What is Domain Hijacking and How to Prevent
Domain hijacking attacks can have many damaging consequences, such as the exposure of sensitive data and financial and reputational damage to organizations. These attacks can result in major data breaches and leaks. This article tells you everything you need to know about domain hijacking and how to protect yourself.
What is Domain Hijacking?
Domain hijacking is another utterance of domain name theft. The attack occurs by changing the registration of the domain name without the consent of the owner or by abusing privileges on domain hosting and domain registrar systems.
Domain Hijacking has several critical results on the owner of the domain. Financial damages might be devastating, especially if the company relies on its websites for a business like e-commerce companies. Reputational damages might also be painful since the hijacker could use the domain to display embarrassing content or use it for further attacks by installing malware or social engineering. The domain owner may face regulatory damages when the hijacker captures the data of users that can be used in cyberattacks such as identity theft.
Before going into much more detail, we should briefly mention how the domain name system (DNS) works to make the subject more lucent.
How Does the DNS Works?
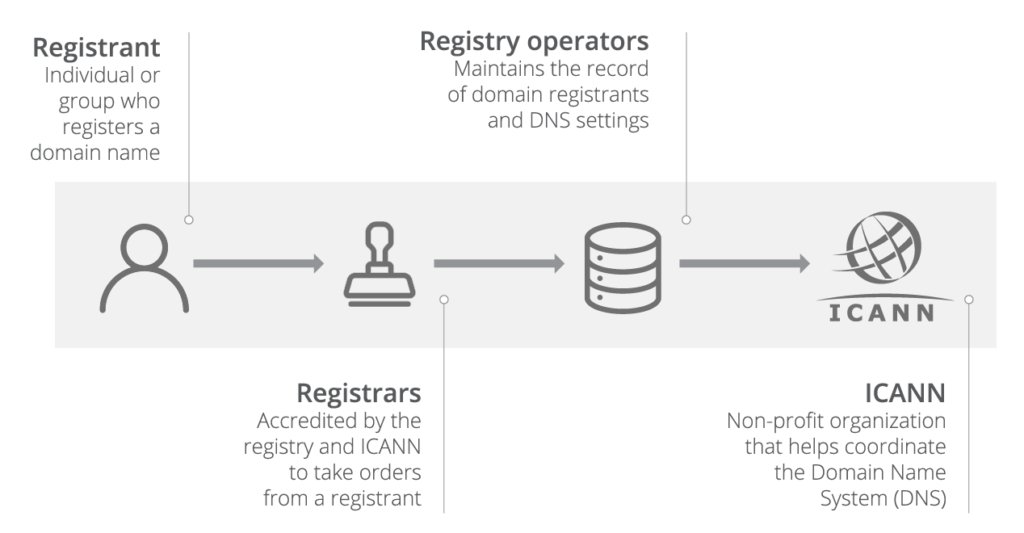
Top-level domains (TLD) are managed by an organization called a domain name registry, which is appointed by the Internet Corporation for Assigned Names and Numbers (ICANN). Verisign (.com and .net) and PIR (Public Interest Registry) (.org) are the two top TLD providers managing the most popular TLDs.
National domains like “.io”, “.com” or “.au” are managed by organizations in their respective countries. (Yes, our beloved .io is technically a country domain assigned to the British Indian Ocean Territory.)
Here the catch is registries do not always manage domain name registration. Organizations are called registrars accredited by ICANN and certified by the registries to sell domain names. They even subcontract to non-accredited registrars, introducing us to 3rd and 4th-party risks.
There are also no limitations on transferring the control of the domain from one registrar to another for any reason like better pricing, customer experience, better security policies, etc.
Increasing the number of parties involved cause lengthening the time to resolve potential domain name conflicts for proving domain ownership and approving domain transfers.
The domain ending up with a registrar that operates in a different jurisdiction is quite possible if processes are insufficient to detect and prevent fraud, misrepresentation, and impersonation of the registrant.
Top Techniques for Domain Hijacking
- Social engineering (phishing) is the most successful way. The hijacker can call the domain owner as the registrar’s impersonator or may convince him to fill in the necessary information on a fake login page.
- Another method is where the attacker convinces a domain registrar to transfer domain control to them by pretending to be the domain owner.
- Exploiting a vulnerability in the registrar system might be another way for the hijacker.
- Using outdated software, particularly outdated WordPress installations, poses high risks as they may be vulnerable to weak password abuse or SQLi attacks.
- Hijackers can gain credentials by infecting a victim’s computer with malware.
- Domain hijackers could also wait until the domain is close to expiring, hoping it will not be renewed in time because of a human error.
Known Domain Hijacking Incidents
- In September 2020, Perl.com hijacked and pointed it to an IP address associated with malware campaigns. The attackers changed the IP address from 151.101.2.132 to 35.186.238.101.
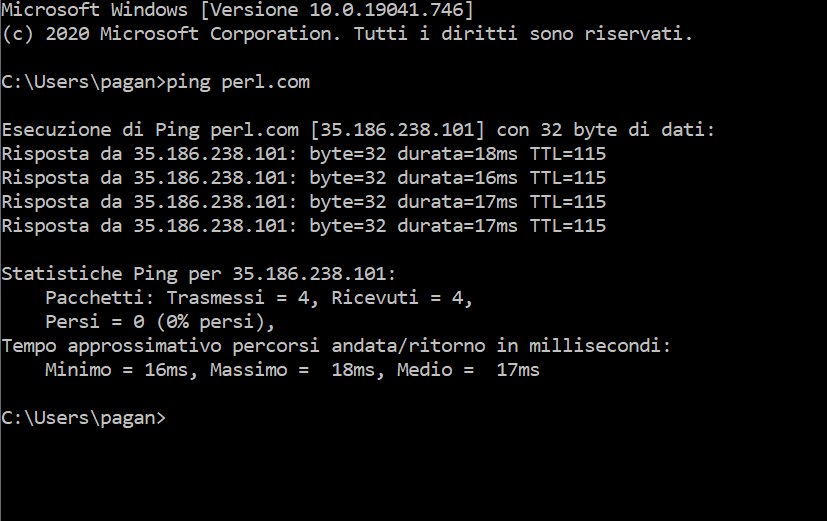
Shortly after the domain hijacking, perl.com was offered for sale for $190k on afternic.com.
- Lenovo’s Vietnam domain was briefly hijacked in 2015.

Users who were trying to access it were briefly redirected to another website (the interface of the official published site above). When the source codes of the website were examined, the names of Ryan King and Rory Andrew Godfrey, who were previously reported to be associated with the hacker group Lizard Squad, were found on the site.
More domain hijacking cases,
- Google’s Vietnam search page was also briefly hijacked in 2015.
- Microsoft forgot to renew passport.com and hotmail.co.uk, which resulted in their domain getting hijacked in 1999.
- ShadesDaddy.com was hijacked and transferred to an account in China in February 2015.
- In 2014 mla.com was hijacked, and it took almost two years for the domain owner to reclaim it.
How to Prevent Domain Hijacking
To prevent domain hijacking attacks, ICANN implements 60 days delay between any changes on the registration transfer and the domain transfer. Hence, once the transfer is completed from one registrar to another, it’s hard to revoke the process because the registrant is given enough time to discover any changes.
Extensible Provisioning Protocol (EPP) helps secure the domain transfer by ensuring communication between registries and registrars and providing an authorization code.
Additional steps to consider for preventing unauthorized domain transfers:
- Choose a reputed registrar which can provide comprehensive customer service, two-factor authentication, secure DNS management, and a solid security policy.
- Enable 2-factor authentication as an extra layer of security.
- Account locking as a precaution for brute-forcing attacks.
- Domain registry locks prevent unauthorized domain name control transfer to another registrar.
- Enable auto-renewal to avoid human error. Your domain might expire, and someone else can register.
- Enable whois protection to reduce the amount of information exposed which may help hijackers in the case of social engineering.
- Using a strong password and avoiding password reuse is a must, as always.
- Use a Sender Policy Framework (SPF) TXT record to help prevent domain hijacking attacks through DNS phishing.
- Keep contact details up to date.
- Continues tracking of your DNS records
How to Recover Hijacked Domains?
Recovering the hijacked domain is challenging and mainly depends on the registrar’s ability to revert the process.
If the transfer to another registrant has not happened yet, the registrar can return the domain name to the original owner with the proof of ownership.
Things get even more complicated when the control of the domain is successfully transferred to another registrar. In this case, we can invoke ICANN’s Registrar Transfer Dispute Resolution (TDRP) to regain domain control. Another way is to apply for ICANN’s Uniform Domain Name Dispute Resolution Policy (UDRP) process.
You will need to provide documentation to registrars (registration or billing records) or UDRP service providers proving an association between you, the complainant, and the hijacked domain name or account before the incident.
Especially with the cases of transferring the control of the domain to a registrar under different jurisdictions, failure of the recovery process is not surprising, which reminds us why we should care more about preventing domain hijacking in the first place.
How Can You Use Socradar for Early Detection of Domain Hijacking?
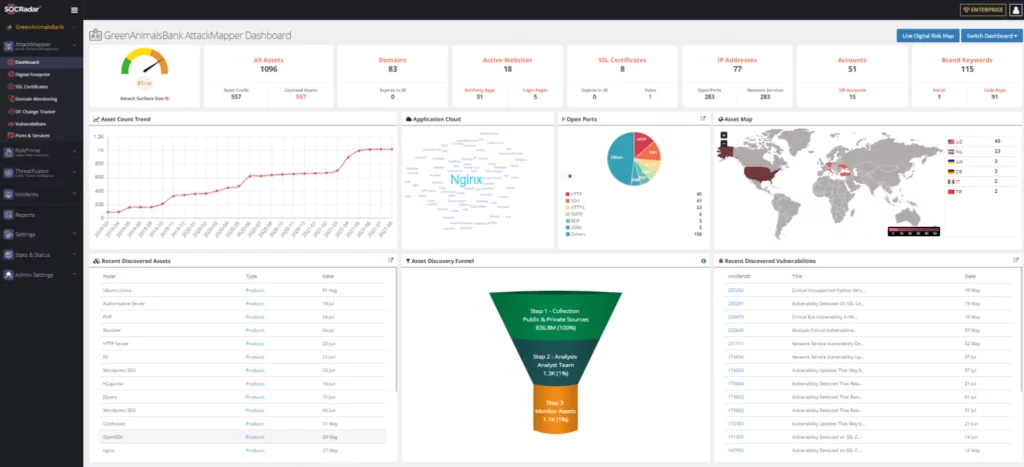
SOCRadar AttackMapper module prevents and quickly detects domain hijacking attacks by discovering and tracking your assets on the internet. AttackMapper helps customers gain additional visibility and context regarding the severity of unknown external-facing digital assets in an automated manner.
- Monitor DNS Record changes, whois information, change of the title, and content information of the website.
SOCRadar RiskPrime module provides the detection of intelligence information about your assets and your company:
- By automatically tracking company domains in dark and deep web sources, it informs your company of every incident,
- Via HUMINT ability of SOCRadar dark web analysts, the confirmation of the accuracy of the information and removal of the post to increase the company’s reputation when necessary.
SOCRadar ThreatFusion module provides to detect intelligence on current cyber events:
- Through the determinations made based on country-specific and sector-specific domain hijacking attacks, the companies which can be affected by these attacks are informed
- Actively informing security personnel about domain hijacking attacks.