
Verizon 2025 DBIR: 10 Takeaways You Should Know
Verizon 2025 DBIR (Data Breach Investigations Report) dissects over 22,000 cyber incidents and 12,000 confirmed breaches to reveal the latest breach trends and attacker methodologies. The report highlights shifts in attacker behavior, exploitation techniques, and organizational vulnerabilities. This year’s data reflects a continued rise in ransomware, an uptick in vulnerability exploitation, especially on edge devices, and the growing threat of credential theft through infostealers and social engineering tactics. Whether you’re part of a global enterprise or an SMB, these insights are essential to understand the risks that are most likely to impact your organization.
In this blog post, we will unpack the top 10 takeaways from Verizon 2025 DBIR, each backed by key statistics, trends, and real-world implications. From the resurgence of espionage campaigns to the role of unpatched systems and the expanding threat from insider misuse, every point connects to broader questions of detection, prevention, and resilience.
How Attack Patterns Shifted Since Last Year
Before we get into the top insights from the 2025 Verizon DBIR, here’s a quick look at how breach patterns evolved compared to the previous year.
| Breach Pattern | 2024 | 2025 |
| System Intrusion | 36% | 53% |
| Miscellaneous Errors | 25% | 12% |
| Social Engineering | 22% | 17% |
| Basic Web App Attacks | 9% | 12% |
| Privilege Misuse | 8% | 6% |
Looking at the table above, it’s clear that System Intrusion has taken the lead among breach patterns, marking a significant jump from last year. This suggests attackers are increasingly relying on multi-step campaigns involving hacking, malware, and ransomware. At the same time, the decline in Miscellaneous Errors and Privilege Misuse may point to improved internal safeguards or simply a pivot in attacker strategies. Moreover, despite slight shifts, Social Engineering and Basic Web App Attacks continue to persist, emphasizing the ongoing challenges of credential misuse and phishing across all sectors.
Want to dive deeper into the key findings and what they mean for your organization? Join our live webinar “Verizon DBIR 2025 De-mystified – Brutal Truth & Insights” happening April 30, from 09:00 to 10:00 AM [ET]. Register here.

Join us live in Verizon DBIR 2025 De-mystified webinar
1. Vulnerability Exploitation Surges Toward Credential Abuse Levels
According to the 2025 DBIR, 20% of breaches now begin with the exploitation of vulnerabilities, showing a 34% increase over last year. This attack vector is quickly catching up to credential abuse, which remains the leading initial access method.
A major driver of this growth is the aggressive targeting of edge devices and VPNs. These accounted for 22% of vulnerability exploitation actions, up from just 3% in the previous report, a nearly eightfold increase. Despite patching efforts, it was found that only 54% of these vulnerabilities were fully remediated throughout the year, with a median time to patch of 32 days.
The report also ties many of these exploitations to ransomware campaigns and nation-state espionage. With zero-days increasingly weaponized against public-facing infrastructure, organizations without proactive patch management are being left dangerously exposed.
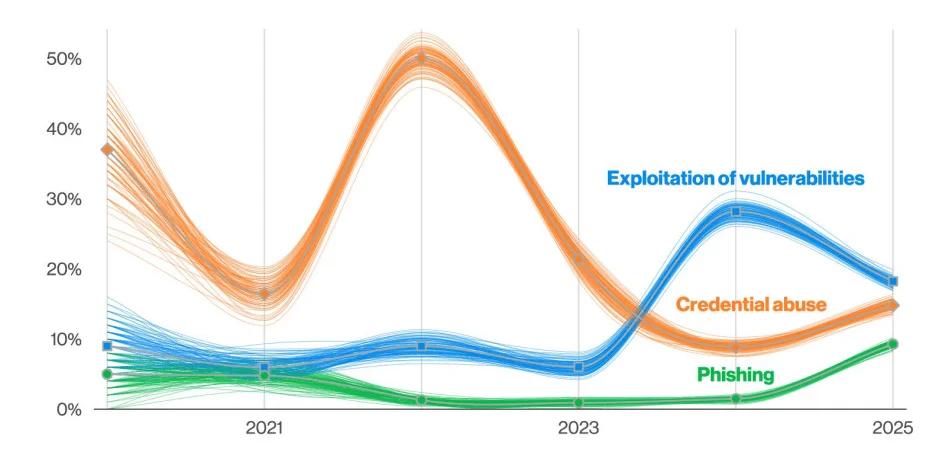
Initial access vectors in ransomware breaches (Verizon 2025 DBIR)
2. Credential Abuse and Infostealer Malware Fuel Breaches
Stolen credentials remain a dominant initial access vector in cyberattacks, leveraged in 32–33% of breaches across both large enterprises and SMBs. Verizon 2025 DBIR reveals just how intertwined the credential economy has become with malware and ransomware operations.
A surge in infostealer malware, which harvests credentials, cookies, and VPN details, has fueled a growing underground marketplace. These credentials often end up in:
- Marketplaces and premium channels, where buyers can search logs by domain
- Live logs, offering near real-time access to fresh infections
- Free samples shared in forums or on Telegram to attract buyers
Verizon 2025 DBIR shows that 54% of ransomware victims had their domains appear in stealer logs, with 40% including corporate email addresses – a clear sign of access broker involvement. Many of these logs included credentials to internal systems like GitHub, cloud portals, or remote access platforms.
Worryingly, 30% of infostealer-infected systems were enterprise-licensed devices, but 46% were unmanaged, typically personal machines used in Bring Your Own Device (BYOD) scenarios. This blend of corporate and personal use introduces dangerous gray areas in enforcement and response.
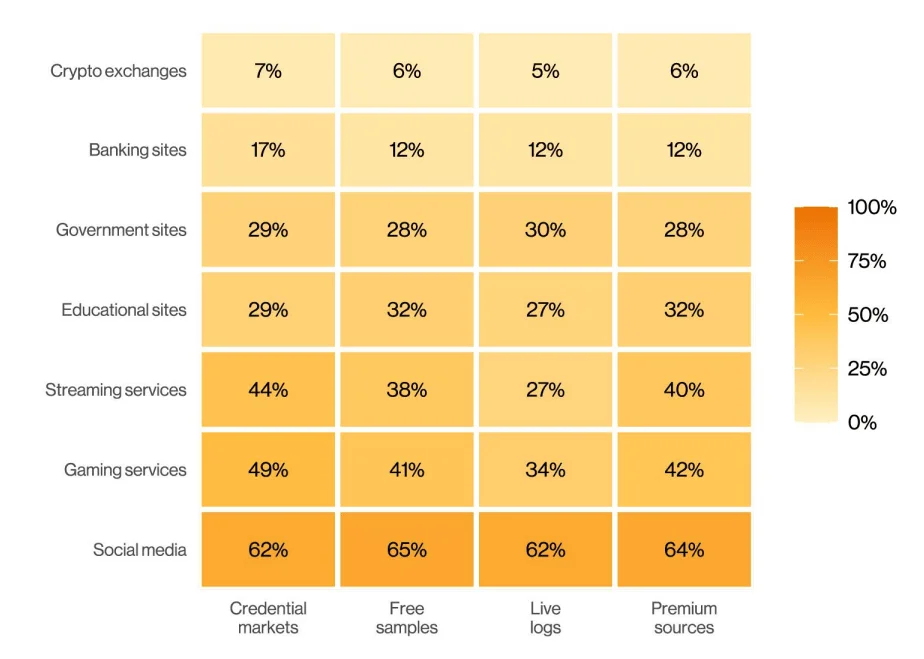
Types of website credentials in stealer logs (Verizon 2025 DBIR)
Overall, credential abuse is still the easiest way in. Today, hackers don’t hack, they log in. When attackers can simply use stolen credentials instead of breaking through defenses, organizations must prioritize credential hygiene, stealer log detection, and continuous Dark Web monitoring – or risk giving attackers a silent key to the front door.
SOCRadar’s Dark Web Monitoring and Threat Actor Intelligence modules give you the power to detect compromised credentials early, track ransomware operators targeting your brand, and disrupt attacks before they escalate. Secure your organization’s presence where attackers operate, before they strike.
SOCRadar XTI, Dark Web Monitoring
3. Ransomware Remains a Massive Threat, but Payment Trends Shift
Ransomware continues to dominate the cyber threat landscape, appearing in 44% of all breaches in Verizon’s 2025 DBIR – a sharp rise from 32% the previous year. Attackers are increasingly targeting small and medium-sized businesses, where ransomware was involved in a staggering 88% of breaches, compared to 39% in large organizations.
However, the financial dynamics around ransomware show signs of change. The median ransom payment has dropped to $115,000, down from $150,000 in the previous year. Moreover, 64% of victim organizations chose not to pay, up from 50% two years ago. These shifts may suggest that organizations are better prepared for ransomware incidents through stronger backups and recovery plans, or that they are less trusting of threat actor promises.
Even as payment trends evolve, ransomware actors remain aggressive. Tactics like double extortion, supply chain infiltration, and rapid exploitation of newly disclosed vulnerabilities continue to drive successful attacks.
4. SMBs Bear the Brunt of Ransomware and Malware Attacks
The 2025 DBIR makes it clear: small and medium-sized businesses (SMBs) are disproportionately impacted by ransomware and malware threats. SMBs accounted for nearly four times as many breaches compared to large organizations, highlighting how cybercriminals have widened their target scope beyond just big enterprises.
Ransomware was a defining factor, appearing in 88% of SMB breaches versus 39% in larger companies. Malware-related breaches were also significantly more common among SMBs. This trend likely stems from limited cybersecurity resources, slower patching, and less robust backup and recovery systems, making smaller companies attractive targets for attackers seeking quicker payouts.
Verizon’s findings dismantle the lingering myth that SMBs are too small to be targets. Attackers have adapted, scaling their demands based on victim size and exploiting weak defenses wherever they find them.
For SMBs, the focus should now be on strengthening endpoint protections, maintaining frequent offline backups, enforcing Multi-Factor Authentication (MFA), and investing in continuous monitoring to detect early signs of ransomware infections.
Maintaining strong backup strategies, rapid patching practices, and enhanced detection around initial access vectors like credential abuse and stolen VPN access are critical. But staying ahead of ransomware and vulnerability exploitation requires more than quick patching. It demands continuous, proactive visibility into your digital footprint.
SOCRadar’s Vulnerability Intelligence
With SOCRadar’s Attack Surface Management and Vulnerability Intelligence solutions, your organization can monitor exposed assets, spot emerging vulnerabilities early, and prioritize the threats that truly matter. Don’t let attackers find weaknesses before you do. Map, monitor, and defend proactively.
5. Espionage-Motivated Breaches Are Rising
While financially motivated attacks still dominate, the 2025 DBIR highlights a notable rise in espionage-driven breaches, which now make up 17% of all analyzed cases, up significantly from previous years. These intrusions were largely enabled through exploitation of vulnerabilities, which accounted for 70% of initial access vectors in espionage incidents.
State-sponsored actors showed a broadening of intent. Although data theft for intelligence purposes remains their primary goal, 28% of espionage-linked breaches were also financially motivated, suggesting some threat actors are “double-dipping” to monetize their access.
The healthcare and public sector industries were notably affected, with espionage appearing in 16% and 29% of breaches in those verticals, respectively. Attackers favored techniques such as lateral movement over internal networks, credential theft, and use of legitimate remote access tools to maintain stealth.
This shift signals a need for organizations to not only defend against ransomware but also prepare for stealthier, longer-dwell-time attacks. Continuous vulnerability management, segmentation, and monitoring for abnormal access behavior are critical to identifying such threats early.
6. Social Engineering Adapts: Prompt Bombing and Advanced BEC Tactics
Social engineering remains a top tactic, present in 17% of breaches, but the techniques are evolving. While phishing continues to dominate, the Verizon 2025 DBIR highlights a growing use of prompt bombing – a method where attackers flood users with MFA requests to wear down their resistance. Among social engineering breaches involving MFA bypass attempts, prompt bombing was the most common technique, appearing in over 20% of those cases.
Pretexting and BEC (Business Email Compromise) scams also continue to mature. Attackers build trust over weeks or months using social platforms, email threads, and even video calls, ultimately convincing victims to transfer funds or share sensitive data. The median loss per BEC incident now sits around $50,000, based on FBI IC3 reports.
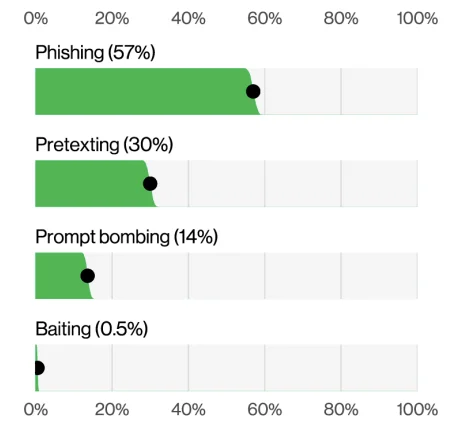
Top social engineering incidents (Verizon 2025 DBIR)
The report also notes a rise in MFA bypass strategies, including token theft, Adversary-in-the-Middle (AitM) phishing, and SIM swapping. In fact, Verizon stresses that SIM protection tools and TOTP-based MFA are now essential for preventing mobile-based takeovers.
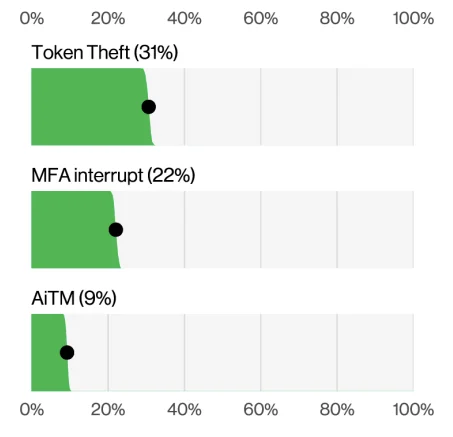
Microsoft 365 MFA bypass attack types (Verizon 2025 DBIR)
As social engineering becomes harder to detect and more customized per victim, organizations must combine user education with stronger identity controls, adaptive MFA, and real-time anomaly detection.
7. Regional Trends: APAC and EMEA See Sharp Rises in System Intrusion
System Intrusion surged globally in 2025, but the trend was especially stark in Asia-Pacific (APAC) and Europe, Middle East, and Africa (EMEA). In APAC, it jumped from 39% to 83% of all breaches – a dramatic rise driven by ransomware, stolen credentials, and vulnerability exploitation. In EMEA, System Intrusion also climbed from 27% to 53%, overtaking Miscellaneous Errors as the leading breach pattern.
In both regions, ransomware played a dominant role. In APAC, 51% of breaches involved ransomware, often following credential theft or vulnerability exploitation. Malware and hacking were the top action types, with stolen credentials found in 55% of APAC breaches.
While Social Engineering and Basic Web Application Attacks declined in relative share, they still accounted for a notable portion of incidents. In EMEA, for example, phishing showed up in 19% of breaches.
These regional shifts suggest a wider adoption of hands-on, multifaceted attack campaigns across geographies, as threat actors move beyond opportunistic phishing to more invasive, tailored compromises.
8. Industry Insights: Healthcare and Retail Face Sophisticated Threats
Threat actors continued to hit industry-specific soft spots in 2025, with Healthcare and Retail standing out due to the complexity of threats they faced.
In Healthcare, 90% of breaches were financially motivated, but Espionage motives spiked to 16%, up from just 1% last year. This shift may reflect increased targeting by state-sponsored actors seeking sensitive medical data or research. The industry’s top breach patterns (System Intrusion, Everything Else, and Miscellaneous Errors) accounted for 74% of all cases, with external actors responsible for most incidents (67%). Notably, partner-related breaches also caused widespread impact, particularly in pharmaceutical supply chains, IT vendors, and radiology services.
Retail, on the other hand, faced a consistent trio of threats: System Intrusion, Social Engineering, and Basic Web Application Attacks made up 93% of breaches. Ransomware and credential abuse remained central issues, while Espionage-motivated breaches rose to 9%, signaling more advanced adversaries in play. The shift away from purely payment data toward broader internal and credential data shows attackers are widening their goals.
To help organizations strengthen their situational awareness, SOCRadar regularly offers Country and Industry Reports. These free resources highlight the most targeted sectors, active ransomware groups, common attack methods, top risks by region, and key cybersecurity trends across industries.
Industry Threat Landscape Report, SOCRadar Labs
For quick, up-to-date insights, you can also explore the SOCRadar Labs Industry & Country Threat Landscape Reports, providing snapshots of current threats.
9. Public Sector and SLTT Governments Remain Prime Ransomware Targets
The Public Sector continues to face sustained pressure from ransomware groups, especially across state, local, tribal, and territorial (SLTT) entities. In 2025, Ransomware appeared in 30% of all Public Sector breaches, with attackers showing no preference between federal agencies and small local councils.
SLTT organizations were hit hardest. 43% of ransomware victims came from U.S. local governments, with similar activity seen across EMEA regions. These entities, often perceived as soft targets with limited cybersecurity budgets, attracted persistent attention from financially motivated attackers. In contrast, federal-level breaches were more likely to involve Espionage, driven by actors seeking sensitive personal or classified information.
Misconfiguration and misdelivery errors also plagued the sector, particularly during mass mailings, while Basic Web Application Attacks and Social Engineering, such as prompt bombing, emerged as rising concerns. The attack surface for public agencies is vast, and many lack resources to implement layered defenses across legacy systems.
Ultimately, the report underscores that obscurity is no protection. Ransomware gangs continue to prioritize ease of entry and impact, regardless of agency size or public visibility.
10. A Look Back: Verizon’s Year-in-Review Highlights from 2024
To close the report, Verizon offers a high-level retrospective that frames 2024 as one of the most turbulent years in recent cybersecurity history. From zero-day exploitation to supply chain attacks and APT-led espionage, the past year pushed organizations to their limits. Let’s take a closer look at the trends that defined the threat landscape in 2024 – and will likely shape what’s to come in 2025.
Zero-Days and Exploited Vulnerabilities
Organizations faced a relentless barrage of zero-day exploitation. Major platforms – including Ivanti, Citrix, Jenkins, Apple, Cisco, Fortinet, and VMware – saw flaws exploited within hours of public disclosure. Verizon’s summary notes that the MOVEit, Atlassian Confluence, and ServiceNow vulnerabilities were especially impactful, often used in follow-on ransomware attacks.
Perhaps the most emblematic case was the XZ Utils supply chain backdoor uncovered in April 2024 – a subtle compromise in a widely used compression tool that could have allowed root-level access on Linux systems. It emphasized how deeply embedded risks can go, especially in upstream open-source software.
Rise of Nation-State Activity
Geopolitics spilled into cyberspace as APT groups from China, Russia, Iran, and North Korea launched high-profile campaigns. Key developments included:
- Salt Typhoon (China) targeting U.S. telecom infrastructure.
- APT44 (Russia) continuing its disruptive cyber campaigns in Ukraine.
- Kimsuky (North Korea) weaponizing job-themed phishing to infiltrate aerospace and IT targets.
The report highlights how espionage increasingly blends with financially motivated operations, making attribution harder and widening the threat surface.
Cybercrime’s Evolution and Law Enforcement Pushback
Ransomware dominated headlines once again, but the ecosystem behind it continued to evolve:
- LockBit, RansomHub, and BlackSuit (a Royal ransomware rebrand) led attacks.
- Law enforcement scored victories through operations like:
- Operation Cronos (LockBit infrastructure seizure)
- Operation Destabilise (Russian money laundering disruption)
- Operation PowerOFF (crackdown on DDoS-for-hire platforms)

LockBit’s data leak site, seized in Operation Cronos
Despite setbacks, ransomware actors quickly adapted – deploying new malware variants like Black Basta with Zloader, and exploiting overlooked CVEs dating back to 2014.
For a deeper look at major law enforcement operations that shaped 2024, you can explore SOCRadar’s full coverage in Year of Takedowns: Law Enforcement Operations of 2024.
Supply Chain Risks and Identity Failures
2024 reminded defenders that even obscure libraries can trigger massive consequences. The Polyfill.io compromise exposed how simple JavaScript tools could become attack vectors at scale.
Meanwhile, breaches like the Snowflake incident exposed the persistent failure to enforce MFA and identity hygiene. In this case, access was reportedly gained through compromised credentials, again showing how a single weak identity can expose an entire ecosystem.
New Threat Vectors: AI and MFA Bypass at Scale
As generative AI tools grew in popularity, so did their misuse. Attackers embraced AI-generated phishing lures, while defenders scrambled to apply AI for detection and response.
Verizon also highlighted the rise of Phishing-as-a-Service (PhaaS) platforms, which help attackers scale phishing operations and specifically target MFA bypass techniques. These platforms contributed to the surge in Prompt bombing, Adversary-in-the-Middle (AitM), and token theft attacks seen across multiple verticals.
Another emerging vector? LLMjacking – the hijacking of cloud-based AI resources using compromised credentials, offering a glimpse into future financial and operational threats.
Conclusion
Verizon 2025 DBIR makes it clear: cybersecurity teams must evolve faster to keep pace with increasingly sophisticated threats. According to the report, over the past year, several critical trends reshaped the landscape:
- Rapid patching and software supply chain vigilance became non-negotiable.
- Credential theft, infostealer malware, and session hijacking remained key enablers of breaches.
- Nation-state operations increasingly blurred into financially motivated attacks.
- Ransomware groups adapted quickly, leveraging new exploits and shifting tactics.
- AI emerged as both a tool for defenders and attackers, creating new threat classes.
At the same time, the fundamentals still matter. Identity protection, layered detection strategies, and early threat visibility remain vital to containing and mitigating breaches before they escalate.
Organizations looking to strengthen their posture can benefit from integrated platforms and services like SOCRadar’s many modules: Attack Surface Management, Cyber Threat Intelligence, Digital Risk Protection, and Supply Chain Intelligence.
SOCRadar XTI platform – ASM Dashboard
These solutions help security teams identify exposed assets, detect leaked credentials, monitor for ransomware activity, and track supply chain vulnerabilities – giving defenders the advantage in a fast-moving threat environment.
The threats may be evolving, but with the right visibility, faster adaptation, and a proactive mindset, organizations can stay protected.





































