
Possible Cyber Threats in the 2024 Olympics
Possible Cyber Threats in the 2024 Olympics The design of the Paris 2024 Olympic and Paralympic torch, introduced on July 25, 2023, struck the first gong for The Paris 2024 Summer Olympic and Paralymp...

How Browser Sync Can Unknowingly Risk Your Business
How Browser Sync Can Unknowingly Risk Your Business An innocuous and maybe a hard worker employee sought to simplify their routines, inadvertently setting a sinister chain of events in motion; they ma...

New Global Phishing Scam Exposed: Facebook and Instagram Users Targete...
New Global Phishing Scam Exposed: Facebook and Instagram Users Targeted by Fake Crypto Platform The thrill of curiosity! It is the spark that drives innovation, leads us to explore new horizons, and s...

Threat-Informed Defense (TID): A Threat Intelligence Perspective
Threat-Informed Defense (TID): A Threat Intelligence Perspective Cyberattacks are increasing in frequency worldwide, posing significant challenges for organizations as they strive to protect their cyb...

Living Off the Land (LOTL): The Invisible Cyber Threat Lurking in Your...
Living Off the Land (LOTL): The Invisible Cyber Threat Lurking in Your System [Update] January 10, 2024: “Countering Living Off the Land (LOTL) Attack Methods with AI and ML” ...

The Black Box of GitHub Leaks: Analyzing Companies' GitHub Repos
The Black Box of GitHub Leaks: Analyzing Companies’ GitHub Repos This research aimed to investigate the files that companies might have accidentally uploaded to GitHub and identify any sensitive...

From Azure AD to Microsoft Entra ID: Navigating the Name Change and St...
From Azure AD to Microsoft Entra ID: Navigating the Name Change and Strengthening Phishing Defense Azure AD, now known as Microsoft Entra ID, is undergoing a name change announced by Microsoft on 11 J...

Ransomware Attacks on Banking Industry
Ransomware Attacks on Banking Industry Due to the escalating illicit pursuits of cybercriminals seeking unlawful financial gains, particular sectors and specific types of cyber attacks tend to gain pr...

Navigating the Assets Discovery Journey with SOCRadar XTI EASM
Navigating the Assets Discovery Journey with SOCRadar XTI EASM The attack surface is the sum of all potential entry points an attacker can use to gain unauthorized access to an organization’s as...

The Mindset Behind Phishing Campaigns
The Mindset Behind Phishing Campaigns Phishing attacks are cybercrimes that target individuals, businesses, and organizations. These attacks use deception and manipulation techniques to trick victims ...
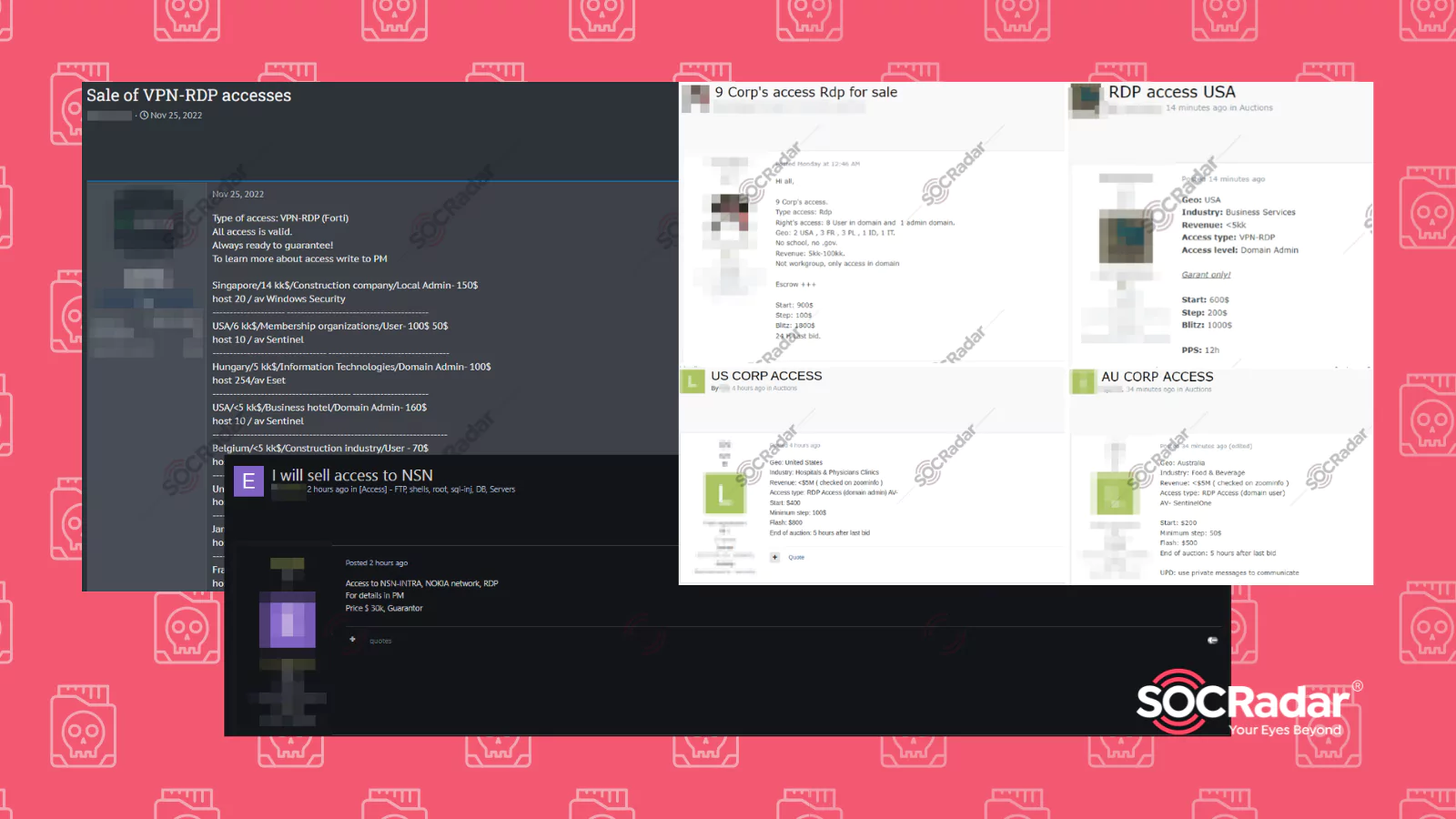
RDP Access Sales on Dark Web Forums Detected by SOCRadar
RDP Access Sales on Dark Web Forums Detected by SOCRadar Remote Desktop Protocol, or RDP, is a protocol developed by Microsoft. It allows the user to control another computer over a network connection...

Exploring the Dark Web Job Market
Exploring the Dark Web Job Market The dark web, notorious for its illicit activities, has evolved into a bustling marketplace for various illegal purposes. It serves as a hub for cybercriminals, offer...

The Surge in Cyber Attacks on Latin American Governments
The Surge in Cyber Attacks on Latin American Governments Latin America, a region bustling with potential and promise, has witnessed a worrying trend of escalating cyber threats directed at government ...

Internet-Exposed Devices within Federal Networks
Internet-Exposed Devices within Federal Networks As technology evolves and becomes increasingly integral to all aspects of society, the need for robust cybersecurity measures becomes more pressing. On...

Fake Extortion: How to Tackle and How to Verify?
Fake Extortion: How to Tackle and How to Verify? Today, one of the most critical aspects of maintaining a respectable business is to have resistance against cyber attacks. To that aim, organizations t...

Exploring Cyber Threats During the Hajj Season
Exploring Cyber Threats During the Hajj Season “More than 2 million cyber attacks were recorded from all over the world within a month” That is the summary of the cyber struggle during the last Hajj s...

Unleashing the Domino Effect: Google's Deletion of Unused Emails and t...
Unleashing the Domino Effect: Google’s Deletion of Unused Emails and the Cascade of Account Compromises Email accounts are the primary key to accessing various online services in today’s d...

The .bank TLD: Benefits and Downsides
The .bank TLD: Benefits and Downsides The world has changed rapidly since the invention of the Internet. One of the most important aspects it affected is using the Internet for banking. According to&n...

AI vs. AI: Future of the Cybersecurity Battles
AI vs. AI: Future of the Cybersecurity Battles Attacks and security solutions tailored with the help of artificial intelligence (AI) have become a trending subject in the security industry as AI bots ...

Customer Story: How SOCRadar Stopped a BEC Attack on Track?
Customer Story: How SOCRadar Stopped a BEC Attack on Track? “Hello Alice, ABC company is one of our new business partners. The invoice attached needs to be taken care of today. This is high prio...
































