
Top 10 VPN Vulnerabilities (2022 – H1 2024)
In the landscape of cybersecurity, VPN security has become a critical concern for organizations worldwide. Compared to 2022, there was a staggering 47% increase in VPN vulnerabilities discovered in 2023, highlighting a significant rise in the risks associated with these essential tools.
VPNs are fundamental for securing remote access to organizational networks, making them indispensable for businesses, government entities, and individuals working remotely. They provide encrypted channels that safeguard data transmissions, ensuring that sensitive information remains protected from unauthorized access. However, the increasing number of vulnerabilities presents a severe threat to VPN security.

AI illustration about VPN vulnerabilities by DALL-E
Vulnerabilities in VPN utilities are particularly dangerous for several reasons. These devices often expose access points in otherwise secure networks, and there is typically little evidence of a breach, making it difficult to detect intrusions promptly. Attackers exploiting these vulnerabilities can infiltrate a VPN and spend months mapping out a target network, gathering valuable information, and potentially deploying ransomware or initiating extortion attempts.
Given these risks, organizations must prioritize VPN security. Paying close attention to vulnerabilities and ensuring that VPN systems are updated and monitored regularly can help mitigate these threats and protect against potential breaches.
In this blog post, we will explore the top 10 VPN vulnerabilities that have significantly impacted the cybersecurity landscape from 2022 through the first half of 2024. We will also list effective mitigation strategies to protect against these threats.
VPN Vulnerabilities Saw 47% Increase
The year 2023 witnessed a troubling surge in VPN vulnerabilities. A total of 133 VPN vulnerabilities were reported, marking a 47% increase compared to the average over the previous two years. This surge underscores the escalating threat landscape surrounding VPN technologies.
According to Top10VPN, 2023 saw 133 VPN vulnerabilities, up from 93 in 2022. Among these, seven were known exploited vulnerabilities, as per CISA, compared to nine in the previous year. The most affected vendors included Zyxel, Cisco, and SoftEtherVPN, highlighting a trend towards targeting prominent VPN providers.
The attack vectors for these vulnerabilities were primarily network-based, accounting for 70% (93 incidents), followed by local (22%, 29 incidents) and adjacent network attacks (8%, 11 incidents). In terms of severity, notably, 15 vulnerabilities were classified as critical (11%), while 75 were deemed high severity (57%).
Common Types of VPN Vulnerabilities and Attacks
VPN technologies face numerous threats that exploit various vulnerabilities. Compromised VPNs can serve as entry points for broader network infiltration, allowing attackers to move laterally across an organization’s systems.
Using stolen credentials, they can alter configuration settings or access internal infrastructures. Unauthorized VPN connections can grant attackers a root shell, providing extensive control over the system.
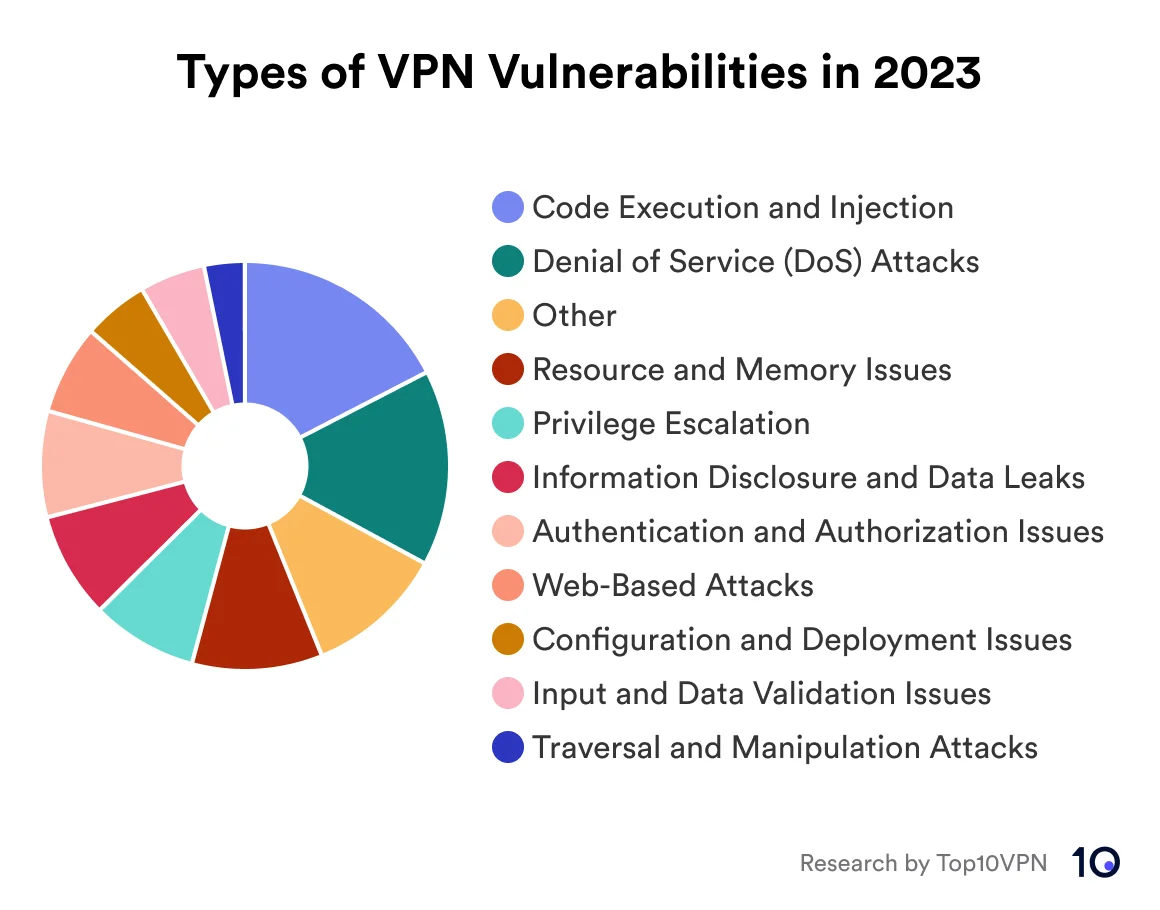
Types of VPN Vulnerabilities in 2023 (Top10VPN)
Common attack types identified by Top10VPN, in only the past year, include:
- Code Execution and Injection – 27
- Denial of Service (DoS) Attacks – 24
- Privilege Escalation – 13
- Information Disclosure and Data Leaks – 13
- Authentication and Authorization Issues – 13
- Resource and Memory Issues – 16
- Web-Based Attacks – 11
- Configuration and Deployment Issues – 8
- Traversal and Manipulation Attacks – 5
- Library and Dependency Attacks – 2
- Input and Data Validation Issues – 8
- Middle-Man Attacks – 5
- Brute Force and IDOR Attacks – 3
- Credential and Access Attacks – 2
- Logic and Design Flaws – 2
- Session and Authentication Management – 1
- Access Control Issues – 1
- Cryptographic Issues – 1
These attacks can lead to data overwriting, malicious code execution, and system disruptions.
Effective mitigation requires regular updates, comprehensive monitoring, and robust authentication mechanisms to safeguard VPN infrastructure against these evolving threats.
What Are the Top 10 VPN Vulnerabilities?
Here are the top 10 VPN vulnerabilities that trended between 2022 and the first half of 2024. These vulnerabilities are not ranked in any specific order but have been selected based on their wide recognition and their SOCRadar Vulnerability Risk Score (SVRS).
The SVRS score reflects a CVE’s popularity by considering sources such as social media, news, code repositories, and the dark web. It also accounts for the vulnerability’s connections to threat actors or malware campaigns.
1. CVE-2024-24919 (Information Disclosure in Check Point Quantum Gateway/Spark Gateway/CloudGuard Network Remote Access VPN)
The vulnerability identified as CVE-2024-24919, with a high-severity CVSS score of 8.6, can result in significant unauthorized information disclosure.
This flaw affects Check Point Quantum Security Gateways, impacting their VPN functionalities, including IPSec VPN, Remote Access VPN, and Mobile Access.
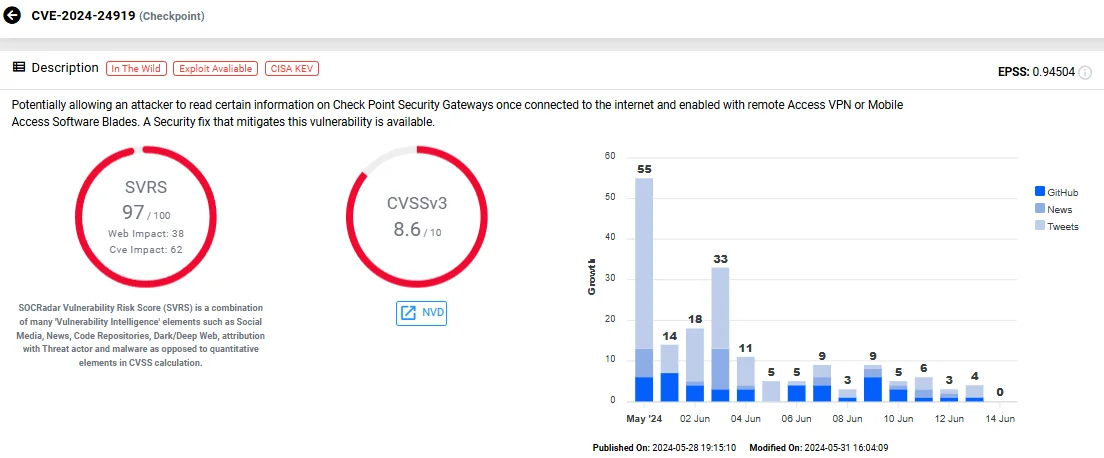
Vulnerability card of CVE-2024-24919 (SOCRadar Vulnerability Intelligence)
This zero-day vulnerability was actively exploited before patches were available. Attackers exploited CVE-2024-24919 starting April 30, targeting VPN devices to steal Active Directory credentials. These credentials facilitated lateral movement within networks, primarily exploiting outdated local accounts that relied solely on password authentication. Such accounts are particularly vulnerable and not recommended.
CVE-2024-24919 has also sparked concern due to being a vulnerability affecting a remote access VPN technology, entering the list of vulnerabilities within this category. The timeline below shows remote VPN vulnerabilities affecting many other products, such as those from Ivanti, Cisco, Fortinet, Palo Alto, and Citrix.
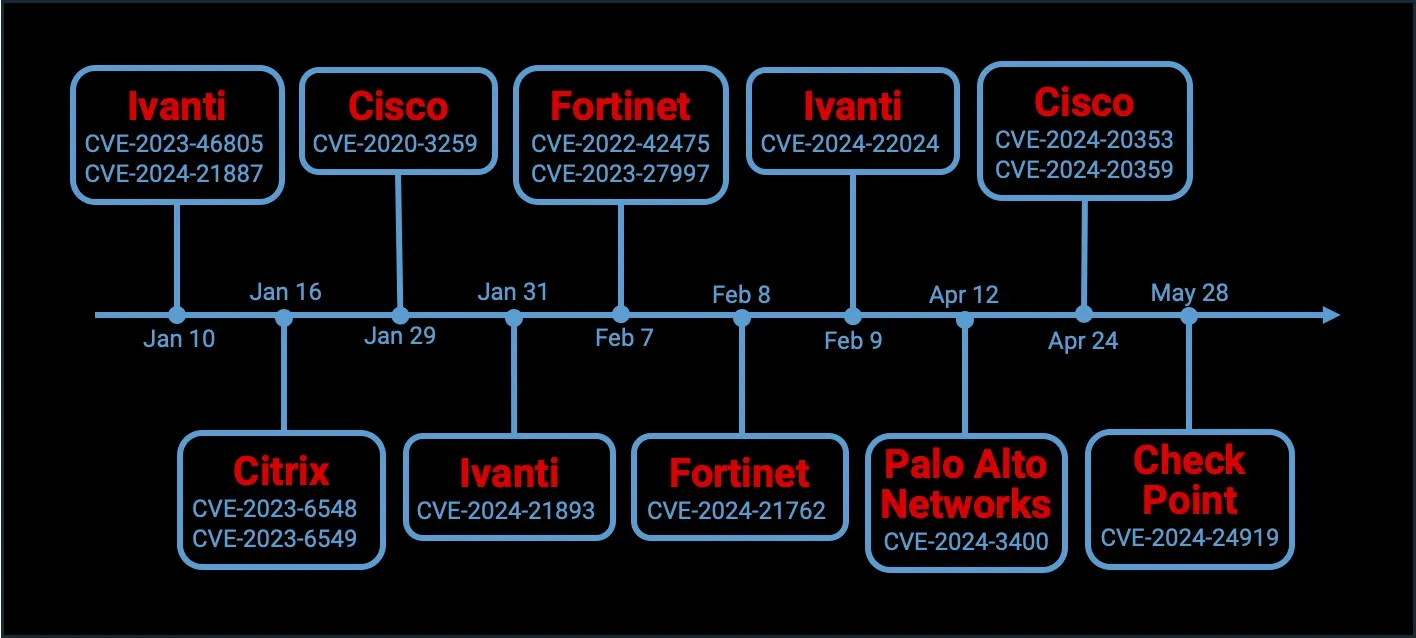
Remote access VPN vulnerabilities (Hackmageddon)
You can find more information on these vulnerabilities on SOCRadar blog:
- Attackers Exploit Ivanti Connect Secure Zero-Day Vulnerabilities to Deploy Webshells (CVE-2023-46805, CVE-2024-21887)
- Zero-Day Vulnerabilities in Citrix Netscaler ADC and Gateway: CVE-2023-6548, CVE-2023-6549
- Fortinet Released Patch for FortiOS SSL-VPN RCE Vulnerability CVE-2022-42475
- Fortinet Rolls Out Patches for Critical RCE Vulnerability in SSL VPN Devices (CVE-2023-27997)
- Vulnerability in Ivanti Connect Secure, Policy Secure, and Neurons for ZTA Exploited (CVE-2024-21893)
- RCEs in FortiOS SSL VPN, Latest Ivanti Flaw Possibly Exploited (CVE-2024-21762, CVE-2024-22024)
- Critical OS Command Injection Vulnerability in Palo Alto’s GlobalProtect Gateway: CVE-2024-3400
- New in CISA KEV: Check Point VPN Zero-Day CVE-2024-24919
2. CVE-2024-21762 (Out-of-Bounds Write in Fortinet FortiOS up to 7.4.2 SSL-VPN)
The vulnerability tracked as CVE-2024-21762, with a critical CVSS score of 9.6, is an out-of-bounds write issue in FortiOS. This flaw enables unauthenticated attackers to execute Remote Code Execution (RCE) through maliciously crafted requests.
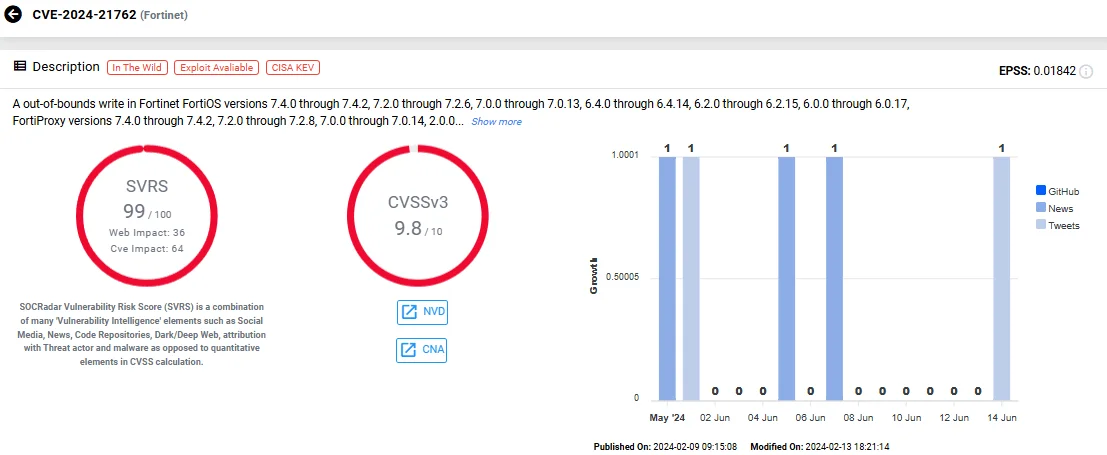
Vulnerability card of CVE-2024-21762 (SOCRadar Vulnerability Intelligence)
Soon after its disclosure, the Cybersecurity and Infrastructure Security Agency (CISA) added the FortiOS vulnerability CVE-2024-21762 to its Known Exploited Vulnerabilities (KEV) Catalog, citing active exploitation. Additionally, Fortinet revealed that Chinese state-sponsored threat actors, known as Volt Typhoon, targeted FortiOS vulnerabilities to deploy custom malware. CISA also issued guidance to mitigate the impact of this threat group.
3. CVE-2024-3400 (Command Injection in Palo Alto Networks PAN-OS GlobalProtect)
Identified as CVE-2024-3400, this vulnerability is classified as a critical OS Command Injection issue with a severity rating of 10. It exists within the GlobalProtect feature of Palo Alto Networks’ PAN-OS software and allows an unauthenticated attacker to execute arbitrary code with root privileges on the firewall.
CVE-2024-3400 affects specific versions of PAN-OS, including PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1. However, products like Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability.
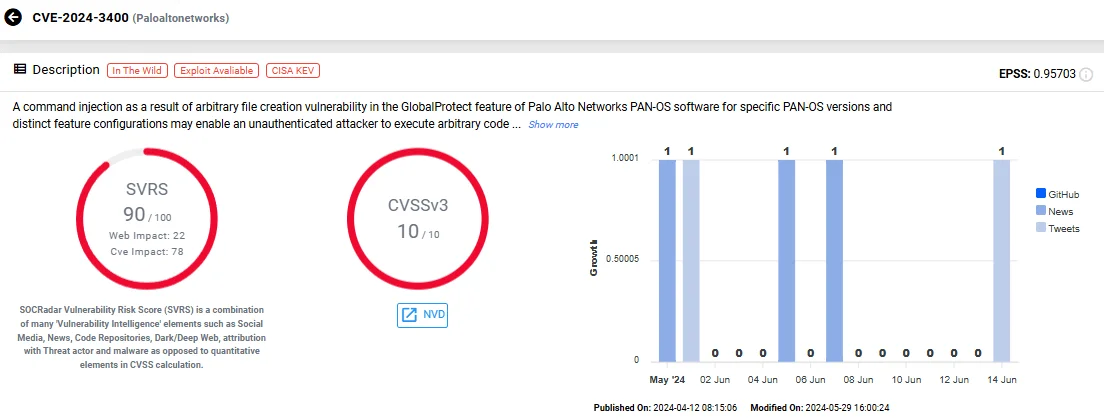
Vulnerability card of CVE-2024-3400 (SOCRadar Vulnerability Intelligence)
Palo Alto Networks has acknowledged a limited number of attacks exploiting this vulnerability, after disclosure. Detailed analysis revealed the sophistication and intent of the attackers, identified as the state-sponsored threat actor UTA0218. These attackers exploited the vulnerability to initiate a reverse shell, enabling them to download malicious tools, exfiltrate sensitive configuration data, and move laterally within the affected networks.
4. CVE-2023-27997 (Heap-Based Overflow in Fortinet FortiOS/FortiProxy FortiGate SSL-VPN)
The vulnerability identified as CVE-2023-27997 is a critical heap-based overflow issue affecting Fortinet FortiOS and FortiProxy SSL VPN products. This flaw poses a significant risk, allowing pre-authentication Remote Code Execution (RCE) attacks.
Fortinet issued firmware updates to address this undisclosed vulnerability in their SSL VPN products. Although the release notes did not explicitly mention the vulnerability, security professionals and administrators inferred that the updates silently fixed it.
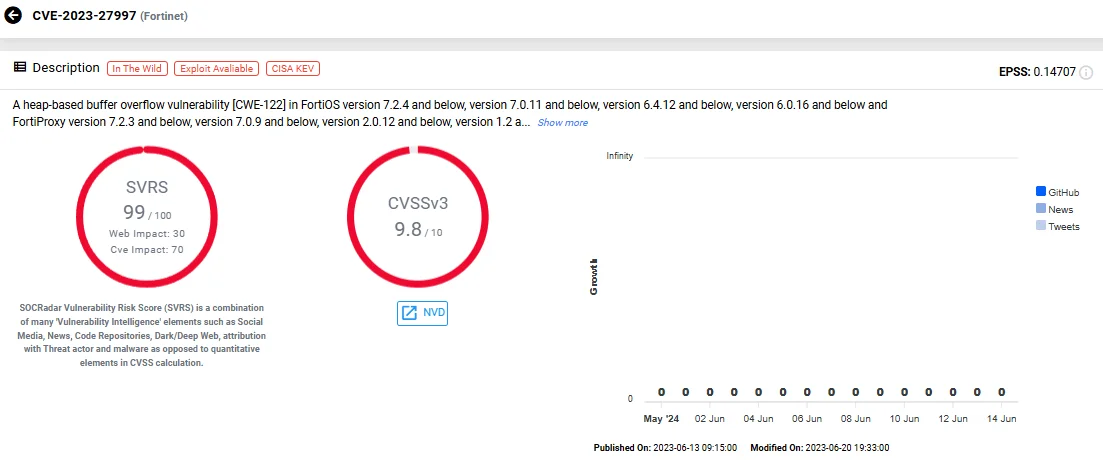
Vulnerability card of CVE-2023-27997 (SOCRadar Vulnerability Intelligence)
According to the French cybersecurity firm Olympe Cyberdefense, the RCE vulnerability could allow threat actors to interfere with the VPN even if Multi-Factor Authentication (MFA) is enabled. The firm indicated that all versions are likely affected, pending confirmation with the release of CVE details on June 13, 2023.
Fortinet devices, being some of the most popular firewall and VPN products, have become attractive targets for attackers. Recent years have seen increased attention on Fortinet vulnerabilities from the cyber threat landscape.
5. CVE-2022-42475 (Heap-Based Overflow in FortiOS FortiOS SSL-VPN/FortiProxy SSL-VPN Requests)
CVE-2022-42475 is a critical heap-based overflow vulnerability affecting Fortinet’s FortiOS and FortiProxy technologies. It allows unauthenticated attackers to execute arbitrary code on vulnerable systems.
Fortinet patched this flaw in November 2022 and made it public in December, urging users to update their devices due to active exploitation by threat actors.
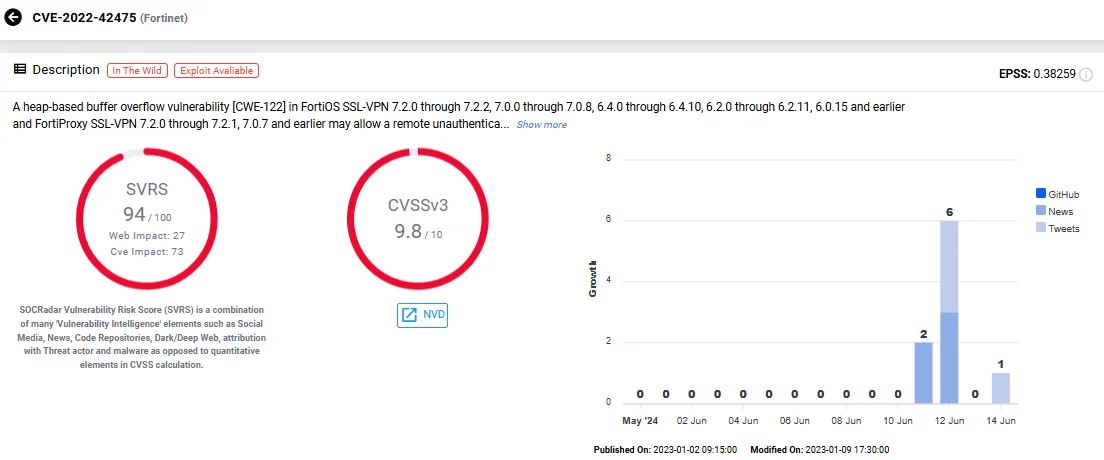
Vulnerability card of CVE-2022-42475 (SOCRadar Vulnerability Intelligence)
Researchers later identified a sophisticated malware named BoldMove, created to exploit Fortinet’s FortiGate firewalls. This malware, developed by a Chinese state-sponsored threat actor, was designed for cyberespionage against government-related targets.
The BoldMove malware was associated with the exploitation of CVE-2022-42475 in January 2023, highlighting the severity and impact of this security flaw.
SOCRadar’s easy-to-use Vulnerability Intelligence dashboard offers a view of global vulnerability trends, helping you gain valuable insights into which vulnerabilities are being exploited by threat actors and better prioritize patching.
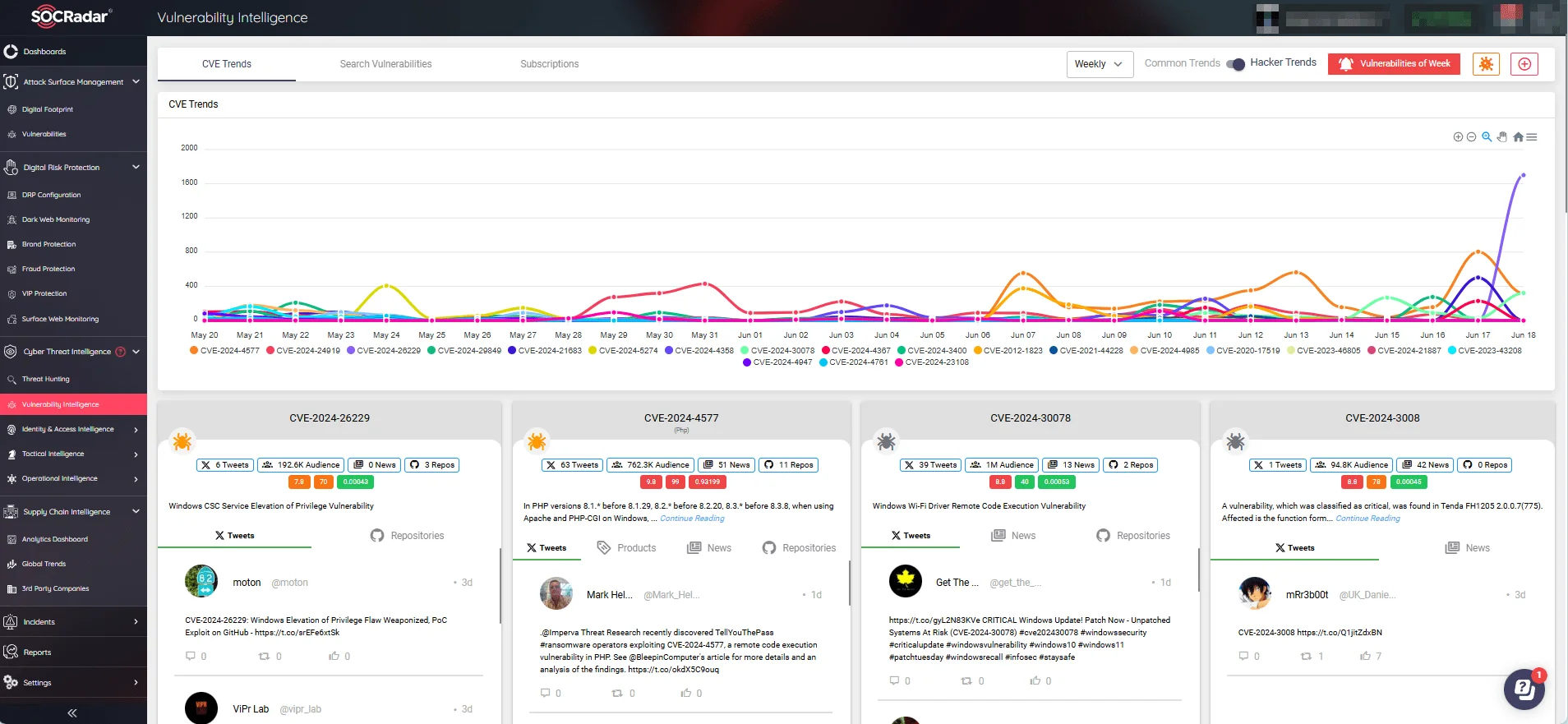
SOCRadar’s Vulnerability Intelligence: Latest CVE and exploitation trends
6. CVE-2023-46805 & CVE-2024-21887 (Improper Authentication & Command Injection in Ivanti Connect Secure/Policy Secure Web)
CVE-2023-46805, along with the CVE-2024-21887 vulnerability, are zero-day vulnerabilities that pose significant risks to Ivanti Connect Secure VPN appliances.
CVE-2023-46805, with a CVSS score of 8.2, allows attackers to bypass authentication checks and access restricted resources. CVE-2024-21887, rated as critical with a CVSS score of 9.1, is a command injection flaw that enables authenticated administrators to execute arbitrary commands via crafted requests.
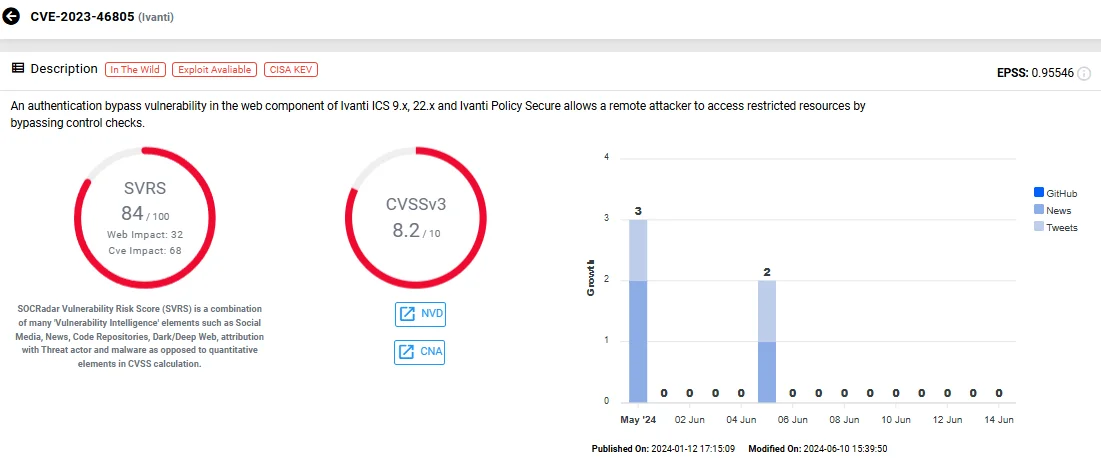
Vulnerability card of CVE-2023-46805 (SOCRadar Vulnerability Intelligence)
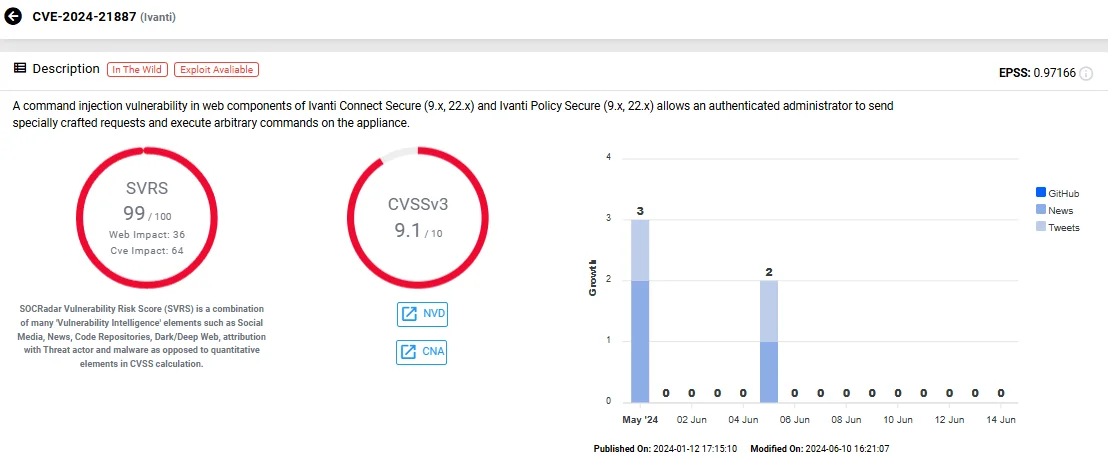
Vulnerability card of CVE-2023-21887 (SOCRadar Vulnerability Intelligence)
In December 2023, researchers identified suspicious activities involving these vulnerabilities. Attackers used these flaws to deploy webshells on internal and external web servers, leading to unauthorized access and control over affected systems.
The exploitation chain allowed attackers to steal configuration data, modify files, and download remote files, facilitating extensive network intrusion.
Ivanti released mitigations for these vulnerabilities and scheduled patches for staggered release. Promptly, CISA added these vulnerabilities to its Known Exploited Vulnerabilities (KEV) Catalog, emphasizing the urgency for federal organizations to patch by January 31, 2024.
7. CVE-2023-28771 (Zyxel USG/USG FLEX/VPN/ATP Error Message OS Command Injection)
In mid-2023, attackers began exploiting a critical vulnerability in Zyxel firewalls, identified as CVE-2023-28771. This vulnerability, with a CVSS score of 9.8, allows unauthorized attackers to execute remote code via unauthenticated command injection. The flaw resides in the Internet Key Exchange (IKE) packet decoder over UDP port 500 on the WAN interface of several Zyxel devices.
The affected devices include various versions of ATP, USG FLEX, VPN, and ZyWALL/USG firewalls. Attackers can exploit this vulnerability by sending specially crafted packets to the targeted device, enabling them to execute arbitrary code with root privileges.
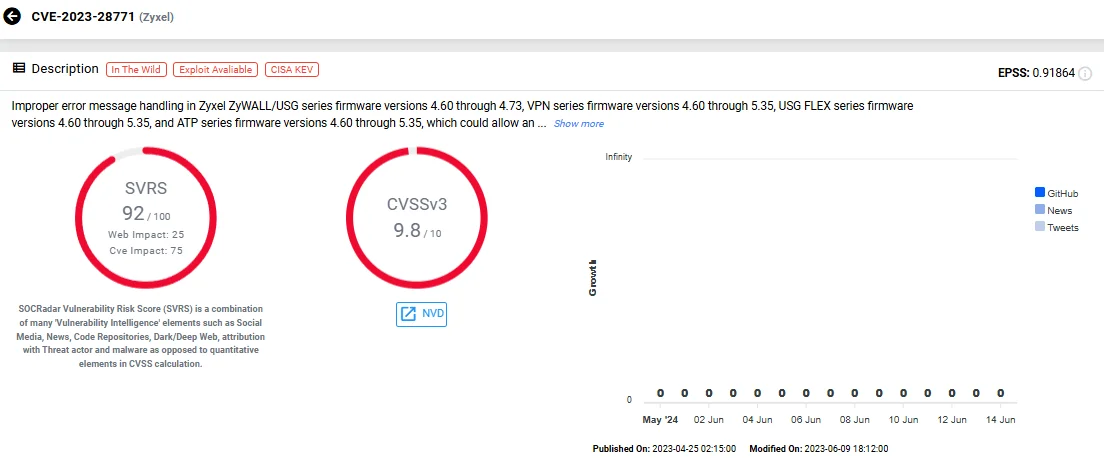
Vulnerability card of CVE-2023-28771 (SOCRadar Vulnerability Intelligence)
Fortinet researchers have observed a significant increase in botnet activity related to this vulnerability, including variants like Dark.IoT, Rapperbot, and the Katana botnet. These botnets leverage the command injection flaw to compromise systems and conduct malicious activities such as Distributed Denial-of-Service (DDoS) attacks.
The Cybersecurity and Infrastructure Security Agency (CISA) has included CVE-2023-28771 in its Known Exploited Vulnerabilities (KEV) Catalog, urging organizations to apply the necessary patches immediately.
8. CVE-2023-20073 (Unrestricted Upload in Cisco RV340/RV340W/RV345/RV345P)
As a critical vulnerability in Cisco’s various VPN routers’ web-based management interface, CVE-2023-20073 allows unauthenticated, remote attackers to upload arbitrary files due to insufficient authorization enforcement.
Exploiting this vulnerability can compromise the integrity of the affected devices, posing a significant security threat.
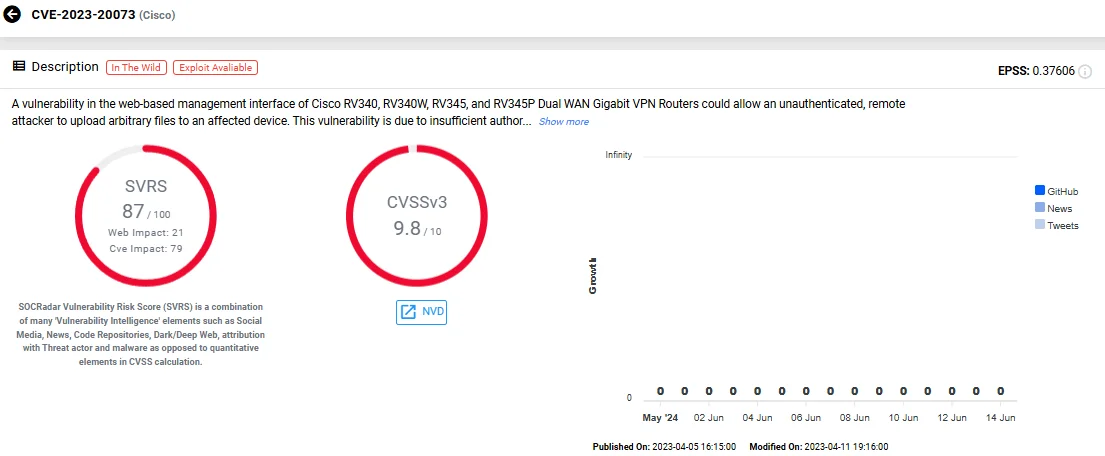
Vulnerability card of CVE-2023-20073 (SOCRadar Vulnerability Intelligence)
9. CVE-2023-46850 (Use After Free in OpenVPN/OpenVPN Access Server)
CVE-2023-46850 is a severe Use-After-Free memory vulnerability. It occurs in OpenVPN versions 2.6.0 to 2.6.6, where the application incorrectly uses a send buffer after it has been freed.
This issue can lead to undefined behavior, allowing attackers to leak sensitive information from the server’s memory or execute remote code by sending network buffers to a remote peer. Configurations using TLS are particularly vulnerable to this exploit, posing a significant risk to affected servers.
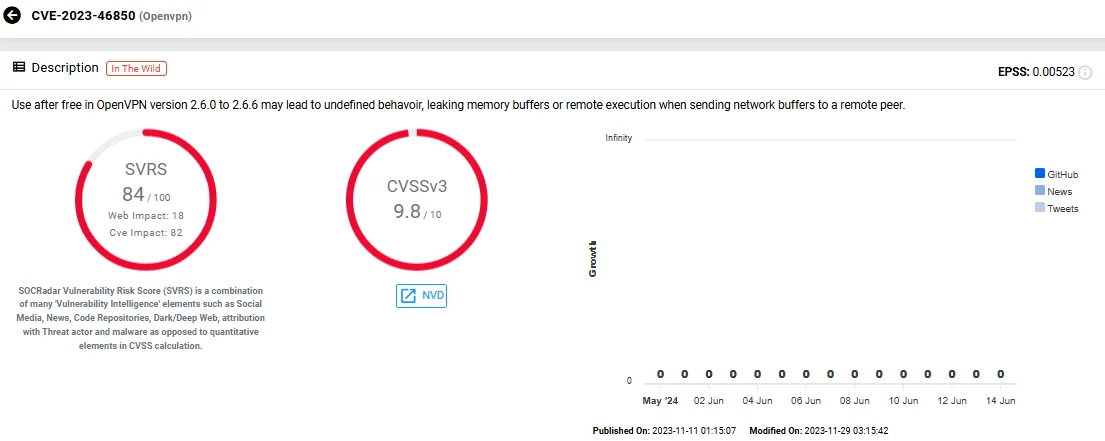
Vulnerability card of CVE-2023-46850 (SOCRadar Vulnerability Intelligence)
Another security vulnerability patched with CVE-2023-46849 is CVE-2023-46849. It is a division by zero crash vulnerability. It affects OpenVPN versions 2.6.0 to 2.6.6 when the –fragment option is enabled in specific configurations, leading to a Denial-of-Service (DoS) condition and potentially exposing sensitive data.
10. CVE-2022-43931 (Out-of-Bounds Write in Synology VPN Plus Server Remote Desktop)
This critical vulnerability in Synology, CVE-2022-43931, affects its router products configured as VPN servers, potentially allowing remote access to stored resources.
Discovered by Synology’s Product Security Incident Response Team (PSIRT), CVE-2022-43931 is an out-of-bounds write issue in the VPN Plus Server’s remote desktop functionality.
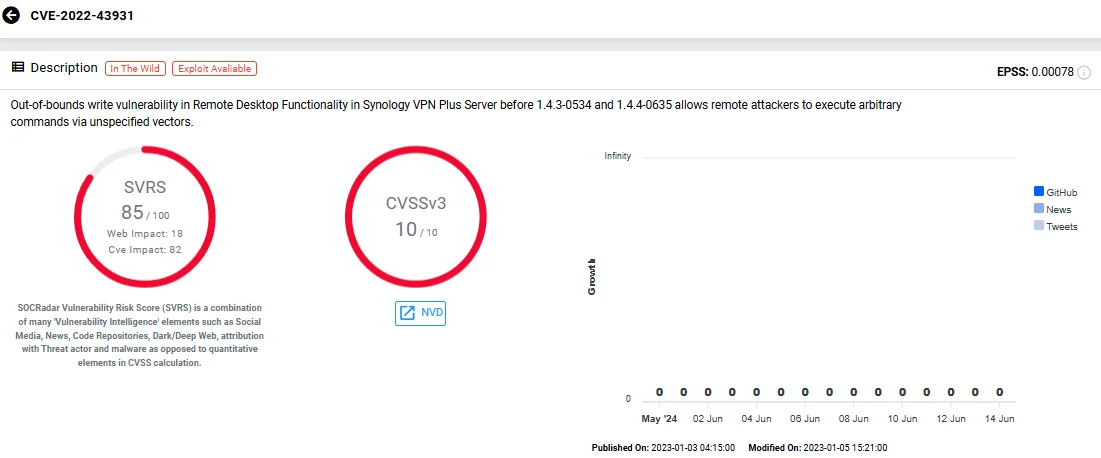
Vulnerability card of CVE-2022-43931 (SOCRadar Vulnerability Intelligence)
If successfully exploited, this security vulnerability could enable remote attackers to execute arbitrary commands on vulnerable Synology VPN Plus Server versions.
With SOCRadar’s Attack Surface Management, you can prioritize patching by precisely targeting your digital footprint. By considering external-facing vulnerable services, SOCRadar provides actionable insights and context to expedite the prioritization process.
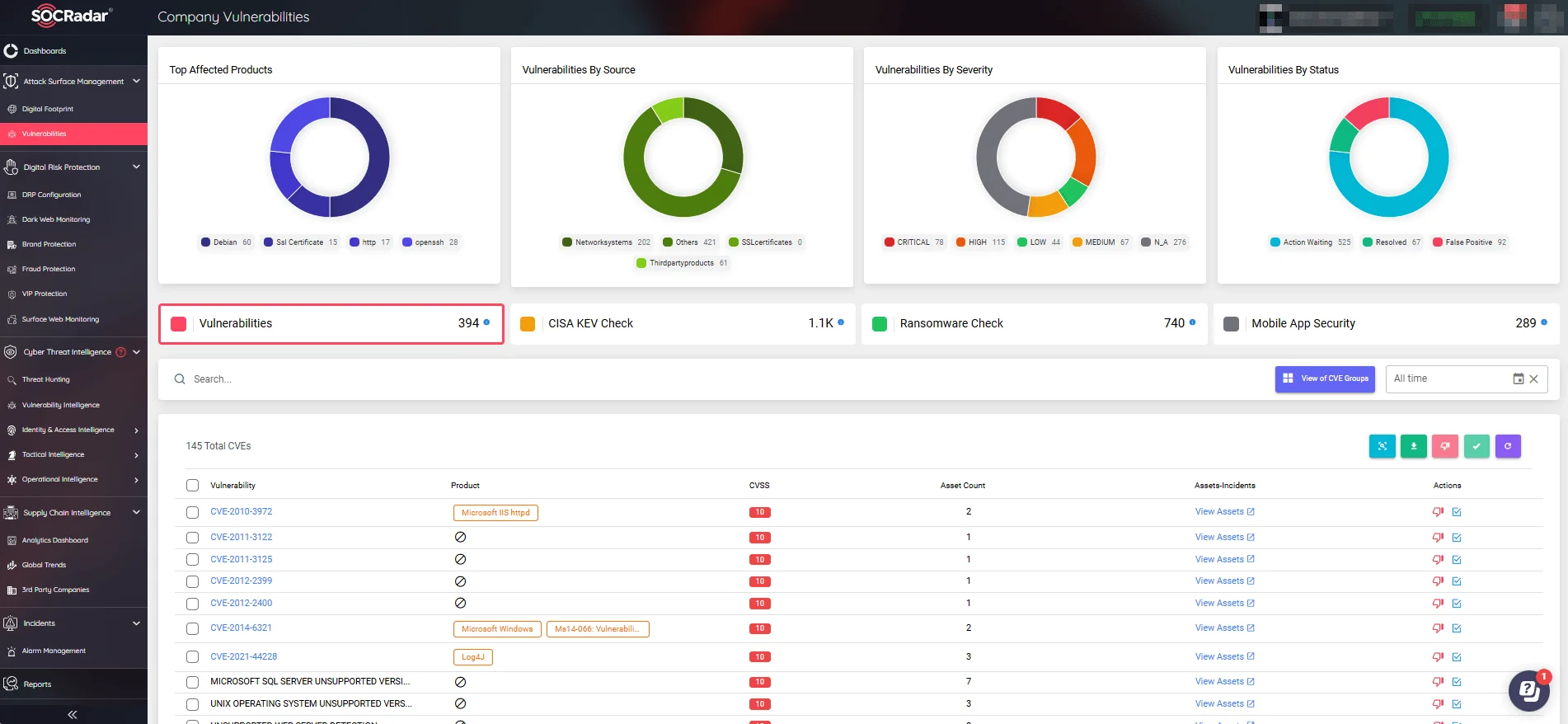
SOCRadar’s Attack Surface Management, Company Vulnerabilities
How to Secure Your VPN?
Ensuring VPN security is paramount for protecting sensitive data and maintaining the integrity of your network. The NSA provides specific recommendations to maintain a secure VPN environment, which network administrators should regularly implement:
- Reduce the VPN Gateway Attack Surface: Minimize the number of exposed VPN gateways and ensure they are configured securely.
- Verify Cryptographic Algorithms: Ensure that cryptographic algorithms comply with the Committee on National Security Systems Policy (CNSSP).
- Avoid Using Default VPN Settings: Default settings can be easily exploited. Customize settings to enhance security.
- Remove Unused or Non-Compliant Cryptography Suites: Eliminate any cryptographic suites that are not in use or do not meet security standards.
- Apply Vendor-Provided Updates: Regularly apply patches and updates provided by VPN vendors to address vulnerabilities.
Additionally, consider the following practices to further secure your VPN:
- Search for Unauthorized Changes: Regularly inspect all configuration options for unauthorized changes. This includes checking the authorized key file of SSH, new IPtables rules, and commands on clients.
- Monitor VPN Logs and Network Traffic: Keep an eye on VPN logs and network traffic. Pay special attention to connections from unusual IP addresses, particularly those with successful connections or long data transfers.
- Wipe Devices if Necessary: If you suspect exploitation but cannot find evidence of changes, consider wiping the device and following the manufacturer’s guidelines for reconfiguration.
- Enable Two-Factor Authentication (2FA): Protect your VPN from password replay attacks by enabling 2FA.
- Disable Unnecessary Functionality and Ports: Turn off any functions and ports that are not required or in use to reduce the potential attack surface.
To maintain a strong security posture, always heed to the following best practices:
- Regular Audits: Conduct regular security audits of your VPN configuration and usage.
- User Training: Educate users about the importance of VPN security and safe practices.
- Incident Response Plan: Develop and maintain an incident response plan specifically for VPN-related breaches.
- Multi-Layered Security: Implement a multi-layered security approach, including firewalls, intrusion detection systems, and endpoint protection, in conjunction with VPN security measures.
- Continuous Monitoring: Utilize advanced monitoring tools to continuously analyze VPN traffic and detect anomalies in real-time.
By following these steps and recommendations, organizations can significantly reduce the risk of VPN vulnerabilities and protect their networks from potential attacks.
Test Your VPN Security with SOCRadar’s VPN Radar
To ensure your VPN security is robust, try SOCRadar’s free VPNRadar tool. This non-intrusive and instant testing solution evaluates your VPN for multiple security aspects, including:
- Malware or Bot-Infected Devices: Detects if any devices connected through your VPN are infected with malware or bots.
- Unpatched Critical Vulnerabilities: Identifies critical vulnerabilities that haven’t been patched, ensuring your VPN is up to date with the latest security measures.
- Cryptographic Infrastructure Issues: Checks for problems in your VPN’s cryptographic setup that could compromise security.
- Man-in-the-Middle (MITM) Risks: Assesses the risk of MITM attacks, where attackers could intercept and alter communications.
VPNRadar is designed to provide immediate and actionable insights without disrupting your network. This ensures you can quickly identify and mitigate potential security issues, keeping your network and data safe.
Explore SOCRadar’s VPNRadar on SOCRadar LABS for a comprehensive evaluation of your VPN security today
Conclusion
The rise in VPN vulnerabilities underscores the escalating threat landscape — a total of 133 VPN vulnerabilities were reported in 2023 alone, marking a 47% increase from the previous two years. These vulnerabilities pose significant risks as attackers exploit them to infiltrate networks, steal data, and deploy malicious software.
Our exploration of the top 10 VPN vulnerabilities highlights the importance of staying vigilant and proactive in addressing these security flaws.
Vulnerabilities that we mentioned in this article, affecting the products of companies like Check Point, Fortinet, Zyxel, and Palo Alto Networks, are just a few examples of critical issues that need immediate attention.
Effective mitigation requires a multifaceted approach, including the application of vendor-provided patches, continuous monitoring for unusual activities, and implementing strong authentication practices.
You can use CTI platforms such as SOCRadar to stay informed about emerging threats, receive alerts on security issues, and better prioritize patching efforts.
For a preview of the Vulnerability Intelligence capabilities of SOCRadar, explore CVE Radar, a complimentary feature provided on SOCRadar LABS; stay updated on the latest emerging vulnerabilities and gain insights into the evolving threat landscape.
CVE Radar on SOCRadar LABS



































