
Active Exploitation of Serious Vulnerabilities in PaperCut, Veeam, and TP-Link
[Update] July 11, 2024: “EstateRansomware Exploits CVE-2023-27532 in Veeam Systems”
[Update] April 18, 2024: “Indicators of Compromise Related to the Exploitation of CVE-2023-1389”
[Update] April 18, 2024: “Multiple Botnet Operations Exploit CVE-2023-1389: Urgent Update Advised for TP-Link Archer AX21 Routers”
[Update] May 15, 2023: The Bl00dy Ransomware gang has started exploiting the CVE-2023-27350 vulnerability. Added the subheading: “Bl00dy Ransomware Exploits PaperCut RCE in Education Industry.”
[Update] May 9, 2023: State-sponsored threat actors named Mint Sandstorm and Mango Sandstorm, both based in Iran, are taking advantage of unpatched PaperCut instances. Microsoft reports that Mango Sandstorm exploitation activity is still minimal, with operators connecting to organizations’ C2 infrastructure using tools from prior intrusions; in contrast, Mint Sandstorm exploitation activity appears opportunistic, affecting businesses across industries and regions.
[Update] May 5, 2023: Added the subheading: “Proof-of-Concept Exploit Available for PaperCut Vulnerability CVE-2023-27350.”
Recent incidents that marked the cybersecurity landscape and brought attention involve the active exploitation of several vulnerabilities affecting PaperCut, Veeam, and TP-Link.
Microsoft has just confirmed that PaperCut servers have been targeted with ransomware. The threat actor FIN7 has been linked to attacks exploiting a vulnerability in Veeam Backup & Replication software. In addition, the Mirai botnet has been updated to exploit a serious vulnerability in TP-Link routers.
In this blog post, you can further explore these three incidents and their implications for cybersecurity.
PaperCut Server Vulnerabilities Exploited to Deliver Cl0p and LockBit Ransomware
Microsoft has confirmed that the active exploitation of PaperCut servers involves the distribution of Cl0p and LockBit ransomware.
The Microsoft threat intelligence team has reported that the intrusions are linked to a threat actor named Lace Tempest (previously known as DEV-0950). In the attacks, the threat actor used multiple PowerShell commands to deliver a TrueBot DLL.
Lace Tempest is a known affiliate of Cl0p ransomware and has previously utilized Fortra GoAnywhere MFT and Raspberry Robin infections in its attacks.
Active Exploitation of PaperCut Servers via CVE-2023-27350 and CVE-2023-27351
PaperCut detected suspicious activity on a customer server in mid-April, indicating that unpatched servers are being exploited in the wild. The initial investigation also pointed to the TrueBot malware, which is attributed to Russian hacker(s) named “Silence.”
The attacks were possible due to two vulnerabilities residing in PaperCut Application Server and MF/NG, identified as CVE-2023-27350 (CVSS score: 9.8, Critical) and CVE-2023-27351 (CVSS score: 8.2, High).
CVE-2023-27350 could allow a remote, unauthenticated attacker to achieve remote code execution on a vulnerable PaperCut Application Server, while CVE-2023-27351 could allow an unauthenticated attacker to obtain sensitive information from vulnerable PaperCut NG or MF instances, such as usernames, names, and email addresses.
Lace Tempest Exploits PaperCut Vulnerabilities to Deploy Cl0p Ransomware
Microsoft has reported that the threat actor has added the CVE-2023-27350 and CVE-2023-27351 vulnerabilities of PaperCut to its attack toolkit as early as April 13.
In the attack that resulted in the deployment of Cl0p ransomware, Lace Tempest used TrueBot DLL to connect to a C2 server. They then attempted to steal LSASS credentials and injected the TrueBot payload into the conhost[.]exe service, as explained by Microsoft on Twitter.
After that, the attacker installed a Cobalt Strike Beacon implant, which helped them to move laterally across the network, conduct reconnaissance, and exfiltrate files via the file-sharing service named MegaSync.
Security firms Redmond and Huntress have also shared details, and they reported that a different threat activity uses PaperCut vulnerabilities to distribute LockBit ransomware. Some threat actors are also exploiting them to deploy Monero cryptocurrency miners on infected systems.
PaperCut released patches to fix CVE-2023-27350 and CVE-2023-27351 vulnerabilities at the end of March. However, on April 19, the company warned in an advisory that the vulnerabilities were being widely exploited in the wild. Refer to the mentioned PaperCut advisory for details and the upgrade documentation for available updates.
Proof-of-Concept Exploit Available for PaperCut Vulnerability CVE-2023-27350
Huntress researchers found a way to get past authentication by going to the SetupCompleted page on the server and then clicking Login. This allowed them to login as if they were an administrator user without needing any credentials.
Additionally, they uncovered that disabling print-and-device.script.enabled and print.script.sandboxed would allow Java code to run on the server. By removing the sandboxing, the printer scripts would have direct access to the Java runtime, allowing for trivial code execution. As a result, an attacker could add malicious code to the default JavaScript template printer script, indicating they could simply edit a printer script to gain remote code execution. You can find video demonstration of the exploit on YouTube.
Horizon3 has briefly examined Huntress’ proof-of-concept (PoC) exploit on their blog and also published their own PoC on GitHub, which you can find here.
VulnCheck has provided another PoC exploit. The PaperCut NG interface allows an administrative user to specify a “Custom Program” to source and authenticate users, and this feature can be abused by attackers to execute arbitrary code by providing a malicious username and password.
Proof-of-concept exploits have been developed for both Linux and Windows. The auth program has to be interactive, but any program on disk can be used.
On the Linux side, the auth program is set to /usr/sbin/python3, while on the Windows side, ftp[.]exe is used.
By providing a malicious username and password during a login attempt, an attacker can execute arbitrary code. The attack is carried out by downloading a binary to C:ProgramData and executing it, resulting in a process tree of pc-app.exe -> ftp.exe -> cmd.exe -> AXtJxdUwlfJI.exe. This approach doesn’t generate expected log entries and bypasses process-creation-based detections. A YouTube video demonstrating the exploit can be found here.
Bl00dy Ransomware Exploits PaperCut RCE in Education Industry
The Bl00dy Ransomware gang is also exploiting the PaperCut remote code execution vulnerability, CVE-2023-27350. The gang has been active since May 2022 and employs an encryptor based on leaked LockBit, Babuk, and Conti source codes.
According to a joint advisory by the FBI and CISA, Bl00dy Ransomware exploited the vulnerability in early May 2023 to gain initial access to networks in the Education Facilities Subsector. Some of these operations resulted in data exfiltration and the encryption of target systems.
CISA has stated that the threat actor focuses on the education industry, which accounts for approximately 68% of the PaperCut servers exposed to the internet.
Visit the official CISA advisory for more information, including indicators of compromise (IoC), signs of exploitation, network traffic signatures, and child processes to monitor. It is advised to apply the latest security updates on PaperCut MF and NG servers for an ultimate fix.
FIN7 Exploits Veeam Vulnerability CVE-2023-27532 with POWERTRASH Dropper
A Russian cybercrime group called FIN7 has been linked to attacks that exploit a vulnerability in Veeam Backup & Replication software, which allows the group to distribute a PowerShell-based dropper called POWERTRASH, which can execute a hidden payload.
WithSecure detected this activity on March 28, 2023, and suspects that the group took advantage of CVE-2023-27532, a high-severity flaw in Veeam Backup & Replication, which allowed attackers to gain access to infrastructure hosts and steal encrypted credentials stored in the configuration database.
Custom PowerShell scripts were used in the attacks to steal system information, establish an active foothold in the compromised host, and retrieve stored credentials from backup servers. This was done by running DICELOADER, also known as Lizar or Tirion, each time the compromised host booted up.
Additionally, the attackers used a previously unknown persistence script called POWERHOLD.
The DICELOADER malware was decoded and executed using another unique loader called DUBLOADER. The group also ran SQL commands to steal information from the Veeam backup database.
According to security researchers Neeraj Singh and Mohammad Kazem Hassan Nejad, these attacks’ objectives were unclear because they were stopped before they could be fully carried out.
However, they noted that these findings suggest that the FIN7 group is constantly evolving and refining its tactics. Additionally, FIN7 has incorporated new malware tools into their arsenal, including a loader and backdoor called Domino, which has been identified by IBM Security X-Force and is intended to facilitate further exploitation after an initial attack.
EstateRansomware Exploits CVE-2023-27532 in Veeam Systems
Although Veeam patched CVE-2023-27532 in March 2023, it continues to be exploited. Recently, researchers uncovered that EstateRansomware leveraged this flaw in unpatched systems.
The attackers initially breached the network through a brute-force attack on a FortiGate SSL VPN using a dormant account and established a persistent backdoor named svchost[.]exe on the failover server, set to activate daily via scheduled tasks.
The attack also employed a credential extraction script, likely from existing PoC scripts, along with tools such as SoftPerfect Netscan and Nirsoft’s password recovery utilities to gather additional credentials and network information.
The attackers moved laterally to the Active Directory server, deployed ransomware using compromised accounts, disabled Windows Defender, and launched the ransomware payload, leading to extensive network encryption. They also cleaned up traces to obstruct forensic analysis.
Mirai Botnet Exploits Flaw in TP-Link Archer AX21 Routers, Causing DDoS Attacks
Recently, the Mirai botnet has been updated to exploit a serious vulnerability in TP-Link Archer AX21 routers. This flaw, CVE-2023-1389 (CVSS score: 8.8), allows hackers to execute code on the router without authentication.
Researchers from Team Viettel and Qrious Security first discovered the vulnerability, and TP-Link released a fix in March 2023.
However, the Zero Day Initiative observed in-the-wild exploitation on April 11, 2023. The attackers took advantage of the flaw by using an HTTP request to connect to the Mirai command-and-control (C2) servers.
The payload downloaded from the C2 servers then turned the device into a botnet that launched distributed denial-of-service (DDoS) attacks against game servers.
The ZDI researcher, Peter Girnus, recommended applying the patch to address this vulnerability as it is the only effective solution.
Multiple Botnet Operations Exploit CVE-2023-1389: Urgent Update Advised for TP-Link Archer AX21 Routers
According to recent reports, multiple botnet operations are exploiting the CVE-2023-1389 vulnerability, infecting TP-Link Archer AX21 (AX1800) routers for further malicious activity.
In our previous report, we highlighted the Mirai botnet’s exploitation of the vulnerability; in a new alert, Fortinet noted a significant increase in exploitation attempts, originating from six botnet operations: AGoent, Gafgyt Variant, Moobot, Mirai Variant, Miori, and Condi.
Fortinet’s telemetry data reveals that since March 2024, infection attempts leveraging CVE-2023-1389 have frequently surpassed 40,000 and peaked at 50,000.
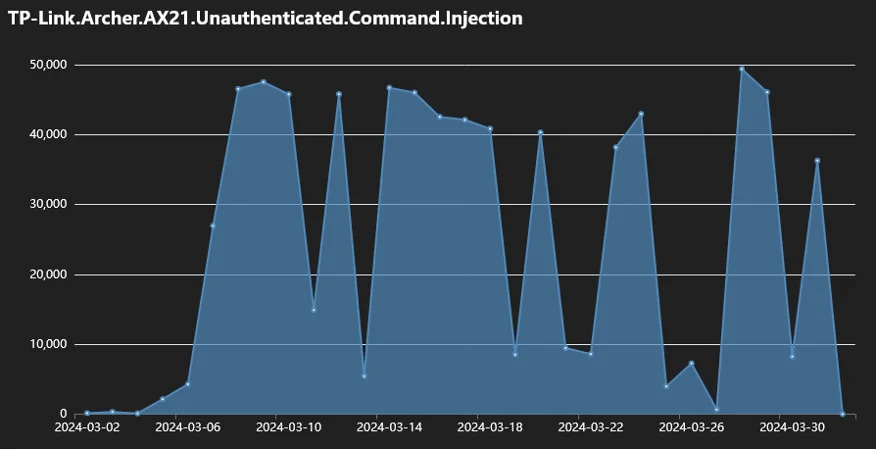
Telemetry of attempted intrusions (Fortinet)
The varying tactics and scripts utilized by these botnets to exploit CVE-2023-1389 often result in Distributed Denial-of-Service (DDoS) and brute force attacks on victim devices.
This surge in malicious activity underscores the prevalence of unpatched instances, thereby, urgent action is required: users of TP-Link Archer AX21 routers should promptly update their firmware.
As a precaution against such threats, disabling web access to the admin panel and using strong passwords are recommended. For further details, refer to Fortinet’s article and review the indicators of compromise provided at the end of this blog post.
Proactive Vulnerability Prioritization with SOCRadar
SOCRadar’s Attack Surface Management feature enables real-time tracking of product vulnerabilities that are automatically detected in an organization’s digital footprint. This allows security teams to proactively prioritize vulnerabilities by accessing contextual intelligence.
Additionally, the Vulnerability Intelligence in the Cyber Threat Intelligence tab provides visibility on vulnerability trends that threat actors actively exploit.
Indicators of Compromise Related to the Exploitation of CVE-2023-1389
C2:
- fjsnsinfinsf[.]ngcv[.]top
- 45[.]155[.]91[.]135
- rooty[.]cc
- bn[.]networkbn[.]click
- 5[.]10[.]249[.]153
- 195[.]62[.]32[.]227
URLs:
- hxxp://91[.]92[.]253[.]70
- hxxp://94[.]156[.]8[.]244
- hxxp://103[.]188[.]244[.]189
- hxxp://185[.]224[.]128[.]34
- hxxp://5[.]10[.]249[.]153
- hxxp://195[.]62[.]32[.]227
Files:
- 6104674bfa58ac11c697062d6068c568384f13037d1a146dbe25cd001104ca8b
- f33a02781d60ca36f4ee56579c6d33846c2549ad7556bca499c73302cee17514
- d02381634921d92358577c106180eba766b98a520c907870898b2c32d7de4547
- 0a3fbc79e742354c8fc82830fc3426f7f8d3b900260c06aa58e53547b48feaa6
- 475487bf7b96fe3da321dac0b5f59231651fc3d71f86bf9580bfa77e59b0f2c8
- a3e8493f2fb38b7f2ba309809577281d3cc25bee9fb3b5c0053a6e89de1dbce7
- 5e6deba076cbe7b9833d0ddee7c8065e91d13f1fc2a5c7daf4db36da458d689a
- 29ef4c5d9172b09d6abc08da800a5a09b460b98aaadf1aa29edda81300fcc609
- e7af5f1d5d68f75ee03a37ee8016695e35edaae528cdba4ab7b9a90570a1e4be
- b45906c711ed4f109a10cfaffa0b4c18e56c6f6ddc8d100c87e0a0349a30293d
- e9e8fc16c586f51eb2f86db5a60e54b46d66275fdd6df8fb72e96e50014a1290
- b731fe97dc723d0d5a51fe8203b33f16a51183b3dab4c9c8ee7bd304462ad192
- 1ffc3c457eb84aa36cd4bc7f3d0dc9a6b8079d63c2bab03c3a646906152876c0
- d8b4d8950ec1a3f812af69d261f452aae2b19d3bced8551f9178e40ca0c1bcf8
- 8562c9ad26ab3ad7d16ac43c9dcbf600d5319e5432d72dc684983cc5f64ff41e
- 092b3a57ee4ecd64591616da6ce0cfb9f01930dbeb179f05e1dbbdbc918098ac
- 092b3a57ee4ecd64591616da6ce0cfb9f01930dbeb179f05e1dbbdbc918098ac
- c65f86d5917025a8674bf9758870decd923ea2662d6611a1365303f4fe55fa26
- 65f64b270a10255db1e55a158a02829a3af982cbcd4b56f14e58132cbb45e6a9
- a383319a28d50e8c280646dc53a2f33fec62ad69ef4948dae76a4f1f6fe2f159
- 7ef190f05fe9be5d7f38bdb556fffdb7d9b5633ddf60cc43b98c09887a292c49
- 7322da39ce05e7496fcaef6602a15266943a59a5027e5ea97344133d42e0f6e3
- a1c14e99cc8490a4d503ffd660e2d881fa5d766a4288eea328f73bd8ee99078d
- a7d3ffbb3edff1956d7422dd04305d8c3ac16418e2eb190ed9a08a1c275c5e8e
- 1427deedaafd5345aa3c41d39b14b23a454ed894c73f3c9224cd0b51c88afcfa
- f97c9802324eeb0ebdfc15ce3e390c8cca5a9062c3348f7d2b5b00d1efa49508
- 3307e4d1daefca1eeb1ee4a6dea7738594076aa04f3e7e470a8b2ae32b9e4893
- 86fe87891311228b58a606114a2d41d94b520c5c4be6ff6bc0add45f5b6250ef
- b9962c3e066904cf8df05f60b9bd21d979466aca64596d2b7557be7fa4358c4d
- a48807aaa7be63c41bbabcf55d40cba416bc23432f247e4038ed0cd32fd05519
- 4119530c4dba8a53ba081094ca163f28a51bd37c6ee40b4aa55097939ec1df38
- 2be7481bfec8fcbb370afa00e9befa97000e7aa987a17cd6c48fc9f2d0b60110
- b605570db3158ba355552b5b638e7df4b0888d56d206004d9af6901c4770c75f
- 0dbf4c327df0159305ffc9776ad2fbdd655fe513712f75e360e211aa6686f69a
- ae2d6b41150d61b828368847a0eba51d4562fa2bae4478c10940f5e3e3e46c6b
- 581adb7645ca54dbc3a043ee39a09037a7b5f572c1b8c137cb0c751b26ff9ebd
- 18753e0c31c2100889f0e085ba03eb1c616dcc50606d9733574b68e75be2ee7a
- 123a392cfa9114daeab28976f5ce740da4288d6ac516b5afbf1ea17e28eaada1
- 8317c084d08450a220fe7f38ce6b1a767b2e8776f8f4a436b84b912476b00cbc
- 94c9297951a48fcc0f22dac94da599bc2651c757d27cb94c9de16d00ea5af04f
- fdcfaa03f99233d8aecc17098833d82860d68c12440c5ff7e898b50891cf65bf
- 045b8b9f7bb69e4450d49eb6197722b9b58a8f0e7af479640ea6f666553db4da
- 96c8ec9a54b0fef4bca739b47d943c295c766c7759d0f3a5a891585609019f42
- 1a6964f76f573dd50f41ee8dc4c5b29868807af6326faee92ad9ffaeba3dc5a3
- e220a88f3c07a6ece0adcbeca93fd6024d9f63a971c4aa732ec90930e386b5aa
- 42deb408f0861891e49205fce2496cfe9a6c0cbf86f5d1c48bd88f9120631b1d
- f19d69486f380f7f22482b17eab7343da36229a4e60b9f3938f7846002ff0fa2
- 8721dc3617731683a34eb7c8d9a688195d2db1efa8da3084edbe04f76cb0d047
- 7e8061fab5ad856312040a78674932dcd08b6926a8cc8a5de91252c590b4f6ba
- 9100bc0eb0bce4f5f7fc314fa820b4dee00db8d31892ec6fdb4fccca801a40d0
- 46d085e7c36ec4ada5f630c47b1ed418ceae077832d6fc2e7730af2715fb954d
- cc197f92fb6564575d7bd64958bc96be9e0c09d06fa19449a0ad3dc50f09ddb6
- 4e94d9808d5c3c414100abb60233614fcbad2e884c2fd851cb9d694186165a4f
- bfa195bd238473bfead86e74b796c4721d1f5281c284b96ff29d8806a82a6520
- 396b1e21260b374a45ba703239bc29b1345dea89ad9d54db0b7f312aa95c6984
- 1a1a8f9ccb66f37f14b5cf2a77e9e8d47400bdec957d9f20729e5c81bfc78be6
- 699d00adf4e8c070d2b955b23054e945c78267beb2ec9cc580130771200e5ea3
- fdae7846f75c7b65130e73bafda28f442913e403534cb91657c21c2426869f2f
- 25f3558a2cdf5aca294254004954bb10d08a0ef0f913f3ddd1f8f3cc71f114dd
- 12273047ec3eb4e1318c26ec7c10b77e5d631738da126880e248d7f54dfa5718
- F7faaadceebe69bec33096166a54ed9b593b1b690ba9594b4c353303f55101aa
- e6d1df0621b10d051ebba4507ac3d14f4d206ab56bafbc3510db542d4c4470d9
- 4480d72a324f519d3a630bf2ef7b118f4e388c5bccdd0a5465bafd2253daa619
- 4509e84a9abcb732f0ee90bf27dd300247b23b6dac9b41cd01f59d6384b5348a
- 08166a0d2fe65a3ad8b289cb2714c3a150635e29664bff24e5befc6b48526899
- ed85c3e25bac63b7e232ac3cfd91116bf7c64f1c4c96b933d5715bbe055ffc89
- f0d62aec4a2a5353a6416bbd403969fc0617d08aeb8eb9e09de4d4068a2fd9f3
- 8cfdcaf4611fd855672ad561de196417deea97341f45efd02e97e26d4674291d
- e73bbef9c7fcaf610c858be52a375b517bc62fd7e05dd867f928cd353536de16
- c192146c8311694342f73a19cfe69ecc53f3f1d6cab006526d2daa5134846357
- ab5ee18fd3df5a2d7f2d84c75b33fd2f73b76c8e0d2df278d9ded40943d16911
- ef30bd34f8c11e042e2600c62cf702515c94290207cf72fad1ec0d277221bb70
- 0571c16d0f2d0267b354f81fdbfb49738f3cb867371b9ef0d3ffe1020fb9f9cf
- bf5e6947f6829d17b8a8e5984366efcf5592d8f6bc7ec6d7e85b1872bebcb24a
- 549d3aac3b42f702f29ab27c653c0f239a51601a6aeb50564beda614f8f1f33e

































