How XDR Powers Rapid Attack Detection and Response
A McKinsey article states that today’s organizations are expected to suffer from three major trends for the next three to five years. These trends can be expressed simply as follows;
- Increase in the on-demand ubiquitous data access & information platforms,
- Threat actors utilizing modern technologies like Artificial Intelligence (AI) and Machine Learning (ML) to sophisticate their attacks,
- Expanding attack surface and security gaps that new endpoints create.
The article also states that SOC Teams should use some tools or systems to tackle these issues. Briefly, these suggestions are zero-trust architecture, behavioral analytics, homomorphic encryption, a risk-based automated response, and the utilization of AI and ML in security tools. Building a secure way to implement technology and identify increasing gaps on the attack surface through appropriate security systems. As a cutting-edge security system, Extended Detection and Response (XDR) is the closest standalone security solution that includes most of the abovementioned features.
What is XDR?
As an evolved version of past security products, XDR is a modern solution that provides multi-layered protection combining many tools from different security systems. Furthermore, XDR utilizes modern technologies like AI and ML to improve itself to detect unknown threats.
Basic XDR focuses on two main security approaches these are,
- Securing endpoints and responding to suspicious events
- Monitoring network and responding to suspicious events
- Each approach requires XDR to contain detection, investigation, response, and threat-hunting elements. Furthermore, XDR uses automated capabilities and risk-based evaluation systems to decrease the false positives and workload that SOC teams must deal with.
XDR is also a cloud-based security system. This feature of XDR can provide scalability, easy integration, and high visibility of endpoint devices for large enterprises. Additionally, XDR does not require manual updates from SOC teams since it updates itself automatically. Lastly, some XDR solutions can also deliver backup and disaster recovery as a service for enterprise data protection.
How Does XDR Work?
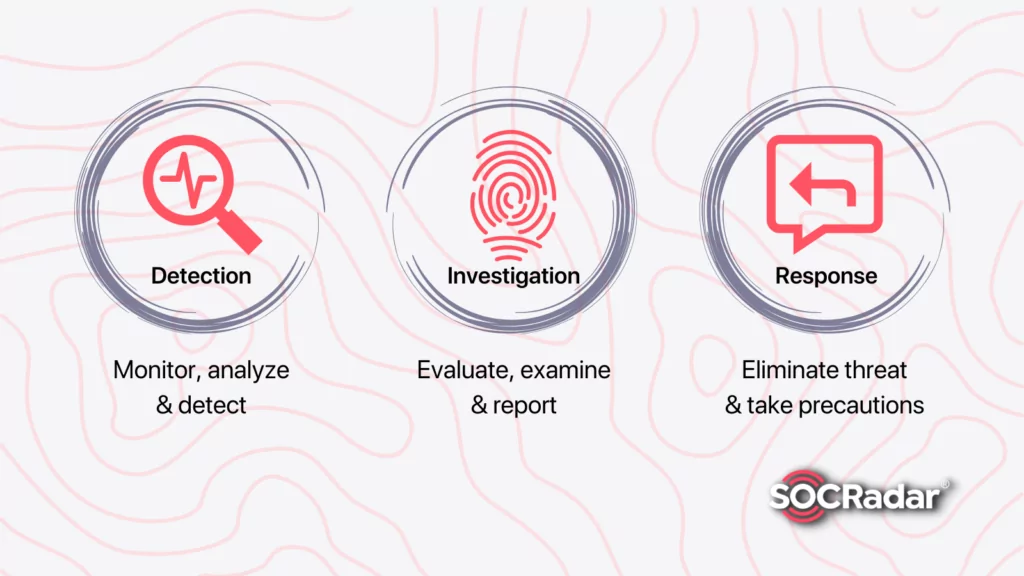
As mentioned above, XDR approaches include three primary steps detection, investigation, and response (including threat hunting). In principle, the working mechanism of XDR can be divided into these main steps.
1. Detection
XDR monitors and analyzes internal and external traffic, including network traffic, endpoint security, cloud activities, and e-mails. XDR detects a broad range of threats. XDR uses various methods to detect these threats.
These methods are signature-based scans, broadened EDR capabilities, and ML-based detection to detect multiple threats, including malware, exploits, ransomware, and fileless malware. Owing to the ML-based detection features, XDR improves itself over time to detect suspicious events and identify a threat, even in cases of zero-day threats.
2. Investigation
While detecting cyber threats, XDR systems can evaluate them. XDR can respond if the threat is a minor threat that can be eliminated automatically, regarding the severity of the danger. In the cases when XDR can’t respond automatically, XDR informs the SOC team. Due to elaborate monitoring capabilities and the centralized control panel of XDR, the SOC team can dive into specific cases and analyze the situation more quickly.
Today, most conventional security systems can detect many threats and alert SOC teams. However, this situation creates another problem, alert fatigue. According to the organization’s size, alarms created by security systems may reach high numbers.
Considering that most of these threats are either minor or false positive alarms, SOC teams may be unable to keep up. To diminish this burden, XDR can also eliminate false positives and automate most responses.
Due to its monitoring capabilities, the Extended Detection and Response product conveniently records personal behaviors to conduct post-alarm investigations. Therefore, the root cause of the cyber incident can be found, including the human factor.
3. Response
Extended Detection and Response allows SOC teams to respond to more severe alarms along with automated capabilities. Owing to cloud capabilities and control panel features for internal and external traffic, SOC teams can react to the threat and take precautions like isolating compromised devices and encrypting or wiping sensitive data on external devices.

Advantages that a Good XDR System Provides
As a modern security solution with its external and internal security responsibilities, XDR is engineered to perform some essential functions, placing Extended Detection and Response solutions in an advantageous position among the other security systems.
- Endpoint Protection: As an extended version of EDR, Extended Detection and Response products accomplish endpoint security responsibilities.
- Network Protection: Extended Detection and Response products should deal with internal and external threats, so XDR successfully protects the network from malicious activities.
- Control Panel Capabilities: Extended Detection and Response products provide a control panel for SOC teams to evaluate critical threats and enable them to investigate and respond to them. Enhanced capabilities and UI (User Interface) are essential for maximizing XDR’s control panel effectiveness.
- High Visibility: XDR products secure a visible path to sensitive data. This secure way is ensured by cloud capabilities, network protection, and extended threat protection. Therefore, the data can be more accessible between multiple platforms without affecting vulnerabilities.
- Automated Capabilities: Like threat actors adapting modern technologies, XDR has many intelligent features. These features help XDR to deal with minor threats, identify unregistered threats and enable SOC teams to work efficiently.
- Risk-based evaluation: To lessen the alert frequency and workload to investigate alerts, XDR evaluates alerts’ separate false positives, responds to threats that can automatically be handled, and show all the alarms on the control panel with all the related information.
- Behavioral Analysis: Extended Detection and Response monitors endpoints and network events, including user records. Hence post-attack investigation can be done quickly, and any user-rooted problems can be detected.
- Standalone Solution: XDR’s broad coverage can ensure cybersecurity alone instead of combining two or more security solutions. So, Extended Detection and Response has the potential to be a smoother security product that eliminates the issue of miscommunication between various security products and collects all the response actions in one control panel.
How XDR Powers Rapid Attack Detection and Response
Being a standalone product that performs multiple security product duties, Extended Detection and Response is an optimal centralized tool to ensure the organization’s security. Including the control panel capabilities that are effective on internal and external threats, XDR provides a broad range of tools for SOC teams to use in an emergency.
All the tools mentioned above and the opportunity of using them via a centralized control panel make Extended Detection and Response an effective product for detecting and responding to cyberattacks. Due to continuous monitoring on different points, the threat is detected, and according to XDR’s workflow, respective responses to the threat are delivered.
Differences Between XDR and Other Security Solutions
XDR vs. EDR: As an endpoint security product, Endpoint Detection and Remediation (EDR) is a comprehensive product to ensure security on the endpoints. It performs many of the XDR actions on the endpoints. In terms of endpoint security, what makes them different is Extended Detection and Response provides extended protection to a larger group of threats, including zero-day threat detection.
On the other hand, Extended Detection and Response covers internal network security, which EDR does not. Therefore, while EDR must be combined with another security product to protect internal and external attack surfaces, XDR can perform the same with extended capabilities.
XDR vs. MDR: Instead of being a tool to be used by organizational SOC teams, MDR is a service that includes other security products and security analyst services combined. The security products MDR offers include EDR, SIEM, and even XDR. So, the main difference between MDR and XDR is that Extended Detection and Response is used by the SOC team of the target organization. In contrast, MDR outsources this SOC service with different security products.
XDR vs. SIEM & SOAR: Security Information and Event Management (SIEM) is another specialized security product for monitoring events and alerts in case of a suspicious occurrence. Yet SIEM products lack XDR’s investigation and response capabilities, making SOC teams deal with each attention manually. SOAR, on the other hand, is a tool that extends the scope of monitored information and events that SIEM does and adds automation capabilities.
The automated capabilities include automated responses for some specific levels of threats. Like SIEM, the significant difference between SOAR and XDR is the platforms’ roles. Where SOAR is an excellent tool for monitoring systems and automating responses, Extended Detection and Response provides general security from a unified panel where SOAR can’t cover all these capabilities.
Conclusion
According to the same McKinsey report mentioned above, it is expected that the global cost of cybercrime will reach a whopping $10.5 trillion in 2025. Since threat actors are primarily motivated by money, they are expected to become more professional and sophisticated in their attacks by using modern technologies.
On the other hand, today’s business trends on device policies or data access methods create additional vulnerabilities on the organization’s surfaces.
To have a secure IT system, security products must contain many tools to handle different issues. Extended Detection and Response is a powerful candidate to tackle all the mentioned issues alone, with its broad capabilities also supported by modern technologies like AI, ML, and Cloud applications.




































