
The Rise of Malicious Packages in DevOps
The Rise of Malicious Packages in DevOps [Update] July 21, 2023: On July 18, 2023, GitHub identified a social engineering campaign that targets the personal accounts of employees of technology firms, ...

What Happens on the Shadowy Lands of Vulnerability Brokers
What Happens on the Shadowy Lands of Vulnerability Brokers In the ever-growing world ofcybersecurity, vulnerability brokers have gained enough voice to be recognized as essential actors in the space. ...

Microsoft Products as an Attack Vector
Microsoft Products as an Attack Vector Microsoft is one of the big five American information technology companies and one of the leading companies in the information technology sector. With a wide ran...

How SOCRadar Can Help Fraud Teams?
How SOCRadar Can Help Fraud Teams? Fraud refers to transactions made using card information without the knowledge of cardholders in the card payment sector in cybersecurity or purchases made...

Customer Story: Social Media Takedown in the Gulf Region
Customer Story: Social Media Takedown in the Gulf Region The birth and growth of social media were one of the events shaping the last decades. It started with a straightforward idea (connecting with y...

How to Maintain Your Online Security? (2023 Edition)
How to Maintain Your Online Security? (2023 Edition) If you’re concerned about your online security and getting more nervous about that, that’s entirely normal. Every day we hear the news ...

CEO Fraud: Investigating A Gift Card Scam
CEO Fraud: Investigating A Gift Card Scam On March 8, 2023, SOCRadar announced that it received a $5 million Series A investment from 212, a leading equity fund investing in B2B technology start-ups. ...

What is Malware as a service (MaaS)?
What is Malware as a service (MaaS)? In time, the hacker underworld creates a similar model of Software-as-a-Service (SaaS). Malware as a service and SaaS have a similar duty with one main difference;...

How to Stop a DDoS Attack? (2023 Edition)
How to Stop a DDoS Attack? (2023 Edition) ...

How Easy Is It to Guess Fortune 500 Executives' Passwords?
How Easy Is It to Guess Fortune 500 Executives’ Passwords? Recently, many cyberattacks on large corporations have begun with acquiring credentials via multiple methods, particularly social ...

Secure Your Cloud Environment: 5 Best Practices
Secure Your Cloud Environment: 5 Best Practices With the increasing adoption of cloud computing, cloud security has become a major concern for businesses that rely on cloud-based services to store, pr...

Top 5 Vulnerabilities Routinely Exploited by Threat Actors in 2022
Top 5 Vulnerabilities Routinely Exploited by Threat Actors in 2022 By SOCRadar Research Day by day, it becomes harder to maintain a good security posture. Threat actors are at every corner, searching ...

Gartner Recognized SOCRadar as a DRPS Vendor in 2 Reports
Gartner Recognized SOCRadar as a DRPS Vendor in 2 Reports The digitalization process has become a norm in any business. Now, organizations’ assets are highly increased, and there are many things...
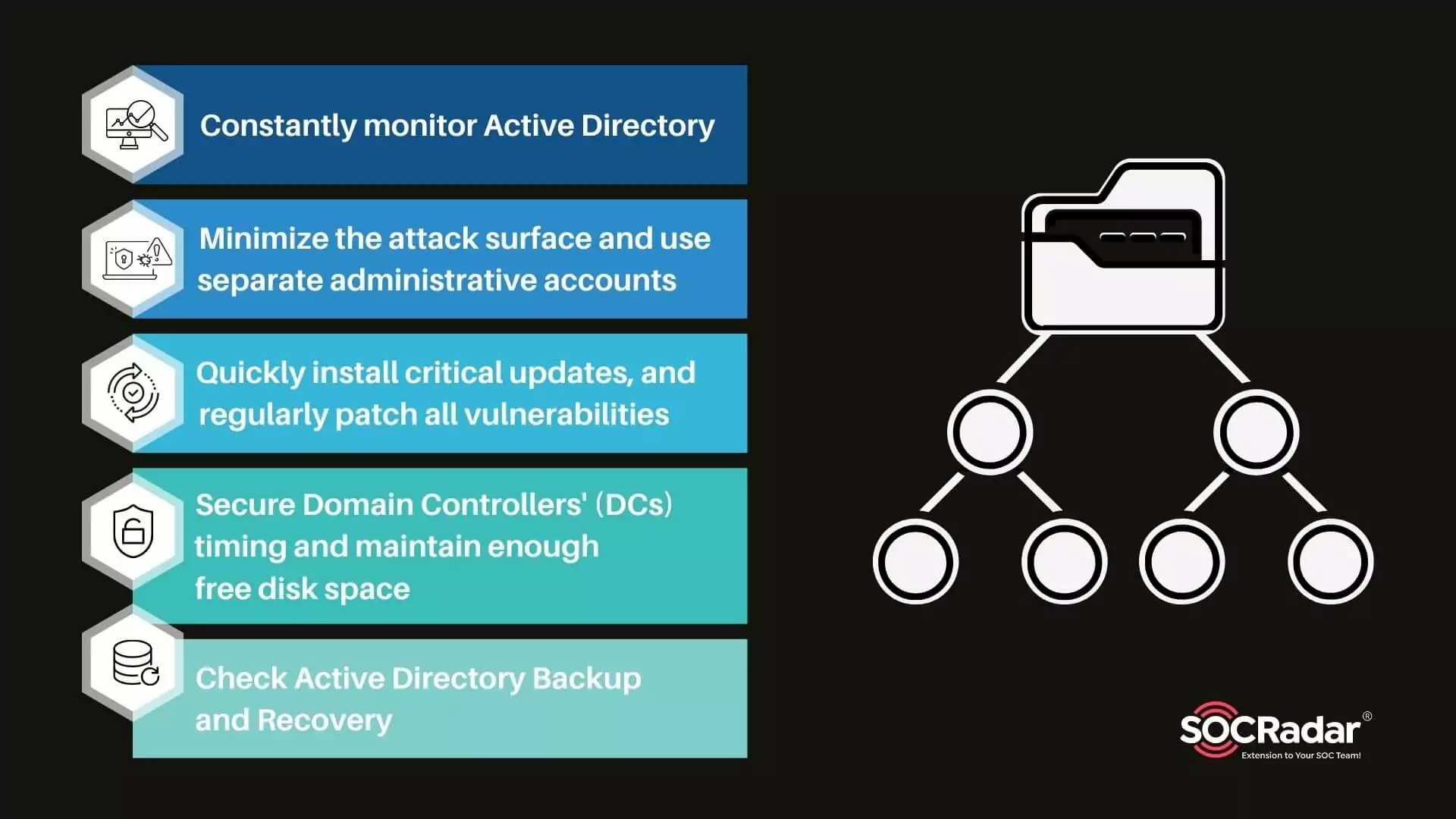
Security for Active Directory in 5 Steps
Security for Active Directory in 5 Steps Microsoft Windows directory service Active Directory (AD) enables IT administrators to manage permissions and restrict access to network resources. With this ...

Danger Lurking in GitHub Repositories
Danger Lurking in GitHub Repositories By SOCRadar Research GitHub is a system that has become the world’s largest source code repository, used by %90 of Fortune 100 companies and 94 million...

What is Password Analyzer?
What is Password Analyzer? A password strength checker is an online application that assesses the security of a user’s password in real-time by analyzing its grammar and highlighting possible vulnerab...

Vulnerability Management Best Practices
Vulnerability Management Best Practices Every day, new vulnerabilities emerge, and multiplying proliferating vulnerabilities throughout today’s complex technology contexts yield a never-ending risk ha...

How Should CISOs Prepare on the Current Cyberthreat Landscape?
How Should CISOs Prepare on the Current Cyberthreat Landscape? Recent research by John Sakellariadis for the Atlantic Council delves deeper into the emergence of ransomware over the past ten...

Top Critical Vulnerabilities Used by Ransomware Groups
Top Critical Vulnerabilities Used by Ransomware Groups As ransomware attacks have grown in popularity recently, researchers have begun compiling an easy-to-follow list of vulnerabilities exploited by ...

A New Rising Social Engineering Trend: Callback Phishing
A New Rising Social Engineering Trend: Callback Phishing Callback phishing emerged as a hybrid social engineering technique that combines phishing and vishing. The phishing technique used to steal sen...
































