
Disrupt Attacker Infrastructure to Prevent Future Attacks with Takedow...
Disrupt Attacker Infrastructure to Prevent Future Attacks with Takedown Service Malware and phishing sites harm companies and organizations all over the world. Through removing sites and blocking atta...

The 8 Key Lessons From the SolarWinds Attacks
The 8 Key Lessons From the SolarWinds Attacks [Update] October 31, 2023: See the subheading: “Repercussions of SolarWinds Attacks: SEC Charges for Fraud.” Nation-state threat actors breached the suppl...
How Credential Stuffing Let To Hack Trump Campaign Website?
How Credential Stuffing Let To Hack Trump Campaign Website? The billions of login credentials available on the dark web make it easy for cybercriminals to steal login credentials. It has been widely r...

How Pandemic Affected Information Security
How Pandemic Affected Information Security ...

How To Detect and Prevent Business Email Compromise (BEC) Attacks?
How To Detect and Prevent Business Email Compromise (BEC) Attacks? ...

Top 5 Critical Vulnerabilities Behind Ransomware Attacks
Top 5 Critical Vulnerabilities Behind Ransomware Attacks Cybercriminals use encrypted ransomware that has become the most common type because it is difficult to crack the encryption and remove the mal...

The Age of Credential Stuffing & Account Takeover
The Age of Credential Stuffing & Account Takeover For mobile and web applications, credential stuffing attacks are considered among the top threats. While on average hackers can find matches betwe...

How To Takedown Phishing Domains for Free
How To Takedown Phishing Domains for Free ...

Top Threat Intelligence Use Cases for the E-commerce Industry-II
Top Threat Intelligence Use Cases for the E-commerce Industry-II Prevention of the landscape is no longer enough in today’s cybersecurity. All have never faced such high and concrete threats from adva...

Top Threat Intelligence Use Cases for the E-Commerce Industry-I
Top Threat Intelligence Use Cases for the E-Commerce Industry-I The prevention of the landscape is no longer enough in today’s cybersecurity. All have never faced such high and concrete threats from a...

Top Threat Intelligence Use Cases for the Finance Sector-II
Top Threat Intelligence Use Cases for the Finance Sector-II Security departments in the financial industry are facing a daunting mission. They have to defend the company from an immense amount of indi...

Using Google Dorks for Threat Intelligence Operations
Using Google Dorks for Threat Intelligence Operations Enterprises have to deal with a range of mass campaigns as well as advanced attacks that target a specific industry or company. Threat actors use ...

Top Threat Intelligence Use Cases for the Finance Sector-I
Top Threat Intelligence Use Cases for the Finance Sector-I Security departments in the financial industry are facing a daunting mission. They have to defend the company from an immense amount of indis...

How Web Skimming Attacks Happen & What You Can Do to Protect Yourself
How Web Skimming Attacks Happen & What You Can Do to Protect Yourself ...

How to (Safely) Access the Deep Web and Darknet
How to (Safely) Access the Deep Web and Darknet You have definitely heard there is a deep side to the internet where not everyone can access it. That is considered by many as hazardous and even illega...

Tools and Features That Can Be Used To Detect Sensitive Data Leaks Fro...
Tools and Features That Can Be Used To Detect Sensitive Data Leaks From Github – Part 2 In part 1 of this blog series, we discussed a few popular osint tools that help developer’s find leaked informat...
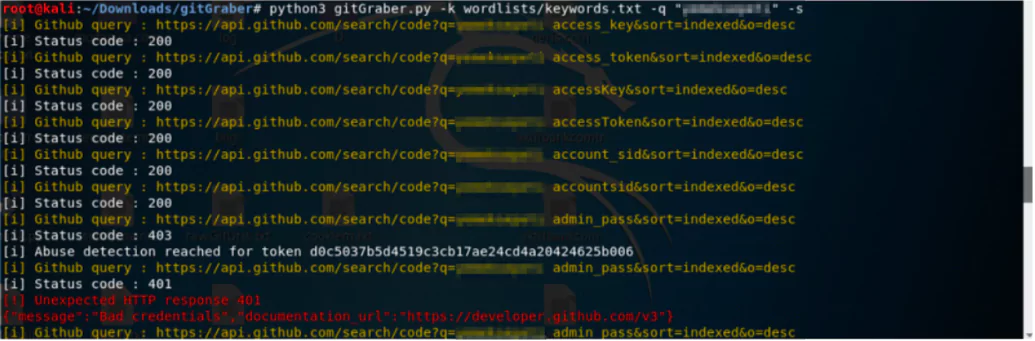
Tools and Features That Can Be Used To Detect Sensitive Data Leaks Fro...
Tools and Features That Can Be Used To Detect Sensitive Data Leaks From Github – Part 1 Back in the time when there was no Github, developers used to share codes in local servers of the company, or ev...

Different Kinds of Impersonating: Phishing & Domain Squatting
Different Kinds of Impersonating: Phishing & Domain Squatting Phishing and domain squatting are commonly used by threat actors to achieve different kinds of goals against an organization. Among th...

6 Benefits You Can Expect From Your Next Digital Risk Protection Solut...
6 Benefits You Can Expect From Your Next Digital Risk Protection Solution In case of a cybersecurity investment, it’s not always possible to satisfy the board by repeatedly saying “better safe than so...

Responding to Risks of Finance Sector
Responding to Risks of Finance Sector Financial services companies in the world witnessed a sharp rise in data breaches which shows how the sector is under attack from threat actors. For example, in t...































