Top 10 Targeted Industries and Countries in 2022
No matter the industry, cyberattacks can cause various problems, ranging from minor disruptions to significant losses or, even worse, lawsuits against your organization.
Threat actors could target a business in any industry in hopes of compromising their digital assets. Although, being the victim of an attack not only results in lost productivity but also harms one’s reputation.
Download SOCRadar’s 2022 End-of-Year Report to gain insights into industry and country-related threats.
How to Assess the Risk Posed Toward an Organization?
The legacy threat intelligence services mostly offered feeds and IOCs (Indicators of Compromise) to organizations. These outputs were almost generic and non-actionable. Nowadays, organizations require the latest intelligence about themselves as well as real-time intelligence on threat actors, botnets, and malware. Organizations must be able to identify and take down phishing websites targeting their consumers as soon as these websites go live.
The way SOCRadar ensures this is to follow the communication channels of threat actors closely. These channels include but are not limited to forums and markets, Telegram channels.
Here are the top industries that are discussed the most on the dark web’s communication channels:
- Government
- Finance
- Cybersecurity
- IT
- E-commerce
- Media & Entertainment
- Cryptocurrency
- Education
- Telecommunication
- Healthcare
What Motivates Threat Actors to Target These Industries?
Threat actors primarily target industries that are more critical to manage, where disruption might cause big trouble. Attacks may be motivated by monetary, political, or other factors. Refer to the notes below to see what the attackers are aiming for:
Government: Government institutions are typical targets for cybercriminals. They store sensitive information, including financial data, classified documents, and citizen records. Hackers can use this data to achieve their goals.
Finance & Crypto Currency: Another popular target for cybercriminals is organizations like banks, investment firms, and cryptocurrency exchange platforms/wallets. These businesses have access to a huge amount of financial information that can be used for theft or fraud. This financial information includes credit card numbers, bank account details, and social security numbers.

Cyber Security: Because of their tools’ extensive access to corporate and governmental clients worldwide, security firms have been a frequent target for nation-states and hackers. Spies and hackers can access victims’ systems by breaking into those tools and stealing the source code.
E-Commerce: With new technologies, automated tools, and bot armies, the threat landscape for e-commerce is growing. E-commerce businesses are aware of the growing cybersecurity concerns and are taking appropriate action. However, large and small e-commerce stores remain the primary targets of web skimming attacks, extortion, vulnerabilities, and other threats.
Media & Entertainment: Companies in the media and entertainment industry must safeguard customer data, which contributes to a large attack surface, and ensure content security. These companies are most likely to be subject to data protection regulations.
Telecommunication: Telecommunication companies keep sensitive information about their customers, such as names, addresses, phone numbers, and financial information. Customers are likely to be the target of phishing scams if a telecommunication company falls victim to a cyberattack.
Education: Numerous private records, including those of students and faculty, financial data, and research data, are kept by educational institutions. Cybercriminals could make use of all this data.
Healthcare: Considering how much Personal Identifiable Information (PII) healthcare organizations store on their systems, they are particularly at risk of cyberattacks. Identity theft happens when PII is free to roam. You can read our blog to learn more about cyberattacks in the healthcare sector.
The ransomware incidents involving the healthcare industry are even more concerning. Patients’ health is directly impacted when hospital systems are held captive in these attacks. Patient information and medical histories are no longer accessible to doctors.
Top 10 Industries Targeted by Ransomware and Extortion Gangs
Since the ransomware and extortion gangs do not follow the same patterns as the rest of the cybercrime world and are very picky about going after certain types of targets, the intelligence about these gangs needs to be differentiated from other dark web intelligence.
Analysts at SOCRadar keep an eye on these gangs through the standard methods in addition to the affiliated blogs and forums.
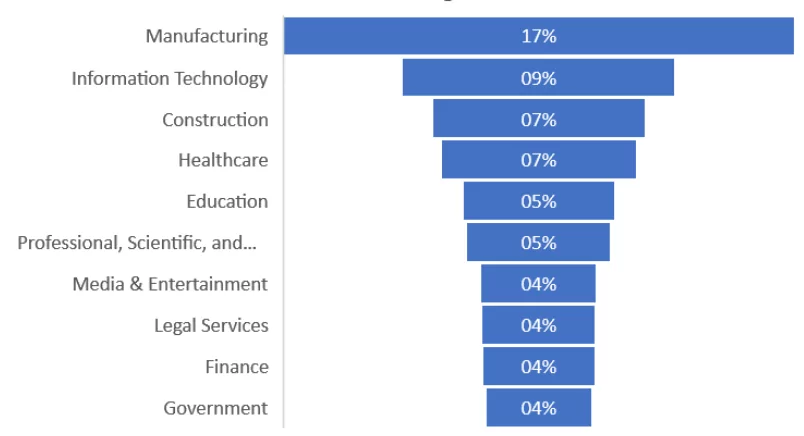
The top industries targeted by ransomware threat actors differ from those mentioned in dark web posts. The graph shows that ransomware actors choose industries that cannot be stopped.
Every minute lost is lost revenue in industries such as manufacturing, information technology, and construction. In healthcare, a disruption could cost lives. Therefore, pressure starts to build up on victims from the first moment.
But why is manufacturing the top industry for ransomware actors? Cybercriminals might target manufacturing companies in order to harm their equipment or products physically. This could result in injuries, deaths, and billions of dollars in losses. Also, hackers who want to steal intellectual property, such as product designs, frequently target them.
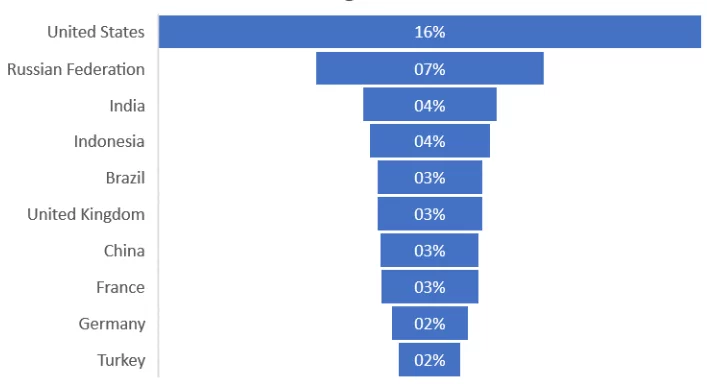
Top 10 Countries Targeted by Threat Actors
There is no single answer to why one nation is targeted more than another. Still, a larger country equates to more devices, which indicates a larger attack surface for attackers to exploit.
Other significant factors include the level of cybersecurity awareness across the country and the existence of more important targets like infrastructure or companies.
SOCRadar brings fresh and actionable threat intelligence to its customers. The way we ensure that is to follow the communication channels of threat actors closely. These channels include but are not limited to forums, markets, and Telegram channels.
In addition, most of these posts are about trading and exchanging data.
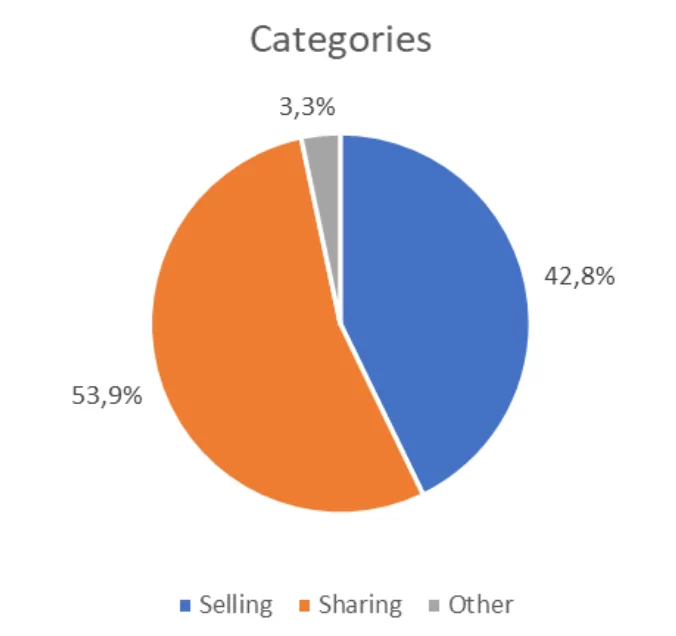
The other 3.3% is about buying data, hacking and target announcements, and partnership/cooperation offers.
Top 10 Countries Targeted by Ransomware and Extortion Gangs
Ransomware gangs do not follow the same trends as the rest of the cybercrime world and can be very selective about their targets. Therefore, again, the top 10 are ranked differently for ransomware actors.
In our CTI solution of SOCRadar Platform, you can find intelligence about ransomware and extortion gangs in a different categories.
SOCRadar analysts follow these threat actors in communication channels and forums or blogs.

Except for Brazil and China, 8 of the top 10 targets belong to North America, Europe, and commonwealth countries.
What has been shared in these channels are the announcements of victims and exposed data of uncooperative victims.
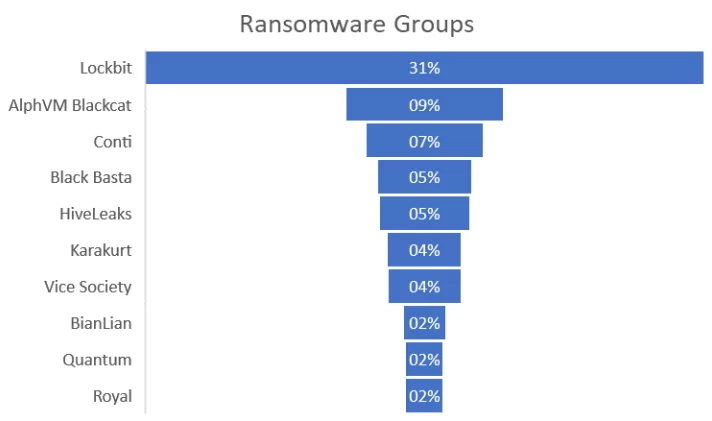
As shown in the circle graph below, most posts were victim announcements, either because the victim actually paid the demanded ransom or because the announcement was a fake story. Even if the ransomware attack is unsuccessful, it will still harm an organization’s customer reputation.

LockBit is by far the most active ransomware group in 2022; BlackCat and Conti follow them.
Stay Safe with SOCRadar in 2023
Regardless of industry and country, all organizations must take the necessary precautions as cyberattacks increase in frequency and sophistication. Here are a few actions you can take to secure your data and defend your organization from attacks, including ransomware operations:
- Implement a continuous monitoring system for your digital assets. SOCRadar excels at this task with its Extended Threat Intelligence (XTI) platform and efficient attack surface management, helping you enhance security, become aware of threats to your assets, and be swift while prioritizing actions.
- Stay aware of new ransomware threats and victim announcements.

- To prevent unauthorized access, use strong and distinctive passwords across all platforms.
- Train employees to raise cybersecurity awareness within your organization.
- Utilize network segmentation to stop the spread of ransomware incidents.
- Only give required access and privileges to employees and third-parties, and be aware of the security measures taken by your third-party vendors. The average cost of third-party data breaches is $4.33 million, which is much costlier than securing against third parties.
- Update your software and hardware. To protect yourself from disruptions, back up your data as well.


































