
Phishing: A Growing Threat to E-commerce
Phishing: A Growing Threat to E-commerce Phishing is a tactic that targets victims primarily through emails and SMS. Emails appear to be from a legitimate source, but their main objective is to steal ...

Cyber Threats to the E-commerce Sector Increased by 37 Percent
Cyber Threats to the E-commerce Sector Increased by 37 Percent The E-Commerce Landscape Report prepared by SOCRadar analysts has been published this week. The report includes a detailed analysis of th...

Why Cyber Threats Against E-commerce Are Important?
Why Cyber Threats Against E-commerce Are Important? The number of cyber threats against e-commerce that appeared on the darknet and the deep web continues to increase from year to year. SOCRadar has r...
What Are the Cyber Threats You Should Know Before Black Friday?
What Are the Cyber Threats You Should Know Before Black Friday? Since the start of the Covid-19 Pandemic, how we do business has dramatically changed. The stocks of big online retailers like Amazon, C...

The Week in Dark Web - 22 November 2021 - Access Sales and Data Leaks
The Week in Dark Web – 22 November 2021 – Access Sales and Data Leaks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. Again, rise of ransomwa...

How Private is Your VPN?
How Private is Your VPN? The term “Virtual Private Network” (VPN) refers to the ability to create a secure network connection while using public networks. VPNs encrypt your internet traffic and hide y...

Why Do Organizations Need IAM?
Why Do Organizations Need IAM? Identity and access management (IAM) is a discipline to ensure that the right people and job roles (identities) can access the tools they need in the organization. The e...

The Week in Dark Web - 15 November 2021 - Ransomware Attacks and Data ...
The Week in Dark Web – 15 November 2021 – Ransomware Attacks and Data Leaks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. Again, rise of ra...

What is External Attack Surface Management?
What is External Attack Surface Management? The attack surface is all hardware, software and cloud assets accessible from the internet that processes or stores data. All exposed IT assets, from server...

A Rising Threat in Mobile: What is Banking Malware?
A Rising Threat in Mobile: What is Banking Malware? Mobile Banking malware is a malware family consisting of malicious apps and trojans designed to infect one’s system and collect financial data, pers...

Dark Web Profile: Phobos Ransomware
Dark Web Profile: Phobos Ransomware Phobos ransomware, first discovered in December 2018, is another notorious cyber threat that targets businesses. Unlike other cybercrime gangs that go after big hun...

What is Vulnerability Management?
What is Vulnerability Management? The increasing number of vulnerabilities that security teams have to deal with makes it impossible to try to remediate all critical vulnerabilities. In fact, a small ...

The Week in Dark Web - 8 November 2021 - Ransomware Attacks and Data L...
The Week in Dark Web – 8 November 2021 – Ransomware Attacks and Data Leaks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. Again, rise of ran...

How Can OSINT Tools be Used and What is External Attack Surface Manage...
How Can OSINT Tools be Used and What is External Attack Surface Management? SOCRadar defines itself as a platform providing an early warning system with extended threat intelligence. In other words, S...

What is Managed Detection and Response (MDR) and How Does It Work?
What is Managed Detection and Response (MDR) and How Does It Work? Over the last few years, it has been understood explicitly that preventive cybersecurity technologies are not effective enough to sec...
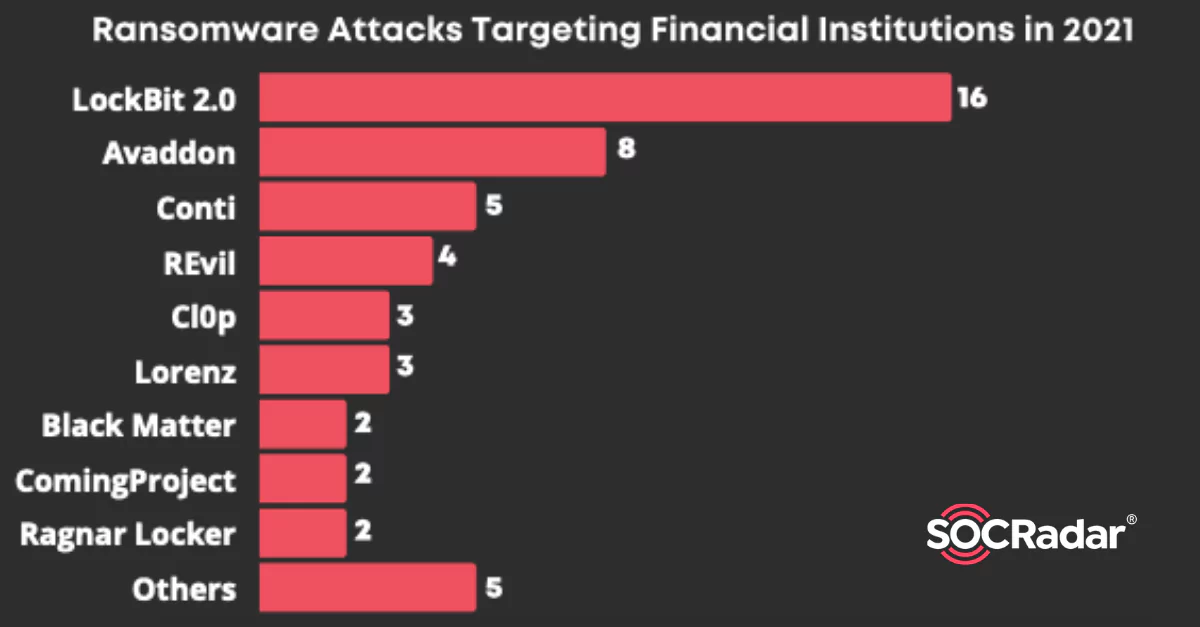
Around 50 Ransomware Attacks Targeting Financial Institutions
Around 50 Ransomware Attacks Targeting Financial Institutions The Q3 Finance Industry Threat Landscape Report prepared by SOCRadar analysts has been published this week. The report includes a detailed...

The Rising Threat in the Financial Industry: DDoS Attacks
The Rising Threat in the Financial Industry: DDoS Attacks The Q3 Finance Industry Threat Landscape Report prepared by SOCRadar analysts has been published this week. The report includes a detailed ana...

Dark Web Threat Profile: Grief Ransomware Group
Dark Web Threat Profile: Grief Ransomware Group New ransomware called Grief was considered to be a new operation at first. Security researchers noticed that a new Grief gang carries similarities with ...

Threats to Financial Institutions on the Rise
Threats to Financial Institutions on the Rise Financial institutions, especially banks, are always one of the significant targets of threat actors. The number of cyber threats against financial instit...

The Week in Dark Web - 1 November 2021 - Ransomware Attacks and Data L...
The Week in Dark Web – 1 November 2021 – Ransomware Attacks and Data Leaks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. Again, rise of ran...

































