Dark Web Profile: Vice Society Ransomware Group
By SOCRadar Research
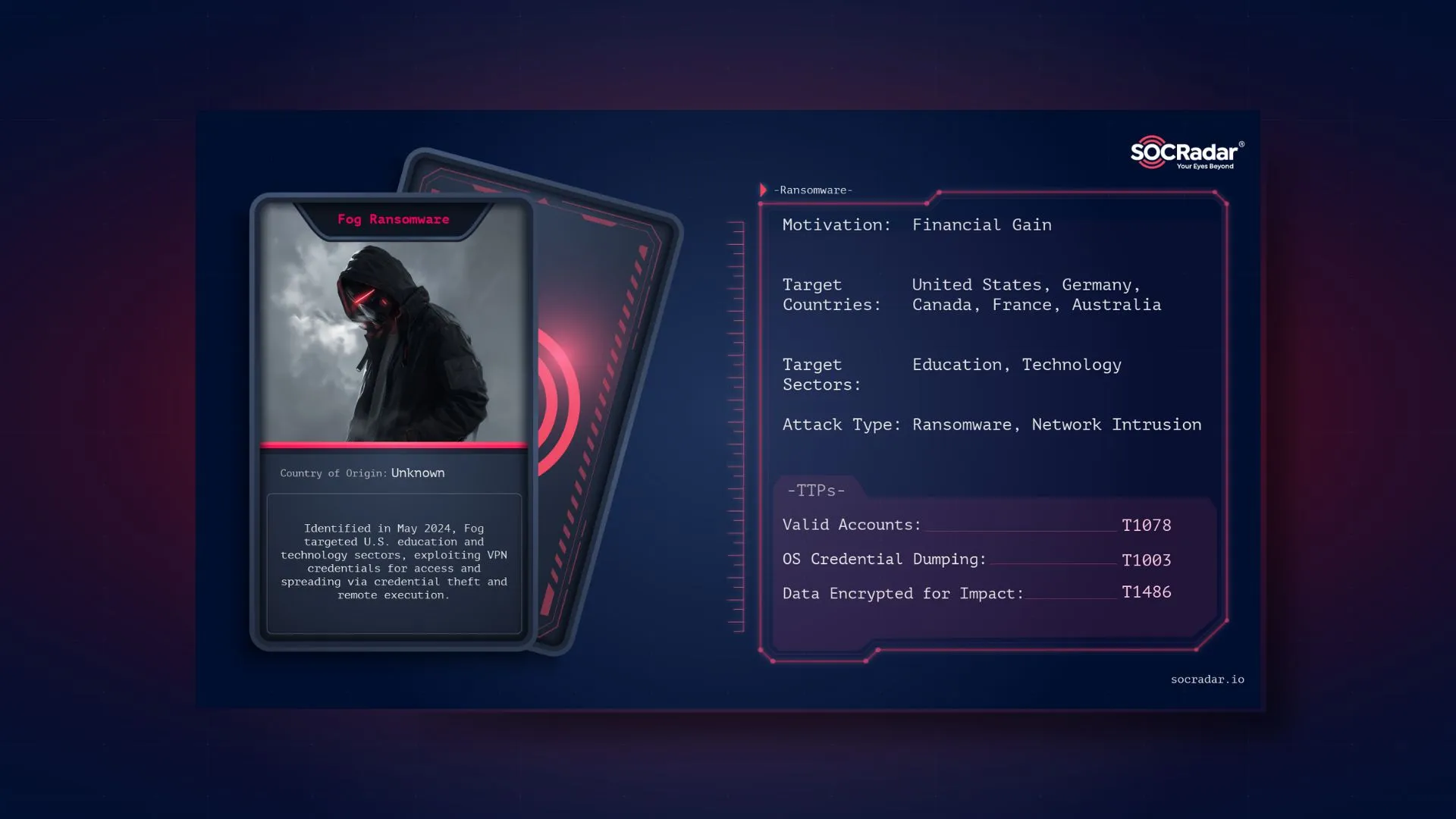
In recent years, the ransomware threat has snowballed. Many new actors have begun to show their heads in the scene and target organizations of all sizes. Some ransomware groups have actively moved up to the level of nation-state actors; however, the greater landscape of ransomware is composed of a fragmented ecosystem with multiple smaller players. The below graphic shows that, other than LockBit and Conti (ceased operations), no big players dominate the ransomware scene. Vice Society is one of the fragmented parts of this Ransomware landscape, performing only 3.4% of the total attacks since 2020.
Education was one of the most affected industries by the rise of ransomware threats. SOCRadar analysts detected a 234% increase in ransomware attacks on the education industry from 2021 to 2022. In 2022, Vice Society was the most active ransomware group targeting the education industry, with 39 attacks shared on the SOCRadar Ransomware Attacks feed.

Who is Vice Society?
Vice Society is a ransomware group that emerged in 2021 and has targeted organizations of all sizes. It has been observed that they have been performing big-game hunting, which is the criminal tactic of going after high-earning organizations. Since they started their activities, they also used double extortion on their targets, which is both encryption and data theft. Unlike most ransomware groups nowadays, they do not operate as a Ransomware-as-a-Service (RaaS) group. They are a closed group that does not have any affiliates. Even though they do not publicly state their origin, it is believed that they are a Russian-based criminal organization.
In addition, it has been marked that this group targets educational institutions, especially public schools. Moreover, like other prominent threat actors, Vice Society has a data leak site where they disclose data stolen from victims who refuse to pay extortion demands. They also share information about themselves regarding their operation on their leak site.
Who are Vice Society’s Victims?
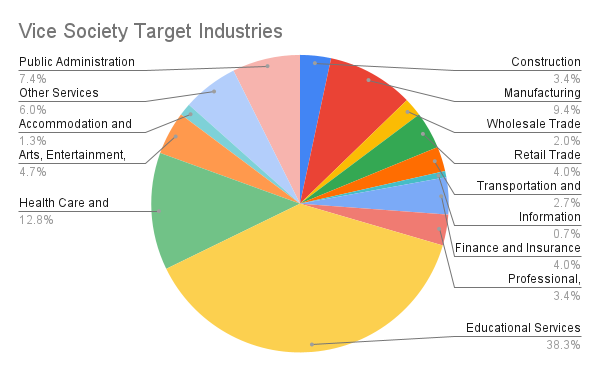
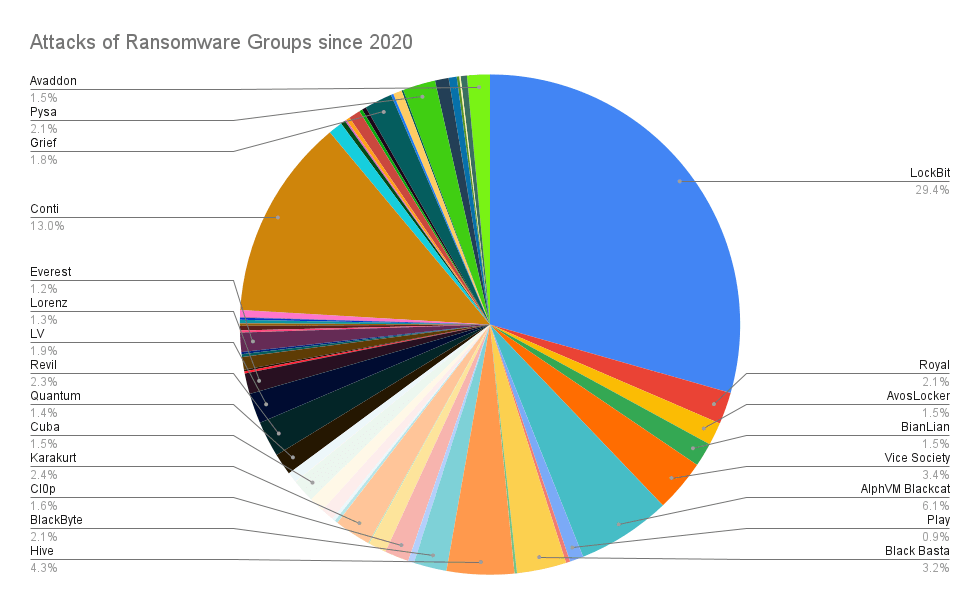
If we examine the data provided by the SOCRadar Ransomware Feed inside the CTI, we can see that Vice Society mainly targets educational and healthcare institutions. From the attacks of Vice Society, we know that this hacker group targets small and medium businesses rather than large ones. As with most ransomware groups, the reason for targeting these industries might stem from the fact that small-to-medium organizations have a lower budget for security measures. There is also the critical nature of the data held by the educational and healthcare institutions in question. Vice Society targets organizations in this realm to successfully achieve their end goal of extorting vast amounts of money.
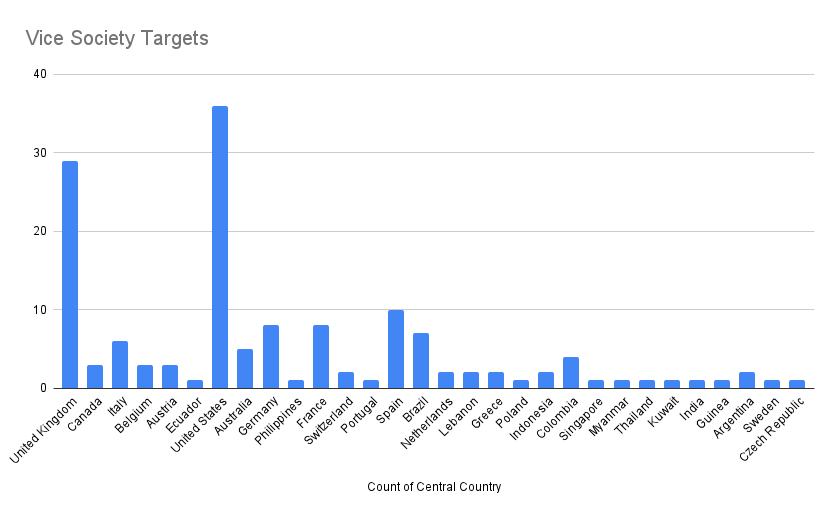
There is no specific geographic area that Vice Society is targeting. If we examine the graphic above, we can see that the Vice Society is active worldwide. However, from the data, it is clear that the US and the UK are two major targeted countries for Vice Society.
How does Vice Society Attack?
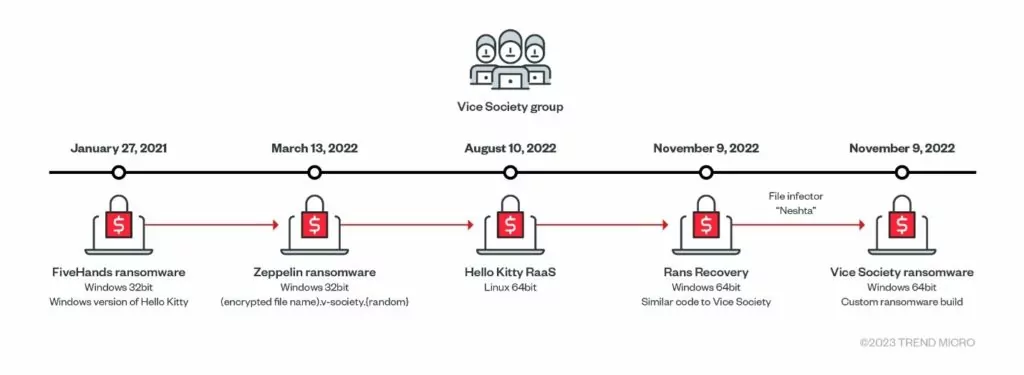
Vice Society, in their emergence, was reported to be exploiting the PrintNightmare vulnerability in their routines. At first, they did not develop their own ransomware but rather used third-party ransomware, including HelloKitty, Five Hands, and Zeppelin. But recently, they stepped up their game and developed their own ransomware called “PolyVice.”
You can find a timeline of their use of ransomware variants below.
Analysis of PolyVice Variant
Malware Composition
The Vice Society consists of the following components:
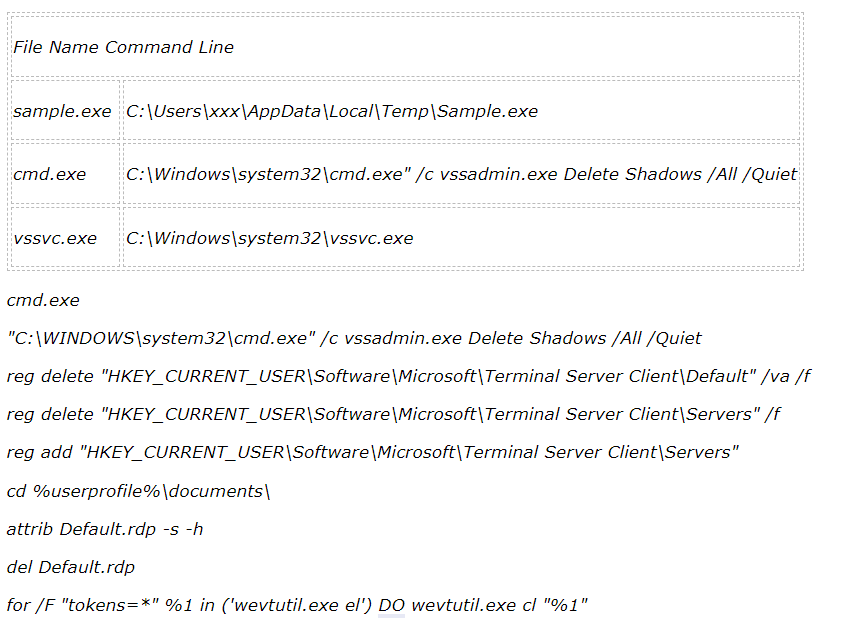
Another API detected with suspicious activity for vssvc.exe is “AdjustPrivilegeToken“. After completing all the processes, it sets the desktop background as in the figure below.
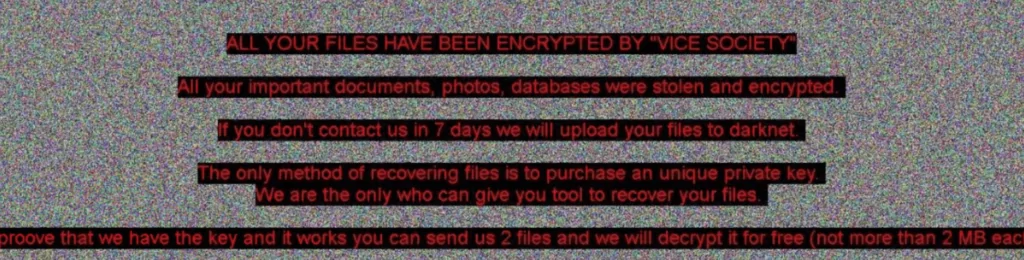
And it presents the ransom note below.
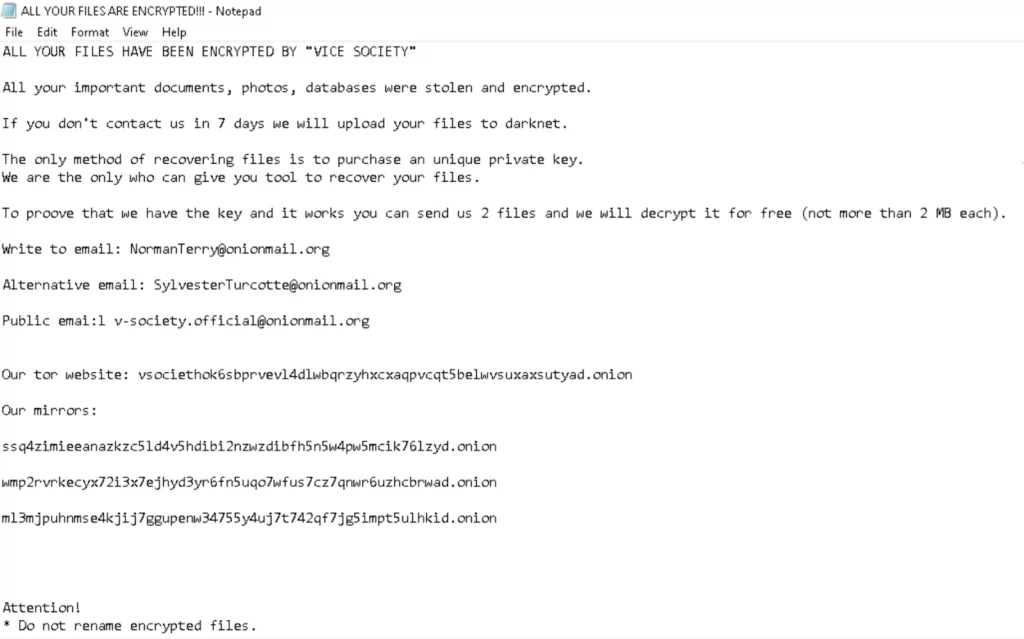
Static Analysis
| File Type Executable | |
| Entropy | 6.347 |
| Dynamic-Link-Library | False |
| File-Can-Be-Executed | True |
| Suspicious APIs | VirtualProtect, FindFirstFileW, FindNextFileW, WriteFile, ShellExecuteExW, CryptAcquireContextA, CryptGenRandom |
First function call
- call GetSystemTimeAsFileTime: This line calls the GetSystemTimeAsFileTime function, which is part of the Windows operating system. This function fills the SystemTimeAsFileTime memory location with the current system time as a 64-bit value.
- call GetCurrentProcessId: This line calls the GetCurrentProcessId function, which returns the identifier of the current process. The return value is stored in the eax register.
- xor rsi, qword ptr [rsp+58h+PerformanceCount]: This line performs a bitwise exclusive OR (XOR) operation between the value in rsi and the value stored in the PerformanceCount memory location. The result is stored in rsi.
It uses an open-source implementation of the NTRUEncrypt algorithm known to be quantum resistant. For symmetric encryption, it uses an open-source implementation of the ChaCha20- Poly1305 algorithm, a stream cipher with message authentication, a 256-bit key, and a 96-bit nonce.
This is achieved through the CreateThread function to spawn multiple workers, and the synchronization with the main thread occurs with a WaitForMultipleObject call. To exchange data between the main thread and the worker threads, it uses an I/O Completion Port, a helper function exposed through the Win32 API call CreateIoCompletionPort that provides an efficient way to manage concurrent asynchronous I/O requests through a queue.
Dynamic Analysis
We used Fiddler, one of our Network Analysis tools, to run and monitor ransomware from the Vice Society group. But this time, it stopped working because Fiddler files were also encrypted. You can examine it more thoroughly with the debugger outputs in the image below. The screenshot is from the activity made during the encryption phase.
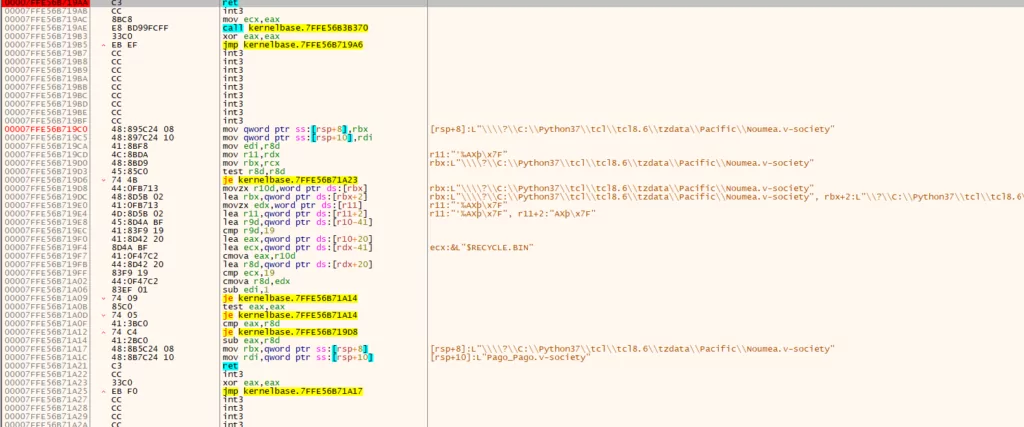
While the malware runs, it provides an internet connection with conhost.exe as a child process. (I/O)
Network Traffic
| IP Adress | Process |
| 40.127.240.158:443 | Svchost.exe |
| 8.253.208.120:80 | Svchost.exe |
| 93.184.220.29:80 | Svchost.exe |
| 209.197.3.8:80 | Svchost.exe |
VirusTotal Graph View
Prominent Attacks by Vice Society
On December 6, 2021, Spar announced via Twitter that for some of its operations in the UK, there had been an attack on the IT systems affecting the card payment functions of the shops; thus, many Spar shops were closed. At first, it was unknown who was responsible for this attack. Still, the Israeli intelligence company Via informed that the ransomware group Vice Society claimed the attack through the data leak site.
It is also known that this attack took place as a result of infiltration into the systems of James Hall & Co., the leading wholesaler of more than 600 sports stores in the north of England, and Heron and Brearley, owner of Mannin Retail. While the intelligence company Kela continued its investigations, it saw 93,000 files leaked regarding the two companies mentioned.
Vice Society carried out this attack for a financial purpose, but the leaked files and the fact that a lot of data was dumped by Vice Society showed that both companies did not pay the desired seedling.
Heron and Brearley left their requests for clarification unanswered for a long time. Moreover, they informed that the websites would remain offline, and the emails directed to them could not reach them. Then, on December 10, the UK National Security Center confirmed that James Hall & Co. had been attacked.
Afterward, the National Cyber Security Center spokesperson said they were aware of the incident and were working with Heron and Brearley to solve it. James Hall & Co. then confirmed that it had brought the affected stores back online.
Attacks Continue
In May 2022, Vice Society listed Indianapolis, Indiana-based Eskenazi Health, a public health provider, in its data leak site. The same month, the organization was responsible for a ransomware assault on the Waikato Region Health Board in New Zealand.
In September 2022, CISA released an alert regarding Vice Society. In this alert, they stated Vice Society aggressively targets educational organizations with ransomware attacks. According to CISA, even though schools with limited cybersecurity resources are the primary targets, the schools with robust cybersecurity measures still get hit by ransomware attacks.
In correlation to CISA’s alert, it was reported on October 2022 that Vice Society had released sensitive information about students from the Los Angeles Unified School District (LAUSD). Vice Society posted 500GB of stolen data on the dark web after employing double extortion to ransom the LAUSD.

Conclusion
In the rise of ransomware attacks throughout recent years, the Vice Society has found a seat for itself among other threat actors and conducted hundreds of attacks on organizations worldwide. According to their leak site, there are currently 149 victims who refused to pay the ransom. Because they are still in the business and the ransomware operations nature of yielding huge profits, there should be way more undisclosed victims.
They are a closed group, and they target industries with low-security measures. Their main target is the education industry, which in itself contains numerous private information of an enormous number of people. Some organizations in the education industry have the necessary means to protect themselves against such threats, but most schools lack the necessary funding for cybersecurity. It is unfortunately clear that Vice Society will continue to target these industries, which lack the required security resources. They pose a tremendous threat globally with their victim selection, but especially to organizations in the US and the UK.
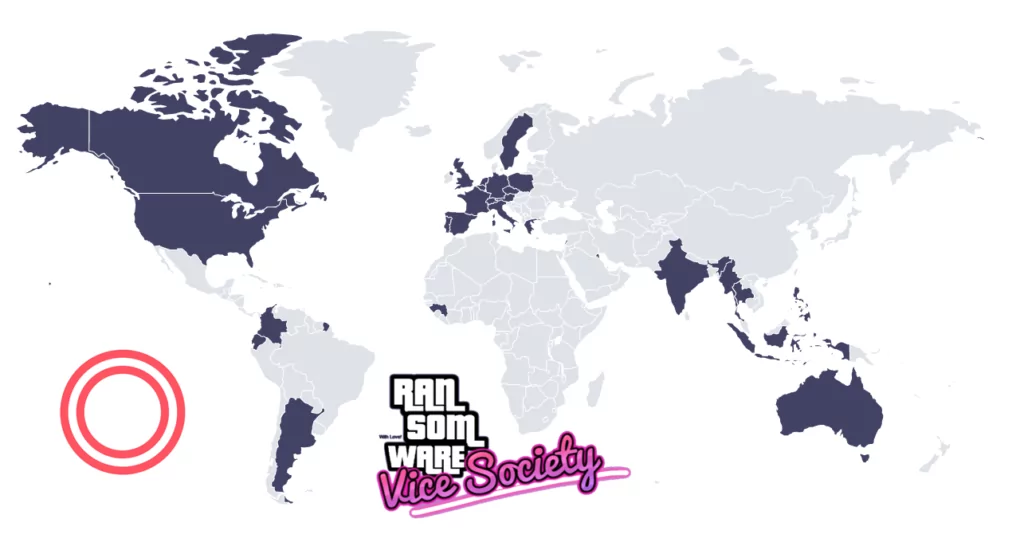
Like many other ransomware groups, Vice Society is looking for an opportunity to steal your data! Choose wisely where and with whom you share your information! You can try to mitigate against the threat of ransomware and Vice Society by following the security measures below:
Security Recommendations
- Vice Society is no different from most ransomware groups while approaching their victims. They leverage phishing for initial access in their attacks. SOCRadar provides brand protection with its Digital Risk Protection service. With brand protection, you can proactively deny potential phishing campaigns that may arise from impersonating domains.
- Vice Society leverages stolen credentials to gain initial access. Demanding the use of MFA for access may prevent the possible entry points from being breached.
- The most crucial suggestion when ransomware is in question is to keep offline backups. Offline backups shorten the time frame of returning to a functional state and possibly save a considerable amount of organizational resources.
- Internet-facing applications and systems vulnerabilities are actively exploited by Vice Society, such as PrintNightmare (CVE-2021-1675) and (CVE-2021-34527), to gain initial access. Organizations should be aware of any vulnerabilities in the environment to prevent this. SOCRadar provides Attack Surface Management which helps gain visibility into external-facing digital assets. With it, security teams can track the vulnerabilities in the environment. Knowing which vulnerabilities are present in the organization can limit the possible attack surface ransomware operators may exploit.
MITRE ATT&CK Techniques
| Techniques | ID |
| Initial Access | |
| External Remote Services | T1133 |
| Exploit Public-Facing Application | T1190 |
| Phishing | T1566 |
| Execution | |
| Command and Scripting Interpreter: PowerShell | T1059.001 |
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Windows Management Instrumentation | T1047 |
| Scheduled Task/Job | T1053 |
| Persistence | |
| Create or Modify System Process: Windows Service | T1543.003 |
| Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 |
| Boot or Logon Autostart Execution: Authentication Package | T1547.002 |
| Privilege Escalation | |
| Exploitation for Privilege Escalation | T1068 |
| Defense Evasion | |
| Masquerading | T1036 |
| Process Injection | T1055 |
| Indicator Removal | T1070 |
| Virtualization/Sandbox Evasion | T1497 |
| Modify Registry | T1112 |
| Impair Defenses: Disable or Modify Tools | T1562.001 |
| Credential Access | |
| OS Credential Dumping | T1003 |
| OS Credential Dumping: LSASS Memory | T1003.001 |
| OS Credential Dumping: NTDS | |
| Discovery | |
| Network Service Discovery | T1046 |
| Domain Trust Discovery | T1482 |
| Lateral Movement | |
| Remote Services | T1021 |
| Remote Services: SMB/Windows Admin Shares | T1021.002 |
| Taint Shared Content | T1080 |
| Lateral Tool Transfer | T1570 |
| Command and Control | |
| Remote Access Software | T1219 |
| Exfiltration | |
| Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002 |
| Automated Exfiltration | T1020 |
| Exfiltration over C2 Channel | T1041 |
| Exfiltration Over Alternative Protocol | T1048 |
| Impact | |
| Data Encrypted for Impact | T1486 |
| Account Access Removal | T1531 |
Appendix:
Appendix 1: Email Addresses
- v-society.official@onionmail[.]org
- ViceSociety@onionmail[.]org
- NormanTerry@onionmail[.]org
- SylvesterTurcotte@onionmail[.]org
Appendix 2: TOR Addresses
- vsociethok6sbprvevl4dlwbqrzyhxcxaqpvcqt5belwvsuxaxsutyad[.]onion
- wmp2rvrkecyx72i3x7ejhyd3yr6fn5uqo7wfus7cz7qnwr6uzhcbrwad[.]onion
- ssq4zimieeanazkzc5ld4v5hdibi2nzwzdibfh5n5w4pw5mcik76lzyd[.]onion
- ml3mjpuhnmse4kjij7ggupenw34755y4uj7t742qf7jg5impt5ulhkid[.]onion
Appendix 3: Network Traffic
- 40.127.240[.]158:443
- 8.253.208[.]120:80
- 93.184.220[.]29:80
- 209.197.3[.]8:80