
Ransomware Attacks on Banking Industry
Due to the escalating illicit pursuits of cybercriminals seeking unlawful financial gains, particular sectors and specific types of cyber attacks tend to gain prominence.
The financial sector, including the banking industry, consistently remains a primary focus for such threats. Cybercriminals are drawn to the banking industry due to its potential for lucrative rewards, and among the various cybersecurity risks that banks encounter, ransomware attacks have emerged as a particularly menacing and disruptive threat.
These attacks involve malicious actors encrypting vital data and demanding substantial ransoms for its release, resulting in institutions experiencing operational paralysis and financial vulnerability. Furthermore, when ransomware groups target institutions holding crucial data, they employ encryption to immobilize their operations, but also they engage in extortion. Their threat level escalates as they coerce institutions by exfiltrating sensitive information from the compromised systems and subsequently threatening to release it publicly.
According to SOCRadar data, even in the first half of 2023, ransomware attacks have exceeded last year’s total. However, not only is the frequency of attacks increasing. The sophistication and scope of ransomware attacks targeting banks have grown alarmingly in recent years. From small community banks to global financial companies, no institution is immune to the risks posed by these insidious cyberattacks. This blog post aims to shed light on the pervasive threat of ransomware attacks on the banking industry, examining their impact, underlying vulnerabilities, and the steps banks can take to mitigate the risks.
Increasing targeting of the Banking Industry in Recent Years
Ransomware has long been a concern for cybersecurity professionals in the financial industry, causing significant damage to institutions of all sizes for several years. Recently, there seems to be a surge in ransomware attacks targeting finance again, therefore, it seems that it will continue throughout 2023 as one of the most important cyber threats.
Various regulations strictly control banks, but this does not always seem enough. If we look at how much attacks have increased in just a few years before the current situation, in 2021, over half (55%) of financial service firms fell victim to at least one ransomware attack, a 62%increase from the previous year (2020) according to Sophos. Moreover, these attacks were not only more prevalent but also more damaging. Ransomware has evolved beyond denying access to data and now involves data exfiltration and establishing persistent network access.
Earlier versions of ransomware simply encrypted files quickly, but modern strains are stealthier and much faster. They gain network access, search for critical data, steal it, and then encrypt it, maximizing the impact before security measures detect it. This increased sophistication is more of a significant concern for financial institutions, because the financial services sector experienced an above-average increase in the complexity of ransomware attacks compared to other industries.
According to another research by Trend Micro, ransomware attacks on the banking industry increased by 1,318% in the first half of 2021 compared to the same period in 2020. Although such a large number has not yet been observed for the last 2 years, the increase continues.
Ransomware Attacks on Banks in 2023
At the end of May 2023, more than 90 companies were added to the victim list of the Cl0p Ransomware Gang due to exploiting a zero-day vulnerability on MOVEit that surfaced in the past months. While many companies are in the financial sector, at least ten banks took their place on this list. This small sample data shows how often banks are targeted among all institutions. Let’s take a deeper look at the situation this year.
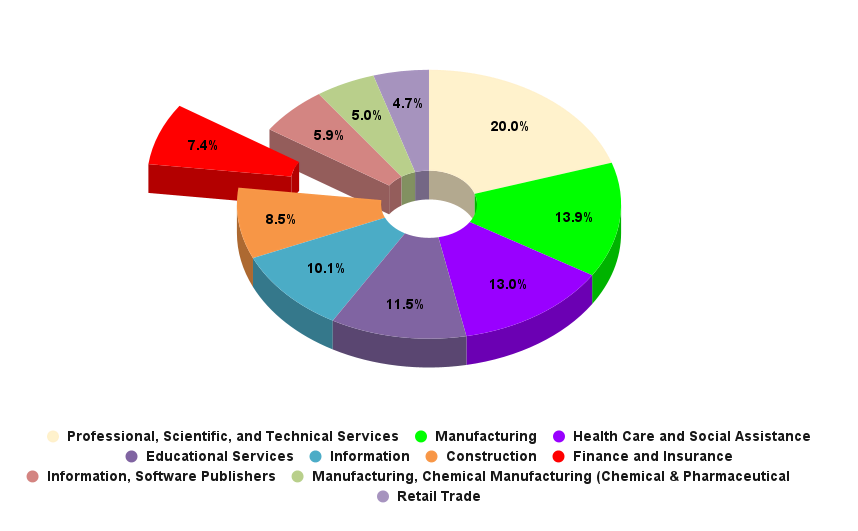
In the first half of 2023, the Finance Industry ranked 7th among the most targeted sectors. According to SOCRadar data, the number of attacks on the financial industry at the end of this year seem to approach twice as much as last year. This year has been such an intense period for the financial industry because of the threat actors that have made the financial sector one of their main targets.
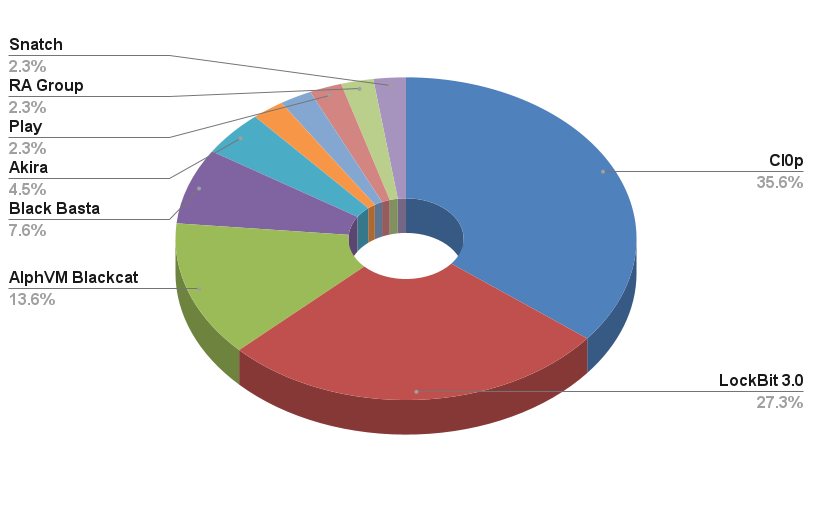
Although the potential target list of each ransom group has expanded considerably with the spread of RaaS, some groups can still stand out. LockBit 3.0 was the most active ransomware group of the last year and this year, but its incapability to passCl0p within this industry shows that Cl0p Ransomware is the most critical threat group for the financial sector this year.
Cl0p and MOVEit
On February 2, 2023, Brian Krebs, shared a post on the Mastodon platform about a newly discovered zero-day. In his post, he mentioned a remote code injection vulnerability in GoAnywhere MFT, Fortra’s secure managed file transfer solution. The Cl0p Ransomware group, based in Russia, significantly amplified the severity of this critical vulnerability. By exploiting the vulnerability in MOVEit, they managed to gain unauthorized access and launch ransomware attacks across numerous countries, focusing on the US, and the finance sector experienced a significant impact as one of the most heavily targeted industries.
For the mentioned ransomware groups, you can check our related blog posts for detailed information and the SOCRadar platform for IoCs and TTPs.
Recent Attacks Targeting Banking Industry
In 2023, dozens of large banks were targeted by ransomware, and the most significant events of the last few months were as follows.
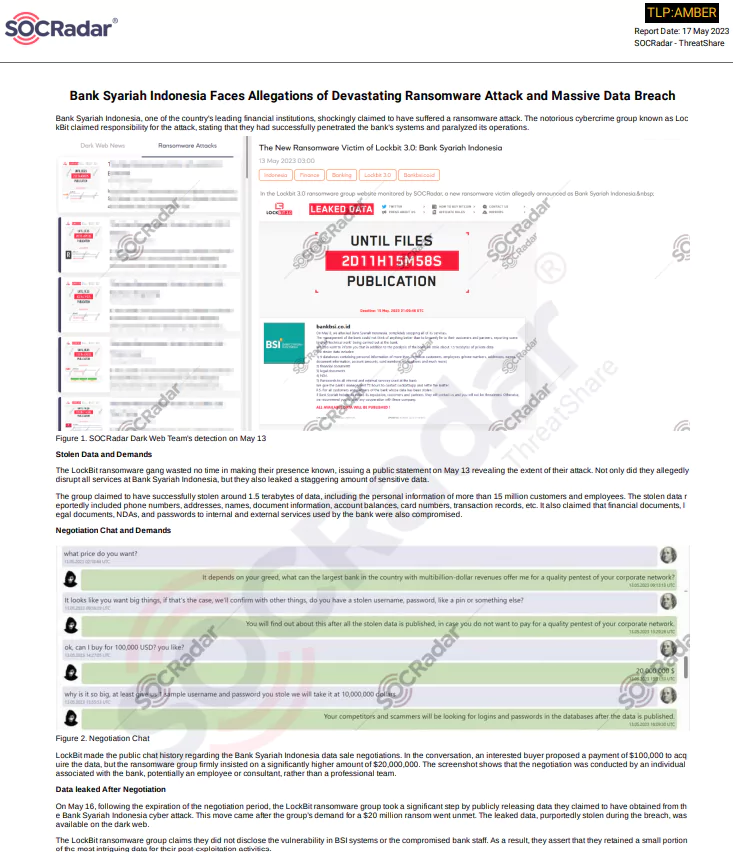
- Bank Syariah Indonesia
On May 13, Bank Syariah Indonesia, one of the most prominent financial institutions in the country, announced that it had fallen victim to a ransomware attack. The notorious cybercrime group known as LockBit took responsibility for the attack, boasting about their successful infiltration of the bank’s systems, leading to the complete paralysis of its operations.
The LockBit ransomware gang wasted no time in making their presence felt, as they publicly disclosed the magnitude of their assault on the same day. Their actions disrupted all services provided by Bank Syariah Indonesia and involved the alarming leakage of a vast amount of sensitive data.
The group claimed to have successfully exfiltrated approximately 1.5 terabytes of data, encompassing the personal details of over 15 million customers and employees. The stolen data reportedly included phone numbers, addresses, names, document information, account balances, card numbers, transaction records, and more.
- Globalcaja fallen victim
On June 2, 2023, confirmation was received that a prominent Spanish bank had fallen victim to a ransomware attack. Globalcaja, situated in Albacete, Spain, was grappling with the attack’s aftermath, which has impacted multiple branches. With over 300 offices across Spain, Globalcaja provides banking services to nearly half a million individuals, manages a consumer loan portfolio exceeding $4.6 billion, and employs 1,000 staff members.
Taking responsibility for the attack, the Play ransomware groupstated that they successfully infiltrated the bank’s systems and illicitly obtained an undisclosed quantity of highly sensitive data. The stolen information includes confidential client and employee documents, passports, contracts, and other pertinent materials.
- Most Recently, in July 2023
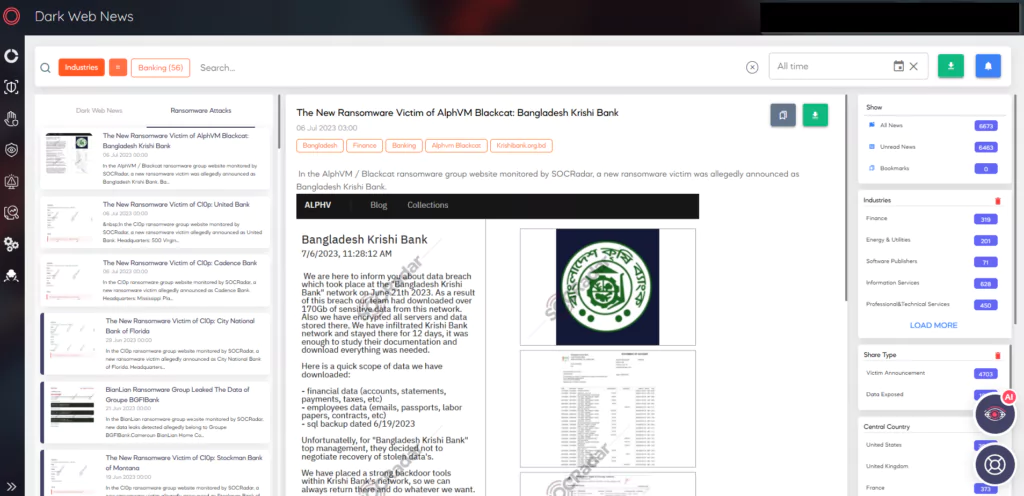
Yet, we started the first week of July with alleged attacks targeting three different banks. The victims, two US, and one Bangladesh-based banks, are Bangladesh Krishi Bank, United Bank, and Cadence Bank. One of the threat actors responsible for the attacks is AlphVM Blackcat, which is also a dangerous and active group, while the other two belong to Cl0p Ransomware. There has been no response or explanation from the banks for now.
Ransomware is Particularly Dangerous for Banks
According to the Center for Strategic and International Studies, the reason why cybercriminals target banks is straightforward: “banks are where the money is.” Attacking banks provides cybercriminals with numerous opportunities to profit through extortion, theft, and fraud. Additionally, nation-states and hacktivists also view the financial sector as a prime target for exerting political influence and advancing their ideological agendas.
According to another report published by the U.S. Treasury Department’s Financial Crimes in 2021, it was revealed banks and financial industries lost money due to a total of $1.2 billion in ransomware payments in a year, and banks were found to be the second industry with the highest ransomware cost after healthcare. Considering that the remediation cost is not included in this astronomical number, the seriousness of the situation becomes apparent.
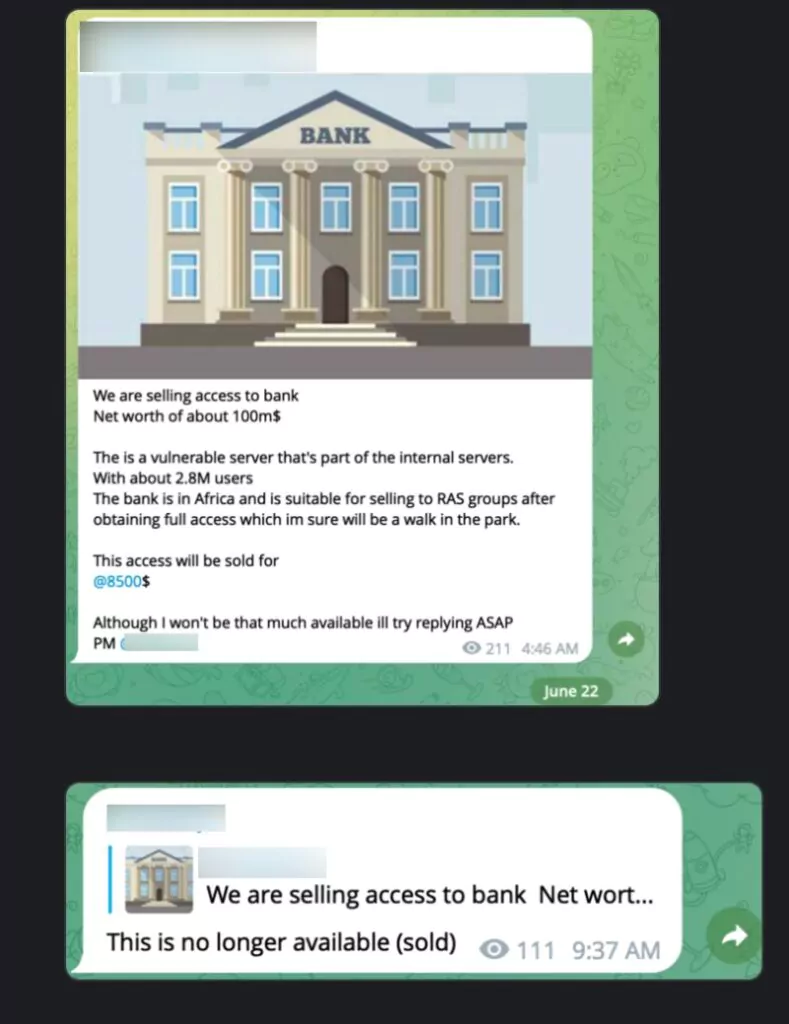
Moreover, as mentioned above, with the escalating ransomware menace, threat actors find Banks a particularly enticing target through other means too, such as initial access and database sales. While infecting targets with ransomware and demanding ransom is an obvious lucrative approach, initial access sales are also sold at high prices within a short timeframe. Extracted databases are similarly sold at high rates, perpetuating a pyramid scheme that amplifies the impact within the digital landscape, creating a snowball effect.
The Reasons and Mitigation Methods
Now that we have discussed the growing threat, we can also examine the causes of this situation and how to take actions against it.
Double-Extortion Opportunities
Financial organizations possess vast amounts of sensitive data, including information about customers, partners, and authentication data. This makes them ideal targets for double-extortion attacks, where cybercriminals first steal data and then encrypt critical systems. They leverage the threat of releasing the stolen data to pressure the company into paying the ransom, as the exposure of such data could severely damage the institution’s reputation and erode trust, making them more likely to comply with the demands. Mitigation methods for this are:
- Implement a robust backup and disaster recovery strategy to ensure critical data is regularly backed up and can be restored quickly during a ransomware attack.
- Conduct regular data classification assessments to identify and prioritize sensitive data, allowing for targeted protection measures.
- Implement a well-designed segregation of duties plan and access control, you can effectively limit the movements of attackers within your network, even if they manage to gain initial access.
- Implement Data Encryption, especially for most sensitive data. By doing this, process the data as encrypted in rest, transit, and in use as much as possible, ensuring that the threat actors have useless data in case of extortion.
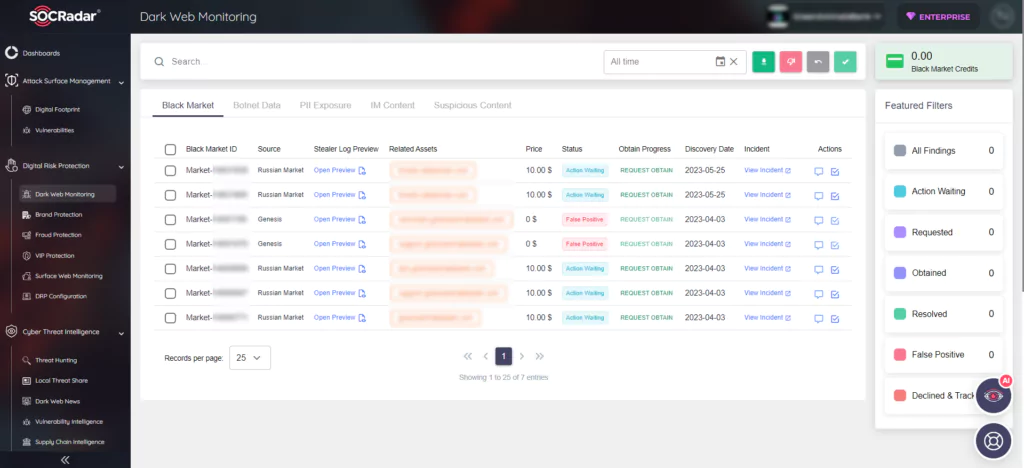
SOCRadar can help organizations identify and monitor potential data breaches by continuously scanning both the surface web and the dark web. This proactive monitoring enables early detection of stolen data and allows organizations to take immediate action to mitigate the impact. Mitigation methods for this are:
Expanded Attack Surface
As the financial industry embraces technological advancements, such as artificial intelligence, data analytics, and cloud technology, digital transactions and operations become more prevalent. While these advancements enhance efficiency, they also create a wider attack surface for cybercriminals to exploit.
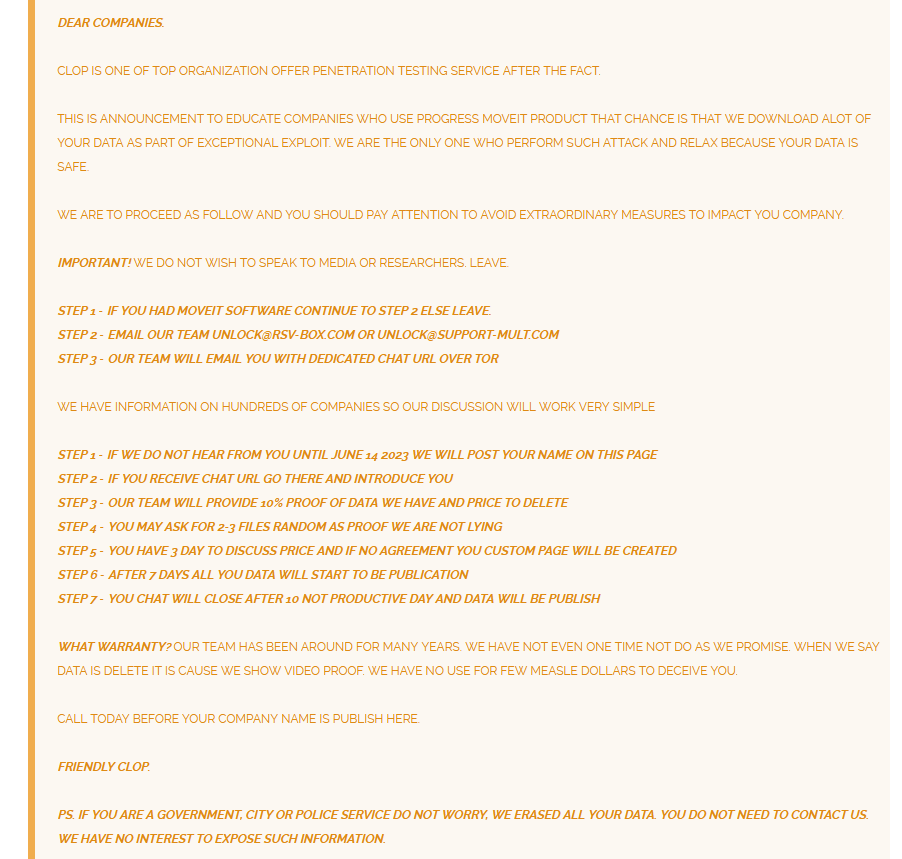
One of the best examples of this situation is again MOVEit software, which was also trojanized through a supply chain back in 2021, and in 2023 many other organizations were targeted by ransomware through the zero-day vulnerability of MOVEit.
Financial institutions engage with third-party providers, collect more data, and implement new digital systems, resulting in a complex network of data and communications. Cybercriminals can exploit vulnerabilities in these interconnected systems, finding indirect paths to infiltrate larger target institutions. Mitigation methods for this are:
- Implement a comprehensive vulnerability management program to regularly identify and address vulnerabilities across systems and third-party integrations.
- Adopt a zero-trust security model, which assumes that all network traffic and devices may be compromised, and implement strict access controls and segmentation to limit lateral movement in the network.
- Conduct regular security assessments and penetration testing to identify and remediate vulnerabilities proactively.
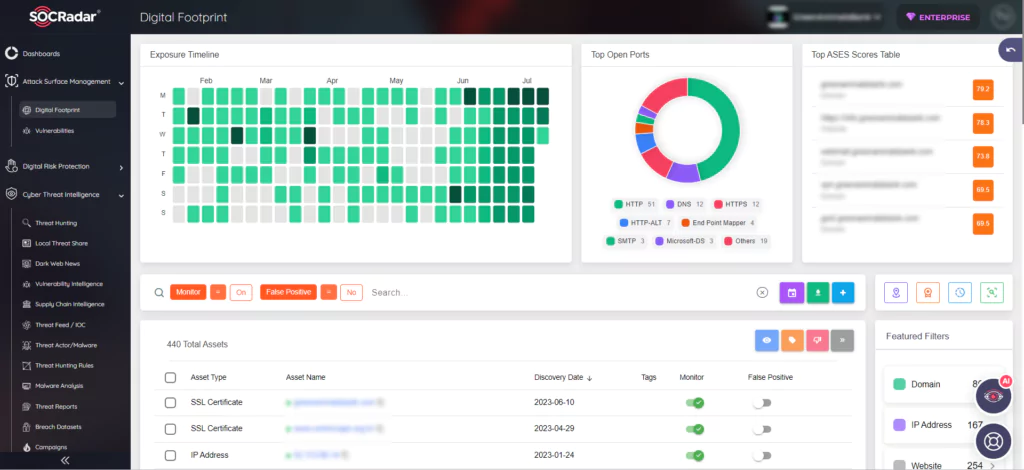
SOCRadar’s Vulnerability Management capabilities can help organizations identify vulnerabilities in their systems, including third-party integrations. By regularly scanning and assessing the security posture, organizations can prioritize and address vulnerabilities promptly, reducing the risk of exploitation.
Complex Task of Securing Digital Assets
Managing and securing digital assets within financial organizations is a challenging endeavor. Existing systems are intricate and continuously evolving, requiring constant updates and monitoring to combat evolving threats. Professionals in the field need ongoing training to keep pace with the ever-changing digital landscape and emerging risks. Mitigation methods for this are:
- Stay up to date with the latest cybersecurity technologies and solutions, including next-generation firewalls, endpoint protection, and network monitoring tools.
- Implement Security Information and Event Management (SIEM) systems to enable real-time monitoring, threat detection, and incident response.
- Engage in partnerships with trusted cybersecurity service providers to enhance expertise and gain access to advanced threat intelligence.
Rapid Digitization
In the pursuit of convenience and automation, the financial sector has rapidly digitized its services. Web portals and banking apps aimed at simplifying financial processes inadvertently increase the vulnerability of banking systems. The Financial Services Information Sharing and Analysis Centre (FS-ISAC) reports that this rapid digitization has led to a surge in global cyber threats. Mitigation methods for this are:
- Prioritize security during the digital transformation process by conducting thorough risk assessments and incorporating security controls into new digital systems and applications.
- Adopt a risk-based approach to cloud security, ensuring proper configurations, encryption, and access controls are in place.
- Regularly review and update security policies and procedures to account for the changing threat landscape and new technologies.
SOCRadar can take down phishing sites that mimic your organization with its integrated takedown feature during and after the digitalization process, and can operate this process in the mobile environment with the Rogue Mobile Application module.
Cloud Adoption
Cloud computing has revolutionized the financial industry, offering cost-effective and efficient IT infrastructure solutions. However, the risks of cloud misconfiguration pose significant consequences for data security. Inadequately secured cloud networks can be breached, leading to the exposure of sensitive information, passwords, and confidential data. Mitigation methods for this are:
- Implement robust authentication mechanisms, such as multi-factor authentication, to protect cloud accounts and prevent unauthorized access.
- Employ cloud security tools and services that provide real-time monitoring, threat detection, and incident response capabilities.
- Regularly audit and review cloud configurations to ensure compliance with security best practices and industry standards.
SOCRadar Cloud Security Module can notify you when new cloud buckets connected to your organization are discovered and update you on their status. SOCRadar CSM constantly monitors the status of your buckets and sends a “Cloud Bucket Status Change” alert if there is a situation.
In summary, these factors have made the financial sector an attractive and accessible target for cybercriminals. Understanding the specific challenges faced by financial institutions is crucial in comprehending how they are being targeted and developing effective strategies to counter ransomware attacks.


































