
Dark Web Profile: MuddyWater APT Group
[Update] April 19, 2023: Added subheading: “MuddyWater Uses SimpleHelp Tool for Persistence on Victim Devices”
Security concerns grow day by day with the rise of cyberattacks. Among the threats, cyber espionage is one of the prominent activities. It can be used to get a hold of sensitive or classified data that may be intellectual property, government, or trade secrets. The threat actors’ goals might be financial gain, reputational harm, political interests, or cyberwarfare. Today, we’ll review a high-profile cyber espionage group MuddyWater.
Who is MuddyWater?
Stuxnet was a big hit on Iran’s nuclear program in 2010. Iran took that as a wake-up call and began investing in and improving its cyberwarfare capabilities. In 2011, Iranian threat actors began to be involved in sophisticated attacks. One area they focused on is cyber espionage campaigns. The first major campaign was observed in 2012, called the Madi campaign.

MuddyWater, also known as Static Kitten, UNC3313, or MERCURY, is an Iranian state-sponsored APT group. According to the FBI and other US and UK-based agencies, they operate as a subordinate element of the Iranian Ministry of Intelligence and Security (MOIS). It is believed that they have been active since late 2017 and have been in close contact with MOIS since 2018.
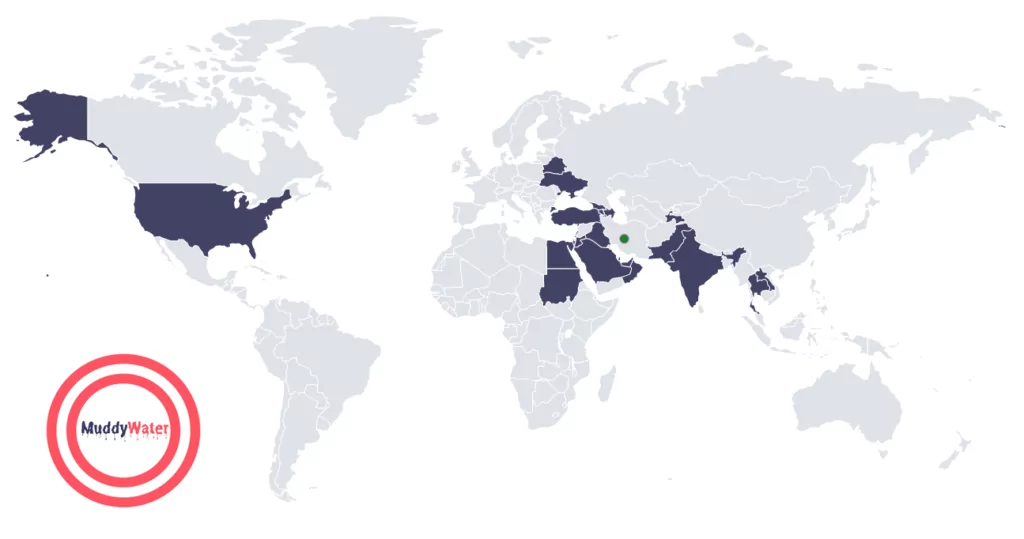
MuddyWater was observed to be conducting malicious activities across Europe, Asia, Africa, and North America. However, their main focus primarily resides on the middle east, per other Iranian threat actors. They are targeting private and government organizations listed below:
- Defense
- Education
- Energy
- Financial Services
- Government and administration agencies
- Healthcare
- High-Tech
- International Organizations
- Media
They are primarily conducting cyber espionage activities and intellectual property (IP) theft attacks, but on some occasions, they have deployed ransomware on the targets. However, it is believed they deployed ransomware to cover their tracks.
How does MuddyWater Attack?
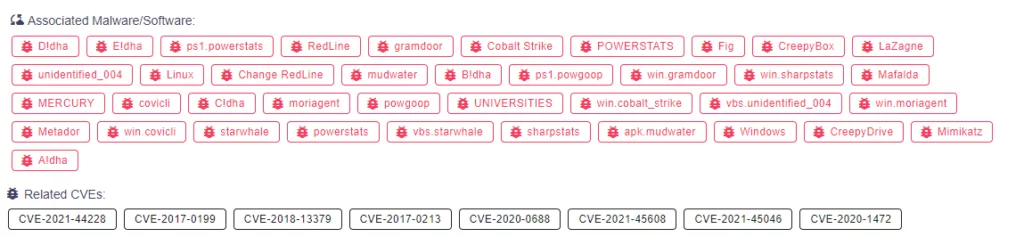
MuddyWater’s arsenal is vast. The group exploits various known vulnerabilities and uses a wide range of tools.
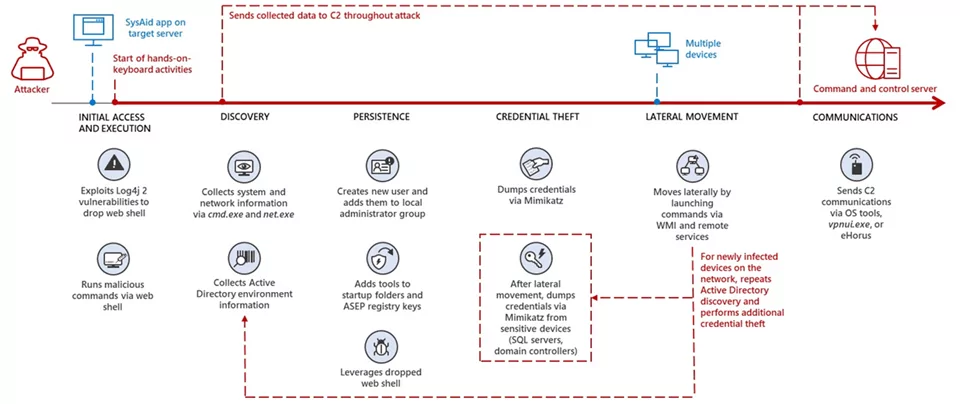
For initial access, the group commonly leverages spear-phishing and tries to trick the victims into opening malicious documents hosted in commercial file-sharing services. After obtaining initial access, they usually drop web shell and gain local administrator access on the infected machine. On the compromised machine, they use tools such as Mimikatz to dump credentials. To broaden the compromise, they laterally move by leveraging in-built or deployed tools within the network.
MuddyWater generally uses DNS to communicate with their C2 servers while using tools such as PowerShell, vpnui[.]exe (a unique version of Ligolo), and remote monitoring software such as ScreenConnect, Remote Utilities, and eHorus.
The figure below shows an instance of the MuddyWater attack chain observed by Microsoft.
Which Tools and Vulnerabilities MuddyWater Use?
- PowGoop DLL Loader: PowGoop malware is a malicious DLL loader. It disguises itself as a legitimate Google Update executable.
- Small Sieve: Small Sieve is a simple Python backdoor used to distribute Nullsoft Scriptable Install System (NSIS) installer.
- Canopy: Canopy is a spyware. It collects the victim’s username, computer name, and IP address and sends it to the MuddyWater group. Canopy malware is also known as Starwhale malware.
- Mori: Mori is a backdoor that uses Domain Name System tunneling to communicate with the group’s C2 infrastructure.
- POWERSTATS: POWERSTATS is a backdoor that runs PowerShell scripts to maintain persistent access on the victim systems.
- BugSleep: BugSleep is a backdoor intended to execute commands from threat actors and facilitate file transfers between the compromised machine and the C&C server. It is currently under development, with the threat actors actively enhancing its features and resolving issues.
MuddyWater Uses SimpleHelp Tool for Persistence on Victim Devices
Researchers found that MuddyWater is using the legitimate SimpleHelp remote support tool to establish persistence on victim devices. While using remote access tools is not a new method for MuddyWater, the SimpleHelp tool expands its toolkit.
The tool is not compromised, but the threat actors have discovered a way to download it from the official website to use in their attacks. The SimpleHelp client can be run as a system service on victim devices, enabling attackers to access it anytime, including after a reboot.
Furthermore, SimpleHelp operators can execute commands on the victim’s device, including those that require administrator privileges. They can secretly gain control of the target device using the “Connect in Terminal Mode” command.
The initial method of infection is currently unknown but is suspected to be phishing. Researchers also discovered novel infrastructure and publicly known IP addresses used by the attackers during its latest analysis of MuddyWater. Security experts advise companies to use corporate email security tools to prevent email as an attack vector.
Who Did MuddyWater Target in Their Campaigns?
MuddyWater’s targets are mostly the neighbors of Iran in the middle east region. If we analyze the graphic below, we can see that Turkey, Israel, Iraq, UAE, and Pakistan are among the top targets of MuddyWater. Observations may show that MuddyWater acts according to the political interests of the Iranian state through the connection of MOIS. So, countries in which Iran has political interests should be aware of MuddyWater’s cyber espionage campaigns.
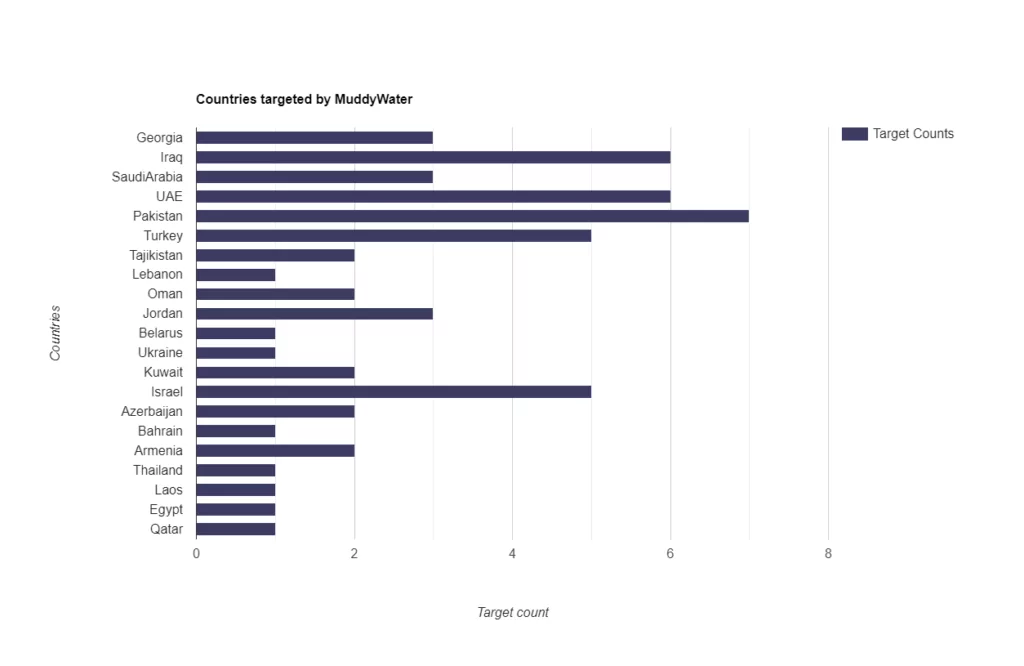
Motivations Behind MuddWater’s Attacks in the Last 2 Years
In September 2020, a series of agreements called the Abraham Accords were signed between Israel, United Arab Emirates, and Bahrain. These countries signed these agreements intending to normalize diplomatic relations in the region. The US brokered the agreements, a major diplomatic breakthrough in the Middle East.
The Abraham Accords can be an improvement in the region from a neutral point of view, but some may feel uneasy about these agreements. In particular, Iran may have felt concerned about the Abraham Accords because they could lead to closer ties between Israel and other countries in the region, potentially undermining Iran’s influence.
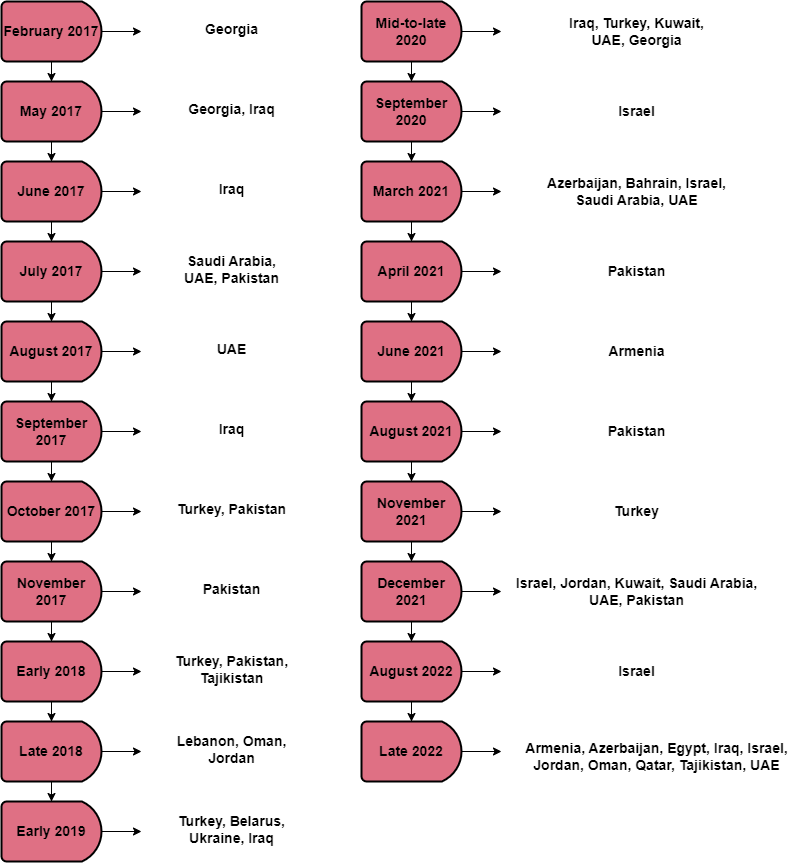
With these developments in mind, we may deduce that the cyber-espionage activities carried out by MuddyWater between September 2020 and March 2021 were a reaction to these agreements. MuddyWater, as far as known, primarily conducted campaigns in the middle east and its neighboring regions in late 2020 and early 2021.
- September 2020 – Operation Quicksand – Israel: According to ClearSky, MuddyWater targeted many prominent Israeli organizations. In this specific campaign, security researchers observed that the threat actor used a variant of Shamoon to encrypt data. However, it is believed that the intent of using Shamoon was not to deploy ransomware but to disrupt operations.
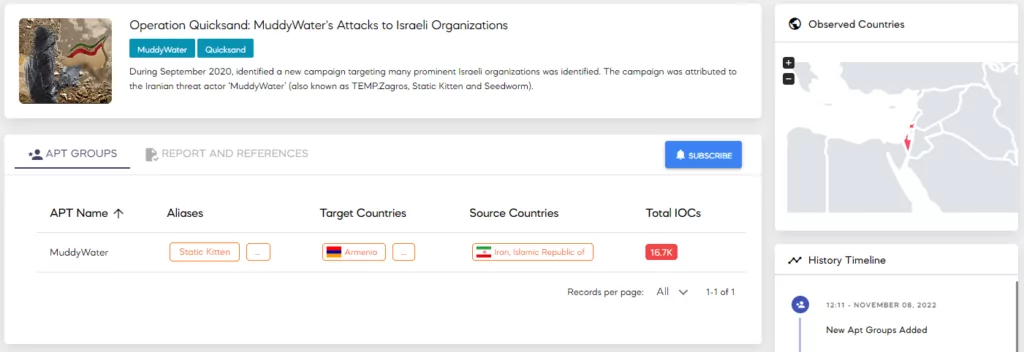
- March 2021 – Earth Vetala Campaign: According to Trend Micro, Azerbaijan, Bahrain, Israel, Saudi Arabia, and the United Arab Emirates were the targets of the campaign. Government agencies, academia, and tourism were some of the targeted sectors.
Latest Attacks of the Threat Actor
In January 2022, cybersecurity researchers reported that MuddyWater targeted Turkish private organizations and governmental agencies. They used multiple malicious PDFs and MS Office documents during the campaign. With the spear phishing technique, the threat actors tried to convince the victims that the documents were from the Turkish Health and Internal Affairs Ministries.
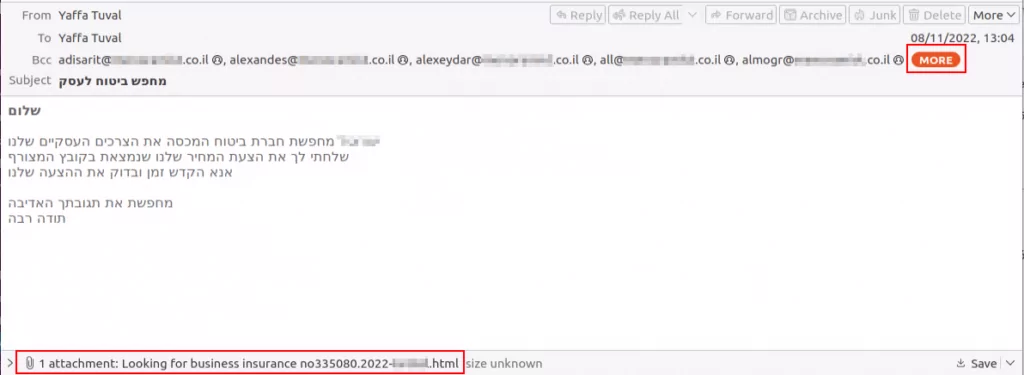
In another incident on December 2022, Deep Instinct reported that MuddyWater, conducted malicious activities, again using spear phishing through emails. Israeli insurance companies were the targets of the attacks. As an evolving threat actor, they added a new tool for remote access, Syncro, to their arsenal.
Conclusion
Observations of MuddyWater’s cyber espionage activities can lead to a conclusion that they act according to Iran’s political strategies through MOIS. Whether it is because of the political implications, or another reason, Israel and Turkey seem to be significant targets for the MuddyWater.
If you are an organization residing in the middle east, there might be a possibility of being a target of MuddyWater. What can you do to defend against them? Excluding the technical mitigations, keeping up with the political climate of the middle east region might give a heads-up if the tension rises. On the technical side, MuddyWater evolves with each attack they perform, but they still bear similar techniques. You can apply the following recommendations per your needs.
Security Recommendations Against MuddyWater
- MuddyWater leverages spear phishing. Provide necessary training to your employees for security awareness.
- Gain visibility into external-facing digital assets with an Attack Surface Management solution.
- Regularly apply security patches and software updates.
- Apply the least privilege principle across the network, especially to critical systems and services
- Secure domain controllers (DC) using best practices.
- Enable multifactor authentication (MFA) to prevent lateral movement.
- Refer to IOCs and take necessary actions toward mitigation.
SOCRadar’s Attack Surface Management provides visibility into external-facing digital assets. SOCRadar has a predictive, preventive, and proactive approach toward security at its core. With SOCRadar’s Attack Surface Management, security teams can track which CVEs are present in the environment. Knowing which CVEs are present in the organization can give the organization an advantage in defending against MuddyWater.
Most threat actors specializing in cyber espionage widely leverage spear phishing, just as MuddyWater does. If you receive any suspicious email, you can use free SOC Tools on SOCRadar Labs to analyze it.
MITRE ATT&CK Techniques
| Techniques | ID | |
| Reconnaissance | ||
| Gather Victim Identity Information: Email Addresses | T1589.002 | |
| Resource Development | ||
| Acquire Infrastructure: Web Services | T1583.006 | |
| Obtain Capabilities: Tool | T1588.002 | |
| Initial Access | ||
| Phishing: Spearphishing Attachment | T1566.001 | |
| Phishing: Spearphishing Link | T1566.002 | |
| Execution | ||
| Windows Management Instrumentation | T1047 | |
| Command and Scripting Interpreter: PowerShell | T1059.001 | |
| Command and Scripting Interpreter: Windows Command Shell | 1.059.003 | |
| Command and Scripting Interpreter: Visual Basic | T1059.005 | |
| Command and Scripting Interpreter: Python | T1059.006 | |
| Command and Scripting Interpreter: JavaScript | T1059.007 | |
| Exploitation for Client Execution | T1203 | |
| User Execution: Malicious Link | T1204.001 | |
| User Execution: Malicious File | T1204.002 | |
| Inter-Process Communication: Component Object Model | T1559.001 | |
| Inter-Process Communication: Dynamic Data Exchange | T1559.002 | |
| Persistence | ||
| Scheduled Task/Job: Scheduled Task | T1053.005 | |
| Office Application Startup: Office Template Macros | T1137.001 | |
| Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 | |
| Privilege Escalation | ||
| Abuse Elevation Control Mechanism: Bypass User Account Control | T1548.002 | |
| Credentials from Password Stores | T1555 | |
| Credentials from Web Browsers | T1555.003 | |
| Defense Evasion | ||
| Obfuscated Files or Information | T1027 | |
| Steganography | T1027.003 | |
| Compile After Delivery | T1027.004 | |
| Masquerading: Match Legitimate Name or Location | T1036.005 | |
| Deobfuscate/Decode Files or Information | T1140 | |
| Signed Binary Proxy Execution: CMSTP | T1218.003 | |
| Signed Binary Proxy Execution: Mshta | T1218.005 | |
| Signed Binary Proxy Execution: Rundll32 | T1218.011 | |
| Execution Guardrails | T1480 | |
| Impair Defenses: Disable or Modify Tools | T1562.001 | |
| Credential Access | ||
| OS Credential Dumping: LSASS Memory | T1003.001 | |
| OS Credential Dumping: LSA Secrets | T1003.004 | |
| OS Credential Dumping: Cached Domain Credentials | T1003.005 | |
| Unsecured Credentials: Credentials In Files | T1552.001 | |
| Discovery | ||
| System Network Configuration Discovery | T1016 | |
| System Owner/User Discovery | T1033 | |
| System Network Connections Discovery | T1049 | |
| Process Discovery | T1057 | |
| System Information Discovery | T1082 | |
| File and Directory Discovery | T1083 | |
| Account Discovery: Domain Account | T1087.002 | |
| Software Discovery | T1518 | |
| Security Software Discovery | T1518.001 | |
| Collection | ||
| Screen Capture | T1113 | |
| Archive Collected Data: Archive via Utility | T1560.001 | |
| Command and Control | ||
| Application Layer Protocol: Web Protocols | T1071.001 | |
| Proxy: External Proxy | T1090.002 | |
| Web Service: Bidirectional Communication | T1102.002 | |
| Multi-Stage Channels | T1104 | |
| Ingress Tool Transfer | T1105 | |
| Data Encoding: Standard Encoding | T1132.001 | |
| Data Encoding: Non-Standard Encoding | T1132.002 | |
| Remote Access Software | T1219 | |
| Exfiltration | ||
| Exfiltration Over C2 Channel | T1041 | |
Appendix:
Appendix 1: IOCs of PowGoop
goopdate[.]dll
- MD5: a27655d14b0aabec8db70ae08a623317
- SHA-1: 7649c554e87f6ea21ba86bb26ea39521d5d18151
- SHA-256: 2c92da2721466bfbdaff7fedd9f3e8334b688a88ee54d7cab491e1a9df41258f
- File type: Win32 DLL
- File size: 88.50 KB (90624 bytes)
vcruntime140[.]dll
- MD5: cec48bcdedebc962ce45b63e201c0624
- SHA-1: 81f46998c92427032378e5dead48bdfc9128b225
- SHA-256: dd7ee54b12a55bcc67da4ceaed6e636b7bd30d4db6f6c594e9510e1e605ade92
- File type: Win32 DLL
- File size: 91.50 KB (93696 bytes)
IOCs
- 104.208.16[.]94:443 (TCP)
- 20.42.65[.]92:443 (TCP)
- 20.42.73[.]29:443 (TCP)
- libpcre2-8-0[.]dll
- MD5: 860f5c2345e8f5c268c9746337ade8b7
- SHA-1: 6c55d3acdc2d8d331f0d13024f736bc28ef5a7e1
- SHA-256: 9d50fcb2c4df4c502db0cac84bef96c2a36d33ef98c454165808ecace4dd2051
- File type: Win32 DLL
- File size: 94.50 KB (96768 bytes)
IOCs
- 20.189.173[.]20:443 (TCP)
- 20.189.173[.]21:443 (TCP)
- 20.42.73[.]29:443 (TCP)
Appendix 2: IOCs of Small Sieve
gram_app[.]exe
- MD5: 15fa3b32539d7453a9a85958b77d4c95
- SHA-1: 11d594f3b3cf8525682f6214acb7b7782056d282
- SHA-256: b75208393fa17c0bcbc1a07857686b8c0d7e0471d00a167a07fd0d52e1fc9054
- File type: Win32 EXE
- File size: 16.21 MB (16999598 bytes)
IOCs
- 13.107.4[.]50:80 (TCP)
- 149.154[.]167.220:443 (TCP)
- 192.168.0[.]15:137 (UDP)
- 23.216.147[.]64:443 (TCP)
- 23.216.147[.]76:443 (TCP)
- a83f:8110:0:0:1400:1400:2800[:]3800:53 (UDP)
index[.]exe
- MD5: 5763530f25ed0ec08fb26a30c04009f1
- SHA-1: 2a6ddf89a8366a262b56a251b00aafaed5321992
- SHA-256: bf090cf7078414c9e157da7002ca727f06053b39fa4e377f9a0050f2af37d3a2
- File type: Win32 EXE
- File size: 16.46 MB (17263089 bytes)
IOCs
- 13.107.4[.]50:80 (TCP)
- 192.168.0[.]1:137 (UDP)
- 192.168.0[.]25:137 (UDP)
- 20.99.132[.]105:443 (TCP)
- 209.197.3[.]8:80 (TCP)
- 23.216.147[.]64:443 (TCP)
- a83f:8110:0:0:7f00:0:0[:]0:53 (UDP)
- a83f:8110:492a:d801:d1df:1328:492a[:]d801:53 (UDP)
- a83f:8110:5067:d801:beac:bf78:cce1[:]d301:53 (UDP)
Appendix 3: IOCs of Canopy
Cooperation terms[.]xls
- MD5: b0ab12a5a4c232c902cdeba421872c37
- SHA-1: a8e7659942cc19f422678181ee23297efa55fa09
- SHA-256: 026868713d60e6790f41dc7046deb4e6795825faa903113d2f22b644f0d21141
- File type: MS Excel Spreadsheet
- File size: 247.00 KB (252928 bytes)
IOCs
- 88.119.170[.]124:80 (TCP)
ZaibCb15Ak[.]xls
- MD5: 6cef87a6ffb254bfeb61372d24e1970a
- SHA-1: e21d95b648944ad2287c6bc01fcc12b05530e455
- SHA-256: 4b2862a1665a62706f88304406b071a5c9a6b3093daadc073e174ac6d493f26c
- File type: MS Excel Spreadsheet
- File size: 249.00 KB (254976 bytes)
IOCs
- 5.199.133[.]149:80 (TCP)
Appendix 4:IOCs of Mori
FML[.]dll
- MD5: 0431445d6d6e5802c207c8bc6a6402ea
- SHA-1: 3765c1ad8a1d936aad88255aef5d6d4ce24f94e8
- SHA-256: 3098dd53da40947a82e59265a47059e69b2925bc49c679e6555d102d1c6cbbc8
- File type: Win32 DLL
- File size: 200.65 MB (210397496 bytes)
Appendix 5:IOCs of POWERSTATS
LisfonService[.]exe
- MD5: f5dee1f9cd47dc7bae468da9732c862e
- SHA-1: 5273ee897e67fc01ee5fef08c37400cb4ee15958
- SHA-256: 6f8226d890350943a9ef4cc81598e0e953d8ba9746694c0b7e3d99e418701b39
- File type: Win32 EXE
- File size: 119.00 KB (121856 bytes)
TestService[.]exe
- MD5: e75443a5e825f69c75380b6dc76c6b50
- SHA-1: 142b5753c608c65e702e41b52abdeb96cb2f9294
- SHA-256: c514c3f293f0cb4c23662a5ab962b158cb97580b03a22b82e21fa3b26d64809c
- File type: Win32 EXE
- File size: 92.50 KB (94720 bytes)
IOCs
- 13.107.4.50:80 (TCP)
- a83f:8110:e0:ffff:e0:ffff:e0[:]ffff:53 (UDP)




































