
MFA Bypass Techniques: How Does it Work?
MFA Bypass Techniques: How Does it Work? Identification and authentication are the first phase of verification in the login processes of Information Systems. Malicious threat actors use various method...
Cloud Security Module: Minimize Risk of Misconfigured Buckets
Cloud Security Module: Minimize Risk of Misconfigured Buckets Not long ago, there were discussions about whether organizations should migrate to the cloud. The future has come, and almost all dig...

Better Protect Your Mobile App with SOCRadar MAS Module
Better Protect Your Mobile App with SOCRadar MAS Module Threat actors use all kinds of methods to achieve their malicious goals. Mobile apps are among the most popular targets for attackers lately. Ta...
![SOCRadar® Cyber Intelligence Inc. | What is Data Loss Prevention (DLP)? [Ultimate Guide]](https://socradar.io/wp-content/uploads/2022/10/what-is-data-loss-prevention-dlp-ultimate-guide.png.webp)
What is Data Loss Prevention (DLP)? [Ultimate Guide]
What is Data Loss Prevention (DLP)? [Ultimate Guide] Data loss prevention (DLP) prohibits users on a business network from transferring sensitive data outside of the network. DLP systems assist networ...

Recent Attack Types Against Cloud Infrastructures
Recent Attack Types Against Cloud Infrastructures ...
How XDR Powers Rapid Attack Detection and Response
How XDR Powers Rapid Attack Detection and Response A McKinsey article states that today’s organizations are expected to suffer from three major trends for the next three to five years. These trends ca...

What is Account Takeover and How to Prevent It?
What is Account Takeover and How to Prevent It? ...

What is Malvertising & How to Stop Ad Malware?
What is Malvertising & How to Stop Ad Malware? ...

What is Customer Identity and Access Management (CIAM)?
What is Customer Identity and Access Management (CIAM)? CIAM (Customer identity and access management) is part of the identity and access management (IAM) system integrated into applications for exter...

10 Free Security Testing Tools to Test Your Website
10 Free Security Testing Tools to Test Your Website Security testing for an application is a crucial element in the lifecycle of software testing. It restricts unwanted intrusions at multiple applic...

All You Need to Know About Endpoint Security
All You Need to Know About Endpoint Security Endpoint Security products are responsible for a market size of approximately 14 million in 2021. Regarding this market’s compound annual growth rate...

Top 10 TLDs Threat Actors Use for Phishing
Top 10 TLDs Threat Actors Use for Phishing [Update] May 18, 2023: Google has released eight new top-level domains (TLDs). Added the subheading: “Google’s New TLDs: Commercial Opportunities...

Top 10 DNS Threat Analysis and Monitoring Tools
Top 10 DNS Threat Analysis and Monitoring Tools DNS converts easy-to-remember domain names into numeric IP addresses determined by the primary network protocols of the computer services and devices to...

How to Detect Reconnaissance Using MITRE ATT&CK Framework
How to Detect Reconnaissance Using MITRE ATT&CK Framework In this article, we will look at the reconnaissance techniques from the MITRE ATT&CK framework’s point of view and discuss how to dete...

Insider Threats Rising: Average Cost of an Incident is $6.6M
Insider Threats Rising: Average Cost of an Incident is $6.6M The annual Cost of a Data Breach Report, featuring research by Ponemon Institute, offers insights from 550 actual breaches to help you unde...

What is Domain Hijacking and How to Prevent
What is Domain Hijacking and How to Prevent Domain hijacking attacks can have many damaging consequences, such as the exposure of sensitive data and financial and reputational damage to organizations....

Top 5 Tools for Phishing Domain Detection
Top 5 Tools for Phishing Domain Detection Phishing attacks have victimized many users and companies for years, and it seems they will continue to do so. Many security measures have been taken against ...

What is BEC Attack and How to Prevent it?
What is BEC Attack and How to Prevent it? BEC attack is a type of social engineering attack that takes place over email and the attacker aims for financial gain. Often, attackers aim to trick employee...

What is Spoofing Attack and How to Prevent It?
What is Spoofing Attack and How to Prevent It? In the context of cybersecurity, spoofing is the act of impersonating another entity to earn our trust, obtain access to our systems, steal data, steal m...
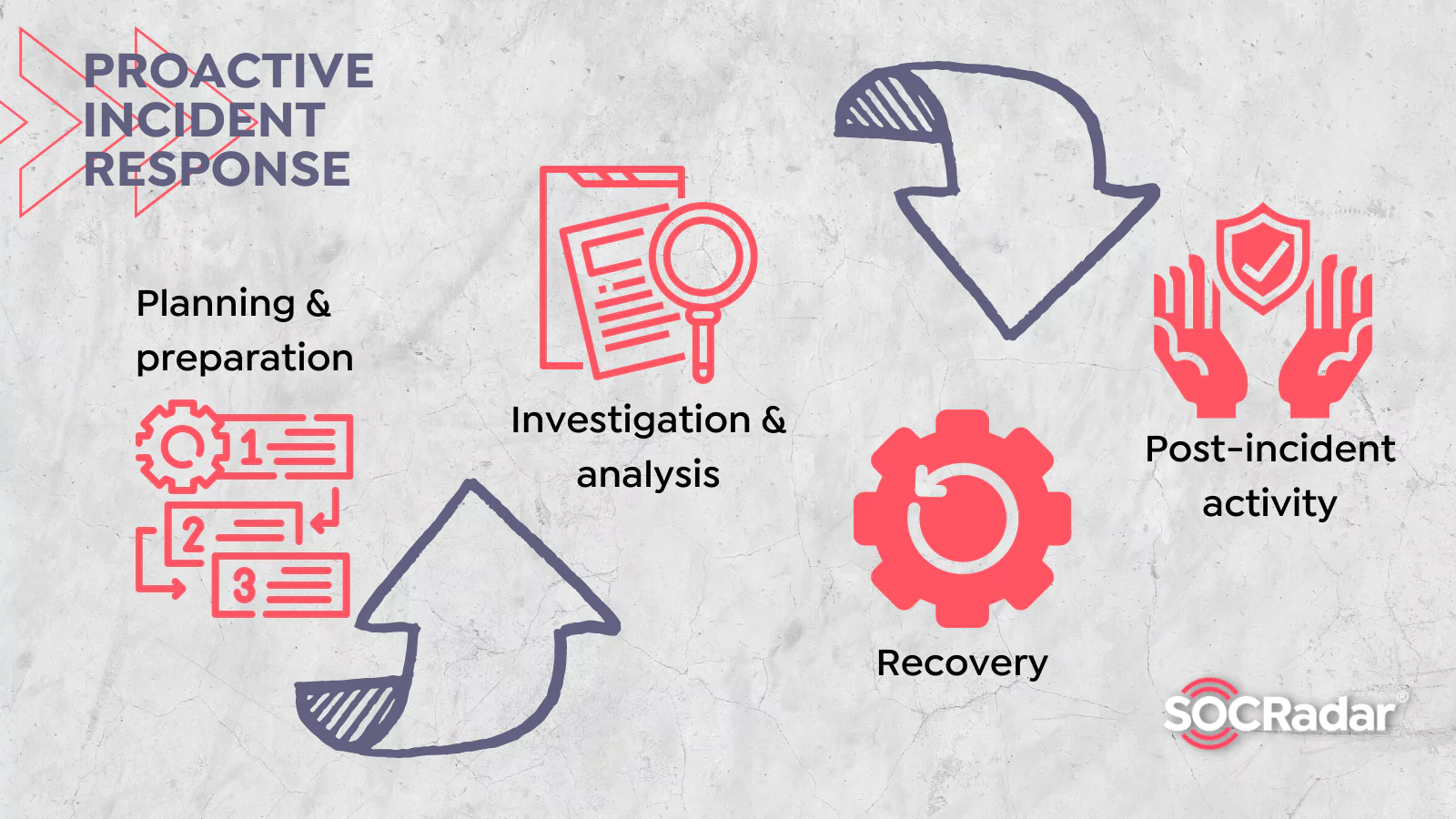
How to Build a Proactive Incident Response Plan?
How to Build a Proactive Incident Response Plan? Some standard cybersecurity measures are endpoint security tools, such as VPNs, proxies, antimalware, and employee cybersecurity awareness training. De...































