
Joint Advisory Warns of Truebot Malware Variants Infecting US and Cana...
Joint Advisory Warns of Truebot Malware Variants Infecting US and Canadian Networks Today, a joint Cybersecurity Advisory (CSA) was released by several organizations, including the Cybersecurity and I...
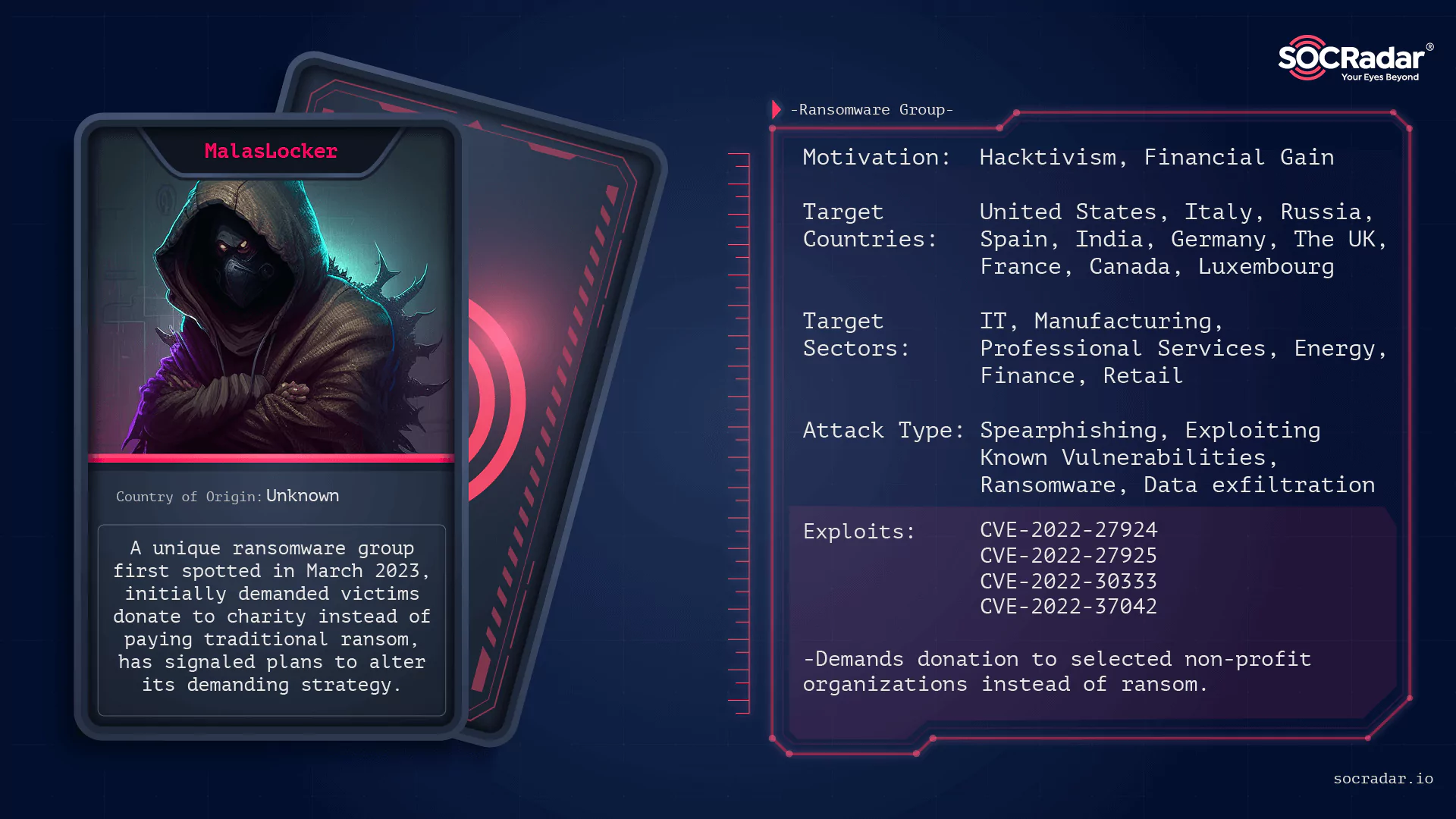
Dark Web Profile: MalasLocker Ransomware
Dark Web Profile: MalasLocker Ransomware A new player has emerged on the stage of cybercrime by announcing multiple victim announcements at the end of April. Dubbed “MalasLocker,” this ran...

Ransomware Chronicles: Unveiling the Monthly Trends in 2023
Ransomware Chronicles: Unveiling the Monthly Trends in 2023 Welcome to our “Ransomware Trends in 2023: A Live Blog of Insights and Analysis.” This live blog delves into the intricate world...

CVSS v4.0 on the Horizon
CVSS v4.0 on the Horizon [Update] November 2, 2023: See the subheading “FIRST Has Released CVSS v4.0: The Next Generation of Vulnerability Scoring” The Common Vulnerability Scoring System (CVSS) is a...

CISA's Recent Summary: Critical Vulnerabilities Impacting Apple and Ot...
CISA’s Recent Summary: Critical Vulnerabilities Impacting Apple and Other Prominent Entities CISA has recently published a Vulnerability Summary for the previous week. This summary encompasses s...

Revealing Critical SAP Vulnerabilities and Proof-of-Concept Exploit
Revealing Critical SAP Vulnerabilities and Proof-of-Concept Exploit In the world of cybersecurity, staying informed about the latest vulnerabilities is crucial for organizations, especially when it co...

US Experiences Increased DoS and DDoS Activities Across Multiple Secto...
US Experiences Increased DoS and DDoS Activities Across Multiple Sectors The United States is currently observing an upswing in targeted Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS...

Major Data Leaks on TikTok, Instagram, and Yahoo
Major Data Leaks on TikTok, Instagram, and Yahoo Welcome to this week’s dark web summary from SOCRadar. Our vigilant Dark Web Team has been working around the clock to keep you updated on the la...

APT Profile: FIN7
APT Profile: FIN7 In the world of cybercrime, a name resounds with an unsettling echo – FIN7. This notorious cyber gang has left its mark on the globe, causing digital chaos wherever they g...

The Mindset Behind Phishing Campaigns
The Mindset Behind Phishing Campaigns Phishing attacks are cybercrimes that target individuals, businesses, and organizations. These attacks use deception and manipulation techniques to tric...

Best of Both Worlds: CISA’s Known Exploited Vulnerabilities Integratio...
Best of Both Worlds: CISA’s Known Exploited Vulnerabilities Integration with SOCRadar External Attack Surface Management In today’s digital landscape, the threat of cyberattacks looms large, wit...
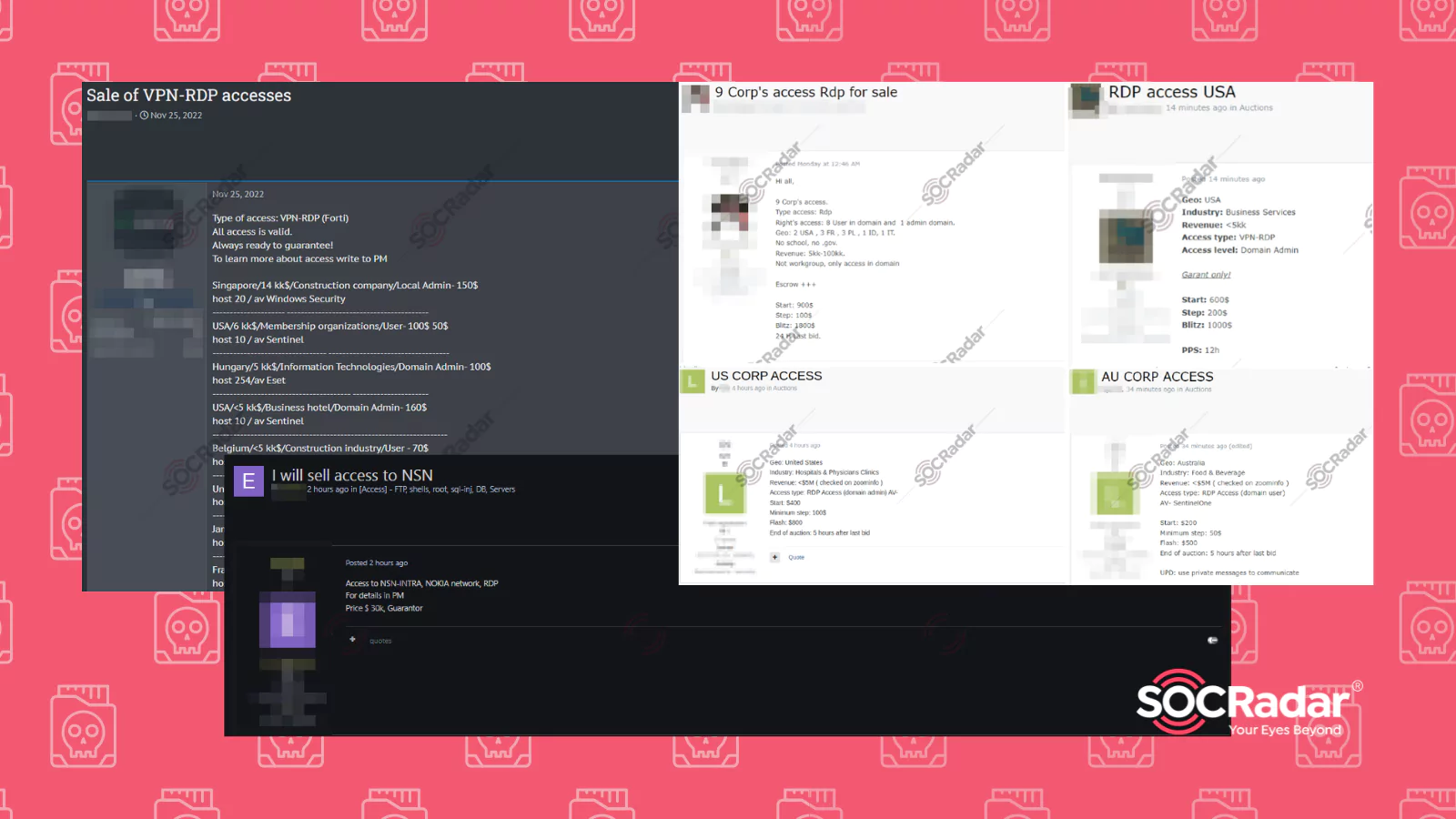
RDP Access Sales on Dark Web Forums Detected by SOCRadar
RDP Access Sales on Dark Web Forums Detected by SOCRadar Remote Desktop Protocol, or RDP, is a protocol developed by Microsoft. It allows the user to control another computer over a network connection...

APT Profile: Turla
APT Profile: Turla In the digital age, war has transitioned into the virtual world, where many types of cybercriminals, such as hacktivists and nation-state actors, are called Advanced Persistent Thre...

Using OSINT to Strengthen Organizational Security
Using OSINT to Strengthen Organizational Security Open-source intelligence or “OSINT” is collecting and analyzing data gathered from publicly available open sources (social media, news, dark web, etc....

Exploring the Dark Web Job Market
Exploring the Dark Web Job Market The dark web, notorious for its illicit activities, has evolved into a bustling marketplace for various illegal purposes. It serves as a hub for cybercriminals, offer...

The Surge in Cyber Attacks on Latin American Governments
The Surge in Cyber Attacks on Latin American Governments Latin America, a region bustling with potential and promise, has witnessed a worrying trend of escalating cyber threats directed at government ...

Internet-Exposed Devices within Federal Networks
Internet-Exposed Devices within Federal Networks As technology evolves and becomes increasingly integral to all aspects of society, the need for robust cybersecurity measures becomes more pressing. On...

Fake Extortion: How to Tackle and How to Verify?
Fake Extortion: How to Tackle and How to Verify? Today, one of the most critical aspects of maintaining a respectable business is to have resistance against cyber attacks. To that aim, organizations t...

Credential Theft Attacks Surge: Microsoft Raises Red Flag on Midnight ...
Credential Theft Attacks Surge: Microsoft Raises Red Flag on Midnight Blizzard (APT29) Microsoft has identified Midnight Blizzard, a Russian state-affiliated hacking group also known as APT29, as the ...

High-Severity Vulnerabilities Identified and Patched in BIND 9 DNS Sof...
High-Severity Vulnerabilities Identified and Patched in BIND 9 DNS Software The BIND 9 DNS software suite, an integral part of the Domain Name System (DNS), has recently received updates to neutralize...



































