
Navigating Cloud Vulnerabilities: Challenges and Solutions
The cloud, in its simplest form, is a system of servers that store data and applications over the internet rather than on a computer’s hard drive. It has become an integral part of modern organizations, offering scalability, flexibility, and cost-effectiveness. It can be seen in the rise of the market size for Software-as-a-Service (SaaS), which is estimated to be worth around $185.8 billion by 2024.
As companies increasingly leverage cloud systems, the risk of attacks on their cloud services simultaneously rises. A recent report by IBM in 2023 highlighted that data breaches stemming from cloud security vulnerabilities have cost companies an average of $4.75 million USD for recovery. Such a hefty price tag encompasses the expenses of investigating and rectifying the breach, in addition to potential fines or penalties levied by regulatory bodies.
However, the ramifications of inadequate cloud security extend beyond financial implications. When customer data is jeopardized, the reputational damage that ensues can lead to a significant loss of business. The total repercussions of ineffective cloud security can be monumental, emphasizing the imperative for companies to fortify their data against potential cloud vulnerabilities. The 2023 Cloud Security Report by Cybersecurity Insiders further underscores this sentiment, revealing that a staggering 95% of security professionals harbor concerns about public cloud security. This statistic is particularly alarming as organizations are progressively adopting multi-cloud environments, amplifying the complexity and potential attack surfaces.
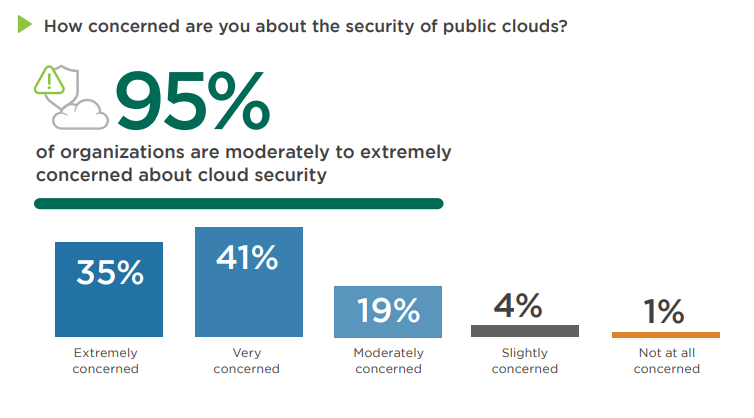
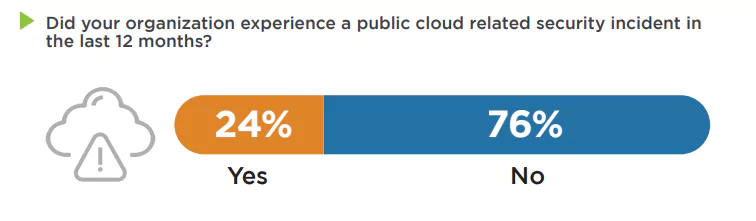
The challenges in cloud security are multifaceted. A predominant issue is the scarcity of qualified security personnel, with 43% of cybersecurity professionals highlighting this as a significant concern. As a majority of organizations utilize services from two or more cloud providers, pivotal security priorities such as preventing misconfigurations, safeguarding cloud applications, and ensuring regulatory compliance become increasingly intricate. This complexity is exacerbated by the existing cybersecurity talent gap. Barriers to robust cloud security are predominantly rooted in human and process-related factors rather than purely technological ones. According to the State of Cloud Threat Detection and Response Report by Google CAT, Security operation teams generally feel well-staffed, so cloud challenges are less about people power and more about gaps in skills and capabilities. The lack of expertise and training in cybersecurity, coupled with budgetary constraints and data privacy concerns, are the primary obstacles. Additionally, it was also reported on the previously mentioned 2023 Cloud Security Report that 24 percent of the organizations faced a public cloud-related security incident in the last 12 months. Which also highlights the attention needed to secure cloud environments.
In this article, we aim to shed light on the most pressing cloud vulnerabilities that organizations might encounter. We will delve into each one, provide real-world examples, and offer mitigation strategies. Because in the realm of cybersecurity, a proactive approach to prevention is invariably more beneficial than reactive remediation.
Improper Authentication & Authorization Management
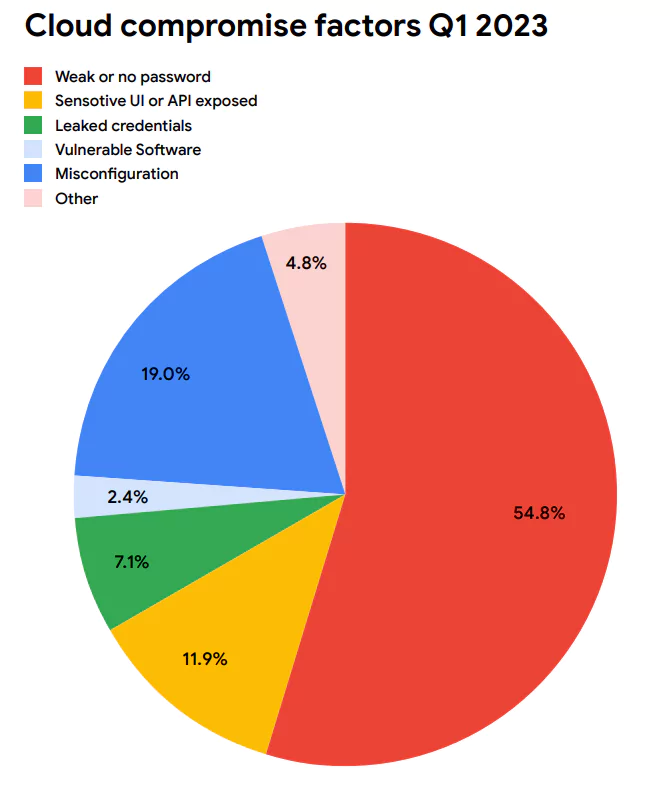
Improper authentication and authorization management stand out as a significant vulnerability. In the Google CAT’s August 2023 Threat Horizons Report, it was noted that in the first quarter of 2023, credential issues persist as a dominant challenge, constituting over 60% of compromise factors. This alarming statistic could be significantly reduced if organizations implemented stronger identity management guardrails. The essence of this vulnerability lies in the mismanagement of various identities, be it users, roles, groups, or functions. Each identity should be equipped with robust security controls and be meticulously maintained. An overlooked identity, especially one with excessive permissions or one that remains unused for extended periods, can pave the way for an undetected breach.
*Sensitive
Several factors contribute to the emergence of this vulnerability. The absence of strong password policies exacerbates the issue, enabling attackers to employ techniques like dictionary attacks or brute force to decipher passwords and gain unauthorized access. Other pitfalls include empty groups, which can be a goldmine for attackers if they gain access to Identity and Access Management (IAM) and can repopulate these groups. The widespread practice of granting excessive permissions without a valid reason, neglecting to enforce Multifactor Authentication (MFA), and maintaining inactive identities further compound the risks. Additionally, the absence of logging for AAA (Authentication, Authorization, and Accounting) operations and misconfigured IAM trust policies can provide attackers with avenues to compromise cloud environments.
To fortify cloud environments against these vulnerabilities, organizations must adopt a proactive stance. Enabling MFA across all users and applications should be non-negotiable. Instituting robust password policies, which encompass not just complexity requirements but also password expirations and administrator resets, can deter attackers. Organizations should also lean towards temporary access, meaning a rationale rotation period over static credentials and continuously reevaluate permissions to adhere to the principle of least privilege. Empty groups should be promptly deleted, and inactive identities should be monitored and removed if they remain dormant for a stipulated period. Lastly, enforcing logging and audits for all AAA operations, both at the cloud and application levels, can provide invaluable insights and early detection of potential threats.
Misconfiguration
Misconfiguration in cloud environments is a prevalent vulnerability that can lead to unintended exposure of critical information and assets. In Q1 2023, according to Google, misconfiguration was responsible for 19% of compromise factors, often intertwined with other vulnerabilities like exposed sensitive UIs or APIs. A practical illustration of this is a misconfigured firewall inadvertently allowing public access to a user interface. The repercussions of such oversights can be severe. For instance, Estee Lauder, a major cosmetic retailer, faced a significant breach due to a misconfiguration, resulting in the exposure of over 440 million records.
The root cause of such misconfigurations often stems from rapid cloud adoption, leading to hasty decisions, errors, or ill-informed configurations. The cloud ecosystem, with its various settings, policies, assets, and interconnected services, is intricate, making it challenging to grasp fully and configure correctly. This complexity is accentuated for organizations that have hastily transitioned to the cloud, especially with the rise of remote work. Misunderstanding the shared responsibility model further complicates matters. While Cloud Service Providers (CSPs) ensure the security of their infrastructure, misconfigurations can arise when assets and services are incorrectly set up by users, impacting the quality of cloud applications.
To counteract these vulnerabilities, organizations must adopt a proactive and comprehensive approach. Implementing security principles like least privilege and defense-in-depth during the initial design and planning phases is crucial. Proper cloud configuration should be rooted in robust infrastructure design and automation. Organizations should employ cloud service policies, encryption, Access Control Lists (ACLs), application gateways, Intrusion Detection Systems (IDSs), Web Application Firewalls (WAFs), and Virtual Private Networks (VPNs) to safeguard their cloud assets. Monitoring and enforcing security through cloud-based automation is vital.
Moreover, configurations should be dynamic, evolving with an organization’s cloud adoption and risk management strategies. Administrators should enforce strict policies, such as preventing public data sharing without a justified role, using tools to detect misconfigurations, and limiting access to cloud resources. Embracing a Zero Trust model, ensuring data defaults as private, and auditing access logs are other essential measures. Additionally, administrators should undergo proper CSP-specific training, enforce strong encryption methods, adhere to applicable standards, and leverage emerging security features from CSPs. Lastly, transitioning to the cloud should be well-organized, with a focus on modernizing systems, understanding data flow, and using tools like Infrastructure as Code (IaC) to minimize misconfiguration risks.
Insecure APIs
Application Programming Interfaces (APIs) have become an integral part of modern software development, facilitating communication between various software components, applications, and platforms. They enable customization and integration, allowing operators to tailor their cloud platforms to specific needs programmatically. However, with this flexibility comes vulnerability. Insecure APIs can pose significant security risks, especially when they affect encryption, authentication, and access controls. The inherent vulnerability of an API lies in the communication between applications, presenting exploitable security risks. The rapid proliferation of APIs, while enhancing service capabilities, simultaneously amplifies these security threats. For instance, cleartext credentials or unprotected credentials on cloud workloads, services, or code repositories, often referred to as secrets, can be a significant vulnerability. Such secrets, like IAM access or API keys embedded in configuration files or actual code, can lead to unauthorized access, lateral movement, and privilege escalation in the environment.
The root cause of insecure APIs often stems from their very nature. APIs are designed to handle requests from a number of sources, including mobile devices, applications, web pages, third parties, and even malicious entities like bots, spammers, and hackers also leverage this nature of APIs. This vast array of communication channels makes them susceptible to various attacks, such as code and query injection, exploitation of poor access control, or vulnerabilities arising from outdated components. The rapid adoption of cloud services has sometimes led to oversights or hasty configurations, further exacerbating the issue. The responsibility of securing these APIs does not solely lie with cloud service providers. While they offer tools and infrastructure, misconfigurations can arise when users incorrectly set up or manage their APIs, leading to potential breaches.
To safeguard against these vulnerabilities, organizations must adopt a multi-faceted approach. Implementing a web application firewall (WAF) can be instrumental in filtering requests based on IP addresses or HTTP header information and detecting code injection attacks. WAFs also allow administrators to set response quotas, ensuring that no single user can overwhelm the system. DDoS protection is another critical layer of defense, ensuring that APIs remain functional even under a barrage of requests. Organizations should also consider using cloud provider solutions like AWS Secrets Manager, Azure Key Vault, or GCP Secret Manager to securely store and manage secrets. Regularly scanning cloud workload configurations, Infrastructure as Code templates, and code repositories can help detect static credentials and keys. Moreover, it is essential to monitor access logs diligently, looking for any suspicious activity related to access keys and certificates. By combining these measures, organizations can significantly reduce the risk posed by insecure APIs and ensure a more secure cloud environment.
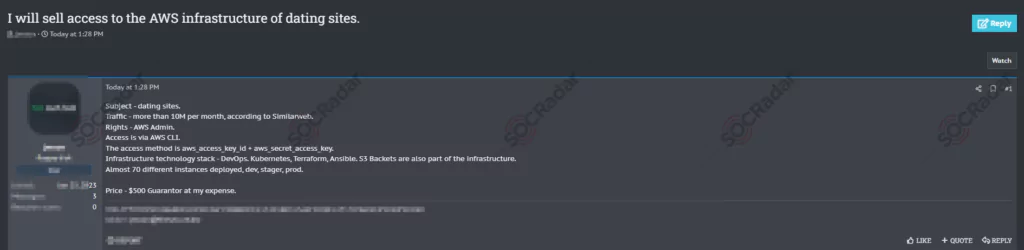
Supply-Chain Risk
The software supply chain, which encompasses the entire lifecycle of software development, presents a ton of potential vulnerabilities. From the initial development phase to the end user’s consumption, there are multiple points where malicious actors can compromise the supply chain. Even if a developer’s intentions are genuine, this does not prevent adversaries from exploiting the supply chain before the software reaches its intended users. Recent research by Sysdig reveals alarming trends: a staggering 87% of container images running in production possess a critical or high-severity vulnerability. Furthermore, supply chain threats have been responsible for significant breaches.

Why do these vulnerabilities occur? The rapid evolution and complexity of the software development landscape play a significant role. For instance, the use of container images, which are sets of files providing initial installation for workloads, has introduced new challenges. These images can be maliciously modified, creating backdoors or embedding malware, leading to a range of cloud-based attacks. Notably, compromised images can originate both internally, from untrusted sources within an organization, or externally, from public repositories or even official marketplaces lacking proper governance. Real-world examples abound: PHP’s source code repository was compromised in 2021, leading to the insertion of a backdoor. Similarly, the Russian military-sponsored Sandworm Team exploited a software update mechanism in 2017, deploying the notorious EternalPetya ransomware. These incidents highlight the multifaceted nature of supply chain risks, where vulnerabilities can arise from both misconfigurations and deliberate malicious actions.
Mitigating these vulnerabilities requires a comprehensive approach. Organizations should prioritize using images only from trusted sources and continuously monitor access to image stores, verifying their integrity and alerting for any modifications. Regular scans of VM/Container images, coupled with ensuring they are updated with the latest security patches, are crucial. And these scan should be part of CI/CD pipeline. Moreover, cloud administrators should establish clear policies regarding the use of open-source software and images, design stringent access control policies, and employ cloud-agnostic management tools. Implementing cloud-native container security solutions can further enhance protection against compromised images and other attack vectors. Tools like Kubernetes network security policies, cloud-native security solutions, and cloud application firewalls can fortify cloud security. By leveraging these tools, administrators can swiftly detect and respond to malicious activities linked to compromised images, ensuring a robust and secure cloud environment.
Conclusion
In the rapidly evolving landscape of cloud computing, the vulnerabilities and threats faced by organizations are multifaceted and ever-changing. As the cloud continues to be an integral part of modern business operations, ensuring its security is paramount. The financial, reputational, and operational implications of cloud vulnerabilities can be monumental, emphasizing the need for a proactive and comprehensive approach to cloud security.
However, organizations are not alone in this endeavor. Platforms like SOCRadar offer a holistic approach to digital risk protection, addressing the countless threats that organizations face in the cloud. From real-time threat intelligence and dark web monitoring to continuous configuration scans and third-party risk assessments, SOCRadar provides the tools and insights necessary to bolster cloud security. By leveraging SOCRadar’s capabilities, organizations can proactively defend against threats, ensuring that their cloud environments remain secure, resilient, and trustworthy.
With SOCRadar’s Attack Surface Management, organizations can continuously monitor their assets, including cloud services, third-party libraries, and cloud buckets. This constant vigilance ensures that potential vulnerabilities are identified and addressed promptly, thereby fortifying the organization’s cloud environment against threats.
In cybersecurity, prevention is invariably more beneficial than reactive remediation. As cloud vulnerabilities continue to emerge and evolve, organizations must stay vigilant, informed, and equipped with the right tools, like SOCRadar, to navigate the challenges and ensure the security and integrity of their cloud operations.
Additional References:
SaaS Market to Reach a Market Size of $185.8 Billion by 2024 – KBV Research | prnewswire
GCAT Threat Horizons Report – January 2023 | Google
Top 10 AWS Security Misconfiguration | Trend Micro
CSI MITIGATING CLOUD VULNERABILITIES – 2020.01.21 | defense.gov
Understanding Cloud Attack Vectors | CSA
Top 6 Cloud Vulnerabilities | CrowdStrike



































