
Cyber Deception at the Ballot Box: Unmasking the Phishing Epidemic in Election Campaigns
During periods of elections, people’s desire to obtain knowledge is outstanding, and they are overloaded with messages varying from fliers to social media advertisements. Campaigns for candidates raise tensions, and social balances are more sensitive than ever. Elections provide a unique opportunity for cybercriminals to mask themselves and their attacks.
From a cybersecurity perspective, elections are high-profile and high-risk events with significant political, economic, and social consequences. Elections have a large and complicated attack surface that involves many stakeholders, such as political campaigns, government agencies, voting systems, and voters.
The technological infrastructure of the electoral system creates new security vulnerabilities and attack vectors that cyber attackers can exploit. The election process provides a suitable environment for cyber threats, including data theft, espionage, and online disinformation campaigns.
According to ENISA (The European Union Cybersecurity Agency), The election lifecycle has four steps;
- The maintenance of the electoral register
- The public political campaigning process
- The voting process
- The delivery of the results
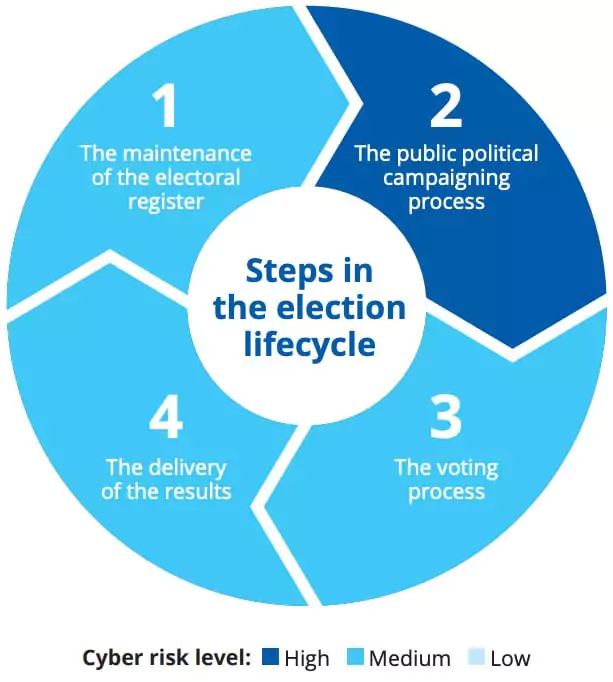
The second phase, “the public political campaigning process,” has the highest cyber security risk. And it has been the scene of disinformation and data leak attacks on various elections.
Recent history also has shown examples of cybersecurity incidents in the election process:
- The Nigerian government announced that it recorded 12.9 million (12,988,978) cyber attacks during the 2023 Nigerian presidential election, originating from within and outside the country.
- Gert Auväärt, head of the National Cyber Security Centre-Estonia (NCSC-EE), told March 5, 2023, Estonia’s Parliamentary elections were targeted by unsuccessful cyberattacks that covered a wide range of recognized threat actor behavior.
- Starting January 11, 2023, A Russian affiliated hacktivist group NoName057 initiated Distributed Denial of Service (DDoS) attacks targeting websites associated with the impending Czech presidential election, set to occur in just two days. The group justified these cyber-attacks through their Telegram channels by citing the anticipated training of 4,000 Ukrainian soldiers at Libavá, a Czech military training facility. They claimed this was their motive for choosing to “engage” in the Czech electoral process.
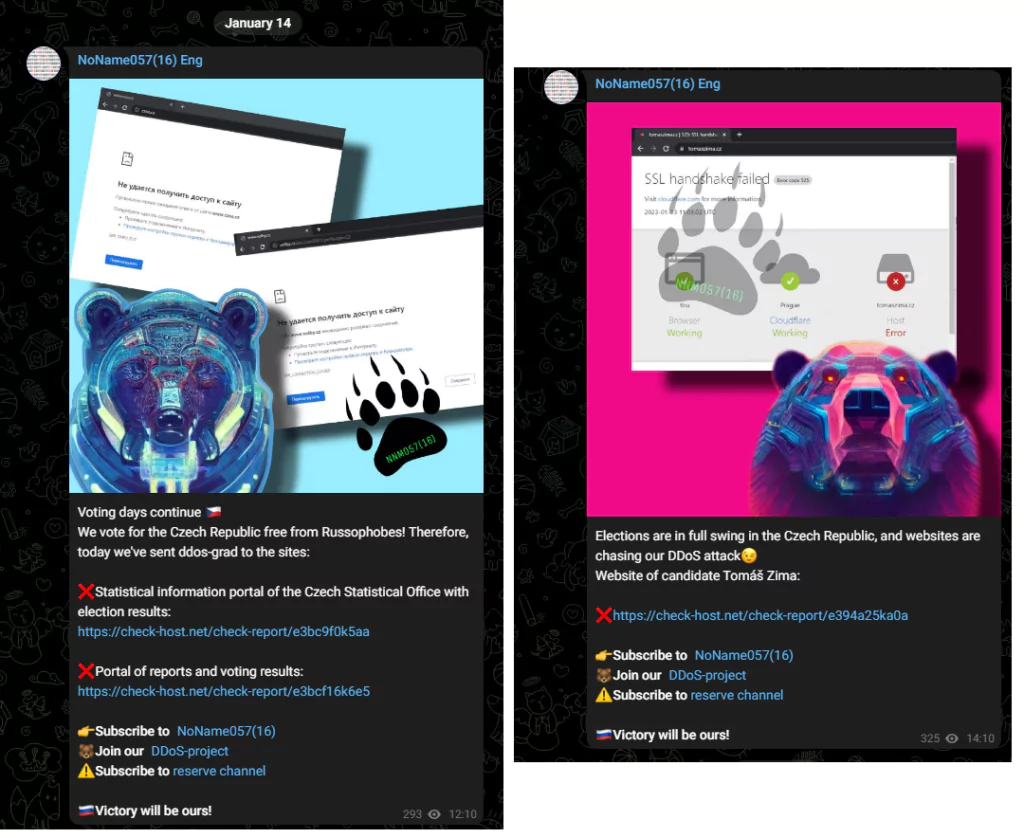
Considering the cyber risks in the election process, the most emphasized issues are; attacks on electronic election systems aimed at directly influencing voting results, manipulation and disinformation attempts aimed at indirectly influencing voting results, and DDoS attacks aimed at disrupting the election process.
However, the risks are not limited to electronic voting or voting machines. As a result of the wide election-specific attack surface, the risks are not only limited to government electoral systems but also involve individual candidates, political parties, election officers, and voters. In this context, phishing attacks can gather sensitive information or gain unauthorized access to campaign-related systems by targeting political campaigns, media outlets, or individual candidates.
Phishing Attacks on the Election Process
Regarding elections, phishing attacks can be used to:
- Steal login credentials for election-related systems, such as voter registration databases or election management systems.
- Distribute malware, such as keyloggers or remote access tools, that can be used to steal data or gain unauthorized access to systems.
- Spread disinformation or influence public opinion: Threat actors may deceive voters by impersonating a trusted source or sending fraudulent messages that appear to come from an official election-related source.
- Target individual voters for financial gain: By impersonating a political campaign or party, threat actors can ask for donations or attempt to steal credit card information or other financial details to carry out fraudulent transactions.
The 2016 US presidential election is one of the most well-known cases of a cyber attack on a political election. Democratic National Committee (DNC) staff were the victims of a spear-phishing attack, and the stolen e-mails were made public by Wikileaks. The e-mails contained information that adversely impacted public opinion over the DNC and the Clinton campaign.
Another example is the 2017 French presidential election, in which Emmanuel Macron’s campaign was targeted by a phishing attempt, resulting in the leak of thousands of e-mails and documents right before the election. The leaked documents contained essential details regarding Macron’s campaign strategy and financing. A group of hackers known as “Fancy Bear” exposed the stolen e-mails and documents online.
Official authorities have also warned the public about the potential risks of phishing attempts during the election process. Several warnings and recommendations have been issued in this regard.
On October 02, 2020, before November 3, 2020, US presidential Election, the Cybersecurity and Infrastructure Security Agency (CISA) and The Federal Bureau of Investigation (FBI) released a public service announcement under the title “Spoofed Internet Domains and E-mail Accounts Pose Cyber and Disinformation Risks to Voters” to help the public identifying and avoiding spoofed election-related internet domains during the 2020 election year.
On March 29, 2022, the FBI released a notification (20220329-001) under the title ‘Cyber Actors Target US Election Officials with InvoiceThemed Phishing Campaign to Harvest Credentials‘ and warned US election officials of a widespread and ongoing phishing campaign trying to steal credentials since at least October 2021.
In June 2022, the Elections Department Singapore (ELD) released a scam and phishing attempt advisory about an e-mail pretending to be from the “Elections Department Singapore” and including a “new replacement poll card” as an attachment. ELD warned, “This e-mail is FAKE and does not originate from ELD, members of the public are advised to ignore the e-mail and avoid clicking on the attachments.”
The case of Singapore demonstrates that the “election” title itself is a useful phishing instrument, even if there is no election process. However, the Turkish presidential election process, which will be held soon, provides examples of ongoing phishing attacks. The Turkish presidential and general elections are scheduled on May 14, 2023. The election process in Türkiye is currently in the “Public political campaigning process” step, which is the riskiest in terms of the cyber security phase of the election lifecycle.
In March, e-mails with the subject of “You need to verify your voter registration” (Turkish: Seçmen kaydınızı doğrulamanız gerekiyor.) were sent to voters, with the name and logo of official institutions used to give the appearance that legitimate organizations issued them.

Phishing e-mails with the phrase “verify your voter registration here” (Turkish: Seçmen kaydınızı buradan doğrulayın) were sent to voters from fraudulent e-mail addresses such as [email protected]; [email protected]; [email protected].
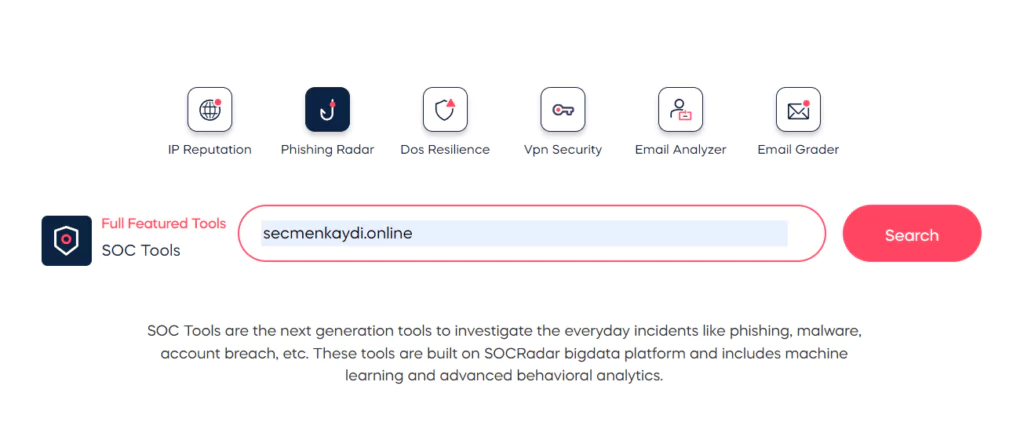
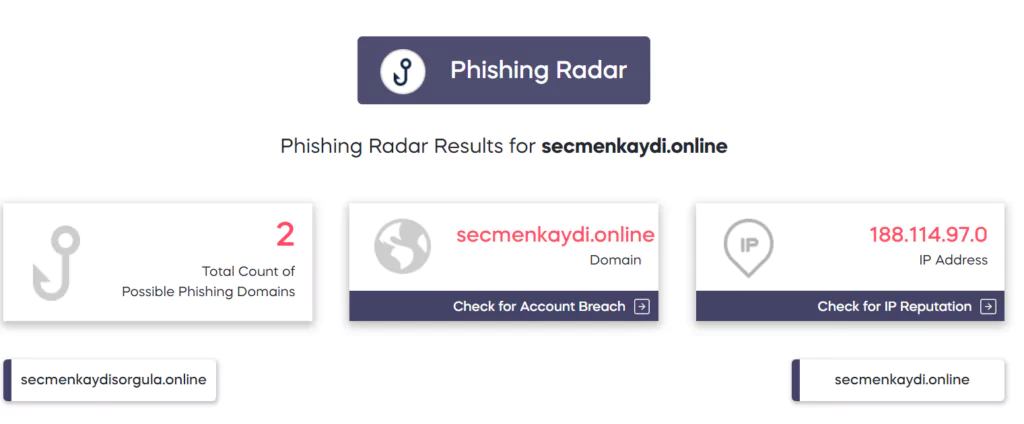
Official authorities confirmed the existence of such e-mails and advised voters to be careful about them.
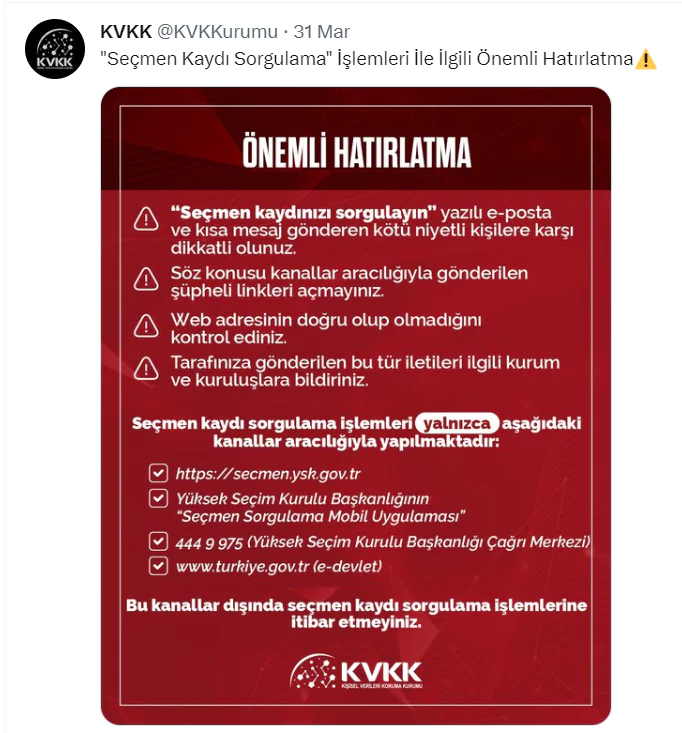
Threat actors can use the information they obtain through phishing attacks for malicious purposes. Personal information can be used for identity theft, such as applying for loans or credit cards or gaining access to other personal data. It can be used as initial access for further cyber-attacks. Voter registration information or other official documents may also be sold on the dark web.
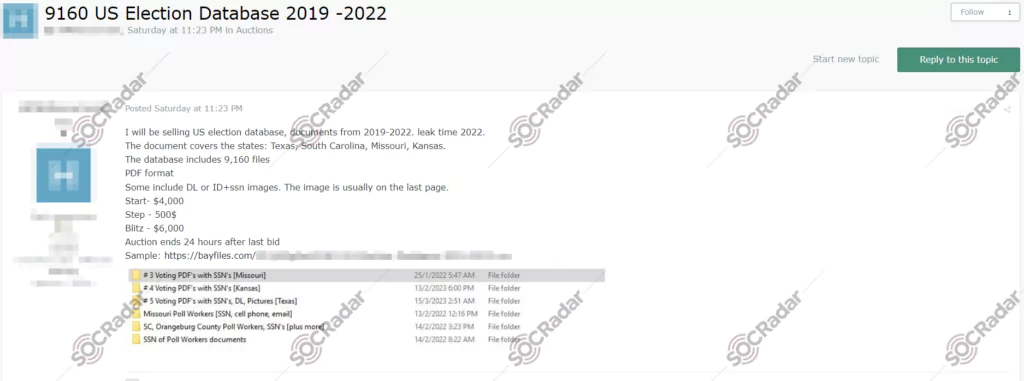
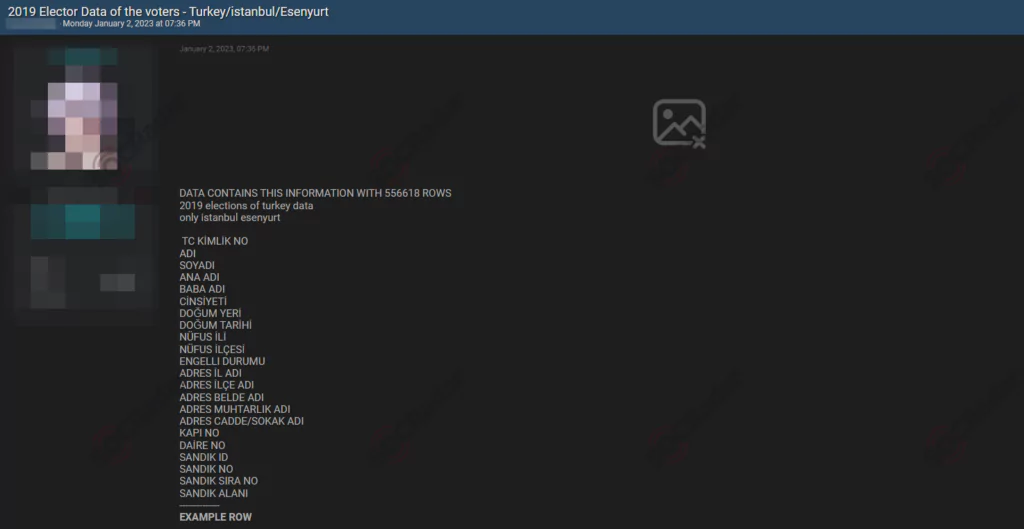
Many sophisticated cyber attacks on elections are carried out by threat actors ranging from nation-state groups to cybercriminals. Phishing attacks pose a significant threat to the integrity of the electoral process.
Using social engineering tactics to deceive and manipulate voters, threat actors can potentially influence election results, spread disinformation, or gain financial benefit by taking advantage of voter excitement in the election process. Many high-profile incidents, such as the DNC attack in 2016 or identity theft e-mails in the upcoming Turkish elections, show that political campaigns, electoral organizations, and voters are the primary targets of phishing attempts.
Election officials must take strict security measures and educate election workers and volunteers about the risks of phishing attacks. This situation includes conducting regular security training and awareness programs, implementing two-factor authentication and other access controls, and regularly monitoring network activity for signs of suspicious behavior.
It is also critical for voters to remain aware of protecting their personal information from phishing attacks. Avoid clicking on strange links or opening suspicious attachments, validating the legitimacy of e-mails and websites before providing personal information, and reporting suspicious activity to election officials or law enforcement are all examples of precautions.
All stakeholders must take a proactive approach to cybersecurity, being aware of potential attackers and attacks to build a secure election environment.



































