Top 10 Ransomware Demands
In cyberspace, few threats rival ransomware attacks’ pervasive and destructive nature. As our interconnected world grows, these digital extortionists demonstrate unparalleled audacity. Their actions span from crippling multinational corporations to disrupting critical infrastructure and compromising personal data, causing ripple effects far beyond the virtual domain.
In this blog post, we embark on a journey to explore the Top 10 Ransomware Demands, each leaving an enduring impact on our digital landscape. We unveil the covert workings of ransomware groups with every account, wielding their technical prowess to hold priceless data hostage. We will create the list by starting from the highest payment demand and analyzing the attacks.
Hive, MediaMarkt, $240 million
In 2021, MediaMarkt, the prominent electronics retail chain, fell victim to a crippling Hive ransomware attack. The attackers initially demanded a staggering $240 million ransom, which resulted in the shutdown of critical IT systems and severe disruptions to store operations in both the Netherlands and Germany. As the largest consumer electronics retailer in Europe, MediaMarkt boasts a network of over 1,000 stores spread across 13 countries. With a workforce of approximately 53,000 employees and a total sales figure of €20.8 billion, the company’s significant presence in the market made it an appealing target for cybercriminals seeking to exploit vulnerabilities for their financial gain.
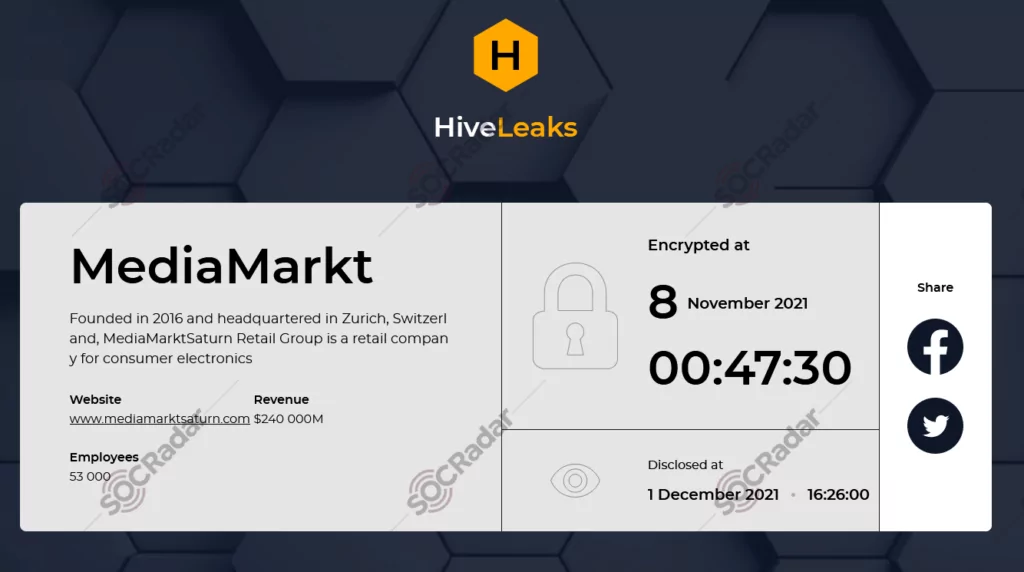
Alleged screenshots shared on Twitter hint at company internal communications, revealing that this ransomware attack has reportedly compromised approximately 3,100 servers. As per the ransom note, the malicious group purportedly claimed to have extracted data. In line with the usual modus operandi of double-extortion ransomware, they have threatened to publicly disclose the stolen information should the company refuse to meet its ransom demands. The attackers were essentially turning the data into a bargaining chip, posing the threat of leaking or selling the compromised information if the victims do not comply with their payment demands. However, it remained unclear whether MediaMarkt succumbed to the extortion and paid the ransom, which was allegedly negotiated down to a sum of $50M.
REvil, Acer $100 million
In March 2021, the REvil ransomware group set a record with unprecedented demand from Taiwanese computer manufacturer Acer. Initially, they demanded a staggering $50 million, which surpassed the previous highest ransomware demand of $30 million, associated with a REvil attack. Interestingly, REvil offered a 20% discount to Acer if the payment was made promptly, emphasizing the urgency of their demand. However, despite the incentive, negotiations stalled, and after eight days of no progress, the hackers astonishingly doubled their demand, escalating it to an eye-watering $100 million. Before the rise of Hive’s exceptionally high demand, even REvil’s $50 million demand was regarded as the highest ransom amount ever sought in ransomware history up to that date.
At that time, Advanced Intelligence detected that the Revil gang targeted a Microsoft Exchange server on Acer’s domain before the ransomware attack.
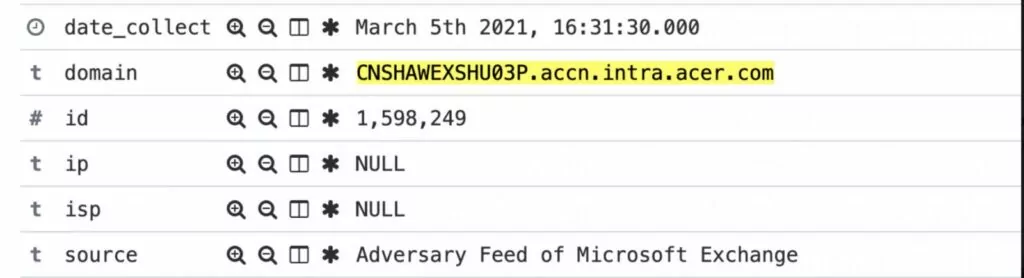
The widespread vulnerabilities (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) in Microsoft Exchange have been held responsible for numerous exploits impacting thousands of organizations globally. Notably, Acer’s ransomware attack emerged as the first high-profile incident directly linked to the exploitation of these Microsoft Exchange vulnerabilities. This association marked a significant milestone in the world of ransomware attacks, particularly in connection with the popular mail server software hack.
LockBit, Royal Mail, $80 million
In 2023, Royal Mail, the renowned British postal and courier company, made headlines worldwide when it fell victim to a high-profile ransomware attack orchestrated by the LockBit group. The attack had severe consequences, causing a disruptive impact on Royal Mail’s IT systems and operations, which persisted for nearly six weeks.
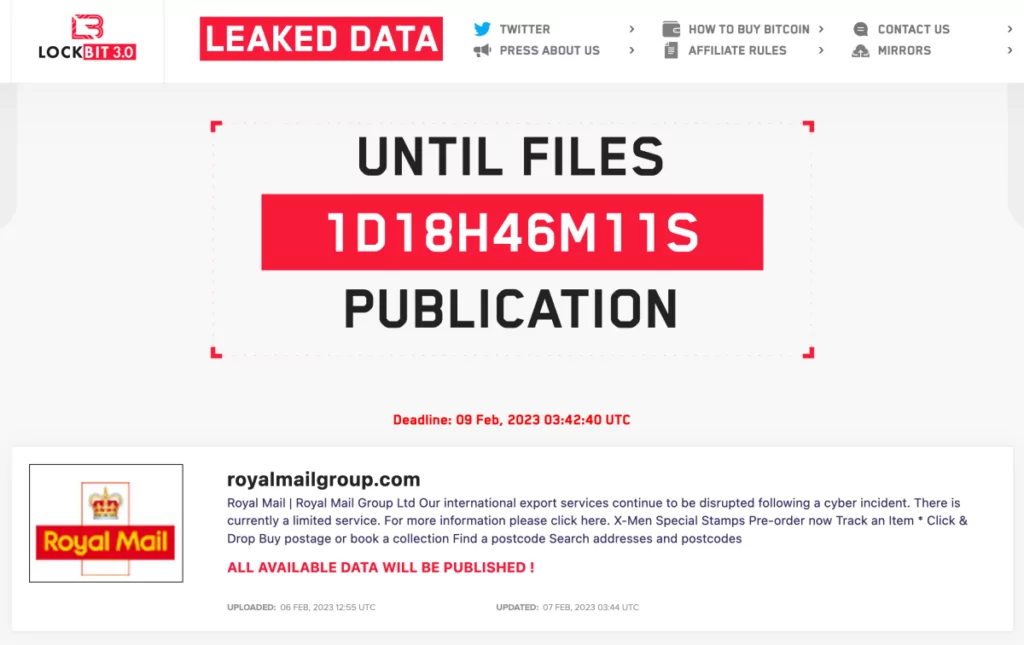
The attack’s ramifications were felt far and wide as Royal Mail’s ability to send parcels overseas was compromised, affecting numerous individuals and small businesses both in the UK and abroad. In a bid to exert pressure on the company, LockBit took an audacious step by publishing what they claimed to be the complete transcript of their negotiations with Royal Mail. Initially, the ransom demand stood at an exorbitant $80 million, with LockBit promising to provide a decryption tool and halt the publication of sensitive data upon payment. However, as negotiations unfolded, LockBit ultimately decreased their demand to $40 million. But later the LockBit group ultimately abandoned their pursuit of a ransom and instead chose to publish the stolen files from the company. This move abruptly ended weeks of negotiations, leaving Royal Mail without access to a decryptor and denying LockBit the payday they had sought.
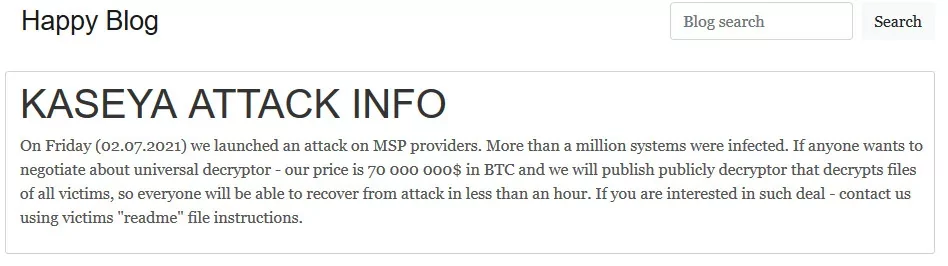
REvil, Kaseya, $70 million
Again, in July 2021, a malicious hotfix unknowingly spread through Kaseya VSA servers, encrypting thousands of nodes across hundreds of businesses with the notorious Sodinokibi ransomware, associated with the REvil group. Kaseya VSA, widely used for remote network management, became a prime target due to its extensive access and complex tasks, making backdoor monitoring challenging. Despite the attack, there was no evidence of Kaseya’s infrastructure being compromised. Instead, the attackers exploited vulnerable, internet-facing VSA servers frequently utilized by Managed Security Providers (MSPs) as backdoors to covertly distribute the ransomware downstream.
Recovering from this widespread infection proved daunting for affected organizations. The distribution of updates to numerous nodes caused a substantial blast radius of infection, forcing many European and APAC businesses to shut down while they worked diligently to remediate the situation. Through their blog, REvil made a ransom demand of $70 million in Bitcoin. The ransom was proposed to obtain a decryptor that could assist all affected victims in unlocking their encrypted files during the attack.
There is an interesting point about the incident: in the short period before the patch was made, the threat actors managed to exploit the pre-patch vulnerability. Kaseya VSA servers fell prey to a SQL injection attack, leaving them susceptible to remote exploitation. This vulnerability was assigned a CVE number: CVE-2021–30116. In contrast to REvil’s previous attacks, which involved prolonged dwell time and careful data exfiltration before ransomware deployment, this attack occurred rapidly.
Threat actors were aware of the race against time to develop a patch. Security researcher Victor Gevers (@0xDUDE) and the team at DIVD.nl had reported the vulnerability to Kaseya and collaborated on a patch, but REvil acted before the fix could be implemented.
Ransomware attacks can reach vast multitudes within the supply chain, like the vulnerability on MOVEit or which we have witnessed in Kaseya’s case in the past. We have a solution for this situation. Thanks to the SOCRadar Supply Chain Intelligence feature, you can receive alerts about the companies in your supply that you add to the WatchList.
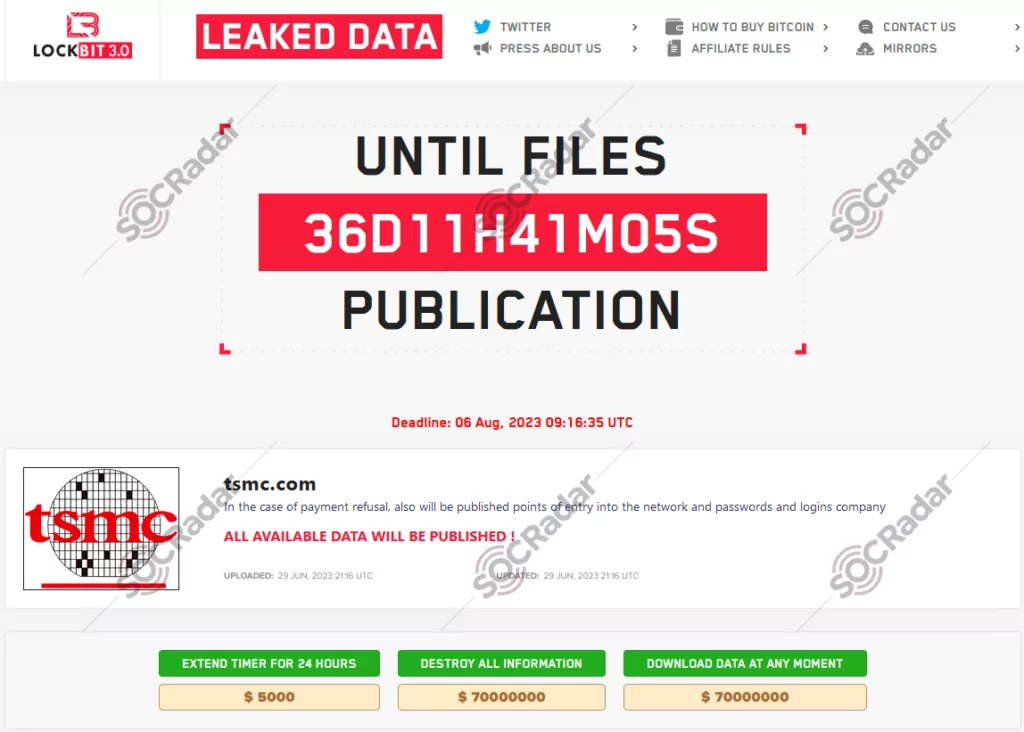
LockBit, TSMC, $70 million
In July 2023, the LockBit ransomware gang publicly added Taiwan Semiconductor Manufacturing Company (TSMC) to its list of victims on their leak site, TSMC confirmed a breach that had occurred at one of its hardware suppliers. On Friday, June 30, TSMC informed various media outlets that it immediately suspended data exchange with Kinmax Technology, a Taiwan-based company, as soon as the breach was discovered. Kinmax Technology had detected the breach on the same day that LockBit listed TSMC on their leak site and demanded a staggering $70 million ransom to delete the data they claim to have stolen securely. According to Kinmax Technology, an unidentified external group managed to gain access to one of its test environments and subsequently retrieved configuration files and other parameter information.
LockBit, Pendragon, $60 million
In 2022, again the LockBit ransomware gang targeted Pendragon Group, a major car dealership with over 200 locations across the U.K. The hackers demanded an astonishing $60 million ransom to decrypt the compromised files and prevent their leak.
Pendragon Group, known for owning car retailers such as CarStore, Evans Halshaw, and Stratstone, offers a wide range of car brands catering to various budgets, from luxury brands like Jaguar, Porsche, Ferrari, Mercedes-Benz, BMW, Land Rover, and Aston Martin to more affordable options like Renault, Ford, Hyundai, Nissan, Peugeot, Vauxhall, Citroen, DS, Dacia, and DAF.
According to Pendragon’s Chief Marketing Officer, Kim Costello, the attack occurred approximately a month prior to the disclosure. As soon as the breach was discovered, Pendragon promptly reported the incident to law enforcement and the U.K.’s data protection office. The company’s IT team reacted swiftly to counter the attack. The investigation into the breach revealed that the hackers had only accessed 5% of the database. Despite the ransom demand, Pendragon remained firm and chose not to pay, adhering to the guidance provided by security authorities.
Yanluowang, Walmart, $55 million
In 2022, the Yanluowang ransomware operation made a bold claim by posting on their data leak site that they had successfully breached a major retailer and encrypted a significant number of devices, estimated to be between 40,000 to 50,000. In an interview with BleepingComputer, the ransomware gang asserted that the attack had taken place over a month prior, during which they were able to encrypt devices but did not manage to steal any data. As part of their offensive, they demanded a colossal $55 million ransom from Walmart, but the retailer did not respond to their demands.
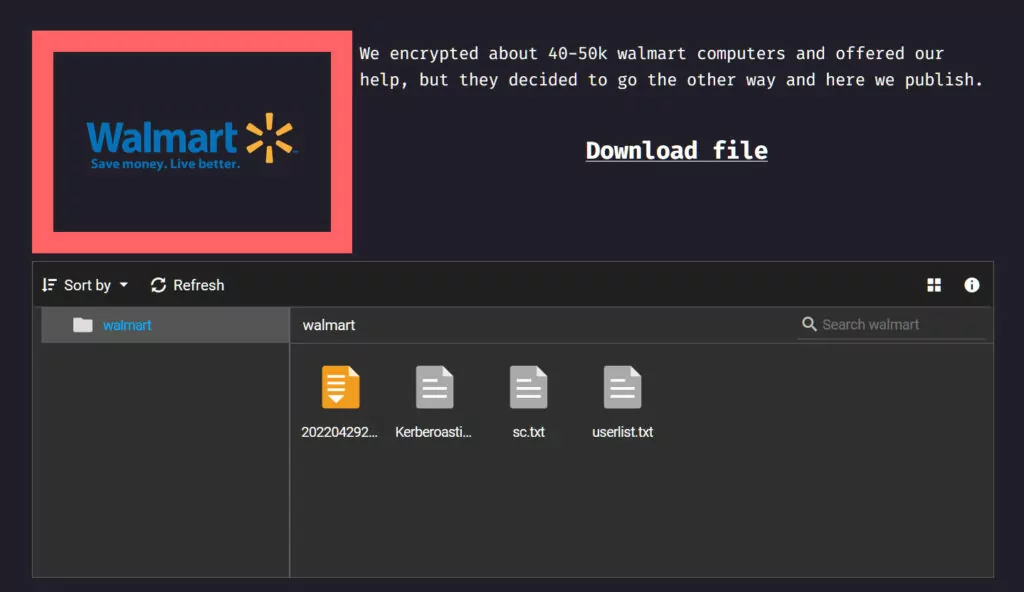
The entry on the data leak site contained several files allegedly extracted from Walmart’s Windows domain during the attack. Despite Walmart denying the success of any such attack, the files presented information claimed to be from the retailer’s internal network. These files included a security certificate, a list of domain users, and the output of a Kerberoasting attack, which is a brute-force password attack on Kerberos
LockBit, Continental, $50 million
In November 2022, the LockBit hacking group took responsibility for the cyber-attack that occurred in August against the multinational automotive group Continental. The ransomware gang threatened to publish Continental’s data through their leak site announcement unless a ransom was paid.

However, Continental refuted LockBit’s claims and chose not to pay the ransom. Consequently, LockBit put the alleged stolen data up for sale, setting a staggering price tag of $50 million. The reported amount of stolen data was approximately 40TB. Insiders familiar with the situation have speculated that the encrypted information may include sensitive materials such as minutes from supervisory board meetings, draft resolutions, and Continental’s board of directors presentations.
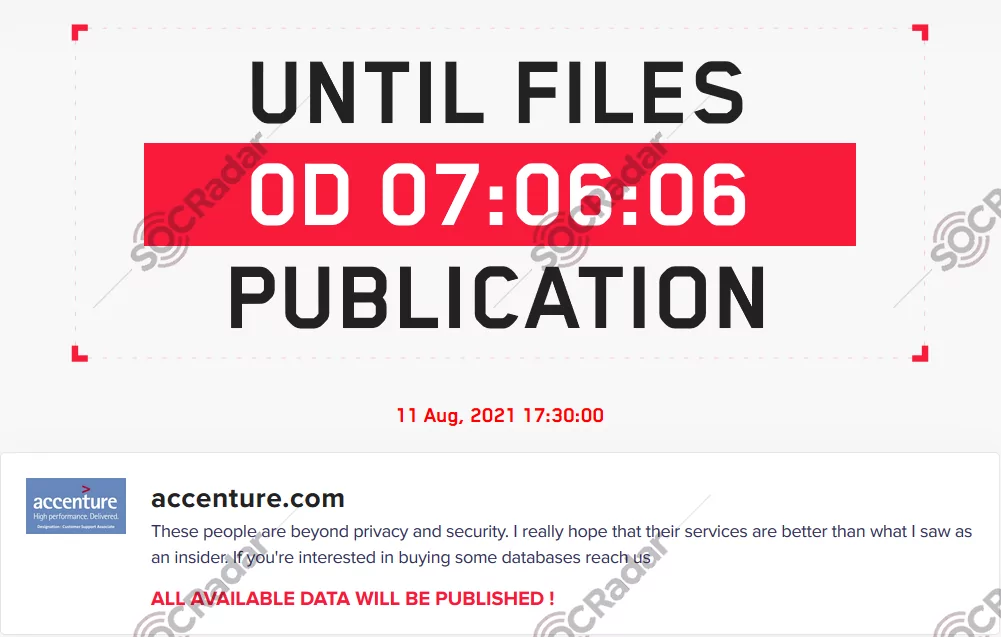
LockBit, Accenture, $50 million
Again and again LockBit. In its financial report for the fourth quarter and full fiscal year ending on August 31, 2021, global IT consultancy giant Accenture confirmed that a LockBit ransomware attack had targeted it. The attack resulted in the theft of data from Accenture’s systems. The ransomware gang claimed to have accessed six terabytes of data and demanded a staggering $50 million ransom.
While Accenture acknowledged the data breach and data leak in its financial report, the company has not made any public announcements outside of SEC filings or filed data breach notification letters with relevant authorities. This suggests that the stolen data may not have included personally identifiable information (PII) or protected health information (PHI), which would have triggered regulatory notification requirements.
However, according to allegations, the LockBit group, who had breached Accenture’s network with the assistance of an insider, later asserted that they used the stolen data to gain unauthorized access to two airports.
REvil, Quanta, $50 million
In a blog post, the ransomware group REvil made a bold claim, stating that they had successfully stolen blueprints for Apple’s latest products. Interestingly, on the same day, Apple CEO Tim Cook unveiled multiple new products during an online event. In response to the incident, Quanta Computer Inc., the company responsible for manufacturing Macbooks for Apple, acknowledged the cyber attack in a statement to Bloomberg. They reported that their information security team collaborated with external experts to address the attack, which specifically targeted a small number of servers. Quanta Computer Inc. reassured that despite the attack, their business operations had not suffered any significant impact.
Remarkably, during the same online event hosted by Apple, REvil took further action by posting plans for a new laptop. The leaked images resembled a Macbook design dating back to March 2021. Subsequently, REvil demanded an astonishing $50 million for the decryption key to unlock the stolen data.
Conclusion
The prevalence of ransomware attacks serves as a stark reminder of the significant cybersecurity challenges we face today. The examples discussed above highlight the costly consequences of such attacks. While the exact methods of some attacks remain unknown, it is generally observed that ransomware incidents often originate from phishing attacks, underscoring the critical importance of maintaining a strong focus on Cyber Security Awareness.
Another notable aspect is how vulnerabilities are exploited and accessed, particularly in the case of breaches involving large corporations. Insufficiently managed patches and neglected vulnerability assessments can create an open door for highly expensive ransomware attacks. As such, proactive measures in addressing vulnerabilities and timely patch management play a crucial role in safeguarding against these threats. The inadequate patch management scheme that led Kaseya to fall victim and the widespread Microsoft Exchange vulnerabilities that led to Acer’s victimization again underscores the importance of Vulnerability Intelligence.
In this context, SOCRadar’s Attack Surface Management (ASM) module comes to the aid of its users. SOCRadar ASM helps customers gain additional visibility and context regarding the severity of unknown external-facing digital assets in an automated manner. Our external attack surface management solution provides security teams with direct visibility into all internet-facing technological assets in use and assets attributed to IP, DNS, domain, and cryptographic infrastructure through advanced internet-wide monitoring algorithms. While discussing the importance of vulnerabilities, you may also use SOCRadar Vulnerability Intelligence to track these vulnerabilities and adjust your patch management accordingly.