
Most Exploited Vulnerabilities of 2023 (Insights to Define Cybersecurity in 2025)
As we near the close of 2024, cybersecurity remains a top priority for organizations navigating an increasingly hostile threat landscape. A recent joint advisory, issued in mid-November 2024 by leading cybersecurity agencies worldwide—including CISA, FBI, NSA, ACSC, CCCS, NCSC-UK, NCSC-NZ, and CERT NZ—has shed light on the vulnerabilities most exploited by cybercriminals in 2023.
One striking finding from the report is the surge in zero-day vulnerability exploitation in 2023. Compared to 2022, malicious actors increasingly leveraged zero-day flaws to compromise enterprise networks, targeting high-value organizations with unprecedented efficiency. Additionally, the majority of the most frequently exploited vulnerabilities in 2023 were initially exploited as zero-days—an alarming shift from the previous year, when less than half fell into this category.

The joint cybersecurity advisory “2023 Top Routinely Exploited Vulnerabilities” (Source: CISA)
Understanding these vulnerabilities and the tactics behind their exploitation provides invaluable lessons for the future. By analyzing patterns and root causes, organizations can strengthen their defenses, reduce attack surfaces, and anticipate emerging threats. In this blog, we’ll walk you through the Top 15 Routinely Exploited Vulnerabilities of 2023, some additional vulnerabilities identified in the advisory, and actionable recommendations for improving your organization’s cybersecurity posture.
Whether your organization is planning for 2025 or looking to mitigate immediate risks, these insights will empower you to stay one step ahead of evolving cyber threats. Let’s dive in.
What Makes a Vulnerability ‘Routinely Exploited’?
“Routinely exploited” vulnerabilities are ones that attackers consistently target due to their high success rates and widespread presence in systems.
These vulnerabilities typically share a common thread: they are often found in long unpatched systems, newly disclosed zero-days, or software components with known weaknesses like improper input validation or insecure configurations.
In parallel, the joint advisory highlights that malicious actors tend to focus on vulnerabilities within two years of their public disclosure. During this period, many organizations fail to patch or update their systems, leaving them exposed.
Zero-days, on the other hand, remain an enticing opportunity for attackers because they exploit unknown or unaddressed flaws. In 2023, the majority of the most exploited vulnerabilities were zero-days, marking a sharp increase from 2022. By understanding these patterns, organizations can better anticipate how attackers operate, prioritize patch management, and deploy proactive security measures. These insights form the foundation for the next section, where we’ll explore the Top 15 Routinely Exploited Vulnerabilities of 2023.
Top Routinely Exploited Vulnerabilities in 2023
The vulnerabilities exploited most frequently in 2023 reveal the sophistication of attackers and also the persistent gaps in organizational cybersecurity defenses. These vulnerabilities, often exploited as zero-days, were particularly valuable to malicious actors seeking to compromise high-priority targets, disrupt operations, or steal sensitive data.
What makes these vulnerabilities critical is their widespread presence across systems and the high success rates attackers achieve by exploiting them. Many of these flaws were found in widely used software and systems, amplifying their potential impact.
Effectively defending against attackers calls for leveraging a holistic vulnerability management solution. SOCRadar’s Vulnerability Intelligence module enables your security team to:
- Prioritize vulnerabilities based on exploitability and impact.
- Stay informed about emerging threats and zero-days in real time with SOCRadar Alarms.
- Streamline patching by focusing on high-risk vulnerabilities first.
By delivering actionable insights, SOCRadar enables businesses to close security gaps before attackers exploit them.
The Top 15 List
Below is a list of the 15 most routinely exploited vulnerabilities in 2023, as identified in the joint cybersecurity advisory. Each vulnerability is accompanied by a brief description of its significance:
1. CVE-2023-3519 (CVSS 9.8) Citrix NetScaler ADC & Gateway Code Injection Vulnerability
Critical infrastructure frequently serves as a prime target for malicious actors, and in 2023, Citrix NetScaler vulnerabilities became a key component of their exploit arsenal.
CVE-2023-3519 is a critical Remote Code Execution (RCE) vulnerability affecting Citrix NetScaler ADC and Gateway appliances. It enables attackers to execute arbitrary code without privilege or user interaction, making it a high-value target.
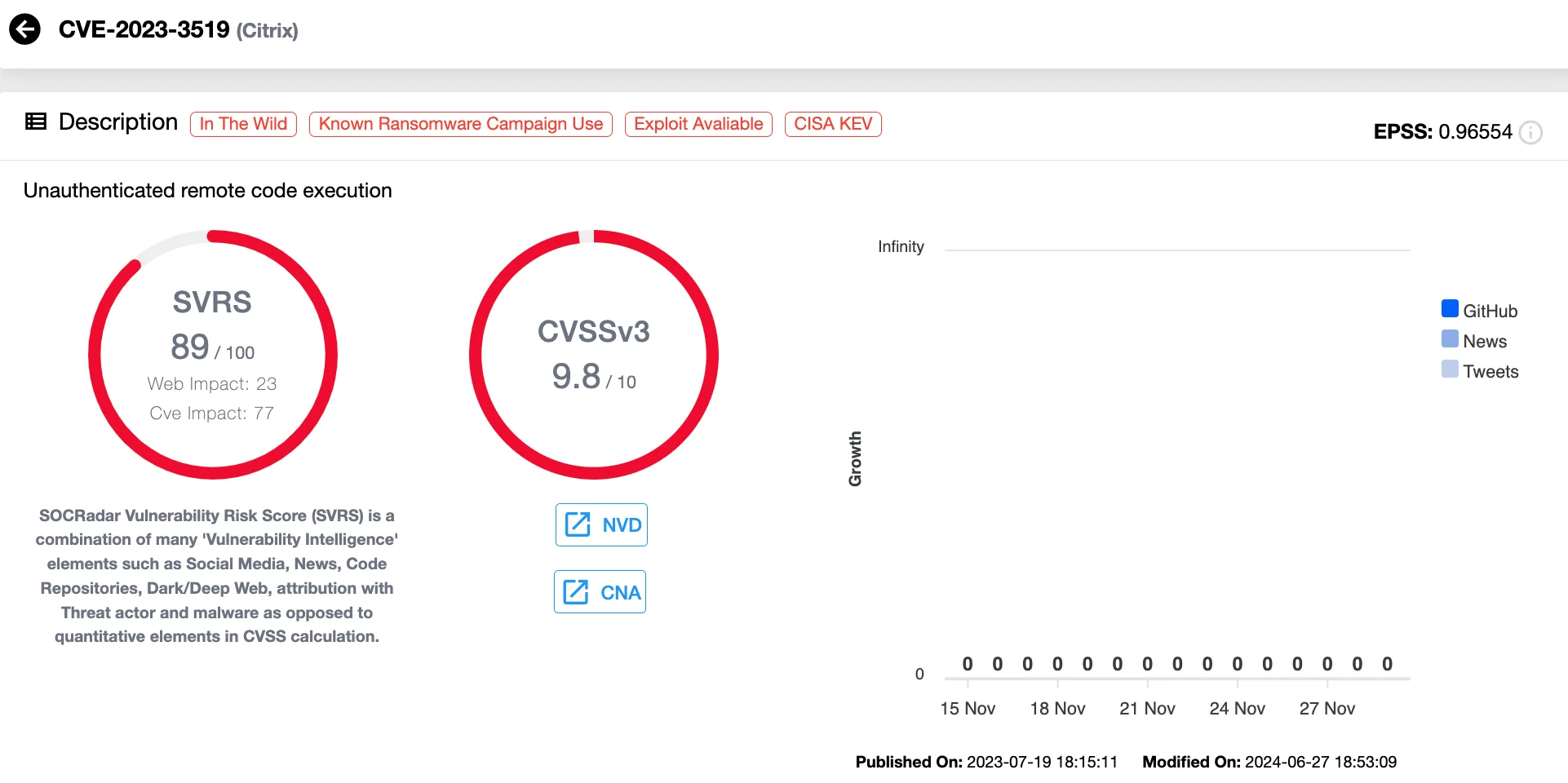
Details of CVE-2023-3519 (SOCRadar Vulnerability Intelligence)
Citrix addressed the flaw in July 2023 alongside other severe flaws (CVE-2023-3466 and CVE-2023-3467), but threat actors had already exploited it as a zero-day to compromise a critical infrastructure organization in June. The attackers deployed a web shell, conducted Active Directory discovery, and exfiltrated data.
2. CVE-2023-4966 (CVSS 7.5) Citrix NetScaler ADC & Gateway Buffer Overflow Vulnerability – Citrix Bleed
Known as “Citrix Bleed,” CVE-2023-4966 is another critical vulnerability targeting Citrix NetScaler ADC and Gateway appliances.
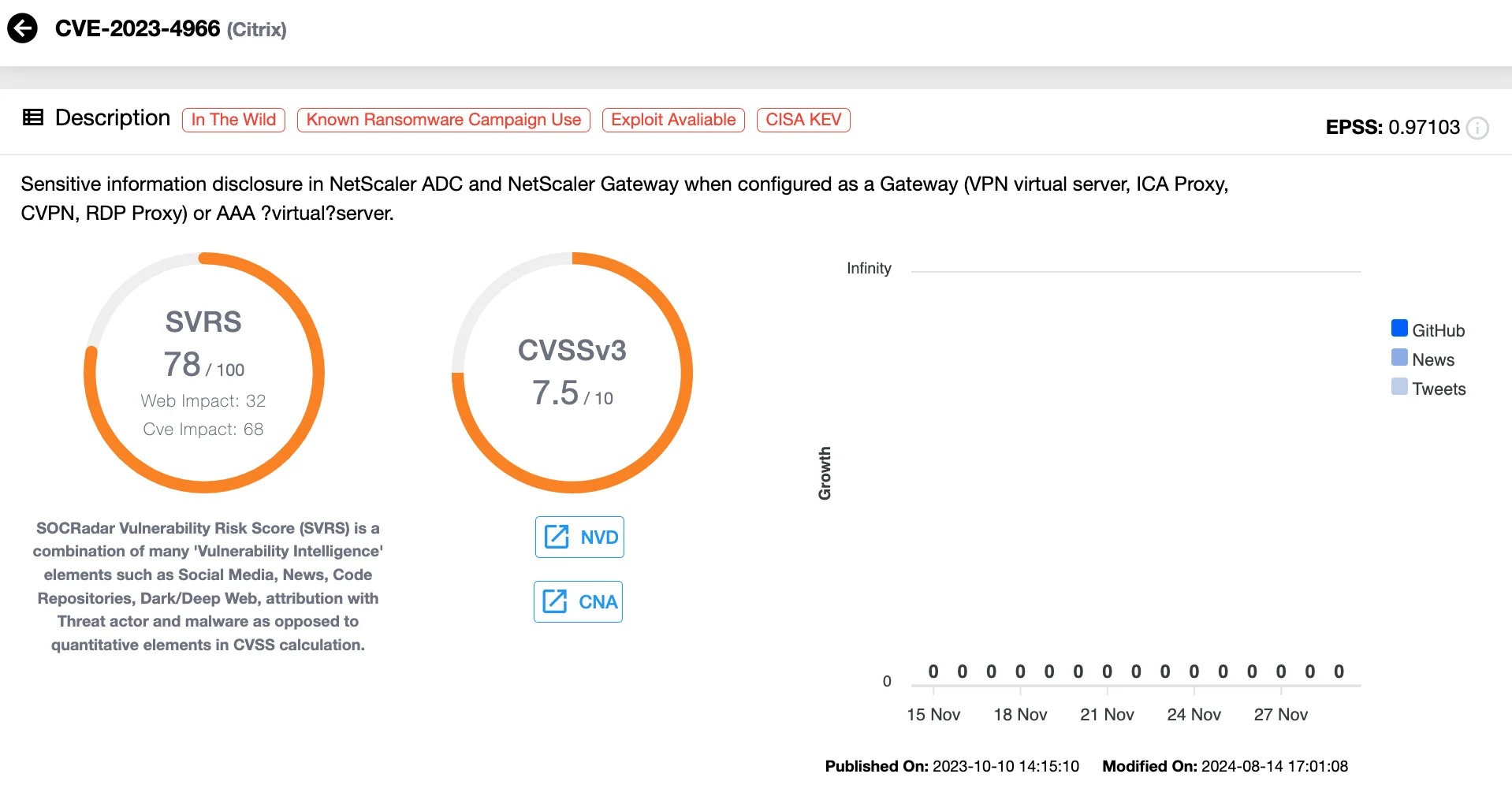
Details of CVE-2023-4966 (SOCRadar Vulnerability Intelligence)
Exploited as a zero-day in August 2023, it allows attackers to hijack authenticated sessions, bypassing Multi-Factor Authentication (MFA) and gaining unauthorized access. This vulnerability disproportionately impacted professional services, technology firms, and government organizations.
In October 2023, Comcast Xfinity disclosed a breach linked to Citrix Bleed, with attackers exfiltrating customer data, including usernames, hashed passwords, and partial Social Security numbers (SSNs). Later reports also tied the exploitation of CVE-2023-4966 to the LockBit 3.0 ransomware group.
3. CVE-2023-20198 (CVSS 10) Cisco IOS XE Web UI Privilege Escalation Vulnerability
Cisco’s ubiquitous network infrastructure made it a prominent target, with two major vulnerabilities exploited in tandem by threat actors. The first of them, CVE-2023-20198, is a critical zero-day vulnerability in Cisco IOS XE’s web UI, earning a maximum CVSS score of 10.0. This flaw allows unauthenticated attackers to create administrative accounts (privilege level 15), providing full control over affected devices.
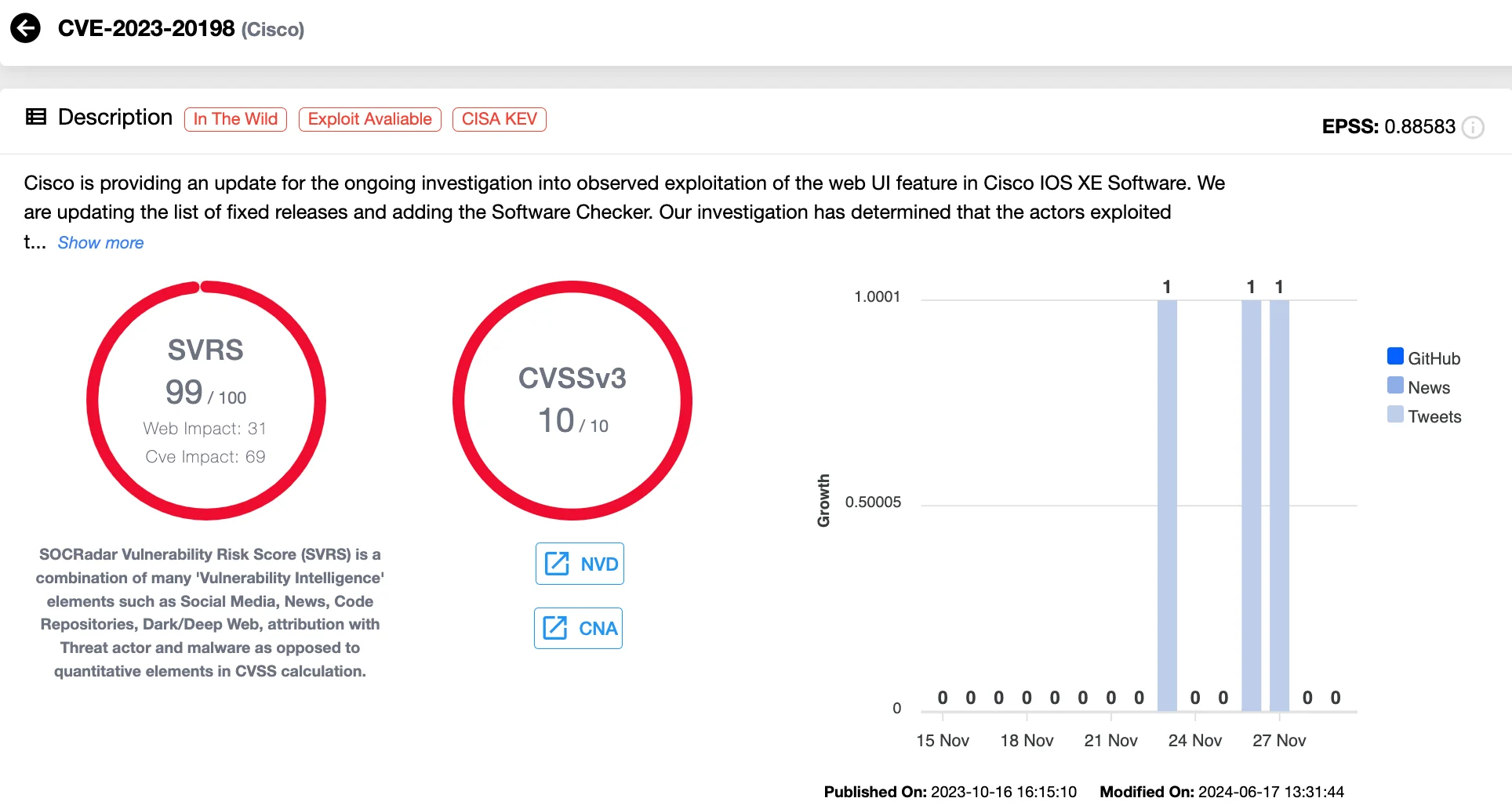
Details of CVE-2023-20198 (SOCRadar Vulnerability Intelligence)
Exploitation enables attackers to execute commands, modify configurations, and escalate privileges. Often, attackers use this vulnerability in combination with CVE-2023-20273, a command injection flaw, to strengthen their foothold.
4. CVE-2023-20273 (CVSS 7.2) Cisco IOS XE Web UI Command Injection Vulnerability
The second Cisco vulnerability is CVE-2023-20273 – a command injection vulnerability in Cisco IOS XE’s web UI. It allows authenticated attackers to execute root-level commands on affected devices. This flaw stems from insufficient input validation in the web UI component. Often exploited alongside CVE-2023-20198, this vulnerability forms part of a dangerous exploitation chain.
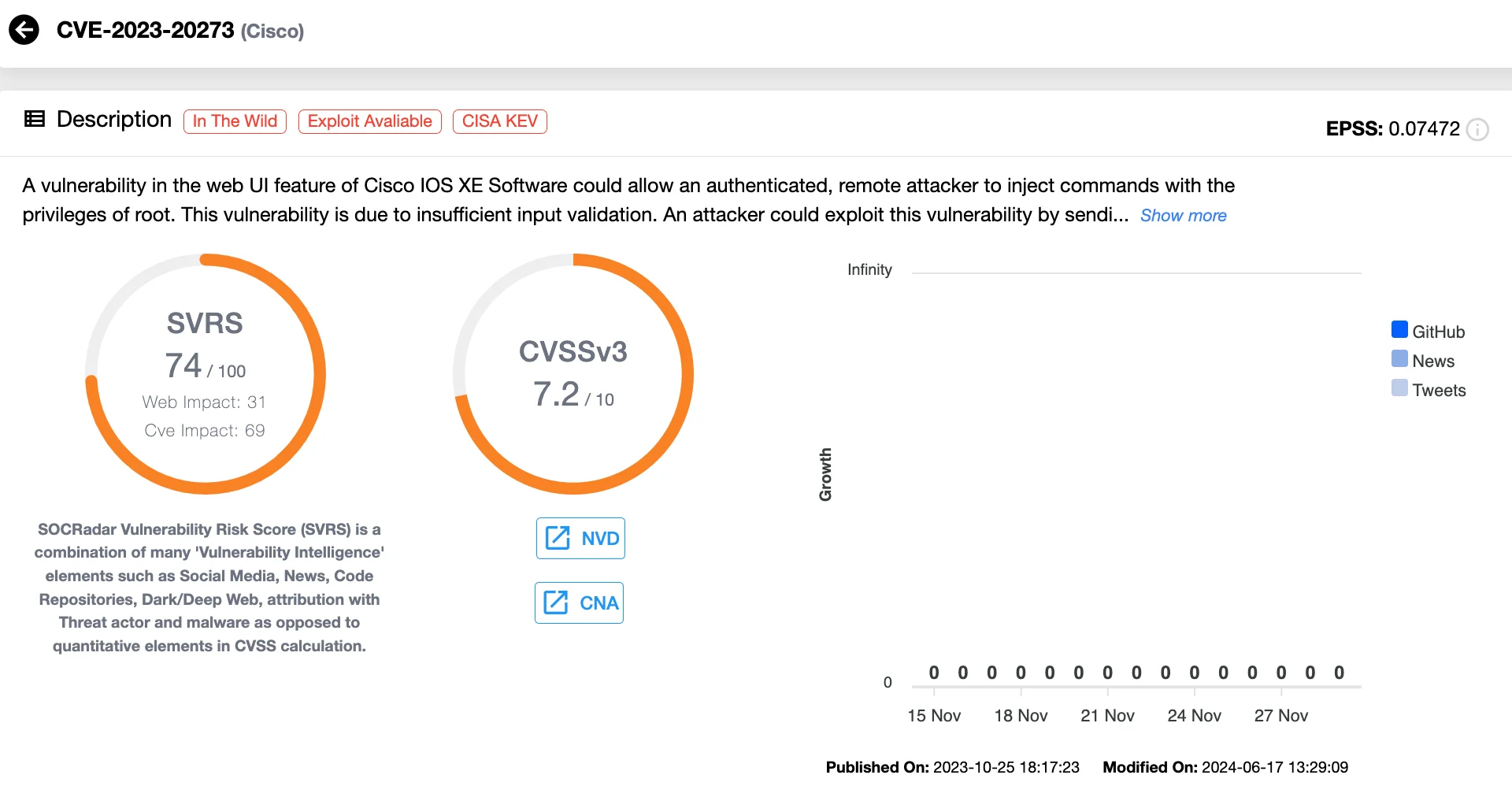
Details of CVE-2023-20273 (SOCRadar Vulnerability Intelligence)
Attackers typically begin by using CVE-2023-20198 to create a user account with normal privileges. They then exploit CVE-2023-20273 to escalate privileges, injecting commands with elevated rights. In live attacks, adversaries have deployed implants to maintain temporary control over compromised devices. These implants contain hexadecimal-encoded strings and allow remote command execution until the device is rebooted.
5. CVE-2023-27997 (CVSS 9.8) Fortinet FortiOS FortiProxy SSL-VPN Heap-Based Buffer Overflow Vulnerability
Fortinet’s SSL-VPN products were another favorite target for attackers in 2023, with critical vulnerabilities enabling sophisticated exploits
As a critical buffer overflow vulnerability in Fortinet’s FortiOS and FortiProxy SSL-VPN products, CVE-2023-27997 allows unauthenticated remote code execution, utilizing crafted requests. In June 2023, Fortinet disclosed that this vulnerability may have been exploited in limited cases. CISA’s inclusion of CVE-2023-27997 in its list of top routinely exploited vulnerabilities highlights its impact.
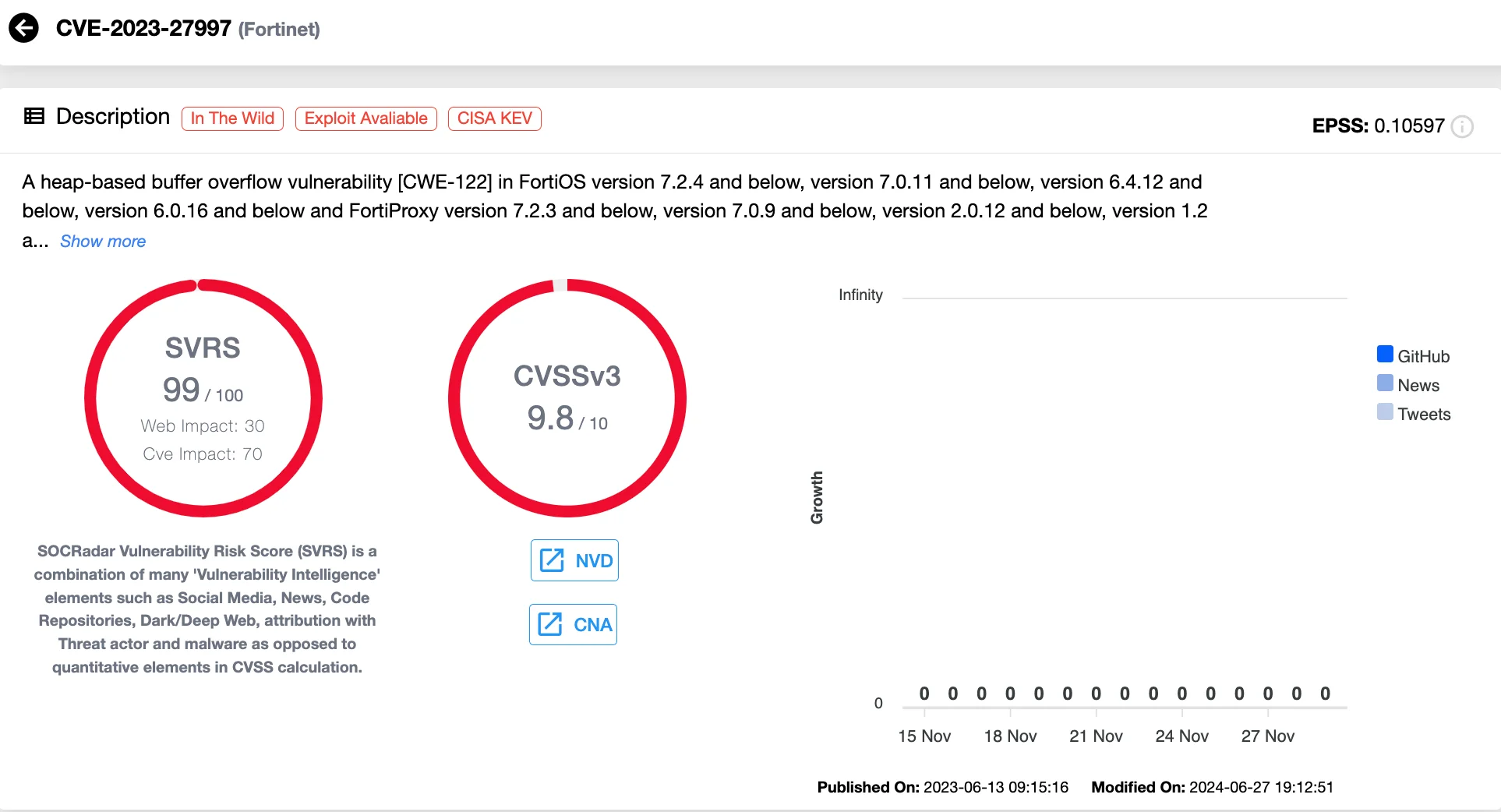
Details of CVE-2023-27997 (SOCRadar Vulnerability Intelligence)
Even if SSL-VPN was not enabled, Fortinet recommended that users upgrade to the most recent firmware versions to mitigate potential risks.
6. CVE-2023-34362 (CVSS 9.8) Progress MOVEit Transfer SQL Injection Vulnerability
Supply chain vulnerabilities, like those in Progress MOVEit Transfer, have underscored the importance of securing data flows in interconnected systems.
CVE-2023-34362, a critical SQL injection vulnerability in Progress Software’s MOVEit Transfer platform, led to one of the most significant exploitation campaigns of 2023, with the Cl0p ransomware gang deploying web shells like LEMURLOOT to steal sensitive data and execute OS commands.
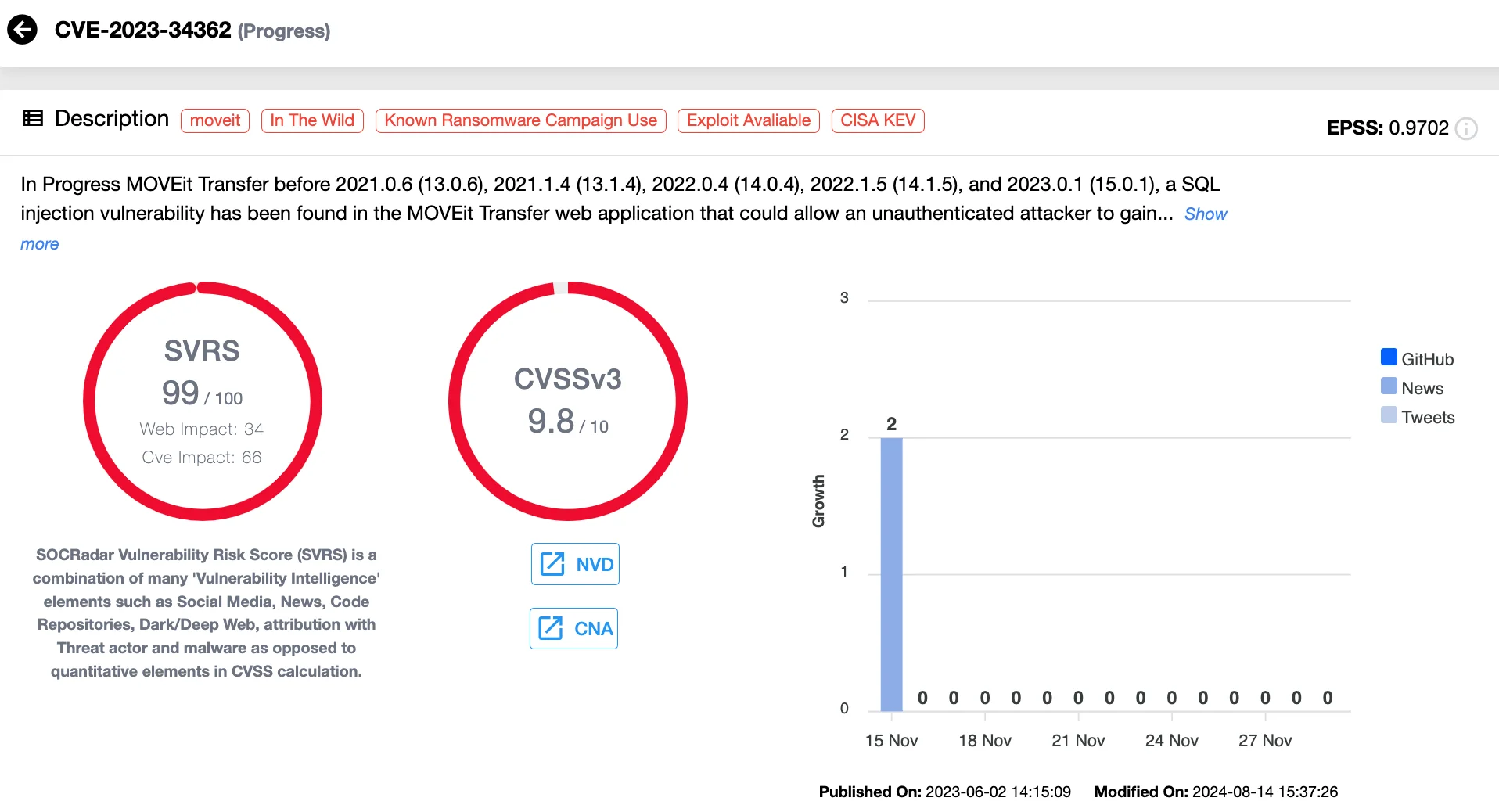
Details of CVE-2023-34362 (SOCRadar Vulnerability Intelligence)
In May 2023, Cl0p targeted this vulnerability to exfiltrate data from high-profile organizations, including the BBC, British Airways, and the U.S. Department of Energy. The attackers demanded ransoms, threatening to publish stolen information if payments weren’t made.
Progress Software faced scrutiny following these breaches, which affected over 95 million individuals and 2,770 companies globally. The SEC concluded an investigation into the company’s handling of this flaw in August 2024, underscoring the far-reaching consequences of unpatched vulnerabilities.
7. CVE-2023-22515 (CVSS 9.8) Atlassian Confluence Data Center and Server Broken Access Control Vulnerability
CVE-2023-22515 is a critical vulnerability in Atlassian’s Confluence Data Center and Server products. This broken access control flaw enables unauthenticated attackers to create unauthorized administrator accounts, granting full access to affected Confluence instances.
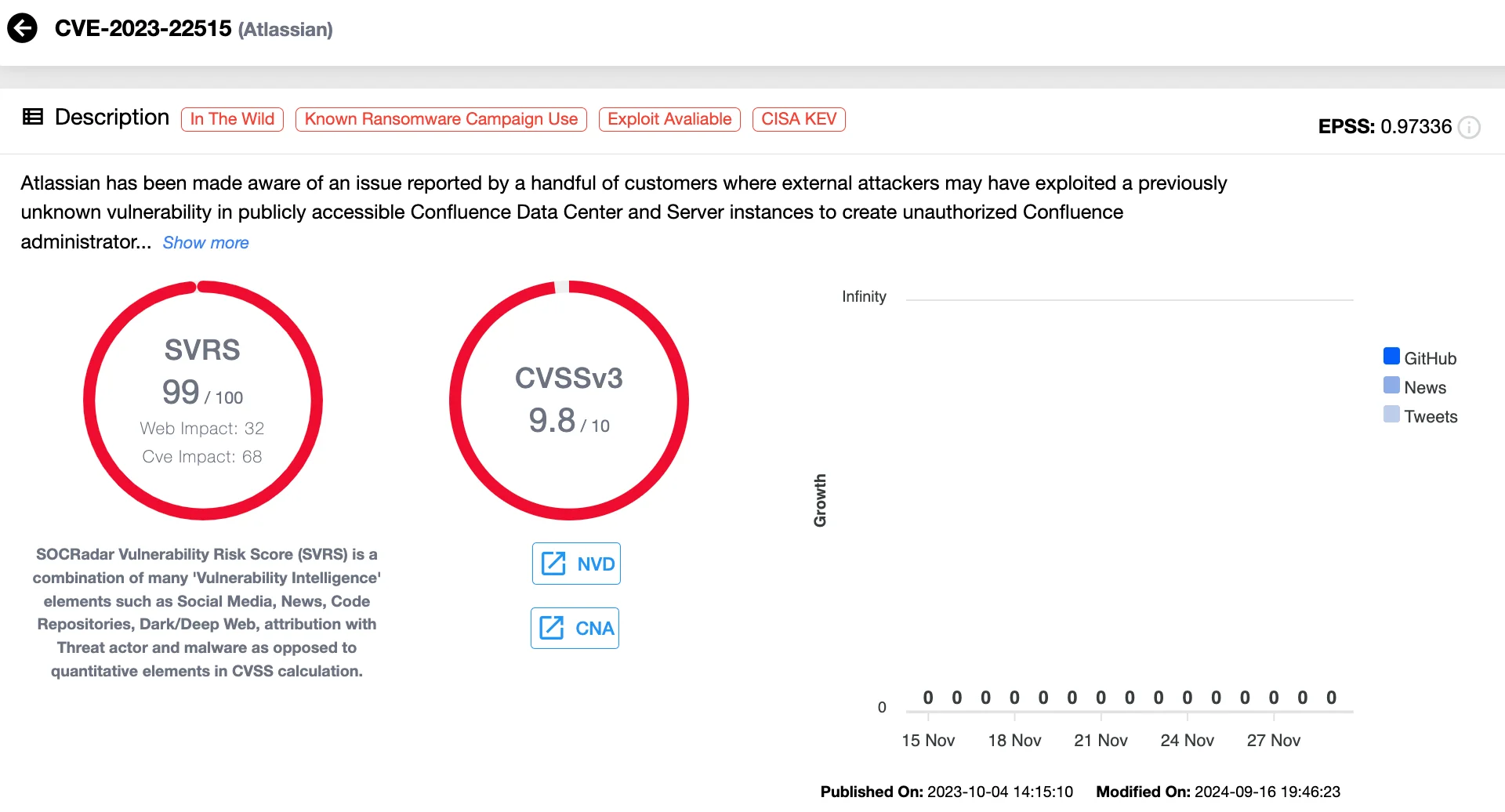
Details of CVE-2023-22515 (SOCRadar Vulnerability Intelligence)
In September 2023, exploitation of this vulnerability was linked to an Advanced Persistent Threat (APT) group identified by Microsoft as Storm-0062. The group actively targeted organizations, leveraging the flaw to infiltrate Confluence environments. Microsoft confirmed the real-world exploitation activity in October, highlighting the persistent risk posed by this vulnerability to businesses relying on Confluence for collaboration.
8. CVE-2021-44228 (CVSS 10) Apache Log4j2 Remote Code Execution Vulnerability – Log4Shell
Even vulnerabilities disclosed years earlier continued to cause havoc, with Log4Shell remaining a persistent challenge well into 2023.
Although first disclosed in December 2021, CVE-2021-44228, or “Log4Shell,” continued to be routinely exploited through 2023, demonstrating the long tail of vulnerabilities in widely used software. This critical flaw in Apache Log4j2 allows attackers to execute arbitrary code by sending crafted data to applications using vulnerable Log4j versions. Once logged, the exploit triggers Log4j to process the input in a way that enables attackers to load and execute remote malicious code.
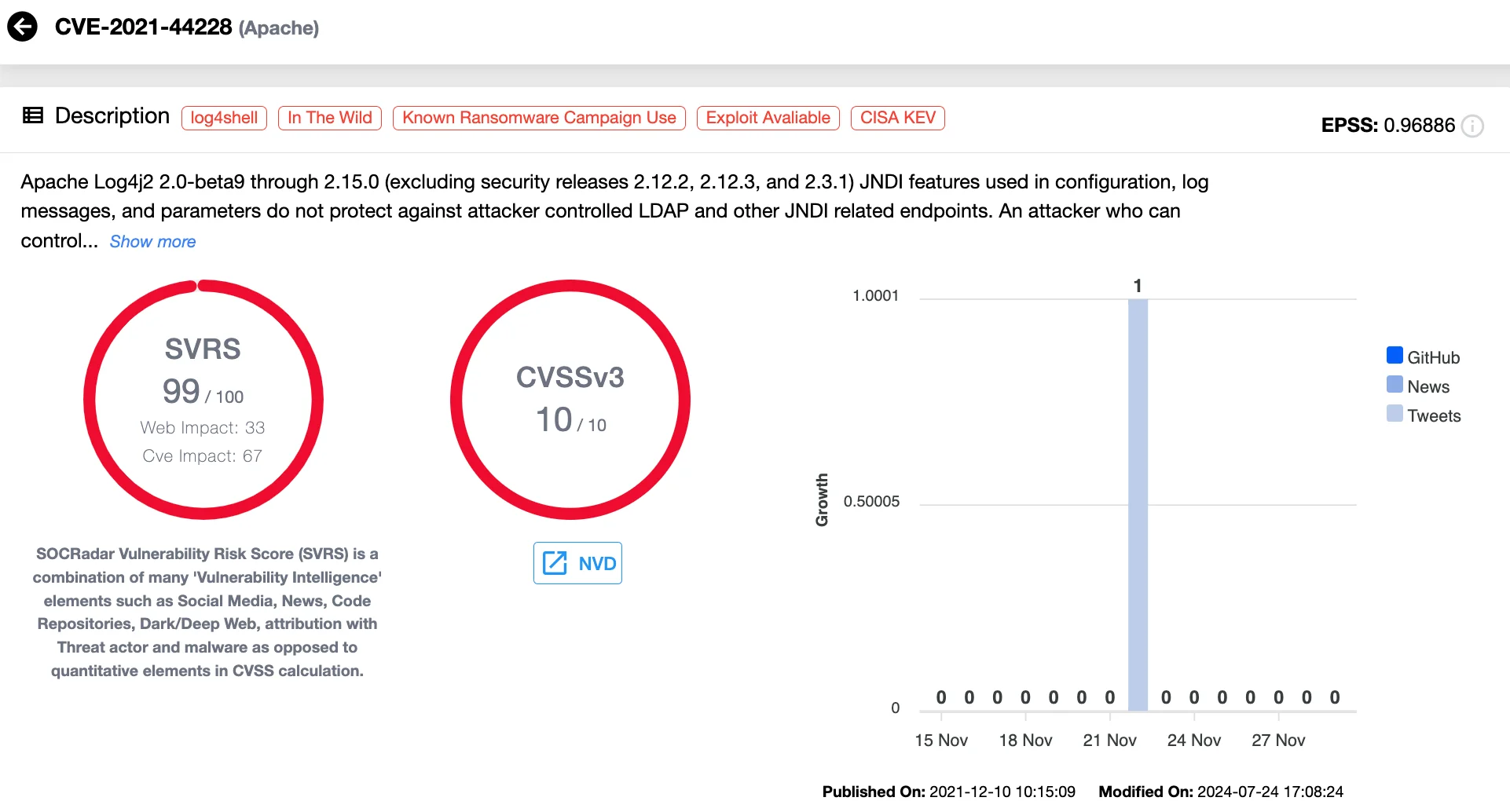
Details of CVE-2021-44228 (SOCRadar Vulnerability Intelligence)
Nation-state actors and cybercriminals have leveraged Log4Shell in various campaigns. A notable example includes its use in VMware Horizon systems, where attackers gained initial access and deployed malware. The widespread use of Log4j across industries magnified the impact, making Log4Shell one of the most exploited vulnerabilities globally.
9. CVE-2023-2868 (CVSS 9.8) Barracuda Networks ESG Appliance Improper Input Validation Vulnerability
CVE-2023-2868 is a critical zero-day vulnerability affecting Barracuda Networks’ Email Security Gateway (ESG) appliances. This flaw stems from improper parsing of TAR file attachments during email screening, allowing attackers to inject and execute system commands remotely.
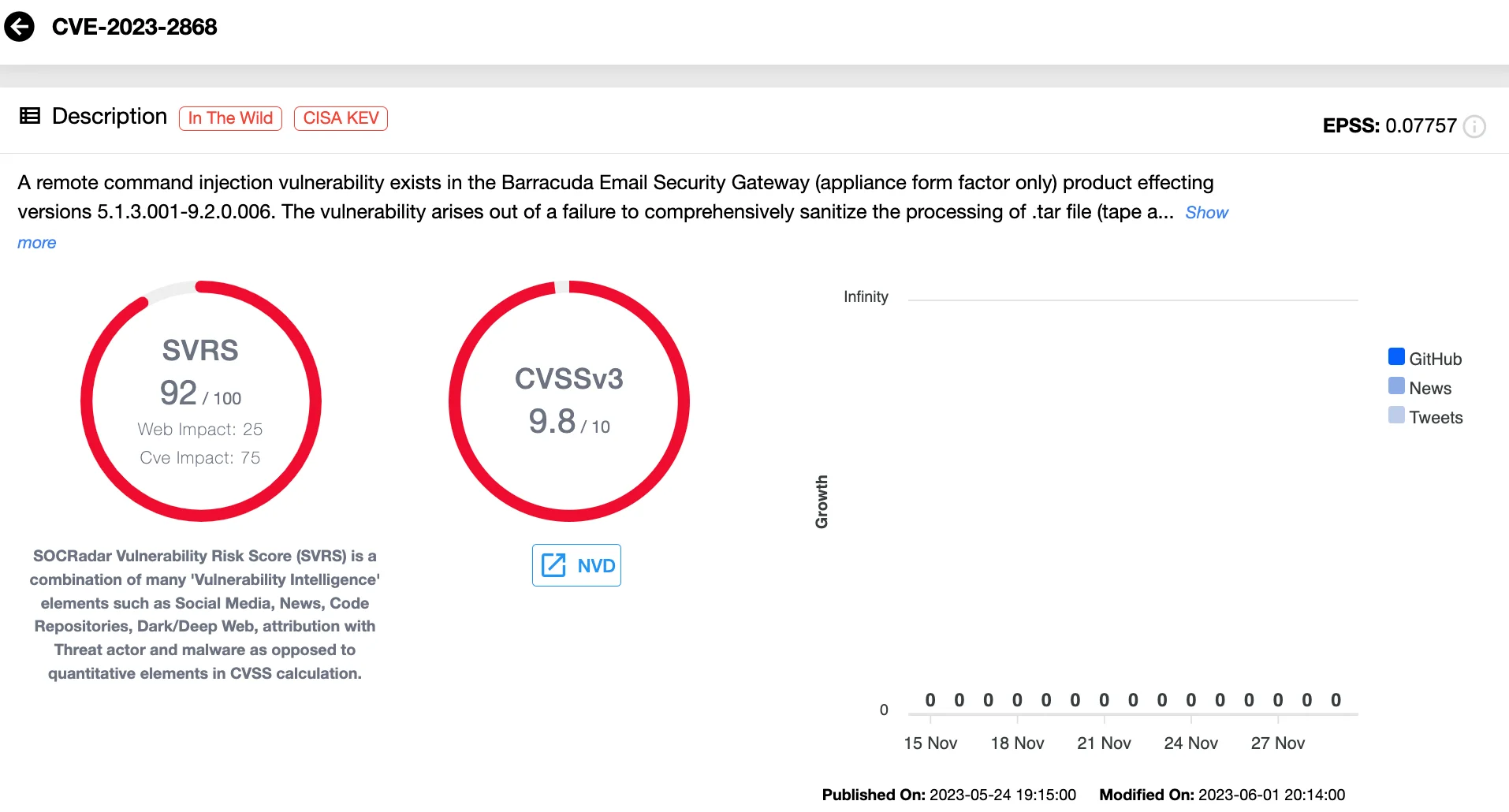
Details of CVE-2023-2868 (SOCRadar Vulnerability Intelligence)
In December 2023, the cyber espionage group UNC4841, assessed to be linked to the People’s Republic of China, exploited this vulnerability to deploy malware. By sending emails with specially crafted TAR file attachments, attackers triggered the flaw to install reverse shell backdoors, enabling persistent access to compromised systems. These attacks highlight the risks of unpatched vulnerabilities in email security solutions, particularly when exploited by sophisticated threat actors in cyber espionage campaigns.
10. CVE-2022-47966 (CVSS 9.8) Zoho ManageEngine Multiple Products Remote Code Execution Vulnerability
CVE-2022-47966 is a critical RCE vulnerability affecting several Zoho ManageEngine on-premise products. This flaw arises from the use of an outdated Apache Santuario library for XML signature validation, leaving systems vulnerable to exploitation. Attackers leveraged this vulnerability to target ManageEngine instances with SAML-based Single Sign-On (SSO) enabled, sending crafted requests to execute arbitrary code.
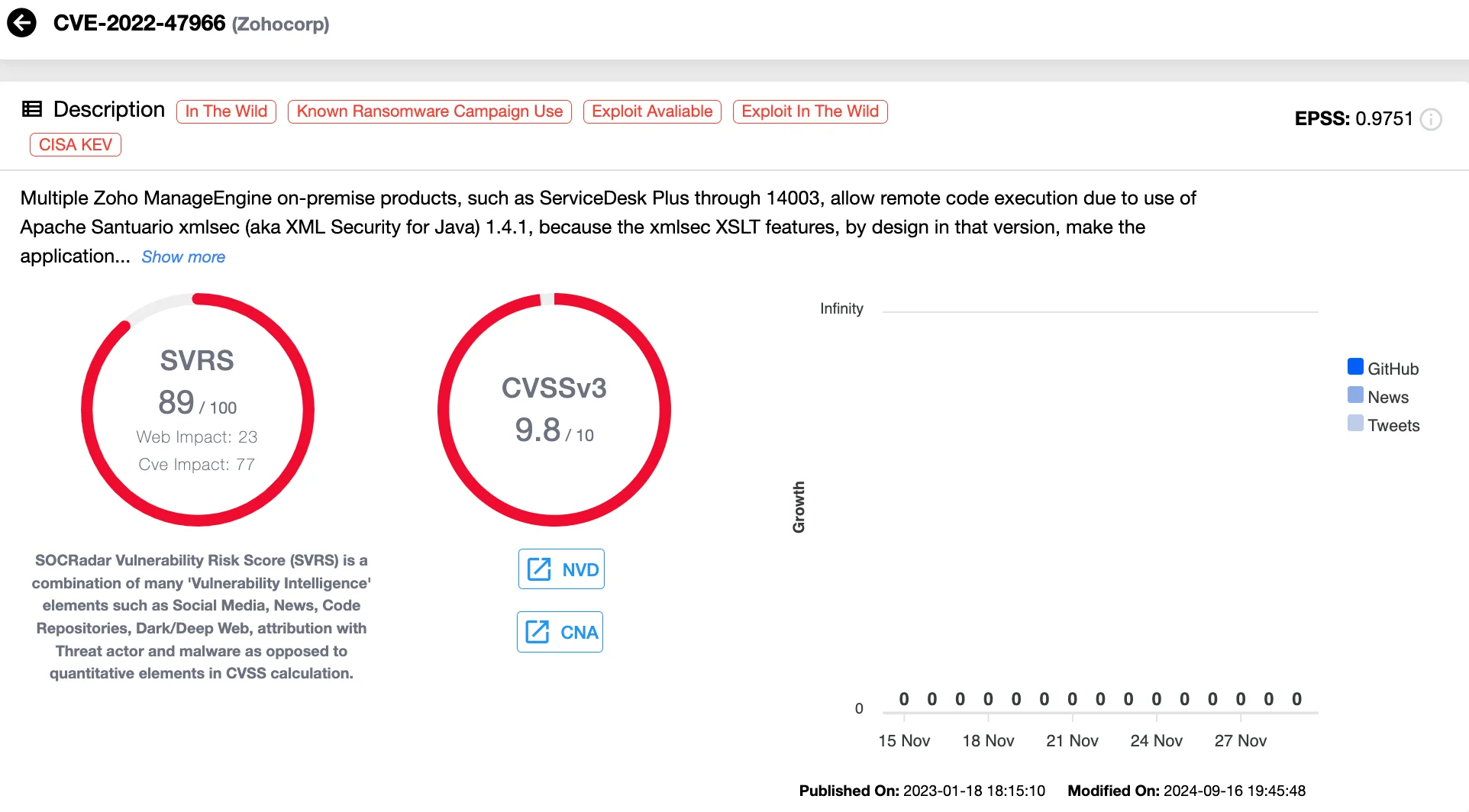
Details of CVE-2022-47966 (SOCRadar Vulnerability Intelligence)
Multiple nation-state Advanced Persistent Threat (APT) actors have been observed exploiting this vulnerability. For instance, in early 2023, APT groups targeted an aeronautical organization by exploiting CVE-2022-47966 to gain initial access to its web server hosting Zoho ManageEngine ServiceDesk Plus. These actors achieved root access, created local administrative accounts, and conducted further malicious activities within the network.
11. CVE-2023-27350 (CVSS 9.8) PaperCut MF/NG Improper Access Control Vulnerability
CVE-2023-27350 is a critical vulnerability in PaperCut MF and NG, widely used print management software. This flaw allows remote, unauthenticated attackers to bypass authentication and execute arbitrary code with system privileges. Attackers exploited this vulnerability to deploy malware, steal sensitive data, and establish persistent network access.
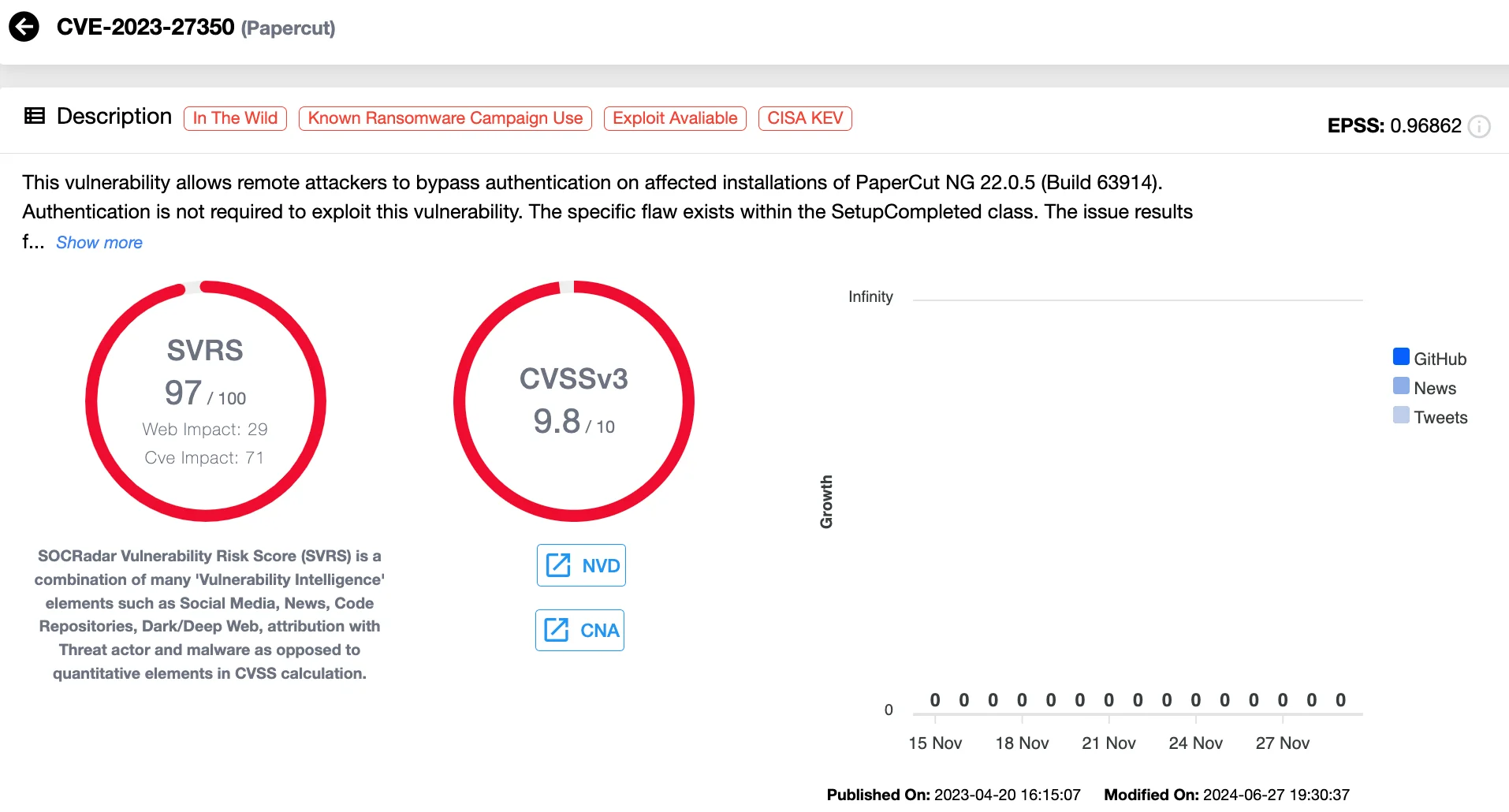
Details of CVE-2023-27350 (SOCRadar Vulnerability Intelligence)
Notable exploitation campaigns in 2023 include the Bl00dy Ransomware Gang targeting education facilities in mid-April, as well as attacks by Iranian state-sponsored groups Mint Sandstorm (Phosphorus, APT35) and Mango Sandstorm (Muddywater).
12. CVE-2020-1472 (CVSS 10) Microsoft Netlogon Privilege Escalation Vulnerability – Zerologon
Although disclosed in 2020, CVE-2020-1472, or “Zerologon,” remained one of the most exploited vulnerabilities in 2023. This privilege escalation flaw in Microsoft’s Netlogon Remote Protocol allows attackers to establish a secure channel connection to a domain controller, bypass authentication, and alter its password. Once exploited, attackers gain full domain administrator privileges, enabling them to add users, execute commands, and compromise entire networks.
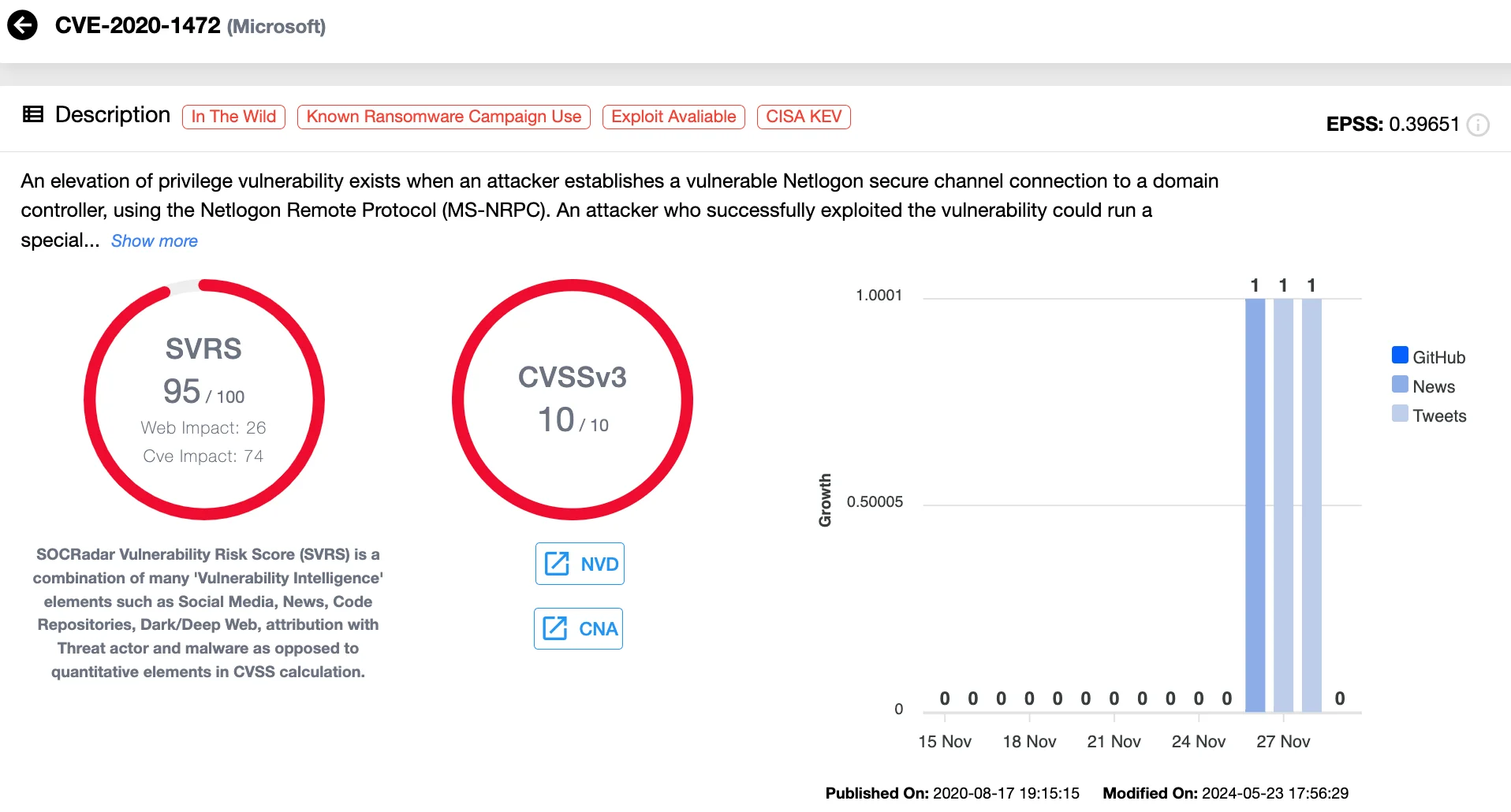
Details of CVE-2020-1472 (SOCRadar Vulnerability Intelligence)
Zerologon has been exploited by a range of actors, including Iranian state-sponsored groups, TA505 (CHIMBORAZO), and Ryuk ransomware operators. These attackers used the flaw to escalate privileges, exfiltrate sensitive data, and deploy ransomware. Its ongoing exploitation highlights the devastating potential of unpatched vulnerabilities in enterprise environments.
13. CVE-2023-42793 (CVSS 9.8) JetBrains TeamCity Authentication Bypass Vulnerability
CVE-2023-42793 is a critical authentication bypass flaw in JetBrains TeamCity, a popular continuous integration and delivery (CI/CD) platform. This vulnerability enables unauthenticated attackers with HTTP(S) access to execute arbitrary code on the TeamCity server, potentially gaining administrative control over the system. Exploiting this flaw allows attackers to escalate privileges, deploy backdoors, and maintain persistent access within compromised environments.
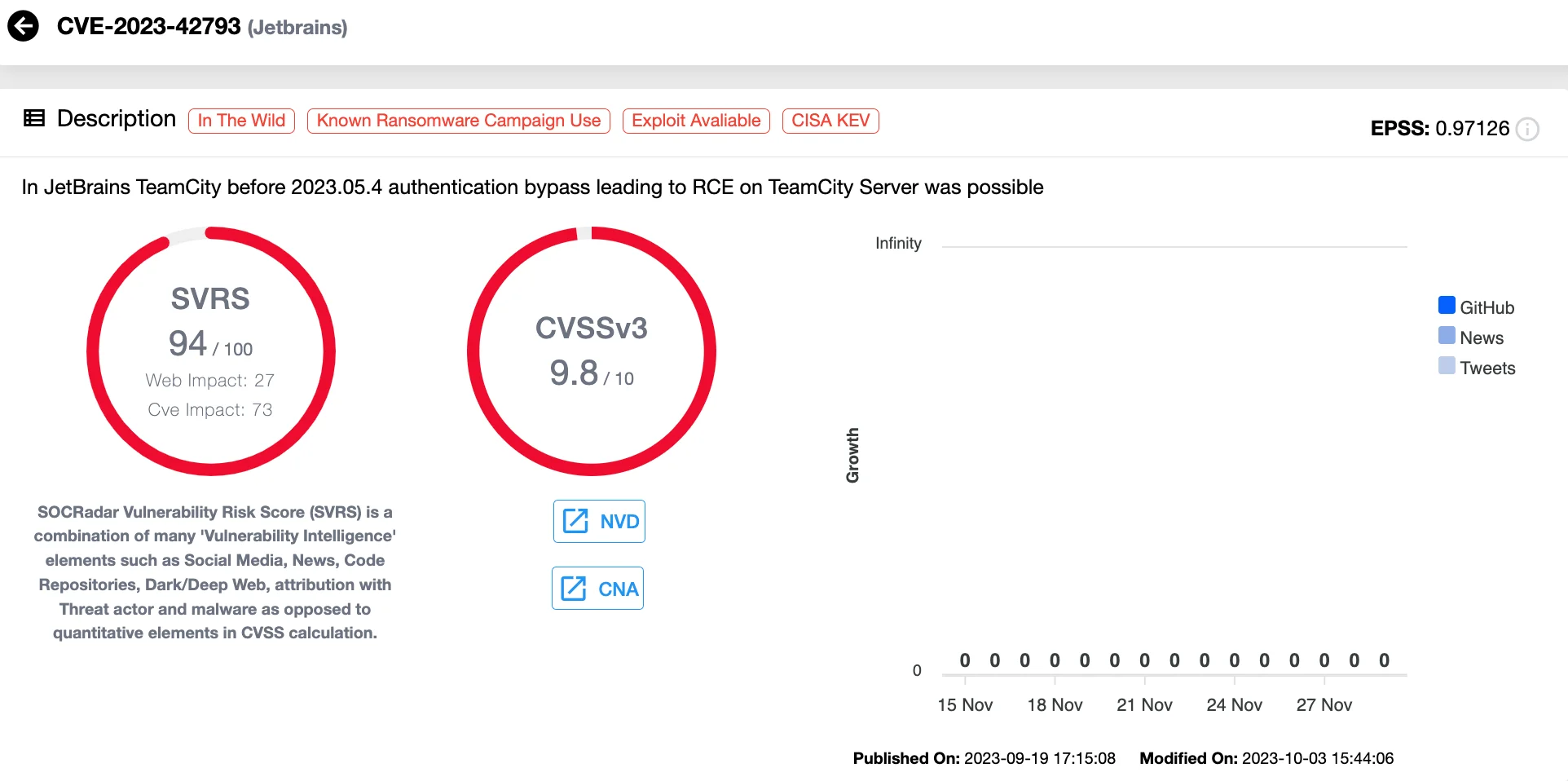
Details of CVE-2023-42793 (SOCRadar Vulnerability Intelligence)
State-sponsored actors have actively exploited this vulnerability since September 2023. Russian Foreign Intelligence Service (SVR), also known as APT29 or CozyBear, targeted TeamCity servers on a large scale, leveraging this flaw to infiltrate and persist in enterprise networks. Additionally, Microsoft identified North Korean threat groups Diamond Sleet and Onyx Sleet deploying malicious payloads through this vulnerability, further emphasizing its critical nature for organizations relying on TeamCity.
The interconnectedness of modern supply chains introduces significant risks, with attackers exploiting third-party vulnerabilities to infiltrate your organization. High-profile supply chain breaches like those affecting MOVEit Transfer or JetBrains TeamCity demonstrate how attackers target trusted vendors and tools to compromise multiple organizations.
What SOCRadar’s Supply Chain Intelligence delivers:
- Comprehensive Third-Party Monitoring: Tracks the cybersecurity posture of vendors, partners, and suppliers to uncover potential vulnerabilities.
- Early Threat Detection: Identifies risks, such as exposed credentials or dark web activity, linked to your supply chain.
- Vendor Risk Assessment: Provides real-time insights into third-party vulnerabilities that could threaten your operations.
Secure your supply chain before attackers exploit its weakest link. With SOCRadar, gain the visibility and control needed to protect your business from third-party risks.
14. CVE-2023-23397 (CVSS 9.8) Microsoft Office Outlook Privilege Escalation Vulnerability
CVE-2023-23397 is a critical vulnerability in Microsoft Outlook for Windows that attackers exploited to steal NTLMv2 hashes without user interaction. The Russian-based APT28 group, also known as Fancy Bear, exploited this vulnerability in targeted attacks against European government, transportation, energy, and military sectors. Their operations aimed to steal credentials and maintain access within compromised networks, highlighting the significant threat this flaw posed to critical industries.
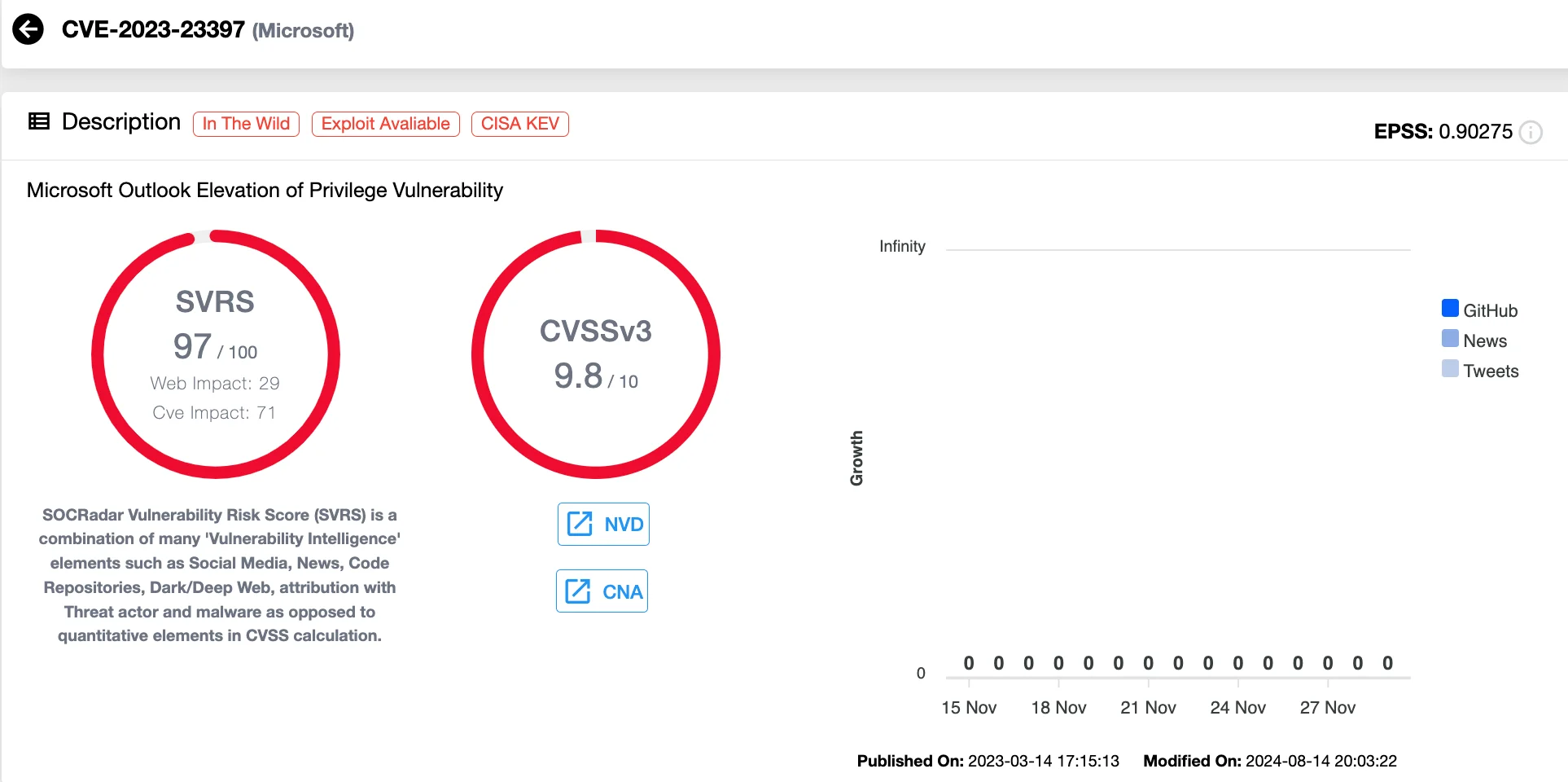
Details of CVE-2023-23397 (SOCRadar Vulnerability Intelligence)
By sending specially crafted emails with a UNC path in the PidLidReminderFileParameter property, attackers forced Outlook clients to connect to a malicious SMB server, automatically transmitting the user’s NTLMv2 hash. These hashes were then used to authenticate against other systems supporting NTLMv2 or cracked offline to extract credentials.
15. CVE-2023-49103 (CVSS 7.5) ownCloud graphapi Information Disclosure Vulnerability
Finally, an ownCloud vulnerability highlighted the risks of third-party libraries and insufficient deactivation measures. The last flaw in the Top 15 list, CVE-2023-49103, is a critical information disclosure vulnerability in the graphapi app of ownCloud.
This flaw allows unauthenticated attackers to retrieve sensitive configuration details, including environment variables containing admin credentials, mail server information, and license keys. The vulnerability stems from the third-party GetPhpInfo.php library, which exposes PHP configuration details.
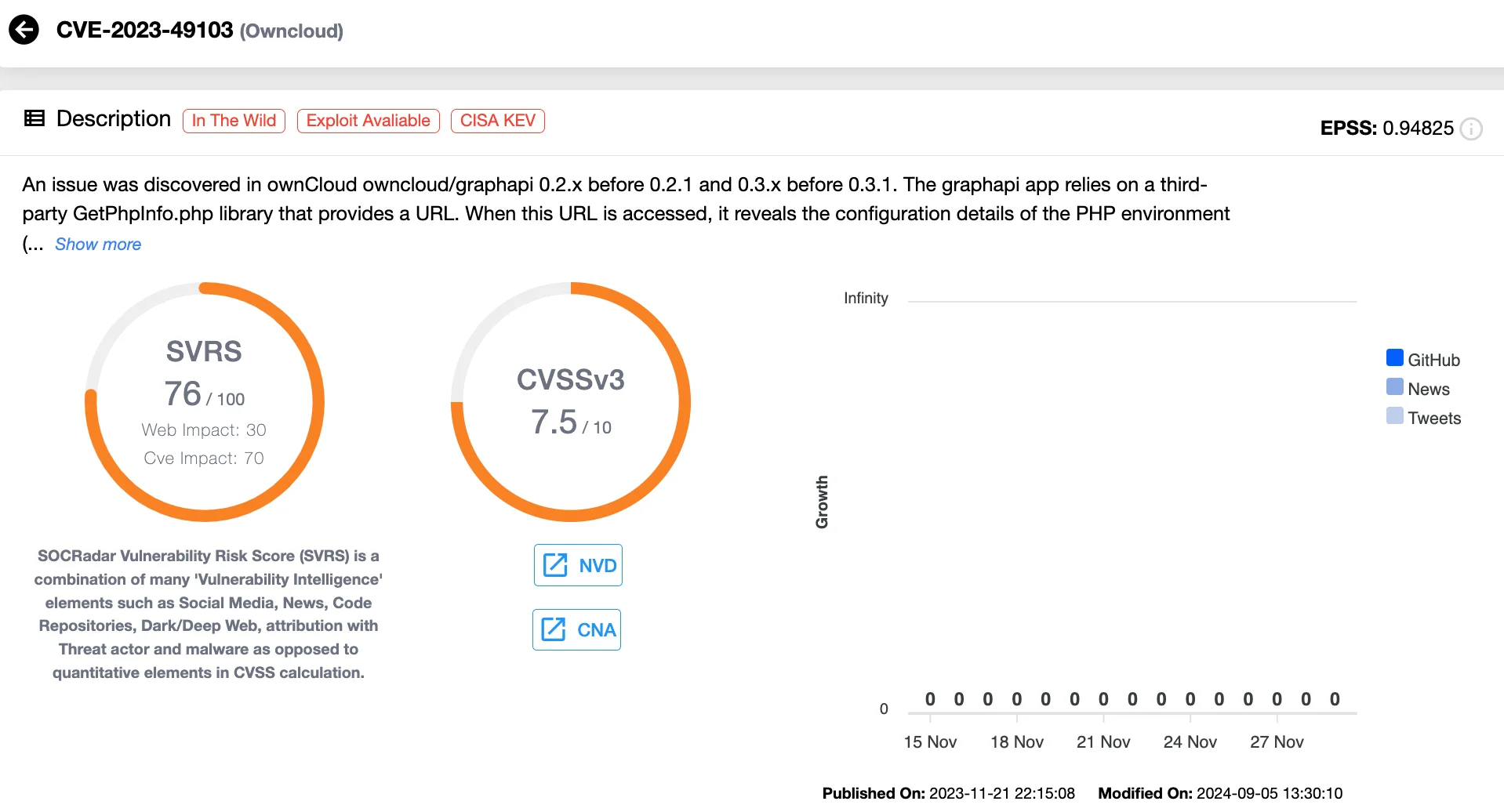
Details of CVE-2023-49103 (SOCRadar Vulnerability Intelligence)
Even disabling the graphapi app did not fully mitigate the risk, making this flaw a serious concern for ownCloud users. Exploitation attempts began in late November 2023, with attackers scanning for and accessing the vulnerable endpoint to extract sensitive data. While no specific threat actors have been attributed, the widespread and rapid exploitation indicates involvement from cybercriminal groups seeking to compromise ownCloud instances.
All in all, these 15 vulnerabilities are more than a historical record—they are a blueprint of attacker priorities and tactics. By analyzing these patterns, organizations can fortify their defenses and close the gaps attackers are most likely to exploit.
Additional Routinely Exploited Vulnerabilities
Beyond the top 15, the advisory highlights several other vulnerabilities that malicious actors routinely exploited in 2023. These vulnerabilities share common characteristics, such as improper access controls, insecure configurations, and a lack of input validation, which attackers leveraged to infiltrate networks and compromise systems.
Exploitation patterns varied but often included Remote Code Execution (RCE), privilege escalation, and authentication bypass attacks, reflecting the diverse tactics employed by cybercriminals. For instance, CVE-2022-47966 (Zoho ManageEngine) of the Top 15 demonstrated how outdated software libraries could expose organizations to root-level access attacks. Similarly, from the additional list of flaws, CVE-2021-22986 (F5 BIG-IP and BIG-IQ) enabled server-side request forgery (SSRF) attacks, allowing attackers to interact with internal systems and exfiltrate sensitive data.
Authentication bypass vulnerabilities, such as CVE-2023-35078 and CVE-2023-35081 in Ivanti Endpoint Manager Mobile, provided attackers unauthorized access and facilitated path traversal attacks, highlighting risks in endpoint management solutions. Additionally, the critical CVE-2019-0708 vulnerability in Windows, known as “BlueKeep,” persisted as a threat in 2023, emphasizing the dangers posed by unpatched legacy systems in Remote Desktop Services.
In another example, vulnerabilities like CVE-2023-38831 (WinRAR) and CVE-2021-34473 (Microsoft Exchange Server) facilitated code execution and SSRF attacks, respectively, showcasing the risks of delayed patching and insufficient security measures.
What Organizations Can Learn from the 2023 Exploitation Trends: 3 Key Lessons
The advisory highlights critical trends in how attackers exploit software vulnerabilities, offering actionable insights for improving cyber defenses. Here’s what 2023 exploitation trends teach us:

Key lessons from 2023 exploitation trends
1. Timely Patching and Prioritization is Key
Unpatched systems remain prime targets, as delays in applying updates leave organizations vulnerable to exploitation. Proactive patch management can close security gaps before attackers strike.
Additionally, not all vulnerabilities pose equal risks; prioritizing critical flaws like CVE-2023-20198 (Cisco IOS XE) and CVE-2023-2868 (Barracuda ESG) helps focus resources on the most exploitable threats. Tools that assess risk based on exposure ensure effective vulnerability management.
Leveraging tools that assess risk based on exposure and exploitability helps organizations allocate resources effectively and focus on vulnerabilities that matter most.
2. Global Cybersecurity Efforts Reduce Zero-Day Lifespans
Zero-days like CVE-2023-23397 (Microsoft Outlook) dominated 2023, but international collaboration has reduced their lifespan. Swift advisories for vulnerabilities like Log4Shell and MOVEit pressured organizations to patch faster, lowering the utility of zero-day exploits for attackers over time.
3. Evolving Threat Actor Strategies Demand Agility
Exploitation of vulnerabilities like CVE-2023-34362 (Progress MOVEit) and CVE-2023-42793 (JetBrains TeamCity) underscores attackers’ focus on supply chain and critical software components. This concludes that organizations must extend defenses to address third-party risks and secure supply chains.
By studying 2023 trends, businesses can adopt a proactive cybersecurity strategy, emphasizing timely patching, prioritization, and collaboration in global threat intelligence efforts to counter evolving threats.
Recommendations for Vendors, Developers, and End User Organizations
To address the routinely exploited vulnerabilities and trends highlighted in the advisory, stakeholders—vendors, developers, and end-user organizations—must adopt targeted measures, as explained below.
For Vendors and Developers
- Embed security into the software lifecycle with secure coding standards, regular code reviews, and static analysis to identify vulnerabilities early.
- Invest in early vulnerability testing. Use methods like fuzz testing, automated scans, and penetration tests during development to uncover exploitable flaws.
- Collaborate globally to expedite vulnerability identification, reporting, and resolution. Clear communication about patches further limits exploitability..
For End User Organizations
- Develop and enforce a patch management policy that ensures timely application of security updates. Tools like SOCRadar’s Attack Surface Management and Vulnerability Intelligence can help track digital assets and monitor for known vulnerabilities across your ecosystem.
SOCRadar’s Attack Surface Management module
- Conduct routine vulnerability scans to identify and prioritize unpatched systems. Implement automated solutions to streamline the process and reduce oversight risks.
- Monitor the Dark Web for potential threats. Threat actors often exploit stolen credentials or target organizations with unpatched systems. Tools like SOCRadar’s Dark Web Monitoring enable proactive detection of compromised data, helping your organization act before attacks escalate.
SOCRadar’s Dark Web Monitoring module
For Everyone
- Unify efforts between vendors, researchers, and organizations to swiftly patch and mitigate vulnerabilities. Shared intelligence and best practices can significantly reduce the lifecycle of zero-day exploits.
By implementing these strategies, all parties can contribute to a safer cybersecurity landscape, reducing the opportunities for threat actors to exploit critical vulnerabilities.
Looking Ahead – What 2025 Might Bring
The advisory for top routinely exploited vulnerabilities of 2023 highlights key insights into malicious actors’ strategies and gaps they continue to exploit. It reveals a rise in zero-day vulnerabilities and persistent targeting of unpatched systems, showing that threat actors favored exploiting vulnerabilities within two years of disclosure, particularly in widely used systems like Cisco IOS XE, Citrix NetScaler, and Microsoft Exchange.
Looking ahead, cybersecurity efforts must evolve in tandem with attacker tactics. Key areas of focus for 2025 include:
- Increased efforts in identifying and mitigating zero-day vulnerabilities will be critical. Leveraging advanced threat intelligence tools and global vulnerability sharing platforms will play a pivotal role in reducing their impact.
- Enhanced partnerships among nations and organizations, like the ones seen in this advisory, will be vital. Unified vulnerability disclosure and mitigation strategies can shorten the lifecycle of exploits and limit global threats.
- Routine exploitation of vulnerabilities affecting critical sectors highlights the need for stronger protections. Organizations must focus on securing supply chains, essential services, and enterprise systems from known attack vectors.
The joint cybersecurity advisory is a roadmap for proactive defense, offering actionable recommendations for vendors, developers, and organizations. Review the advisory, adopt its strategies, and implement tools like SOCRadar’s Extended Threat Intelligence (XTI) platform to stay ahead of emerging threats. By learning from 2023 and preparing for what’s ahead, your organization can fortify its defenses and contribute to a safer cyber landscape in 2025.






































