
Major Cyber Attacks Targeting the Automotive Industry
Due to its growing connectivity and perceived vulnerabilities, the Automotive Industry is increasingly targeted by cyberattacks, like data breaches and ransomware. As we all know, cyber threats can cause significant disruptions in production, operations, and supply chains, leading to car failures, data breaches, and intellectual property theft.
The Automotive Industry has been continuously threatened by sophisticated cyber attacks, ranging from data breaches to ransomware attacks targeting supply chain entities. Each incident showcases the evolving tactics and sophistication of threat actors keen on exploiting vulnerabilities within this sector. But before checking the major attacks since 2023, let’s look at the cybercrime landscape targeting the Automotive Industry.
When we look at channels that can also be used for cybercrime, such as Dark Web channels, hacker forums, and Telegram, we can talk about at least 735 significant incidents that directly target the Automotive Industry since last year.
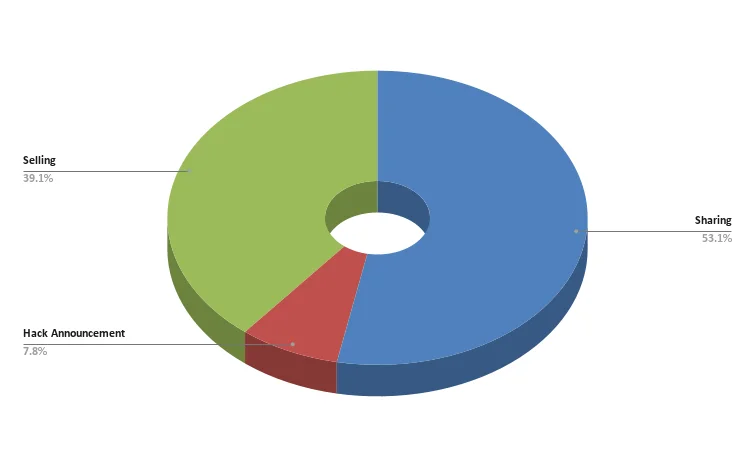
Types of the posts targeting Automotive Industry (2023-2024 H1)
Especially in hacker forums, we see that most of this data allegedly obtained from the Automotive Industry is shared. However, this table does not reflect the exact distribution. Situations such as sharing the same data over and over on different platforms and re-sharing in combo lists inflate the “Sharing” section. The other significant type is “Selling”. A small portion of the posts in this area are initial access sales, but most of them are data leaks.
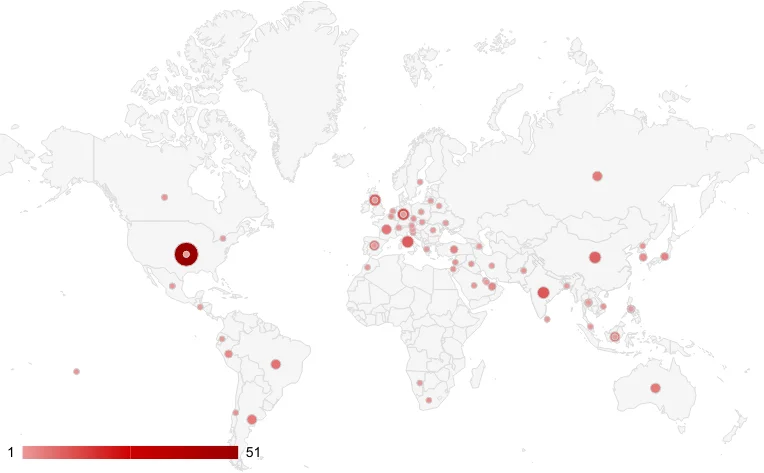
Density map for Automotive Industry (2023-2024 H1)
When we look at production-oriented sectors, we can witness a relatively equal distribution similar to the table above. Thus, upon close inspection, it is evident that the US is the primary target. Again, almost all European countries and the UK are frequently targeted countries. India and China appear to be popular targets in the eastern hemisphere.
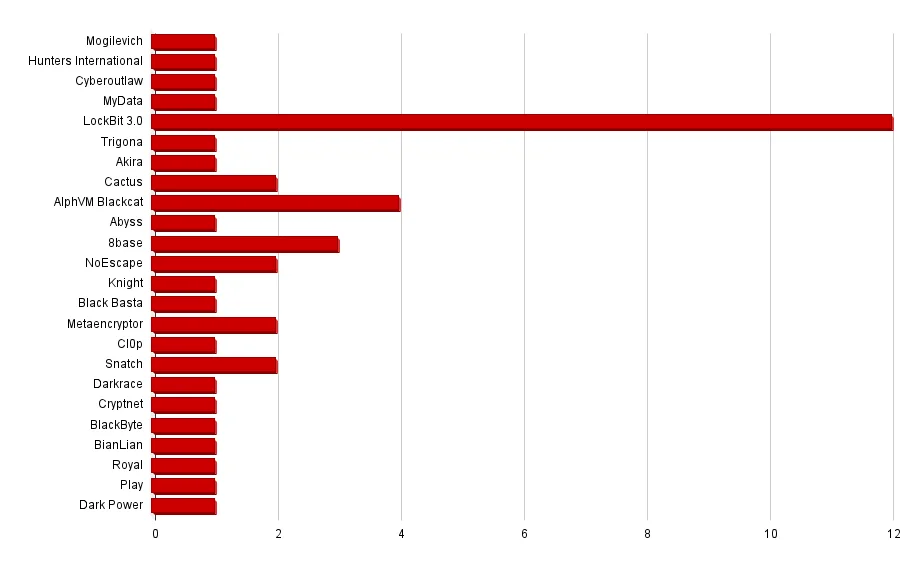
Ransomware groups targeting Automotive Industry (2023-2024 H1)
Various groups are targeting this industry, but we can see that LockBit, the most notorious group of recent years, is the leading actor. Although LockBit has now been greatly disrupted, the Automotive Industry is a suitable target for ransomware groups, especially those attacking with the LockBit 3.0 leaked builder (eg. Brain Cipher).
Although there are a total of 42 attacks that directly affect the Automotive Industry, the threat landscape becomes much wider when we think about it in the context of Supply Chain. Now let’s look at the major attacks between 2023 to 2024 H1 and their implications.
Ransomware Actors targeting Cars.com
The threat actor IntelBroker, previously known as Endurance Ransomware, and a group of hackers formerly evaluated as CyberNiggers, have been targeting various sectors, including the Automotive Industry. IntelBroker claimed to have leaked internal data from Cars.com, a car shopping site with around 40 million visitors. This leaked data reportedly includes information that could facilitate supply chain attacks.
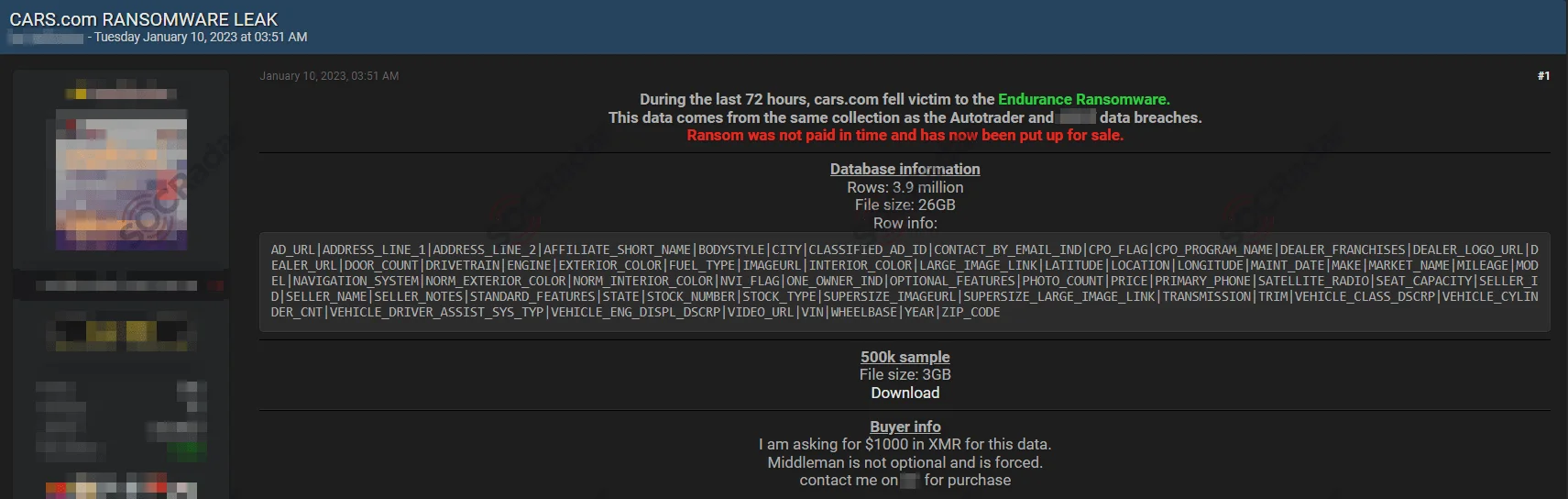
Alleged leak by Endurance Ransomware
This data allegedly contains information that could lead to supply chain attacks like affiliate names, customer information etc. The data resulting from a ransomware attack can also include invoice files and this can be used for various frauds.
11 Million Customer Relation Data from China
A database containing sensitive information from a Chinese vehicle dealer was sold on the dark web for $8,000. The data included names, addresses, phone numbers, and identity card numbers of over 11 million individuals, exposing them to financial fraud and identity theft. This breach highlighted the need for robust cybersecurity measures in the Automotive Industry.
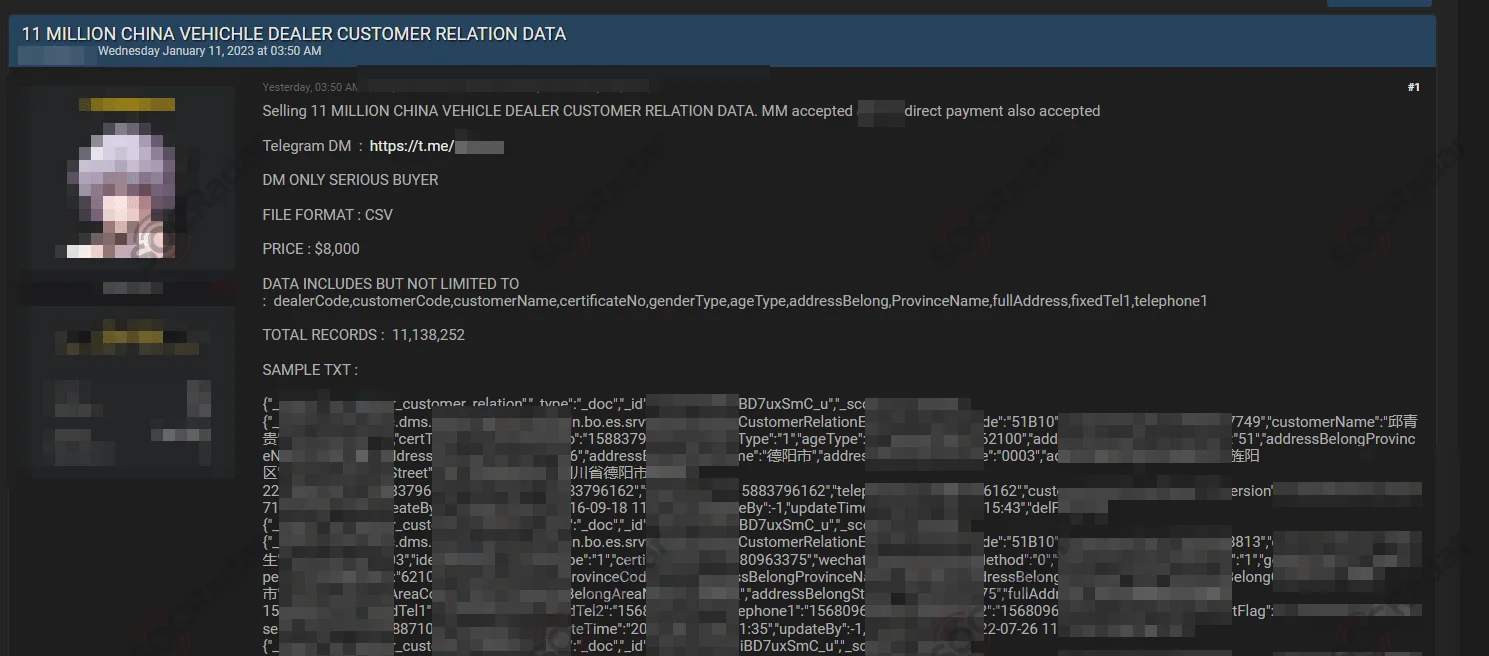
Sale post for the data
This incident highlighted the Automotive Industry’s vulnerability to supply chain attacks due to its extensive network of suppliers, manufacturers, and service providers. Data breaches in this sector can cause significant disruptions, affecting both vehicle production and the delivery of essential parts and services. Compromised sensitive data can be exploited to infiltrate various points of the supply chain, leading to widespread operational and financial damage. Implementing robust cybersecurity measures is essential to protect against these vulnerabilities and ensure the integrity of the automotive supply chain.
Vauxhall Motors Leaks
An alleged database containing 2.6 million Vauxhall Motors customer records was stolen and leaked on a hacker forum. The alleged data included phone numbers, call durations, and CRM details, leading to potential phishing attacks and identity theft.
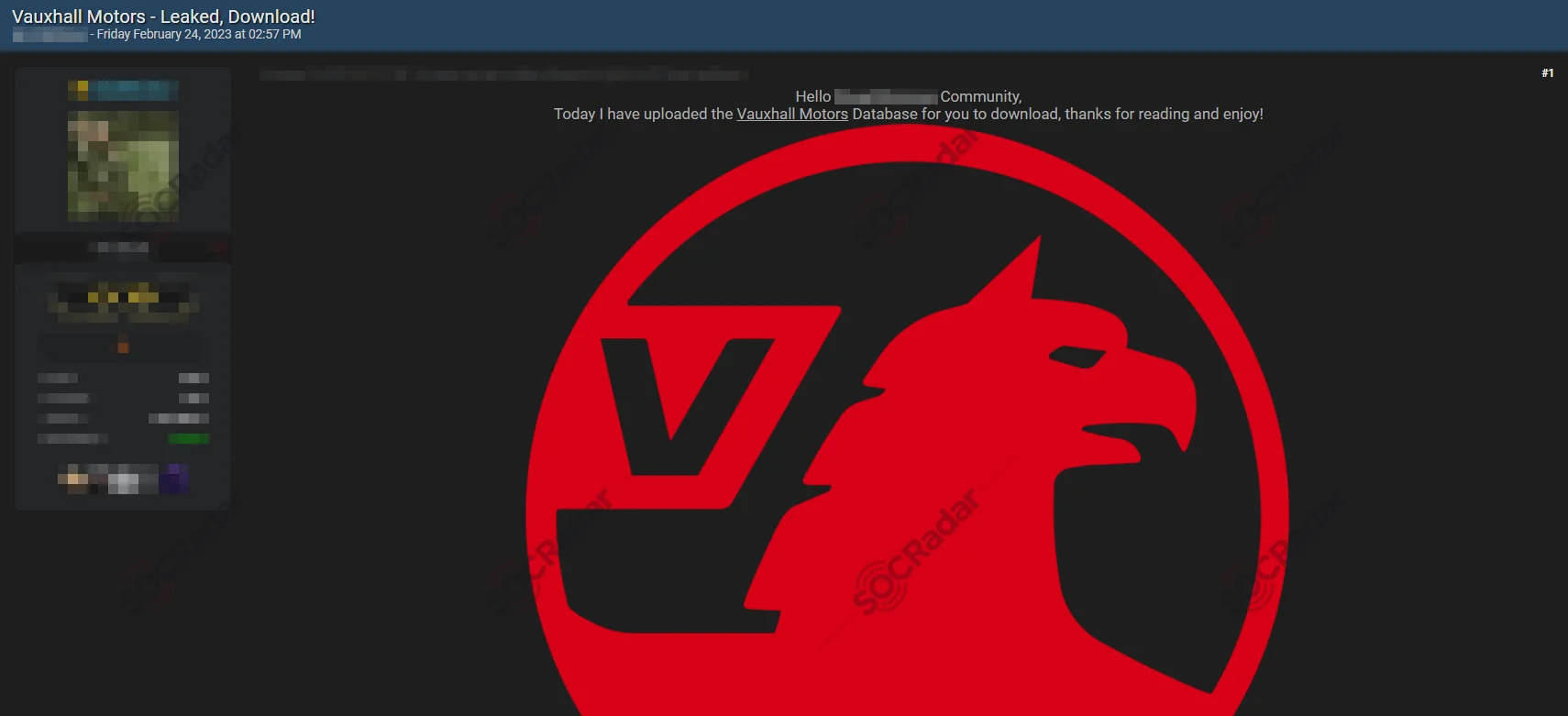
First Vauxhall leak post
However, this was not the only breach involving Vauxhall. Allegedly, call logs of 5.5 million employees and customers of Vauxhall Motors were exposed on a well-known underground forum by the cybercriminal IntelBroker again. The leaked database included data such as UserIDs, SiteIDs, call dates, and phone numbers. This type of information, when obtained by malicious actors, is highly valuable for executing phishing and smishing campaigns.
Ferrari Leaks
Alleged breaches of similar scale and content have continued to surface on various hacker forums since 2022, often referred to as the Ferrari Database leaks. The Ransom EXX group was the first to publish internal documents that year. Despite this, the sharing leaks persisted. The purported database included internal confidential documents, datasheets, repair manuals, and other sensitive information.
One of the posts that resharing 2022 data in 2023
Around 2023 similar alleged data leaks from Opel, Renault, Mercedes-Benz and Audi are also shared in the dark web. For further information refer to SOCRadar Platform, Dark Web News.
Access Sales to Vehicle Dealers and Authorized Services
Of course, not all threats come from database leaks and ransomware attacks. Below are two examples of access sales, though many similar instances can impact the Automotive Industry. Access sales, which may later lead to ransomware attacks, are sold for thousands of dollars.
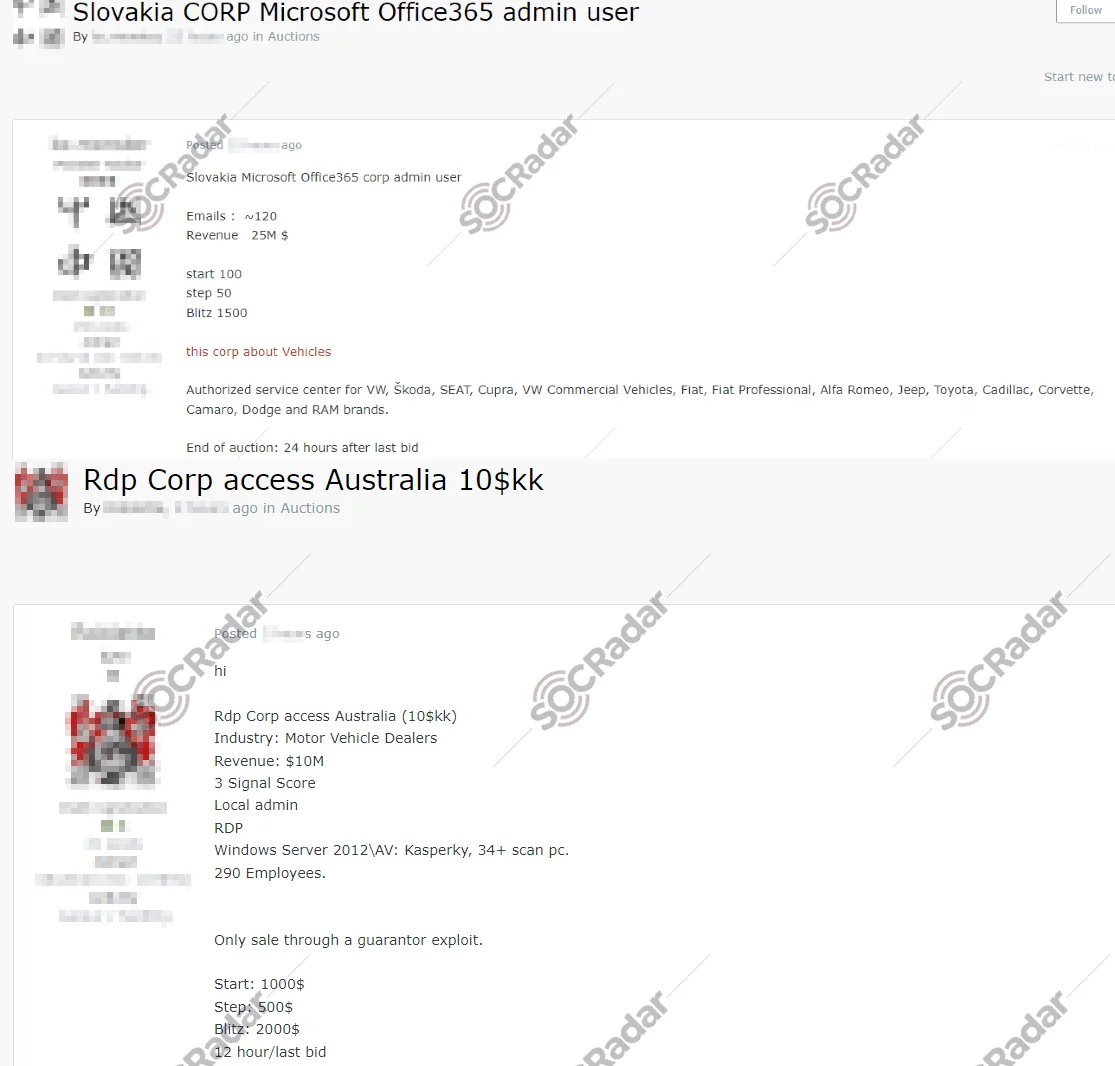
Access sales in a hacker forum with similar dates
In 2023 June, SOCRadar identified two unauthorized network access sales on a hacker forum. One sale pertained to an Australian motor vehicle dealership with $10M in revenue and 290 employees. The access included local admin RDP on Windows Server 2012 with Kaspersky antivirus, starting at $1000 with a blitz price of $2000, ending 12 hours after the last bid. The other sale involved a Slovakian automotive company with $25M in revenue, offering Microsoft Office 365 corporate admin user access for around 120 emails, starting at $100 with a blitz price of $1500, ending 24 hours after the last bid.
Hacktivist Attacks to Automotive Industry
On November 15, 2023, SOCRadar dark web analysts reported that Team UCC had conducted a cyber attack on Clean Fleet Report, a website focused on the clean fleet industry. The attack appeared targeted, raising concerns about data breaches, reputational damage, and supply chain impacts. Suggested mitigation strategies included strengthening cybersecurity measures, monitoring dark web activity, educating employees, and considering cyber insurance.
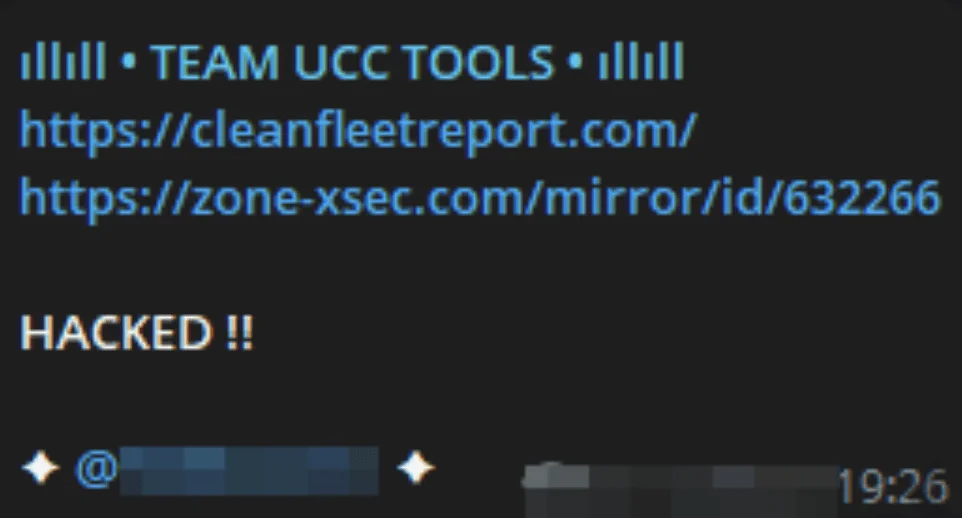
Team UCC’s Telegram post
Around the same time, Phoenix Reborn announced a DDoS attack on Automotive and Aviation giants.
Of course, although the individual attacks carried out by these hacktivist groups are far from being major, they can still cause great risks, especially when many hacktivist groups working in the same direction act together. These types of groups are mostly organized via Telegram today and prefer relatively simple attack vectors such as DDoS attacks and Defacement.
Iranian Threat Actors Targeting Toyota Israel
With the onset of the Israel-Hamas conflict last year, hacktivism surged significantly, with many hacktivist groups taking action based on their allegiances. Iranian-origin groups, in particular, were highly active and vocal. One of their notable targets was Toyota Israel.
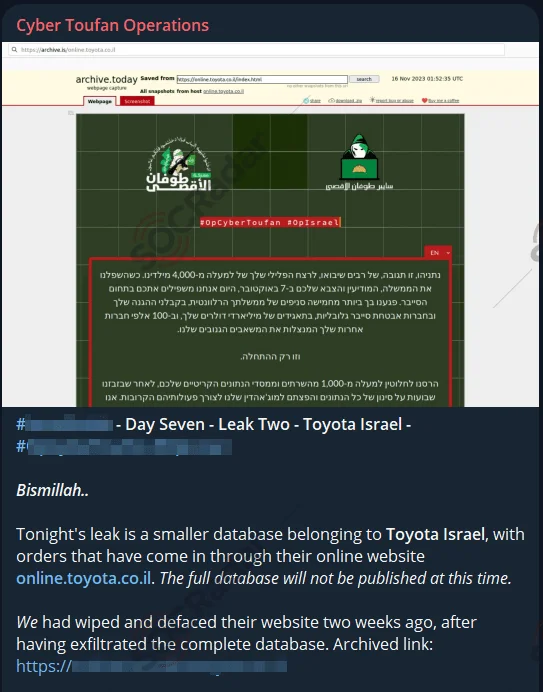
Cyber Toufan Al Aqsa’s Telegram post about the incident
In a Telegram channel monitored by SOCRadar, Cyber Toufan Operations announced a database leak for Toyota Israel. They claimed to have wiped and defaced Toyota Israel’s website two weeks prior after exfiltrating the complete database, although they only released part of the database.
One another example of this kind of political attack was targeting Australia. On December 2, 2023, the Stucx Team announced a cyberattack on Oz Car Parts, an Australian automotive parts company. In other words, not only Israeli-based companies or Israeli branches were hacked, but they could choose victims from any country they think is pro-Israeli.
Continuous Threat to Formula Races and The FIA
Recently, The International Automobile Federation (FIA) experienced a phishing attack that compromised two email accounts, raising concerns about potential data breaches involving sensitive information. The FIA swiftly cut off unauthorized access and informed relevant data protection authorities. They emphasized their commitment to data security and implemented additional measures to prevent future attacks. Detailed information about the attack was shared with employees, and partner organizations were advised to bolster their cybersecurity protocols.
However, this attack was neither the first nor the only one; it is a known fact that cyber threats increase during major events such as the Olympics and Summits. During Formula 1 races, both the FIA and the automobile companies involved in the organization are exposed to intense cyber attacks.
Thus, we have come to the end of the article we prepared to highlight different attack vectors and vulnerabilities from hundreds of attacks, and we were able to reveal the threat landscape facing the Automotive Industry.
Conclusion
The Automotive Industry faces a relentless onslaught of cyber threats, highlighted by numerous incidents of data breaches, ransomware attacks, and unauthorized access across its global supply chain. From sophisticated ransomware groups like LockBit targeting critical infrastructure to the leaking of sensitive customer data from major companies like Cars.com and Vauxhall Motors, the industry’s vulnerabilities are exposed.
These attacks not only disrupt production and operations but also compromise sensitive information, posing significant risks of financial fraud and identity theft. As cybercriminals increasingly target interconnected networks within the automotive sector, robust cybersecurity measures are imperative to safeguard against future breaches and ensure the integrity of the supply chain.
Supply Chain Intelligence by SOCRadar
It is evident that the Automotive Industry is one of the sectors that is highly susceptible to Supply Chain Attacks. Gartner’s projection that 45% of global organizations will face software supply chain attacks by 2025, securing supply chains has become paramount. These statistics underscore a critical vulnerability: attackers frequently exploit weaknesses in less secure, interconnected suppliers to evade robust corporate defenses. This necessitates organizations to extend their security measures beyond internal perimeters, focusing on comprehensive assessments of vendors’ security postures.
SOCRadar’s Supply Chain Intelligence emerges as a comprehensive solution tailored to combat these challenges. Adopting a proactive approach, SOCRadar intelligence isn’t just about surveillance but also about preemptively understanding and mitigating real-world threats. It features advanced capabilities such as automated supply chain mapping, real-time threat updates, and tiered risk categorization.
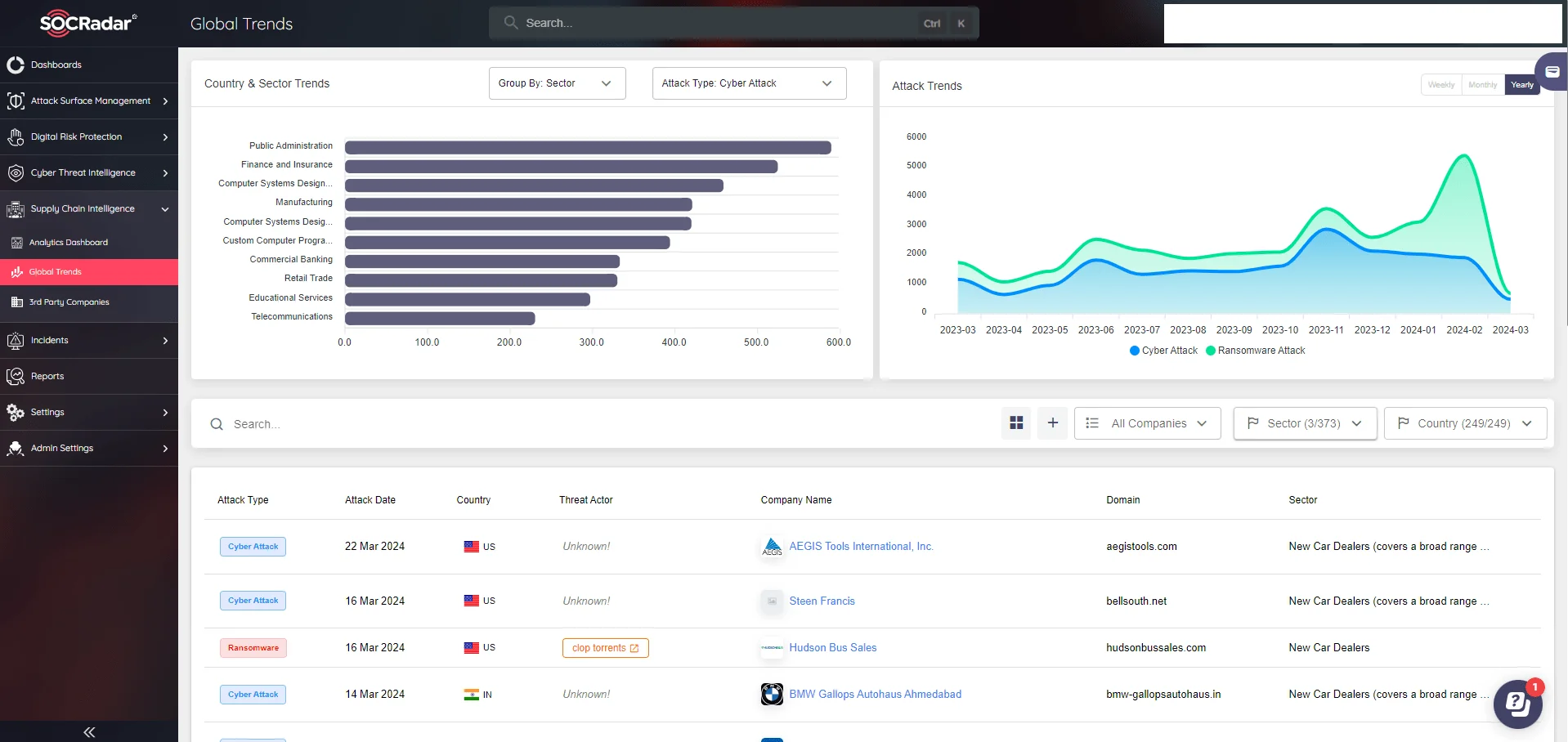
SOCRadar’s Supply Chain Intelligence module
SOCRadar excels by automating supply chain mapping, delivering crucial recommendations, and offering The Analytics Board for streamlined monitoring and detailed trend analysis. Additionally, it includes a sophisticated alerting system to promptly notify organizations of critical events and potential risks. Detailed security reports leverage advanced scoring mechanisms like Cyber Exposure Level and Popularity Score to provide comprehensive insights into third-party vendors’ cybersecurity readiness and operational integrity.
In the face of escalating supply chain attacks posing existential threats to automotive companies, SOCRadar proves indispensable. It empowers organizations to anticipate disruptions and ensure uninterrupted operations in an environment where supply chain vulnerabilities are not merely potential risks but expected challenges. By leveraging SOCRadar, Automotive Industry stakeholders can effectively fortify themselves against the sophisticated and increasingly indirect tactics employed by modern cyber adversaries.






































