
Dark Web Profile: BlackByte Ransomware
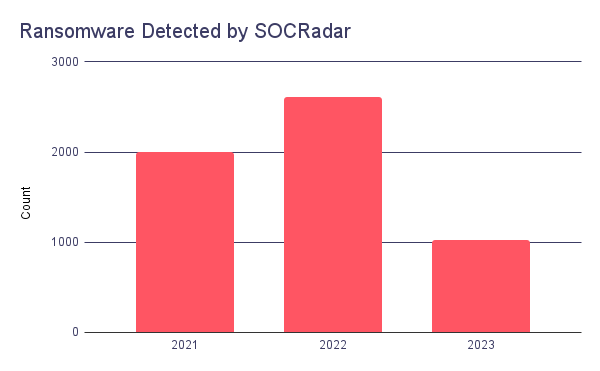
Ransomware has been one of the most glaring threats against organizations in recent years. Since 2021 SOCRadar has detected around 5,600 ransomware attacks. There was a rise from 2021 to 2022 in the number of attacks detected. This trend seems to continue in 2023 because even though it is not half of the year, there is already half the number of attacks detected compared to 2021. In 2021 total monetary damage of ransomware was around $20 billion, and it is predicted that in 2024 this amount will be $42 billion.
The importance of ransomware is reflected in research conducted by Kaspersky in 2022. The research found that even though 64% have already been victims of at least one ransomware attack, only 42% of companies would report a ransomware attack to law enforcement and a cyber security incident response service. Of the 64% that have previously been attacked, 79% have paid the ransom. Of those, 88% said they would pay the ransom again if attacked.
Ransomware attacks are frequently directed at education, government, healthcare, and manufacturing. BlackByte ransomware is among the ones that prioritize these industries with less robust security measures.
Who is BlackByte?
BlackByte is a Ransomware operation that began targeting corporate victims worldwide in July 2021. The first findings regarding the group emerged after victims sought help decrypting their files. They are a Russian-based ransomware group operating in a ransomware-as-a-service (RaaS) model and leverage double-extortion to force their victims into payment. In their first year, they caught the attention of the Federal Bureau of Investigation (FBI) and the US Secret Service (USS). These agencies released a joint advisory cautioning against BlackByte.
Which Countries and Industries Do BlackByte Target?
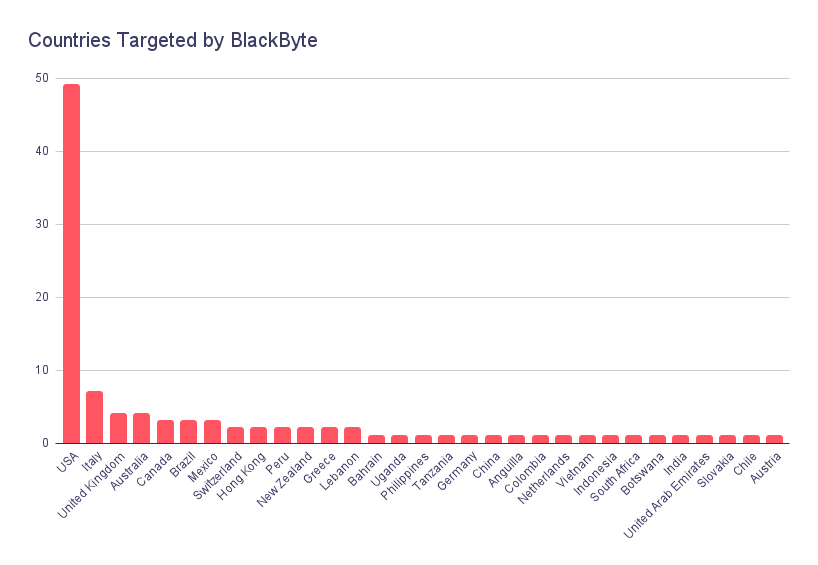
In more than 100 detected attacks, around 30 countries are targeted by BlackByte operators. Among the countries, in correlation with the other Russian-based ransomware, the US is the top target with nearly half of the attacks.
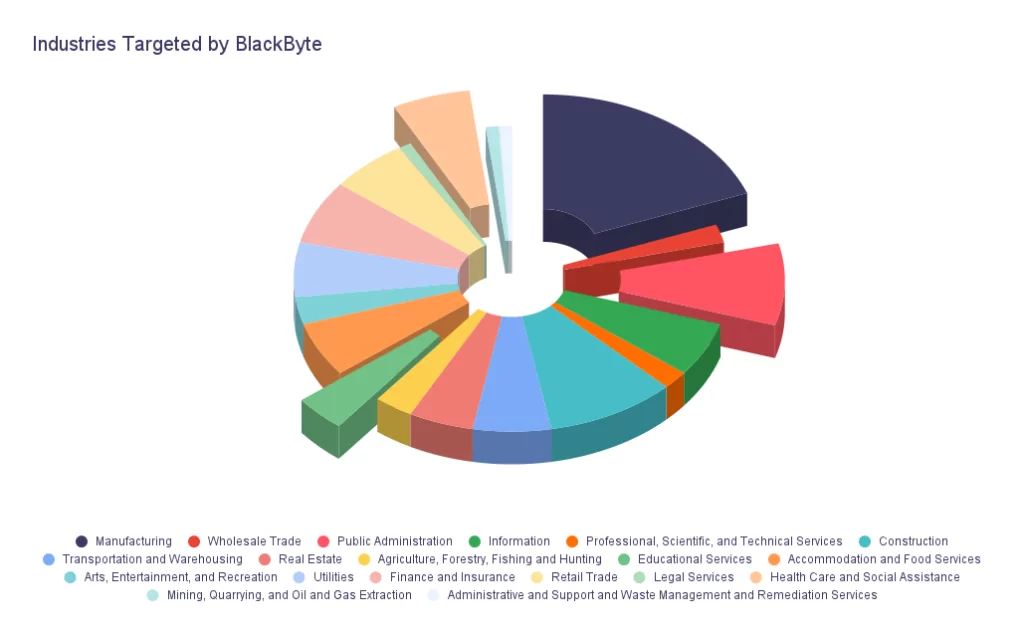
Regarding the graphic below demonstrating the industries targeted by BlackByte, manufacturing, educational services, healthcare, and social assistance are among the top targeted industries. This is in correlation with the ransomware trend in general. Ransomware operators target critical and low-security budget industries to ensure the data is vital enough for a hefty payment.
How Does BlackByte Operate?
BlackByte came into the scene with relatively low activity. According to the information reported then, BlackByte was not as active as other ransomware operations, but the researchers’ eyes were on it. They did not pose the greatest threat because of their ransomware.
The same key is used in each campaign to encrypt files in the prior variant of BlackByte. It employed AES, a symmetric key algorithm that allowed researchers to create a decrypter to help BlackByte victims. As a result, the group changed their encryption method in the newer variants. They transitioned from C# to GoLang around February 2022. This follows the trend of ransomware groups leveraging relatively little knowledge about programming languages such as GoLang and Rust. This means that it is easier to conduct static analysis in common programming languages such as C#; however, in programming languages such as GoLang, static analysis is harder. Many security products have been designed for years based on the signatures of well-known and widely used languages, so signatures of a different language can make static analysis much more difficult.
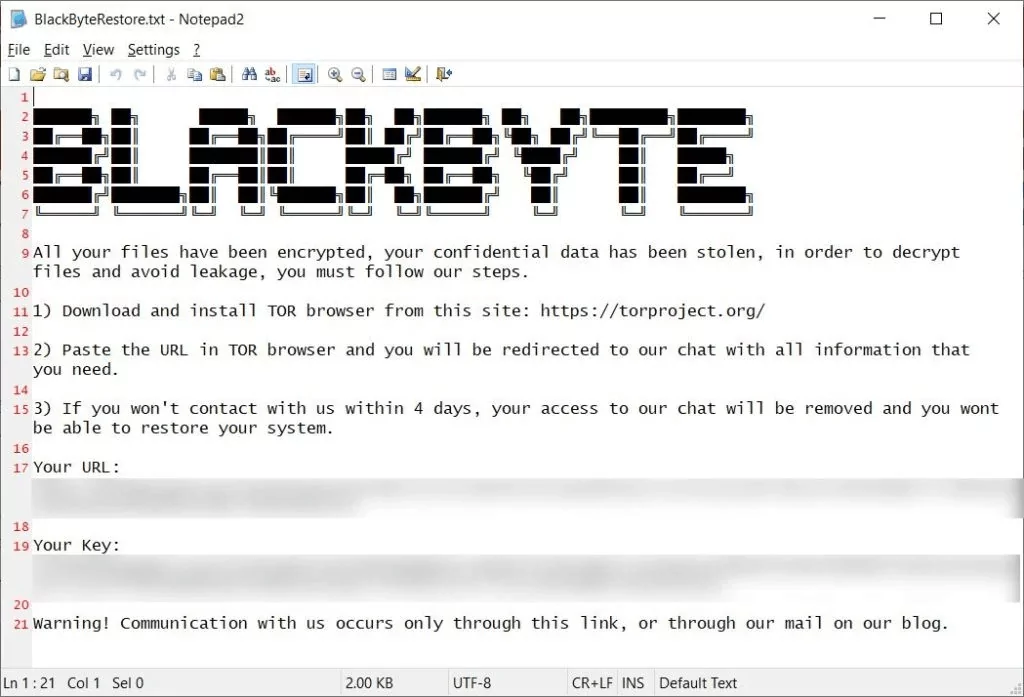
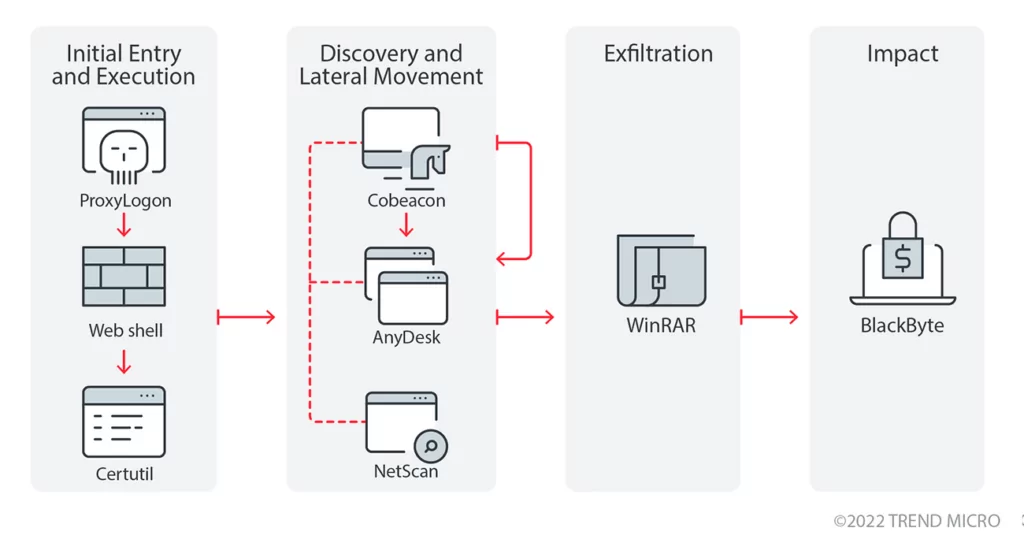
Like most ransomware groups, they leverage phishing and known vulnerabilities, such as ProxyLogon, for initial access. Another important aspect of the BlackByte is that its ransomware cannot exfiltrate data. So, they exfiltrate data before the encryption leveraging WinRAR and file-sharing sites. They also leverage legitimate tools such as AnyDesk to gain a foothold on the victim machines.
Who Are the Major Activities Regarding BlackByte?
BlackByte Exposed
Researchers released a free decryptor for the first variant of the BlackByte that victims of the BlackByte ransomware can use to restore their files. The free tool is available on GitHub.
Researchers said this process was rather simplistic than the more complex and secure encryption routines used by other gangs. The ransomware fetches a .PNG file that contains multiple keys, which researchers used to create the decryptor.
After the release of the decryptor, some researchers observed this file, which dissolved Black Byte. According to detailed analyses, the ransomware downloaded a file called ‘forest.png‘ from a remote site under their control. Although this file is named to appear as an image file, it contains the AES encryption key used to encrypt a device.
In the warning message published on the BlackByte blog, monitored by SOCRadar analysts, threat actors stated they had encountered a decryptor for ransomware. Threat actors also claim that some systems will irreversibly fail if decrypted incorrectly.
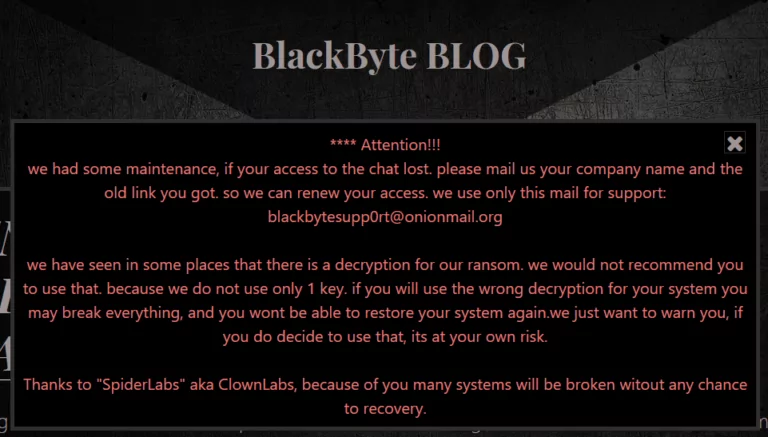
The group also stated that they do not use a single symmetric encryption key as suggested in the research but organize attacks with multiple encryption keys.
When the BlackByte ransomware gang became aware of the researchers’ report and decryption tool, they cautioned that they had used multiple keys and that utilizing the decryptor with the wrong key might damage the victim’s files.
BlackByte software also disables Microsoft Defender software before encrypting files on targeted systems. Also, like RYUK ransomware, it has a wormable feature that can infect another from the infected system.
SOCRadar analysts found that the BlackByte group has reduced its time to pay the ransom from 30 days to 12 days.
Being Near Silicon Valley Does Not Matter
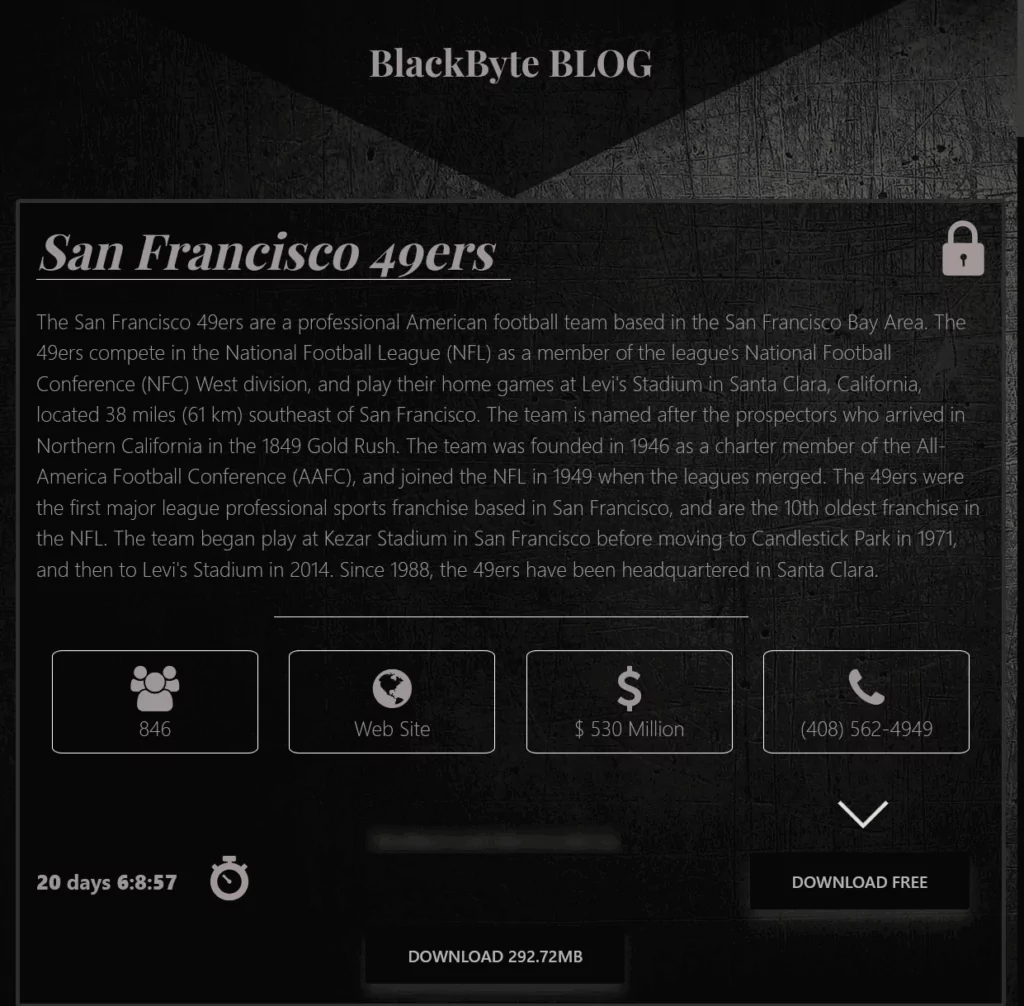
One of the most famous NFL teams, the San Francisco 49ers, was the victim of BlackByte ransomware back in February 2022. They mailed notification letters confirming a data breach affecting over 20,000 individuals following a ransomware attack that hit its network. In the stolen data, names and social security numbers were involved.
The team resides near Silicon Valley, yet the BlackByte ransomware group was successful in their attack. The group claimed responsibility before the pinnacle of the NFL, the Super Bowl, and published 292 MB of files containing invoices.
Conclusion
If we look at the lifespan of BlackByte out of context, we can say that they are a new actor in the scene. However, in the context of ransomware, they have been active for quite a long time. They have been active for two years, and less than a handful of ransomware actors can stay as active as them without getting apprehended. We can see that in the recent examples of Hive ransomware leak site overtaken by FBI and Conti imploding.
Ransomware attacks are not always successful or damaging. However, when a ransomware attack takes place, it hits heavy and forces the hands of an organization into giving up the payment. As reported in the previously mentioned research, of the 64% that have been attacked, 88% said they would pay the ransom again if attacked.
BlackByte is one of the actors to keep an eye on and prepare against, even though they have shown some weaknesses in their earlier variants. They have since adapted themselves and carried some hard-hitting attacks resulting in large payments.
Security Recommendations
- Just as most ransomware attacks, BlackByte also leverages phishing for initial access in their attacks. SOCRadar provides brand protection with its Digital Risk Protection module. With brand protection, you can proactively deny potential phishing campaigns that may arise from impersonating domains.

- One of the essential defenses against ransomware is to keep an offline backup of the systems in place. If the critical systems have backups, there is an opportunity to get back into action without paying or decrypting.
- BlackByte forces its victims’ hands by stealing the data before encrypting, which is a technique called double extortion. In this situation keeping offline backups is not enough. This situation can be prevented beforehand. Organizations should provide cyber security awareness for their employees. Also, organizations should keep track of the vulnerabilities in their environment. BlackByte leverages ProxyShell vulnerability variants in its attacks. SOCRadar provides Attack Surface Management which helps gain visibility into external-facing digital assets. With it, security teams can track the vulnerabilities in the environment. Knowing which vulnerabilities are present in the organization can limit the possible attack surface ransomware operators may exploit.
MITRE ATT&CK Techniques
|
Techniques |
ID |
|
Reconnaissance |
|
|
Phishing for Information |
|
|
Initial Access |
|
|
Exploit Public-Facing Application |
|
|
Persistence |
|
|
Scheduled Task/Job: Scheduled Task |
|
|
Privilege Escalation |
|
|
Access Token Manipulation |
|
|
Defense Evasion |
|
|
Deobfuscate/Decode Files or Information |
|
|
File and Directory Permissions Modification |
|
|
Impair Defenses: Disable or Modify Tools |
|
|
Discovery |
|
|
File and Directory Discovery |
|
|
Permission Groups Discovery: Domain Groups |
|
|
Lateral Movement |
|
|
Lateral Tool Transfer |
|
|
Collection |
|
|
Archive Collected Data: Archive via Utility |
|
|
Exfiltration |
|
|
Exfiltration Over Web Service |
|
|
Command and Control |
|
|
Application Layer Protocol: Web Protocols |
|
|
Impact |
|
|
Data Encrypted for Impact |
|
|
Service Stop |
|
Appendix
Appendix 1: IOCs BlackByte Ransomware
SHA256: 8d2581e5cc6e6fdf17558afe025ff84d9023ea636aca74dee39900d8f523e912
SHA256: 91f8592c7e8a3091273f0ccbfe34b2586c5998f7de63130050cb8ed36b4eec3e
SHA256: 388163c9ec1458c779849db891e17efb16a941ca598c4c3ac3a50a77086beb69
SHA256: 3de8fe5cee8180e93697e4ddca87e721910b9dd922de849cab7b1b3a50e54a00
SHA256: 884e96a75dc568075e845ccac2d4b4ccec68017e6ef258c7c03da8c88a59753
URL: jbeg2dct2zhku6c2vwnpxtm2psnjo2xnqvvpoiiwr5hxnc6wrp3uhnad[.]onion
URL: http://45.9.148[.]114/forest.png
URL: http://185.93.6[.]31/mountain.png

References:
- https://www.cybersecurityventures.com/top-5-cybersecurity-facts-figures-predictions-and-statistics-for-2021-to-2025
- https://www.kaspersky.com/blog/anti-ransomware-day-report/
- https://www.ic3.gov/Media/News/2022/220211.pdf
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-blackbyte
- https://socradar.io/why-ransomware-groups-switch-to-rust-programming-language/
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-blackbyte
- https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/blackbyte-ransomware-pt-1-in-depth-analysis/
- https://github.com/SpiderLabs/BlackByteDecryptor
- https://www.bleepingcomputer.com/news/security/san-francisco-49ers-blackbyte-ransomware-gang-stole-info-of-20k-people/



































