
What is Account Takeover and How to Prevent It?
What is Account Takeover and How to Prevent It? ...

What is Malvertising & How to Stop Ad Malware?
What is Malvertising & How to Stop Ad Malware? ...

What is Customer Identity and Access Management (CIAM)?
What is Customer Identity and Access Management (CIAM)? CIAM (Customer identity and access management) is part of the identity and access management (IAM) system integrated into applications for exter...

10 Free Security Testing Tools to Test Your Website
10 Free Security Testing Tools to Test Your Website Security testing for an application is a crucial element in the lifecycle of software testing. It restricts unwanted intrusions at multiple applic...

All You Need to Know About Endpoint Security
All You Need to Know About Endpoint Security Endpoint Security products are responsible for a market size of approximately 14 million in 2021. Regarding this market’s compound annual growth rate...

Top 10 TLDs Threat Actors Use for Phishing
Top 10 TLDs Threat Actors Use for Phishing [Update] May 18, 2023: Google has released eight new top-level domains (TLDs). Added the subheading: “Google’s New TLDs: Commercial Opportunities...

Top 10 DNS Threat Analysis and Monitoring Tools
Top 10 DNS Threat Analysis and Monitoring Tools DNS converts easy-to-remember domain names into numeric IP addresses determined by the primary network protocols of the computer services and devices to...

How to Detect Reconnaissance Using MITRE ATT&CK Framework
How to Detect Reconnaissance Using MITRE ATT&CK Framework In this article, we will look at the reconnaissance techniques from the MITRE ATT&CK framework’s point of view and discuss how to dete...

Insider Threats Rising: Average Cost of an Incident is $6.6M
Insider Threats Rising: Average Cost of an Incident is $6.6M The annual Cost of a Data Breach Report, featuring research by Ponemon Institute, offers insights from 550 actual breaches to help you unde...

What is Domain Hijacking and How to Prevent
What is Domain Hijacking and How to Prevent Domain hijacking attacks can have many damaging consequences, such as the exposure of sensitive data and financial and reputational damage to organizations....

Top 5 Tools for Phishing Domain Detection
Top 5 Tools for Phishing Domain Detection Phishing attacks have victimized many users and companies for years, and it seems they will continue to do so. Many security measures have been taken aga...

What is BEC Attack and How to Prevent it?
What is BEC Attack and How to Prevent it? BEC attack is a type of social engineering attack that takes place over email and the attacker aims for financial gain. Often, attackers aim to trick employee...

What is Spoofing Attack and How to Prevent It?
What is Spoofing Attack and How to Prevent It? In the context of cybersecurity, spoofing is the act of impersonating another entity to earn our trust, obtain access to our systems, steal data, steal m...
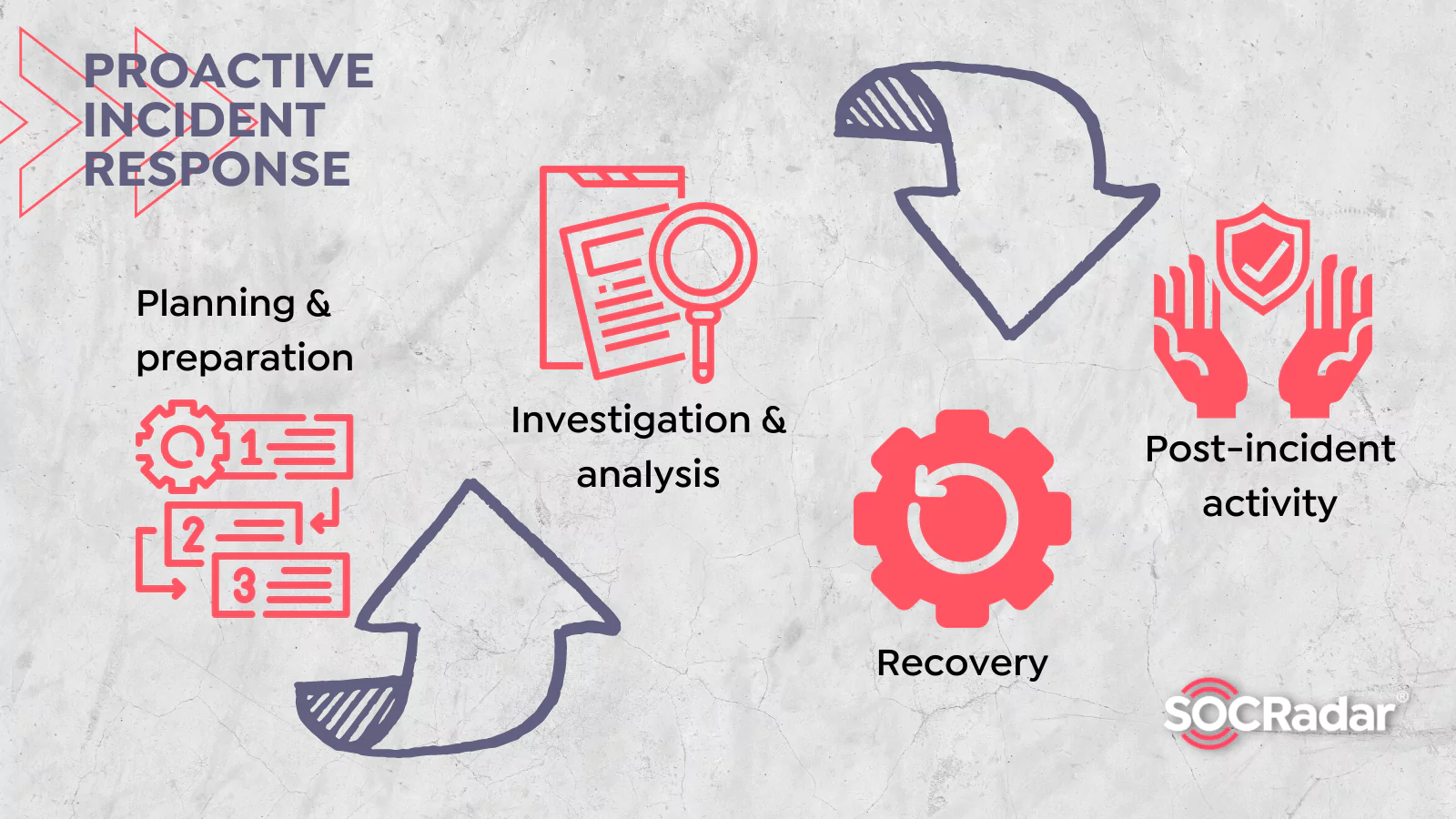
How to Build a Proactive Incident Response Plan?
How to Build a Proactive Incident Response Plan? Some standard cybersecurity measures are endpoint security tools, such as VPNs, proxies, antimalware, and employee cybersecurity awareness training. De...

New Playground for Fraudsters: How Do I Get WhatsApp Scam IoCs?
New Playground for Fraudsters: How Do I Get WhatsApp Scam IoCs? SOCRadar analysts, while investigating phishing attacks via WhatsApp, recently found a significant increase in an attack with the same t...

Cyber Threats to NGOs Increase: Half of Organizations Targeted
Cyber Threats to NGOs Increase: Half of Organizations Targeted NGOs and humanitarian nonprofits depend on digital communication technologies and software to coordinate their missions worldwide. In par...

5 Tips for Social Media Security
5 Tips for Social Media Security Social media is great but a lot of risks and threats have evolved with this social media frenzy. Financial fraud, blackmailing, phishing, invasion of privacy, and iden...
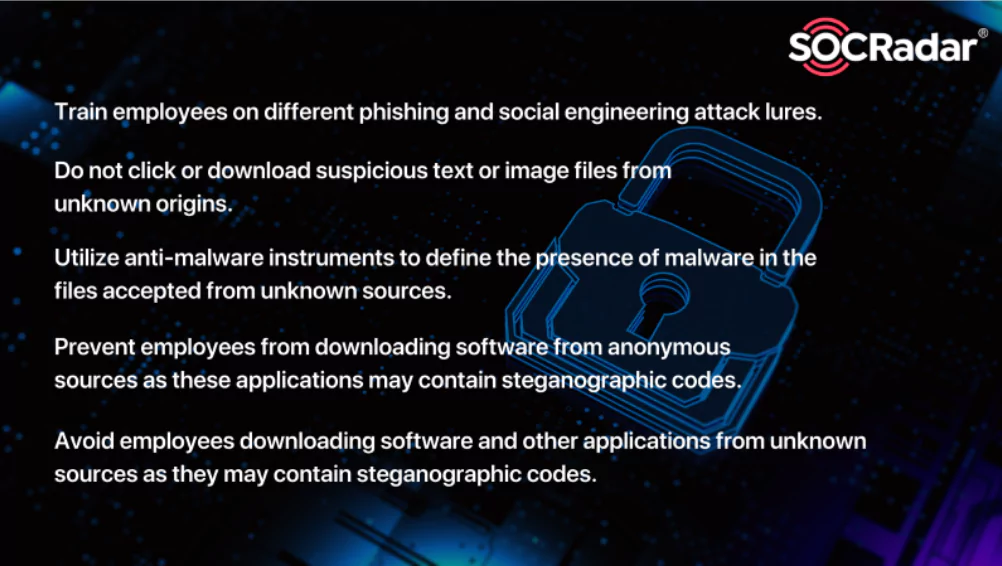
How to Prevent Steganography Attacks
How to Prevent Steganography Attacks Steganography is an antique soft craft concealing information in paintings or different art products. Most artists use this technique to hide their signatures and ...

The Ultimate Guide to Brand Protection
The Ultimate Guide to Brand Protection As technology advances toward innovation, many firms seize the opportunity to thrive on the digital network. On the other side, even criminal entities enter...

What are the Different Types of Attacks in Cybersecurity?
What are the Different Types of Attacks in Cybersecurity? A cyber attack is a sort of attack that uses numerous tactics to target computer systems, infrastructures, networks, or personal computer devi...



































