
Exploring the Dark Web Job Market
The dark web, notorious for its illicit activities, has evolved into a bustling marketplace for various illegal purposes. It serves as a hub for cybercriminals, offering opportunities for stolen data transactions, hacking services, and collaborations in nefarious activities. Within this hidden realm, job seekers can find diverse postings for roles related to cybercrime, ranging from developers to pen testers and specialized positions.
As we delve into the dark web job market, we shed light on the recruitment process, motivations, and risks involved. Society must recognize the urgent need to strengthen cybersecurity, enforce legislation, and educate individuals about the perils of engaging in illegal activities on the dark web.
The Dark Web Job Market
Dark web forums and marketplaces attract individuals fascinated by the world of cybercrime, providing them with opportunities to engage in stolen data transactions, hacking services, and collaborations for nefarious activities.
Within the dark web, job seekers can come across many postings for diverse roles related to cybercrime. These positions encompass a broad spectrum, including developers, pen-testers (penetration testers), designers, and other specialized positions. The recruitment process on the dark web often involves:
- Prospective candidates are undertaking test assignments.
- Having their CVs or portfolios reviewed.
- Even participating in interviews.
The motivations for seeking employment on the dark web can vary greatly. For some, the allure of easy money proves irresistible, especially compared to the limited financial rewards offered by conventional jobs. Others may be dissatisfied with the pay rates in legitimate industries, while the absence of stringent requirements like higher education or a clean criminal record entices some. Furthermore, during periods of crisis or layoffs in the tech industry, individuals may be drawn to the dark web job market to sustain their livelihood.
In the dark web job market, compensation is often denoted in U.S. dollars but frequently remunerated using cryptocurrencies for added anonymity. However, it is crucial to acknowledge that engaging in illegal activities on the dark web comes with substantial risks and offers no guarantee of payment. The absence of legally executed employment contracts further exacerbates this precarious situation. Individuals involved in cybercrime face the constant threat of legal consequences if their illicit activities are uncovered, and law enforcement agencies intervene.
The job postings on the dark web span various domains, covering areas such as malware development, phishing tools, website hacking, email hacking, encryption cracking, and web scraping. Each category seeks individuals with specialized skills to carry out these illegal activities. Whether it is the creation of sophisticated malware, the development of phishing campaigns, the exploitation of vulnerabilities in websites and emails, or the decryption of encrypted data, there is a demand for skilled individuals who can execute these tasks with precision and expertise.
It is important to emphasize that participating in the dark web job market and engaging in cybercrime perpetuates illegal activities and exposes individuals to significant personal risks. The absence of legal protections and the constant threat of law enforcement intervention make this realm treacherous. As society grapples with the challenges posed by cybercrime, efforts to strengthen cybersecurity, enforce legislation, and educate individuals about the risks and consequences of participating in illegal activities on the dark web become increasingly vital.
Ransomware Gang’s Recruitments
As the incidence of ransomware attacks continues to escalate, there is a simultaneous growth in the quantity of ransomware groups and their operational capabilities. These groups, which encompass a range of business models, such as Conti functioning akin to a formal company prior to disbandment, and RaaS groups like LockBit offering ransomware strains as a service, are also actively seeking collaborators and affiliates. In an audacious move, LockBit has even established its bug bounty programs, further indicating the evolution and sophistication of the ransomware ecosystem.
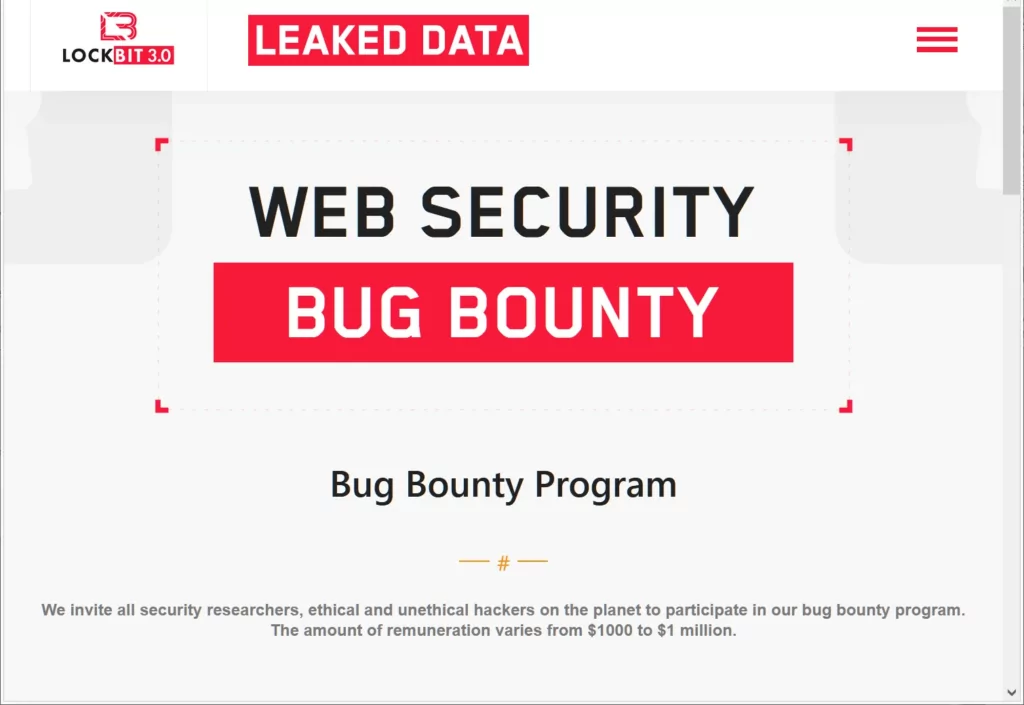
With the rise in popularity of the Ransomware-as-a-Service (RaaS) model, gaining entry into the ransomware market has become more accessible, leading to the emergence of job listings on hacker forums that were previously confined to private communication channels. These listings act as a gateway for individuals interested in participating in ransomware attacks, providing an opportunity to join established groups or start their own.
Ransomware groups actively strive to expand their operational endeavors, resulting in an ongoing demand for new labor, partners, or brokers. The positions advertised in these job listings vary, catering to a wide range of skills and expertise required to carry out successful ransomware attacks. Some common roles include developers creating sophisticated malware strains, encryption specialists devising unbreakable encryption algorithms, negotiators communicating with the targeted organizations, and money launderers facilitating the conversion of ransom payments into untraceable currencies.
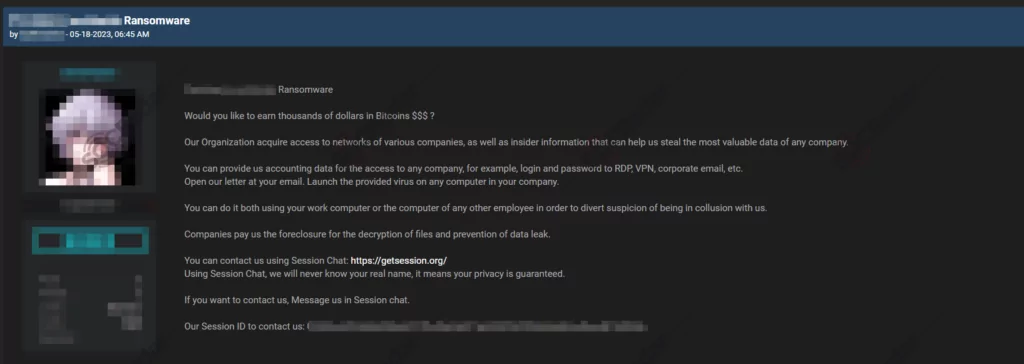
These job listings often outline specific requirements for applicants, such as technical proficiency in programming languages, experience in evading cybersecurity measures, and a proven track record of successful attacks. As the ransomware ecosystem becomes more organized, some groups even prioritize candidates with prior experience in specific industries, such as healthcare or finance, to target high-value victims more effectively.
In addition to technical skills, collaboration and communication abilities are highly valued in the ransomware job market. Cybercriminals seek individuals who can work well within a team, adapt to evolving attack techniques, and maintain discretion to avoid detection by law enforcement agencies. Successful applicants may also need to demonstrate proficiency in utilizing various underground tools and platforms, such as dark web marketplaces and encrypted messaging services.
Recent Recruitment Posts and Insights
SOCRadar has observed many recruitment ads since the beginning of 2023. Some of these postings observed in Dark Web Forums are as follows:
One Time Hacking Jobs
A common trend in the internet’s dark corners is the prevalence of advertisements seeking hackers for hire, often accompanied by requests to target specific websites. These ads typically seek the services of skilled threat actors specializing in various areas, ranging from web penetration testing to crypto wallet manipulation and corporate infiltration.
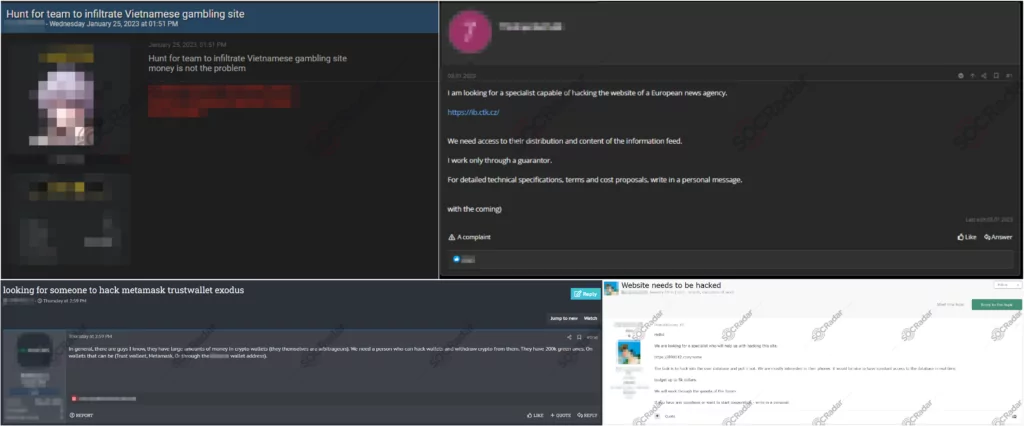
The demand for capable specialists in the world of cybercrime is extensive. Advertisements seeking to hire hackers are widespread, attracting individuals with diverse skill sets and expertise. The most desired proficiencies are manipulating crypto wallets, capitalizing on weaknesses in encryption algorithms, and penetrating corporate networks to extract valuable information.
Insider Threats
Another distinct form of recruitment advertisement focuses on enticing employees from specifically targeted companies. These posts serve a dual purpose, potentially leading to the leakage of sensitive data and creating significant vulnerabilities within the company. Insiders, individuals with authorized access to internal systems and information, can be highly sought after by various criminal organizations, ranging from Advanced Persistent Threat (APT) groups to Ransomware groups.
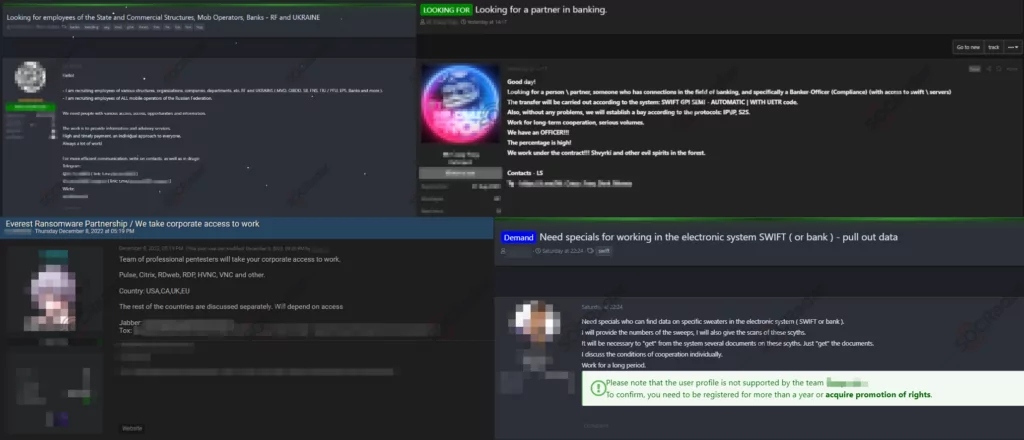
These recruitment advertisements strategically target individuals working within the desired companies, aiming to exploit their insider knowledge and access privileges. By enticing employees with promises of financial gain, coercion, or ideological alignment, cybercriminals seek to recruit insiders who can facilitate their malicious activities.
Ransomware Operators
As previously discussed, hacker forums are a common platform for various Ransomware-related posts. These forum discussions encompass a wide range of offerings, including Ransomware-as-a-Service (RaaS) propositions, RaaS opportunities for personal use, and employment opportunities within the field of Ransomware. Additionally, there is a consistent demand for skilled and malicious penetration testers who can identify vulnerabilities in systems and networks.
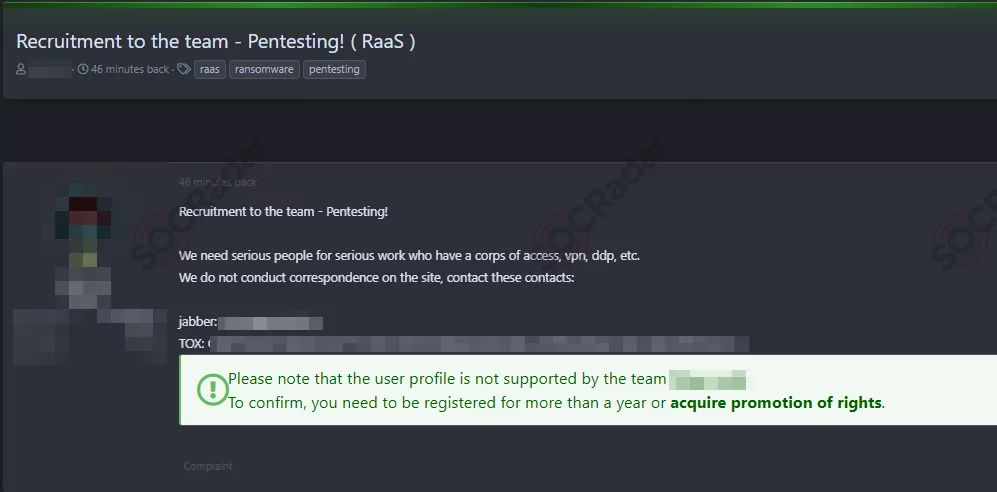
One prevalent type of post found in hacker forums revolves around RaaS. These posts highlight the availability of ransomware strains and associated infrastructure for individuals interested in launching their ransomware campaigns. RaaS offerings provide aspiring cyber criminals with the tools, support, and guidance to carry out ransomware attacks, typically in exchange for a percentage of the profits generated.
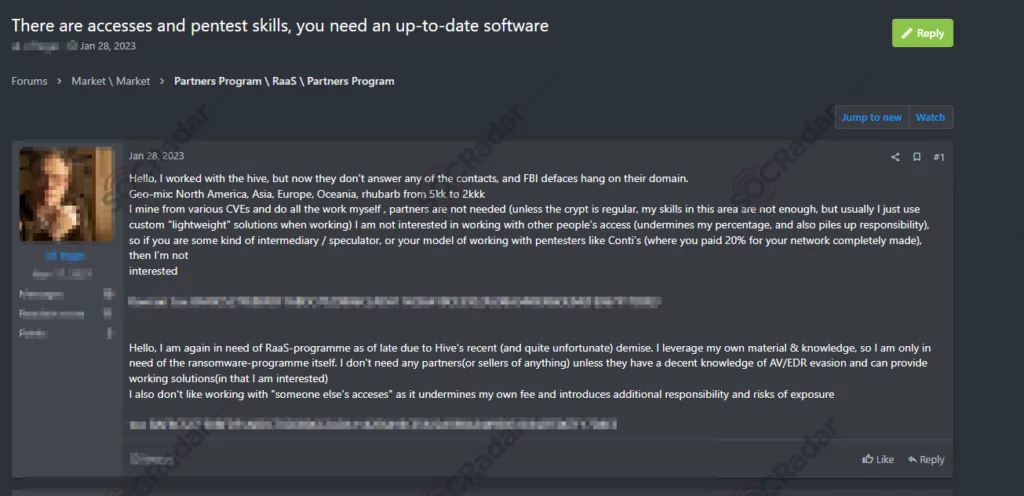
Moreover, hacker forums also witness many advertisements targeting individuals seeking employment in ransomware. These posts indicate the demand for skilled professionals with the technical expertise to develop, deploy, and manage ransomware operations. Such positions may involve creating sophisticated malware strains, orchestrating targeted attacks, negotiating with victims, or handling the financial aspects of ransom payments. Simultaneously, the search for malicious penetration testers, often called “pen testers,” remains a prominent theme in these forums.
Other Trends and Insights
In a study by Kaspersky, the following is observed in the trends in the Dark Web Job markets:
In March 2020, the dark web experienced a surge in job advertisements, potentially influenced by the economic impact of the COVID-19 pandemic. Hacker teams and Advanced Persistent Threat (APT) groups emerged as primary employers, seeking skilled individuals capable of developing and spreading malware code and building and maintaining IT infrastructure. The article shares information about the dark web job market dynamics, highlighting the range of roles, salaries, and selection criteria involved.
- Role Distribution and Salaries: Among the job ads on the dark web, developers comprised the majority, accounting for 61% of the postings. These positions also boasted the highest advertised salaries, with some reaching up to $20,000 per month. The median pay across different roles ranged from $1,300 to $4,000, with reverse engineers commanding the highest compensation at $4,000 per month.
- Legality Spectrum: The jobs on the dark web exhibited a wide range of legality, from semi-legal roles like creating IT learning courses to outright illegal activities such as hacking and running fraudulent schemes. The allure of these positions often lies in the absence of traditional employment requirements and the perceived freedom and flexibility they offer.
- Factors Influencing Job Seekers: Despite expectations of higher pay, it is worth noting that salaries on the dark web are not necessarily significantly higher than in legitimate jobs. The remuneration depends on factors such as experience, talent, and work ethic. However, specific individuals are drawn to dark web employment due to dissatisfaction with their current jobs, changes in the job market, or the impact of layoffs.
- Selection Process: Dark web employers typically adopt selection methods similar to legitimate businesses, including interviews, test assignments, and probation periods. Interestingly, one common requirement in the dark web recruitment process is the absence of addictions, such as drugs and alcohol, reflecting the need for reliable and trustworthy individuals in these underground operations.
- Employment Terms and Benefits: Remote work, full-time employment, and flexible working hours are frequently offered in the dark web job market. Cybercrime groups often entice potential candidates with additional benefits, such as promotion prospects and incentive plans. However, unlike legitimate jobs, formal employment contracts are often absent, leaving the terms of employment less structured.
Summary
In cybercrime, noteworthy outcomes are observed in the recruitment of hackers. One prominent trend is the escalating demand for skilled threat actors with expertise in various areas. These sought-after individuals specialize in web penetration testing, crypto wallet manipulation, and corporate network infiltration. Their abilities to exploit vulnerabilities and bolster websites’ security measures make them highly sought after.
Another noteworthy aspect is the targeted recruitment of insiders within specific companies. Cybercriminals strategically entice employees with promises of financial gain, coercion, or shared ideologies. By exploiting their insider knowledge and authorized access to internal systems and information, criminals aim to create significant vulnerabilities within their target organizations. This poses a considerable risk to sensitive data and overall security.
Hacker forums serve as platforms where discussions on ransomware-related activities flourish. One prevalent offering is RaaS, catering to aspiring cyber criminals. These posts highlight the availability of ransomware strains and associated infrastructure for individuals interested in launching their ransomware campaigns. RaaS provides tools, support, and guidance, typically in exchange for a percentage of the profits generated.
Moreover, there is a rising demand for skilled professionals in ransomware. These positions involve developing, deploying, and managing ransomware operations. Responsibilities may include creating sophisticated malware strains, orchestrating targeted attacks, negotiating with victims, or handling the financial aspects of ransom payments. Simultaneously, the search for malicious penetration testers, often called “pen testers” remains a prominent theme in hacker forums.
In conclusion, the future of cybercrime showcases a growing need for skilled hackers, a strategic focus on recruiting insiders, and the affiliates for ransomware for financial gain. These trends emphasize the significance of robust cybersecurity measures, employee awareness, and proactive defense strategies to combat the evolving threats in this realm.
How Can SOCRadar Help?
The dark web poses unique challenges that require specialized skills and extensive knowledge to gather threat intelligence. SOCRadar accesses critical dark web intelligence by communicating with specific communities and continuously identifying new sources. However, the large volume of dark web information can be deceptive, making accuracy challenging to determine. SOCRadar utilizes advanced data analysis tools, AI, and machine learning algorithms to overcome this challenge and offers risk scoring to prioritize threats.
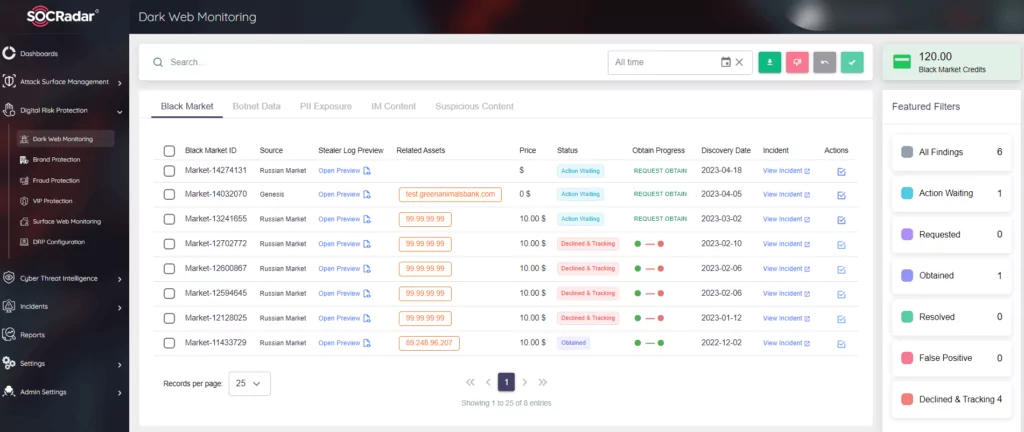
SOCRadar provides a platform for real-time monitoring, risk scoring, and automation to help organizations manage dark web intelligence effectively. It also offers sectoral and regional dark web news to inform organizations about evolving threats. With agile intelligence collection processes, SOCRadar adapts to changing environments. By leveraging SOCRadar’s capabilities, organizations can proactively protect their critical assets and data from cyber threats.




































