
Excel's Blind Spot: The Strategic Deployment of Agent Tesla Malware by...
Excel’s Blind Spot: The Strategic Deployment of Agent Tesla Malware by Cyberattackers In the ever-evolving landscape of cyber threats, a notable trend has emerged: the exploitation of a longstan...

Dark Web Profile: Haghjoyan
Dark Web Profile: Haghjoyan The Haghjoyan hacker group, self-identifying as the Iranian cyber army, emerged at the forefront of cyber warfare during the Israel-Hamas conflict. Their presence, prominen...
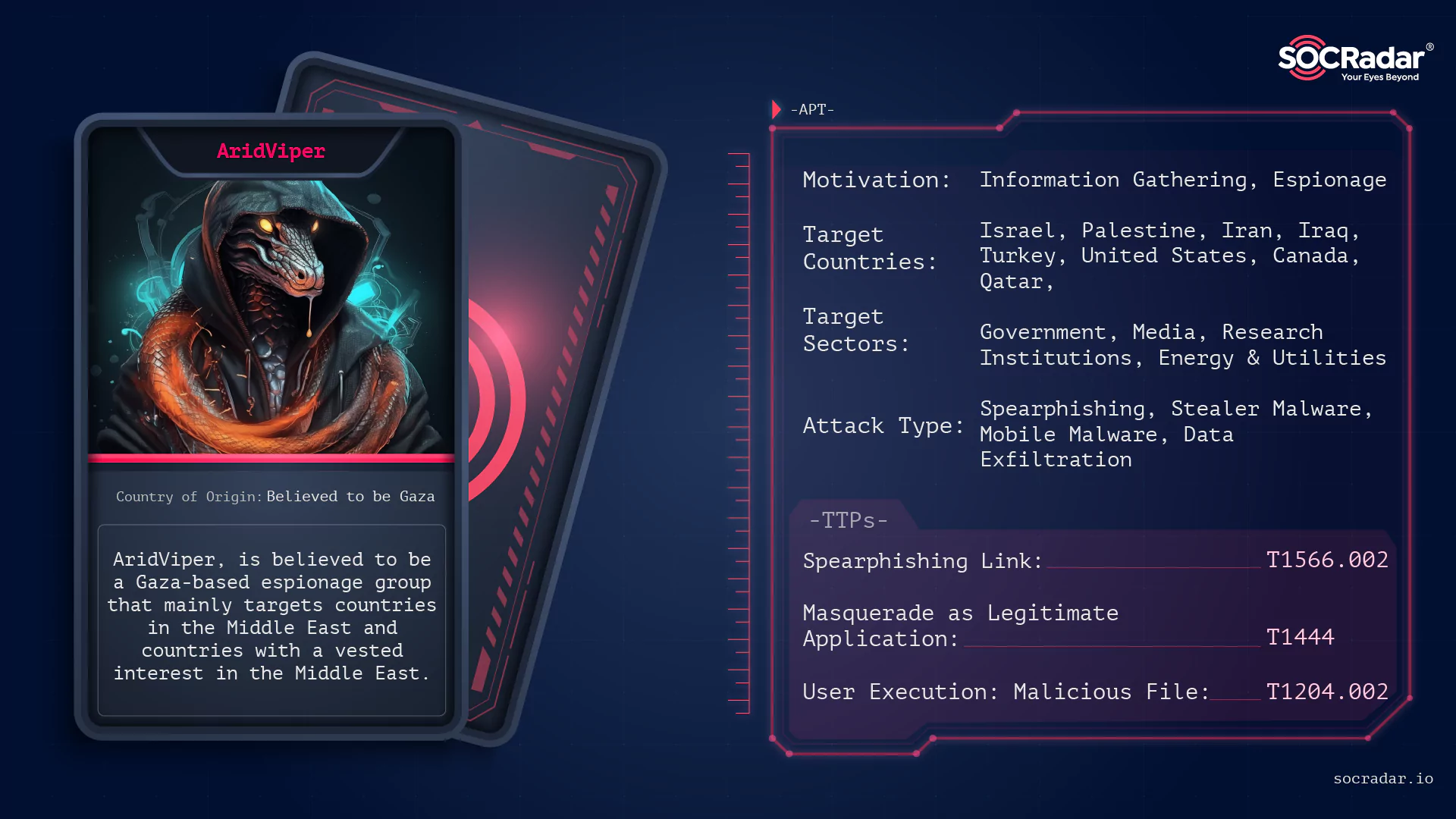
Threat Actor Profile: AridViper
Threat Actor Profile: AridViper A stealthy predator lurks in the vast, unforgiving digital desert, known as AridViper. Like a snake silently slithering through the sands, this state-sponsored cyber th...

Disney Data Leak, Meduza Stealer Sale, Nissan Australia and The Econom...
Disney Data Leak, Meduza Stealer Sale, Nissan Australia and The Economist Targeted in Cyberattacks Last week’s findings by the SOCRadar Dark Web Team include a substantial 1.9 million credit car...

Dark Peep #7: Shadows of Betrayal and Leadership in Flux
Dark Peep #7: Shadows of Betrayal and Leadership in Flux Shrouded in the mysterious alleys of the dark web, “Dark Peep #7” delves into a world where betrayals happen as often as tiny secre...
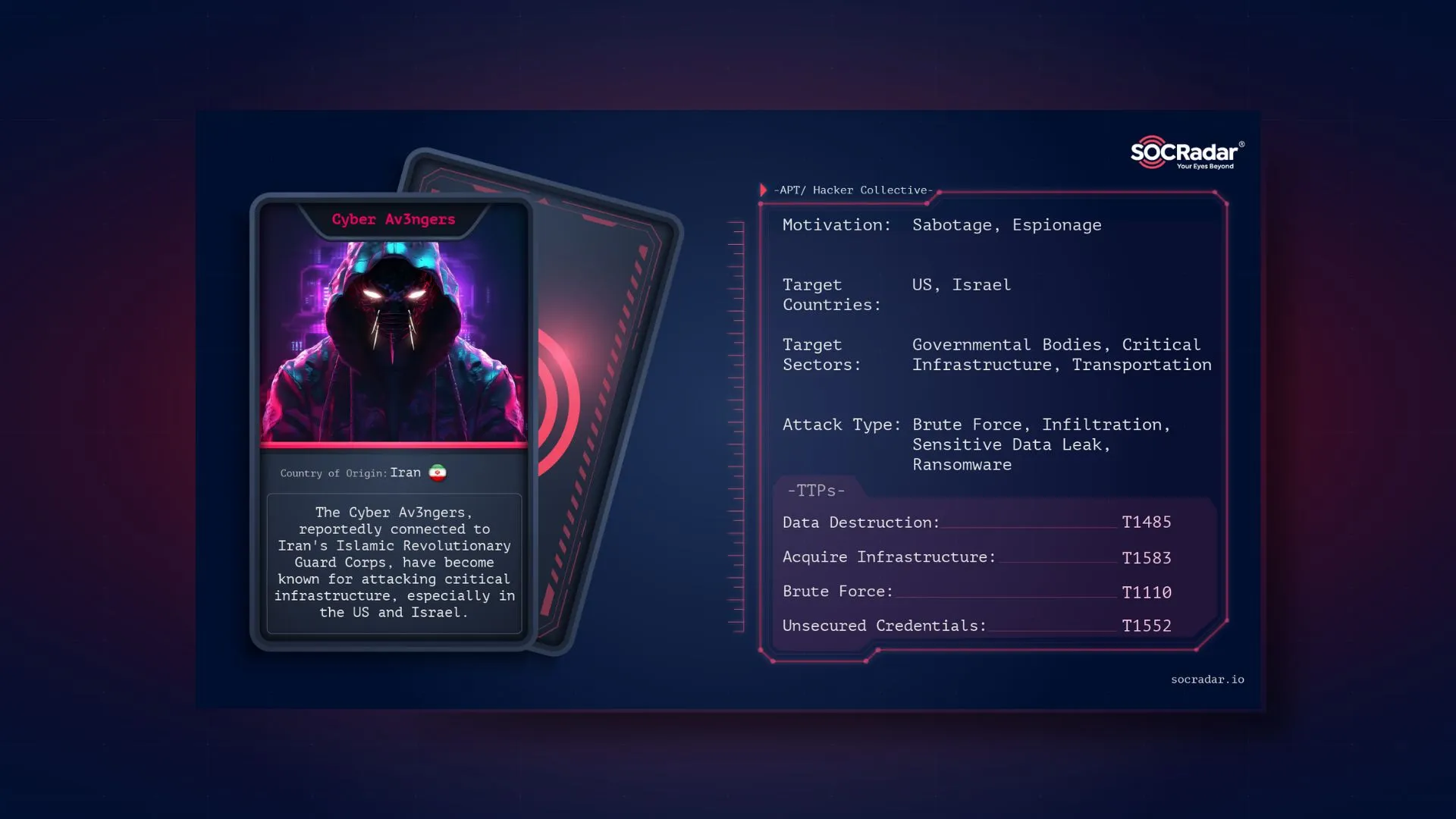
Dark Web Profile: Cyber Av3ngers
Dark Web Profile: Cyber Av3ngers The Cyber Av3ngers, reportedly connected to Iran’s Islamic Revolutionary Guard Corps, have become known for attacking critical infrastructure, especially in the US and...

CISA Updates: Microsoft 365 Guidance, SCuBAGear Tool, Mozilla Alert, Q...
CISA Updates: Microsoft 365 Guidance, SCuBAGear Tool, Mozilla Alert, QNAP & FXC Vulnerabilities Enter KEV CISA has officially released the Microsoft 365 Secure Configuration Baselines, aiming to a...

Massive Data Leak by BidenCash: 1.9M Credit Card Details Exposed on Ha...
Massive Data Leak by BidenCash: 1.9M Credit Card Details Exposed on Hacker Forum The SOCRadar Dark Web Team detected a significant data breach on a hacker forum, revealing the leak of 1.9 million cred...

Dark Web Profile: Cyber Toufan Al-aqsa
Dark Web Profile: Cyber Toufan Al-aqsa On November 16 2023, a new group emerged in the intricate web of modern cyber warfare: Cyber Toufan. This group, shrouded in the digital shadows, has recently ga...

ALPHV Seized, Unseized, Decrypted; Pandora's Box May Be Reopened
ALPHV Seized, Unseized, Decrypted; Pandora’s Box May Be Reopened Emerging as a significant player in the ransomware landscape, ALPHV (BlackCat) has established itself through sophisticated ranso...

Major Cyber Attacks in Review: November 2023
Major Cyber Attacks in Review: November 2023 In November 2023, the digital landscape witnessed a series of major cyber attacks, creating ripples across industries. From disruptive ransomware attacks t...

New DDoS Service, Microsoft Defender Vulnerability, Network Access to ...
New DDoS Service, Microsoft Defender Vulnerability, Network Access to Indian Bank, Princeton University Data Leak In the last week, SOCRadar’s Dark Web Team uncovered critical developments, incl...

Spain Database and Australian Access Sale, Everlast Breach, macOS Meta...
Spain Database and Australian Access Sale, Everlast Breach, macOS Metamask Stealer, New Microsoft Exploit In the latest edition of the Week in Dark Web, the SOCRadar Dark Web Team has uncovered signif...

Alarming Increase of Access Sales in the Dark Web
Alarming Increase of Access Sales in the Dark Web The SOCRadar Dark Web Team has revealed an alarming increase in the sales of unauthorized network access to a myriad of companies in the previous week...

Hacker Forums Are on the Rise: Dumped, Raiding, BlackForums
Hacker Forums Are on the Rise: Dumped, Raiding, BlackForums Recently, cyberspace has witnessed a surge of activity, particularly within the hacktivist space, traditionally active on Telegram and Twitt...

Dark Strom’s Android RAT, Sales of Financial Data and UK RDP Access, S...
Dark Strom’s Android RAT, Sales of Financial Data and UK RDP Access, SiegedSec’s Government Breach The SOCRadar Dark Web Team unveils a fresh wave of illicit activities as the relentless pace of...
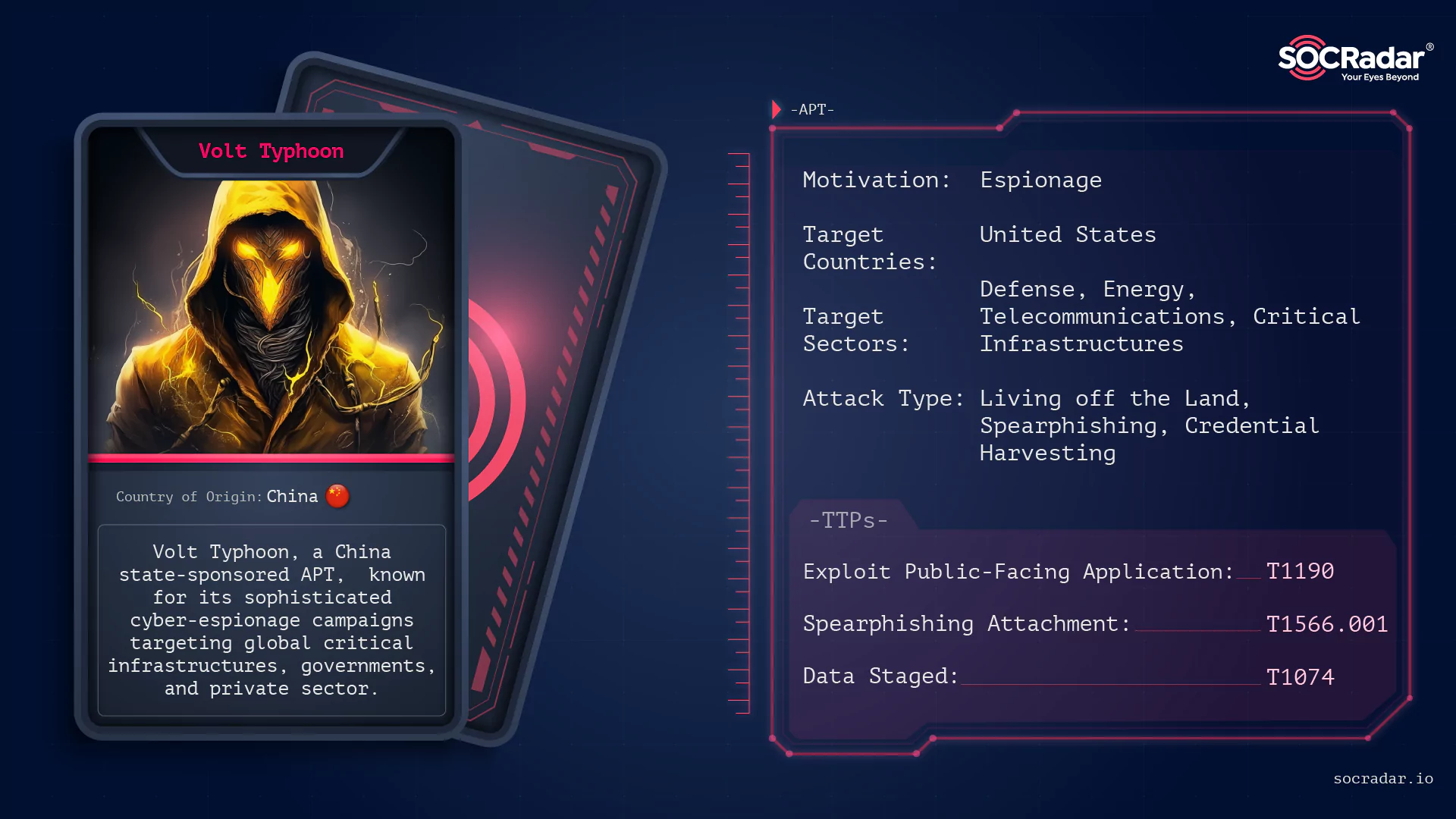
APT Profile: Volt Typhoon
APT Profile: Volt Typhoon [Update] March 13, 2025: Volt Typhoon Maintained Access to U.S. Utility Systems for Nearly a Year [Update] February 01, 2024: U.S. Government Actions Against Volt Typhoon As...

Dark Web Sales: E-Commerce and Crypto Wallets' Databases, Fortinet Acc...
Dark Web Sales: E-Commerce and Crypto Wallets’ Databases, Fortinet Access in US, UK Credit Cards Embarking on a relentless pursuit of the shadows, the SOCRadar Dark Web Team brings to light a se...

Dark Peep #5: The Calm Before the Storm
Dark Peep #5: The Calm Before the Storm On the dark web, the weather has closed, the thunder is rumbling, and the wind is picking up. Chaos is coming, ahem, not that chaos, ChaosSec is coming(!) Let&#...

LockBit Shares Boeing Data, Software Company and US Database Leaks, Du...
LockBit Shares Boeing Data, Software Company and US Database Leaks, Dutch RDP Sale The SOCRadar Dark Web Team has diligently documented a series of unsettling activities within the depths of the dark ...































