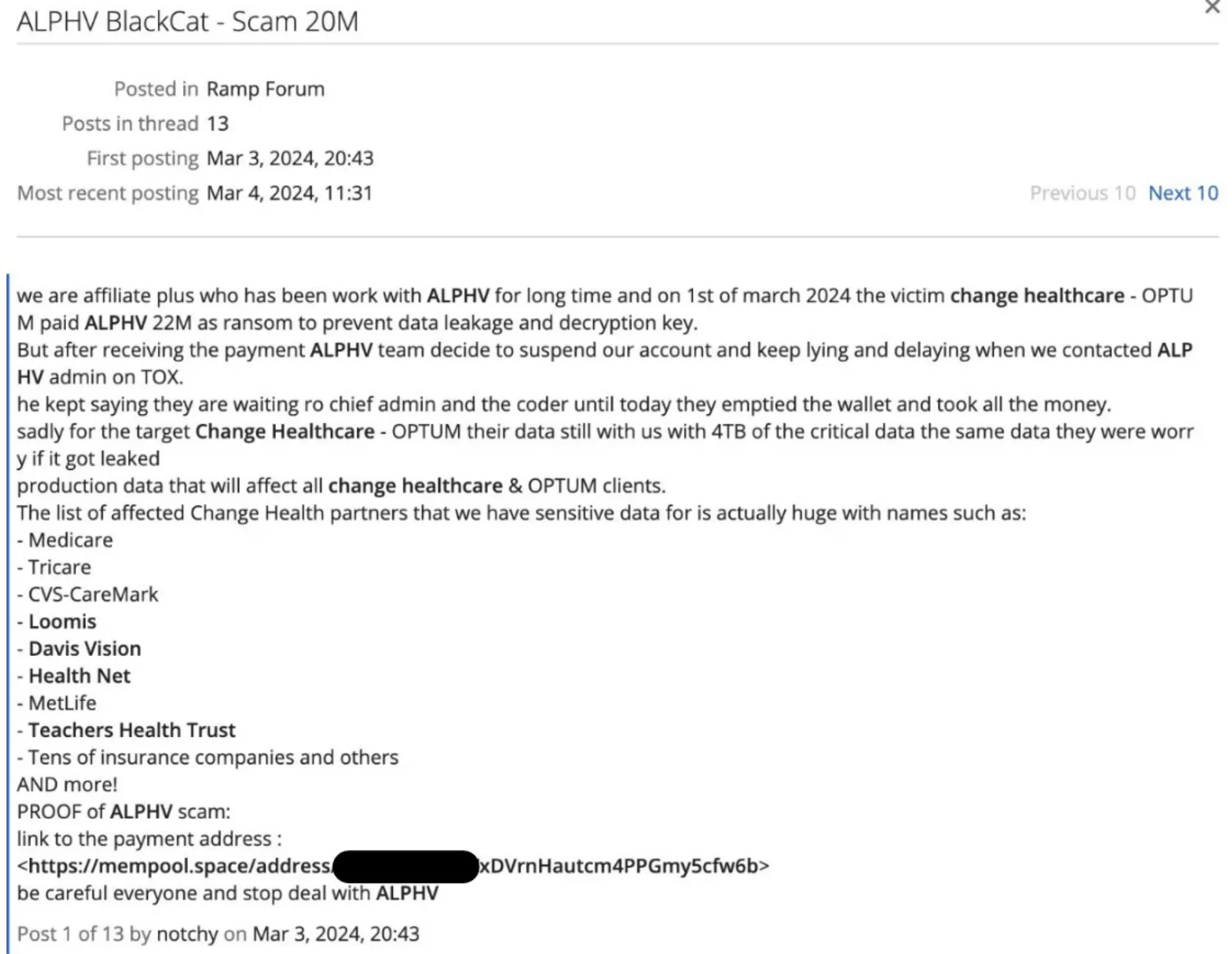
The forum post by notchy
Even more alarming, the ransom payment, if made, did not result in the deletion of the stolen data, as Notchy claimed to still possess sensitive information. This situation has led to fears that ALPHV is conducting an exit scam, especially after the group announced plans to shut down and sell its ransomware source code.
6. Cencora Healthcare
Affected Organizations: Numerous/Undetermined
In February 2024, Cencora, a major pharmaceutical services provider, experienced a significant data breach. This incident compromised the personal and health-related data of patients connected to some of the world’s largest pharmaceutical companies.
The breach was initially disclosed in a Form 8-K filing with the SEC, where Cencora confirmed that unauthorized parties had accessed and exfiltrated sensitive information from its systems.
Although Cencora did not provide details at the time, further developments revealed the breach’s broad impact. The California Attorney General’s office published data breach notifications from 11 major pharmaceutical firms, all linked to the February Cencora breach. These companies, including Novartis, Bayer, AbbVie, and GlaxoSmithKline, warned that the compromised data included patients’ full names, addresses, health diagnoses, medications, and prescriptions.
Despite the extensive data exposure, Cencora’s investigation, which concluded in April 2024, found no evidence that the exfiltrated information had been publicly disclosed or used for fraudulent activities.
7. HealthEquity
Affected Individuals: 4.3 million
In March 2024, HealthEquity, a healthcare benefits administrator, experienced a data breach affecting the personal and protected health information of 4.3 million individuals.
The breach involved unauthorized access to an unstructured data repository outside of HealthEquity’s core network, containing sensitive information such as customer names, addresses, phone numbers, Social Security numbers, and health-related details like diagnoses and prescriptions.
The breach was traced back to a compromised account belonging to one of HealthEquity’s vendors. The hacker used stolen credentials to access the data repository, raising concerns about the security of third-party vendor relationships. HealthEquity’s data breach notice, filed with the Maine Attorney General, revealed that the stolen data also included details about customers’ benefits, employer information, and some payment card information.
Despite the significant impact, HealthEquity described the breach as an isolated incident and confirmed that it was unrelated to other recent breaches involving major companies like Snowflake.
8. MediSecure
Affected Individuals: 12.9 million
In November 2023, MediSecure, a key provider of electronic prescriptions in Australia, suffered a devastating ransomware attack that exposed the personal and health information of approximately 12.9 million individuals. This incident is one of the largest data breaches in Australian history, compromising the sensitive data of nearly half the population.
The breached data included full names, phone numbers, dates of birth, home addresses, Medicare numbers, and detailed prescription information.
The attack persisted undetected until May 2024, when MediSecure confirmed the loss of 6.5 terabytes of data. The breach has not only exposed millions of Australians to potential targeted cyberattacks but also raised significant concerns about the cybersecurity posture of critical infrastructure in the healthcare sector.
The Australian authorities have responded by issuing warnings about potential scams and providing online resources and mental health support for affected individuals. The incident has sparked a national conversation on the need for stronger cybersecurity measures and legislative action to protect critical infrastructure. MediSecure, after losing its primary government contract, entered voluntary administration in June 2024, further complicating the response to this significant breach.

July 2024 statement from MediSecure
9. Rite Aid
Affected Individuals: 2.2 million
Rite Aid, a prominent US pharmacy chain, experienced a significant data breach following a ransomware attack on June 6, 2024.
The RansomHub ransomware group claimed responsibility for the attack, alleging they had exfiltrated over 10 GB of sensitive customer information, including names, addresses, dates of birth, driver’s license numbers, and Rite Aid rewards numbers.
The breach compromised the personal data of approximately 2.2 million individuals, with the exposed information linked to purchases made between June 6, 2017, and July 30, 2018. Rite Aid discovered the breach on June 20, 2024, and promptly launched an investigation into the incident.
RansomHub set a leak timer for July 26, threatening to release the stolen data unless their ransom demands were met.
10. NHS (Qilin)
Affected Data: Nearly 400GB of healthcare data
In June 2024, the Qilin ransomware group executed a major cyberattack on Synnovis, a pathology laboratory servicing NHS organizations across London. The attack led to the theft of nearly 400GB of sensitive healthcare data, severely disrupting patient care across multiple NHS trusts and GP surgeries.
The incident caused delays in medical procedures, blood stock shortages, and the cancellation of over 1,100 operations.
On June 21, Qilin published the stolen data online after failing to extort a ransom from Synnovis. The leaked information, shared on the darknet and Telegram, reportedly includes patient names, dates of birth, NHS numbers, and descriptions of blood tests. The attack has sparked a coordinated investigation involving Synnovis, NHS England, and the National Cyber Security Centre (NCSC) to assess the extent of the data breach.
The Growing Threat Landscape
The healthcare sector has faced an alarming surge in cyberattacks, with incidents in 2023-2024 causing widespread disruptions and compromising the personal data of millions. While each of the attacks mentioned had severe consequences, they are just a fraction of the cyber threats targeting this critical industry. There are also emerging threat actors, such as Qilin and RansomHub, which have been active in 2024, launching crippling attacks that underscore their growing menace.
Qilin, also known as Agenda ransomware, has rapidly gained notoriety for its sophisticated and adaptable tactics. The group has been linked to at least 15 healthcare sector infections since October 2022, as noted by the US Department of Health and Human Services. Their high-profile attack on NHS England’s pathology services provider, Synnovis, in June 2024 led to the cancellation of numerous medical procedures and disruptions in patient care across London hospitals.

Learn more about Qilin’s tactics and operations on SOCRadar’s Dark Web Profile
RansomHub has also emerged as a significant threat in 2024, with its first major claim against a Brazilian company, YKP, followed by numerous other attacks. Speculated to be a possible rebranding of ALPHV (BlackCat), RansomHub has distinguished itself by making claims backed by data leaks. The group’s operations resemble those of traditional Russian ransomware setups, and their recruitment of affiliates through forums like RAMP suggests a well-organized, globally dispersed operation. Despite the similarities, it remains uncertain if RansomHub is indeed a new face for ALPHV or an entirely distinct entity.
These emerging groups join the ranks of other notorious ransomware operators like BlackCat (ALPHV), Cl0p, and BlackSuit (Royal), all of whom have inflicted significant damage on the healthcare sector. BlackCat has aggressively targeted healthcare organizations since late 2023, while Cl0p’s 2023 MOVEit attack compromised data from over 2,700 organizations, including many in the healthcare sector. BlackSuit, a strain linked to the Royal ransomware family, has also become a serious threat since its emergence in May 2023.
Staying informed on the tactics and operations of these emerging threats is critical. SOCRadar’s Threat Actor Intelligence module offers comprehensive profiles and real-time updates on the latest cybercriminal activities targeting the healthcare sector.
SOCRadar’s Threat Actor Intelligence module
Conclusion
In conclusion, the healthcare industry continues to face unprecedented cybersecurity challenges, with increasingly sophisticated attacks that threaten patient safety and operational stability.
In 2023 alone, over 124 million healthcare records were compromised, accounting for nearly 93.5% of all breached records across sectors. The rise of Ransomware-as-a-Service (RaaS) and increasing exploitation of supply chain vulnerabilities have only heightened these risks, making it clear that traditional security measures are no longer sufficient.
Integrating advanced monitoring solutions, such as SOCRadar’s Dark Web Monitoring and Supply Chain Intelligence, can offer vital insights into potential risks and help detect threats before they manifest.