
APT Profile: FIN7
In the world of cybercrime, a name resounds with an unsettling echo – FIN7. This notorious cyber gang has left its mark on the globe, causing digital chaos wherever they go. By infiltrating countless businesses worldwide, they have stolen millions of dollars, taking advantage of vulnerabilities and spreading fear throughout industries.
Operating at a scale and sophistication that puts them comparable to state-sponsored threat actors, they’ve become a noteworthy danger.
Their modus operandi combines an array of innovative malware, targeted spear-phishing campaigns, and relentless persistence, making them a formidable adversary.
From billion-dollar digital heists to systematic breaches of high-profile companies, FIN7 has not only made headlines but also consistently challenged and rewritten the conventions of cybercrime. Their operations are as intricate as they are audacious, blending elements of espionage with masterful cybercriminal tactics.
As we dive into this shadowy realm, we’ll spotlight the FIN7 – their methods, targets, and tools in this article. But more than just a profile, this is a call to action, a strategy of defense. Knowledge is our most potent weapon in the ongoing war against cyber threats.
Who is FIN7?
FIN7 (Carbon Spider) is a sophisticated and financially-motivated cybercrime group. The group is believed to be Russian. The group has been active since at least 2013 and mainly aims to steal credit card information from businesses across various sectors.
Despite the arrests of several key members in 2018 by law enforcement agencies, the group continues to be active and dangerous, showing a remarkable ability to recover and adjust, which is both rare and concerning. They work in a structured way, similar to a corporate business, with a hierarchy of roles, a regular work schedule, and even bonuses for successful operatives.
Fact: Microsoft named and investigated FIN7 as Elbrus before, but after the firm changed its name taxonomy, FIN7’s new pseudonym from Microsoft has changed to Sangria Tempest.
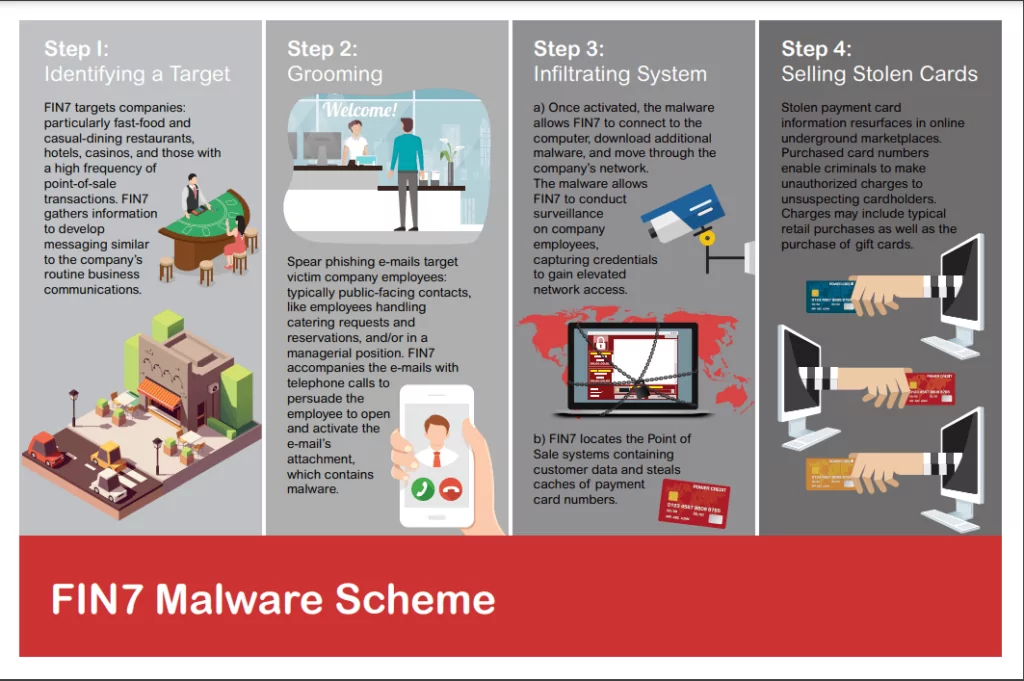
How Does FIN7 Attack?
FIN7 employs a variety of attack vectors to gain initial access to its target systems. These include:
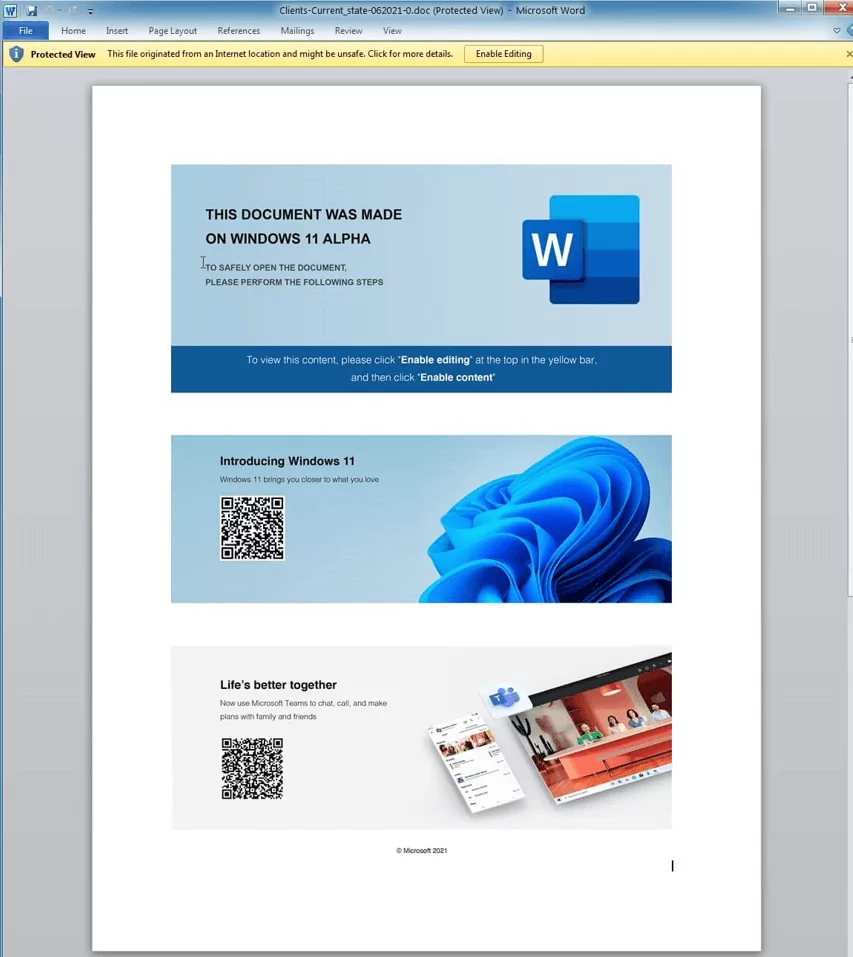
Spear-phishing: FIN7 typically starts its attacks by sending spear-phishing emails to its targets. These emails often include a malicious attachment, such as a Microsoft Word document or Excel spreadsheet, that contains a macro designed to exploit vulnerabilities in the recipient’s system. For example, the group has observed using CVE-2017-11882, which is known as “Microsoft Office Memory Corruption Vulnerability,” an Office (version 2007, 2010, 2013, and 2016) vulnerability that enables a hacker to execute any code they choose under the permissions of the current user. This is due to a failure in correctly managing objects stored in memory.
Initial Access and Lateral Movement: If a user opens the attachment and successfully executes the payload, it can give FIN7 initial access to the target’s network. From there, the group uses various tools and techniques to move laterally within the network, including using legitimate credentials they have managed to steal or crack.
Persistence: FIN7 uses various methods to maintain persistence within a compromised network. This can include the use of malware that’s designed to automatically reinfect systems after being cleaned out, as well as the creation of new user accounts that give them ongoing access.
Data Exfiltration: Once they have sufficient access and control over a target’s network, FIN7’s primary goal is typically to exfiltrate data. This often includes sensitive financial information, which the group can use for financial gain.
Use of Custom Tools: FIN7 is known for using various custom tools in its attacks. This includes the Carbanak backdoor, which allows them to remotely control infected systems, and various Point-of-Sale (POS) malware, which they use to steal credit card information from POS systems.
The group’s style of operation is marked by a detailed understanding of their targets’ internal processes. This allows them to execute very targeted attacks. Often pretending to be a vendor or customer, they can bypass traditional security measures using carefully crafted scam emails designed for the recipient’s role or sector.
Which Tools and Vulnerabilities Does FIN7 Use?
FIN7 is not just a user of advanced hacking tools, but they also create them. They’ve been found using and creating a variety of advanced harmful software and attack techniques.
Here are some noteworthy examples:
Carbanak: A sophisticated backdoor Trojan primarily used by FIN7 for espionage, data exfiltration, and providing remote control over infected systems.
Bateleur: This JScript backdoor provides extensive capabilities, including executing commands, taking screenshots, uploading, downloading, and executing files. Bateleur is delivered by legitimate-looking Outlook and Google documents.

Pillowmint: It is a type of malicious software designed to steal credit card details. It specifically targets and exploits point-of-sale (POS) systems. According to Trustwave, Pillowmint is like a monkey thief. It steals all the money from the victim and places it on one side, to be later collected by the FIN7.
BOOSTWRITE: It is a loader specifically designed to manipulate the DLL search order in applications that load the valid ‘Dwrite.dll’ from Microsoft DirectX Typography Services. Once initiated, DWrite.dll establishes a connection with a fixed IP and port, obtaining a decryption key and an initialization vector (IV) to decode two built-in payload DLLs.
BIOLOAD: This is another program used by the group that works similarly to the BOOSTWRITE tool. One of these extra features is a unique obfuscation mechanism for evading detection.
Astra Panel: This is a control center on the internet used for handling the SQLRat malware. The malware is used to run SQL scripts that can manipulate and steal data from a compromised system.
JSSLoader: This remote access trojan (RAT) provides the ability to execute commands, upload/download files, and perform data exfiltration.
Regarding vulnerabilities, the group is known to exploit both zero-days and known software vulnerabilities, often ones that remain unpatched in systems. They also exploit human vulnerabilities through effective social engineering tactics such as spear-phishing.
Adventures of FIN7
FIN7 has shifted its focus from financial institutions to ransomware attacks on large corporations since 2020. This strategy is known as big game hunting (BGH). This shift has increased the threat they pose to large organizations.
The group’s first BGH Campaign was using PINCHY SPIDER’s REvil ransomware in 2020. They introduced their own ransomware, the Darkside, later. This evolution shows the group’s increasing sophistication and the growing threat of ransomware attacks.
Darkside Ransomware: Darkside is a sophisticated ransomware that encrypts files and demands a ransom from the victim. Darkside follows the double-extortion method, which also threatens to leak stolen data if the ransom is not paid. This dual-threat approach increases the pressure on victims to pay the ransom and makes Darkside a particularly dangerous threat.
Darkside Ransomware-as-a-Service (RaaS): FIN7 operated Darkside as a RaaS, allowing other cybercriminals to use the ransomware in exchange for a portion of the ransom payment. This business model allowed FIN7 to profit from the attacks of others and increased the reach and impact of Darkside.
FIN7’s shift to BGH and the development of Darkside showed the group’s adaptability and the evolving threat of cybercrime. The group’s ability to change tactics and develop new tools highlighted the ongoing challenge of combating cybercrime.
Colonial Pipeline: FIN7 was involved in the ransomware attack on the U.S. oil pipeline system Colonial Pipeline in May 2021. The group claimed to be apolitical and stated that their goal was to make money, not create societal problems. This incident brought significant attention to the group and highlighted the potential impact of their attacks. After that incident, they announced that their ransomware service and the affiliate program were discontinued.
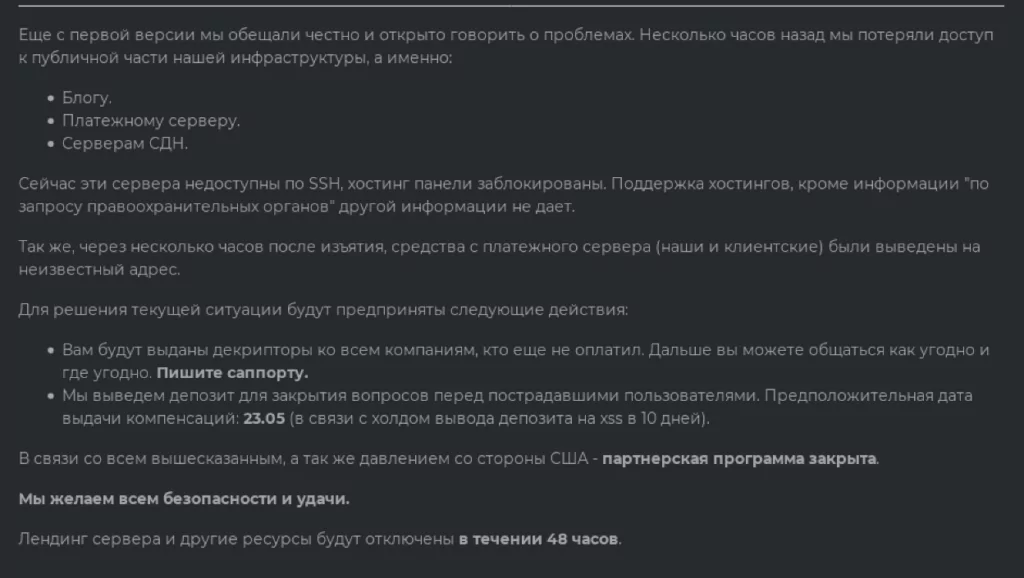
After the termination of Darkside, FIN7 continued its operations using different tools and techniques, including SQL injection and malicious Microsoft Excel and Word documents. This adaptability showed the group’s ability to evolve its methods in response to changing circumstances one more time.
BlackMatter: In July 2021, a new RaaS program showed up, the BlackMatter. BlackMatter has extensive coding similarities with Darkside, indicating that it is likely the successor to Darkside. The introduction of BlackMatter suggests that FIN7 remains a significant threat despite the termination of Darkside.
FIN7 has also been linked to the deployment of the Black Basta, BlackCat (ALPHV), and ClopRansomware.
What are the Targets of FIN7?
FIN7 has a wide target range across various sectors, mainly focusing on the retail, restaurant, and hospitality industries. Their victims are usually large-scale businesses, sometimes even multinational corporations.
Target Sectors of FIN7
- Finance
- Retail
- Telecommunications
- Government
- Energy
- High-tech
- Education
- Hospitality
- Business Services
- Construction
- Restaurants
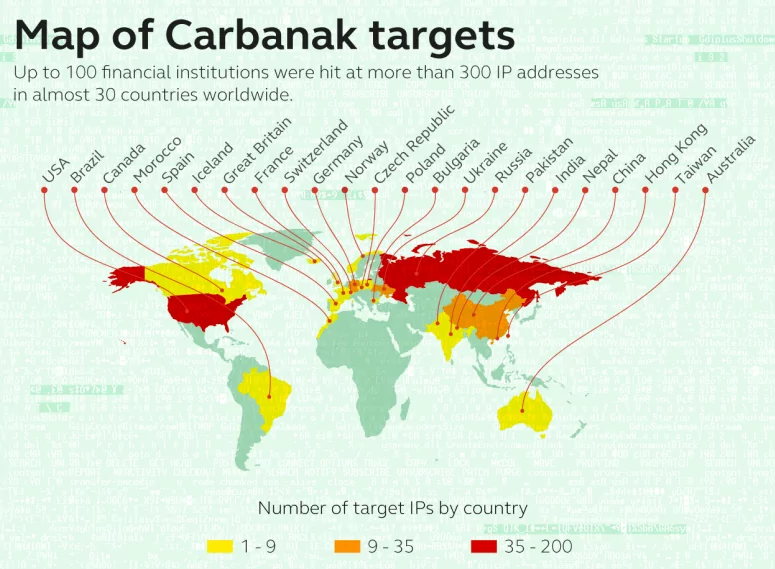
Target Countries of FIN7
The geographic spread of their targets is global, with operations seen in the United States, Europe, and even parts of Asia. However, they’ve been notably active in the United States, where they’ve caused substantial financial and data losses to many businesses.
The countries targeted by FIN7 may be chosen based on several factors. These include the opportunity for financial gain, the presence of suitable targets, or the regulatory and cyber defense situations in those countries.
Notable victims of FIN7 include:
Chipotle Mexican Grill: A major data breach in 2017 affected most of its restaurants, leading to the theft of customer card data.
Arby’s: A fast-food chain that had more than 350,000 payment cards compromised in a malware attack attributed to FIN7.
Saks Fifth Avenue and Lord & Taylor: These high-end retailers were affected by large-scale credit card data theft.
Attribution and Connections between Other Groups
Attributing cyber attacks to specific threat actors can be an extremely complex task. This is due to these groups’ ability to hide their tracks, use deception techniques, and share certain tools or malware. However, a detailed analysis of tactics, techniques, and procedures (TTPs) can often provide strong evidence of who is responsible.
FIN7 has been linked to several other threat groups, most notably the Carbanak group (also known as Anunak). While initially considered to be separate entities, evidence collected by several cybersecurity firms, such as similarities in their TTPs and shared use of the Carbanak malware, suggests a close relationship or possible overlap between the two.
Furthermore, there have been connections drawn between FIN7 and a financially motivated threat actor group known as “Magecart Group 5“. Magecart 5, responsible for attacks on large-scale eCommerce platforms, was found to use a domain that has previously been used by Carbanak/FIN7 in their operations, suggesting potential collaboration or shared resources.
However, while these connections suggest a level of cooperation or shared identity, it’s important to note that the dynamic nature of cybercriminal operations means relationships between groups can change and have many aspects. For example, a threat actor might sell or share tools with another, or one group might split into several smaller factions, each with a different focus or methodology.
In addition, recent research findings have linked FIN7 to the Clop ransomware attacks. Clop, known for its disruptive ransomware campaigns that particularly target Microsoft products, has caused significant damage in the cybersecurity landscape. The connection suggests that FIN7 might be expanding its arsenal of cyberattacks, further emphasizing the necessity for organizations to strengthen their defenses.
Notable Attacks of FIN7
FIN7 continues to carry out sophisticated and far-reaching cyberattacks. Several recent operations stand out due to their scale, methodology, or targets.
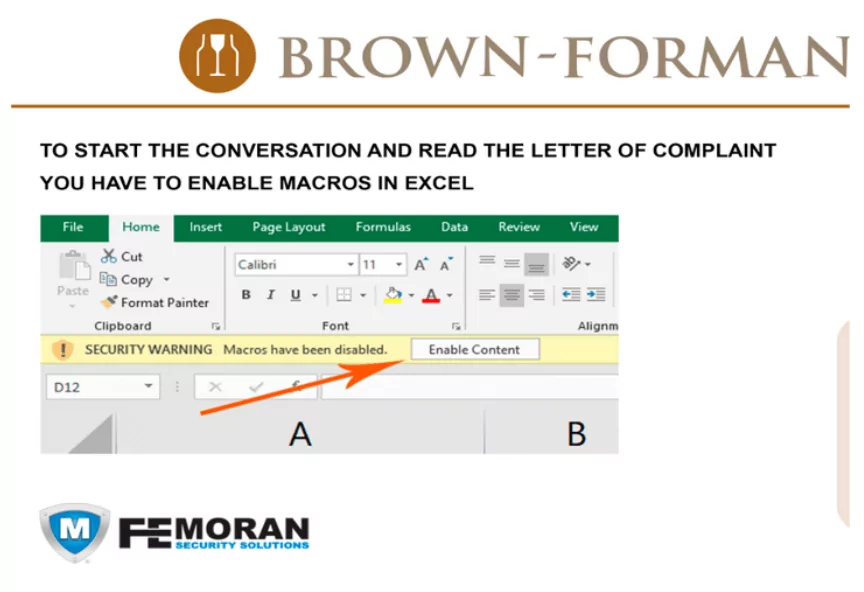
Attack Disguised as Brown-Forman Inc.
In June 2021, FIN7 attacked a law firm with a fake complaint that appeared to belong to Brown-Forman Inc., a prominent American company in the wine and spirits industry known for Jack Daniels whisky. This deceptive complaint served as bait to trick a law firm into downloading a version of the JSSLoader Remote Access Trojan (RAT) that was hidden within an Excel file attachment.
Clever Phishing Lure in the Form of a Gift Card Exchange
In 2020, one of its attacks, FIN7 sent out physical letters purportedly from Best Buy, with a $50 gift card and a USB drive, claiming to contain a list of items to spend on. The USB was identified as a “BadUSB Leonardo USB ATMEGA32U4” device, programmed to emulate a USB keyboard, allowing it to automatically inject malicious commands once plugged in.

Exploiting Veeam Vulnerability
A recent report highlighted FIN7’s targeting of Veeam servers. The group has been seen exploiting a vulnerability (CVE-2023-27532) in the Veeam Backup & Replication software. Using a PowerShell script, Powertrash, the group deployed a backdoor called Diceloader to perform various post-exploitation operations. The attacks involved the theft and exfiltration of credentials, network reconnaissance, and lateral movement within the compromised systems.
These incidents underline the group’s ability to adapt and its persistence. Despite multiple arrests, the group continues to operate, changing tactics and targets as necessary to achieve its objectives.
Conclusion
FIN7 is a sophisticated cybercrime group active since at least 2013. Their operations, marked by a high level of sophistication and persistence, have led to losses in the billions for companies worldwide. Their wide range of attack methods, ranging from spear-phishing to exploiting software vulnerabilities, combined with their extensive use of custom-made malware, shows their technological skill and adaptability.
The group has shown an ability to evolve and adapt in the face of challenges, such as arrests and cybersecurity developments. Their targets include multiple industries, particularly those dealing with financial transactions or possessing sensitive data, which they exploit for monetary gain. Despite significant efforts by law enforcement and cybersecurity organizations, FIN7 continues to be a significant threat to global cybersecurity.
Security Recommendations Against FIN7
To defend against a threat actor as sophisticated and persistent as FIN7, a multi-faceted approach is needed:
- Education and Awareness: Given that FIN7 often starts its attack through spear-phishing, employees must be trained to recognize and respond appropriately to suspicious emails. This includes not clicking on unknown links, not opening unexpected attachments, and being wary of unsolicited requests for sensitive information. In addition, with the rising physical attacks from removable devices like USBs carrying malware, employees should also be educated about the risks associated with using untrusted external storage devices. They should be instructed to avoid using any unknown or suspicious removable devices and to report any such devices found within the organization’s premises.
- Regular Patching and Updates: Since FIN7 is known to exploit known vulnerabilities, it’s critical to regularly update and patch all systems, applications, and infrastructure. This reduces the risk of an attack via unpatched software vulnerabilities.
- Endpoint Security: Implementing robust endpoint security solutions can help detect and prevent malware infections. Solutions should be capable of detecting both known malware types and unusual behavior indicative of zero-day threats.
- Network Monitoring: Constant monitoring of network traffic can help in detecting suspicious activities. In the case of FIN7, unusual outbound traffic or connections to known malicious IPs should pound the alarm.
- Incident Response Plan: Prepare for a potential breach by having a strong incident response plan in place. This plan should include steps to identify, isolate, and fix infections and to notify the appropriate parties (including law enforcement) as needed.
- Threat Intelligence: Stay informed about the latest tactics, techniques, and procedures (TTPs) used by FIN7 and other threat actors. Cybersecurity organizations and vendors often provide this information, which can be crucial in adjusting your defense strategies.
The sophistication and persistence of FIN7’s operations are a stark reminder of the evolving nature of cyber threats. It underlines the importance of staying ahead in the cybersecurity game, requiring businesses to not only invest in advanced security measures but also in creating a culture of security awareness within the organization.
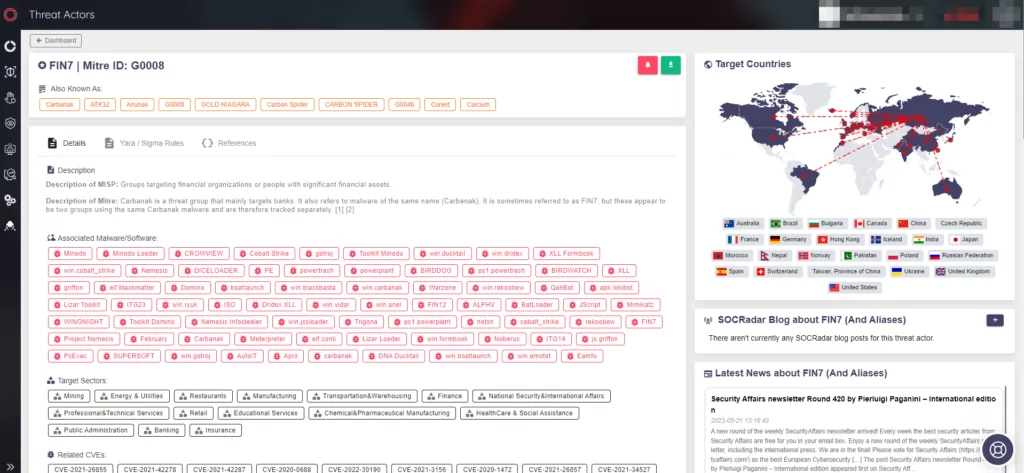
With SOCRadar, organizations can ensure that their cyber defenses are always updated and ready to deal with evolving threats like FIN7.
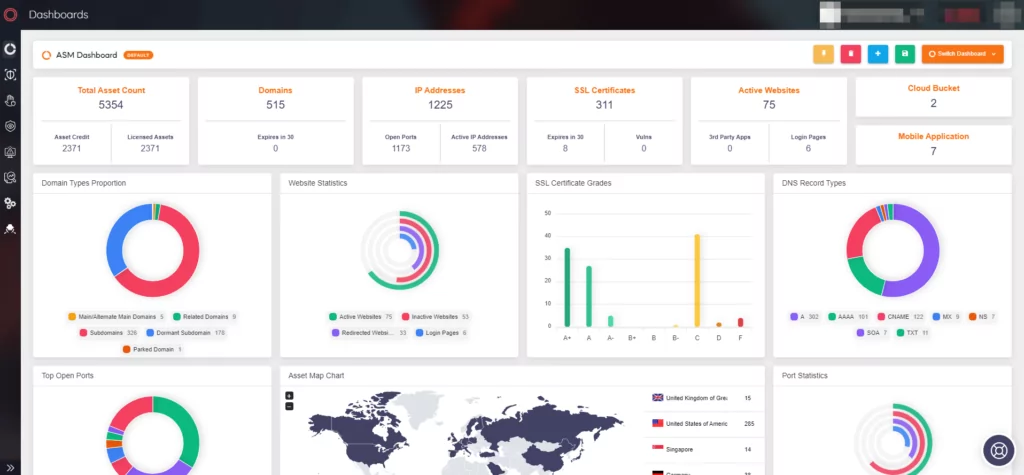
Attack Surface Management: SOCRadar’s ASM continuously identifies, maps, and monitors an organization’s digital footprint from an attacker’s perspective, helping organizations understand their online exposure. It can discover forgotten, unknown, or rogue digital assets, vulnerabilities, and misconfigurations, providing crucial intelligence to minimize the exploitable attack surface.
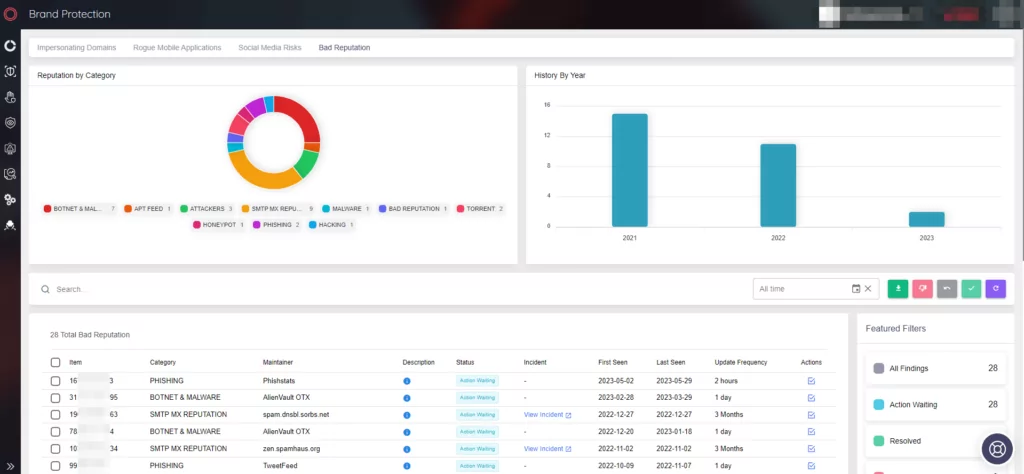
Digital Risk Protection: With FIN7’s diverse attack vectors, having a proactive digital risk protection tool is essential. SOCRadar’s digital risk protection services can help identify potential threats, security vulnerabilities, and fraud attempts that groups like FIN7 may exploit.
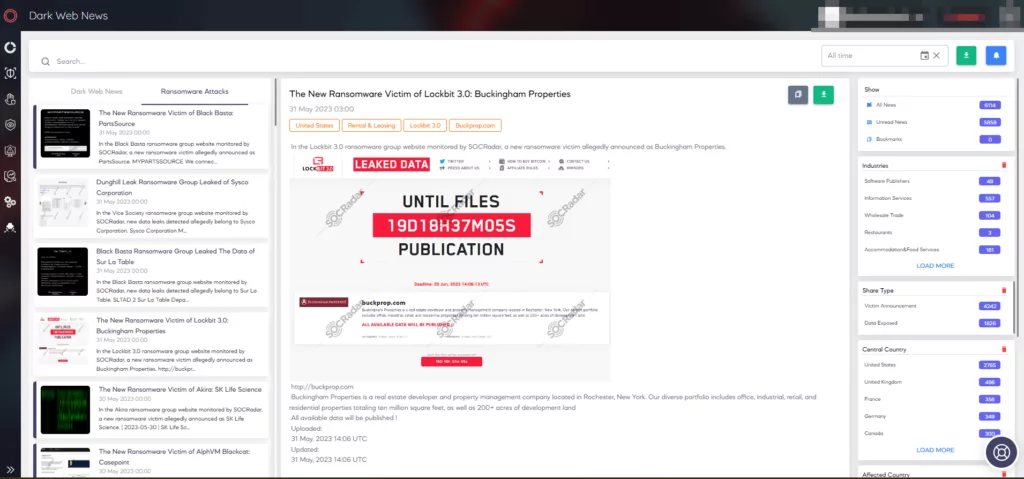
Dark Web Monitoring: SOCRadar’s Dark Web Monitoring can identify if any of the organization’s sensitive data has been compromised and shared on Telegram, dark web forums, etc. This is particularly relevant as FIN7 has been known to steal and sell sensitive data.
MITRE ATT&CK TTPs Used by FIN7


































