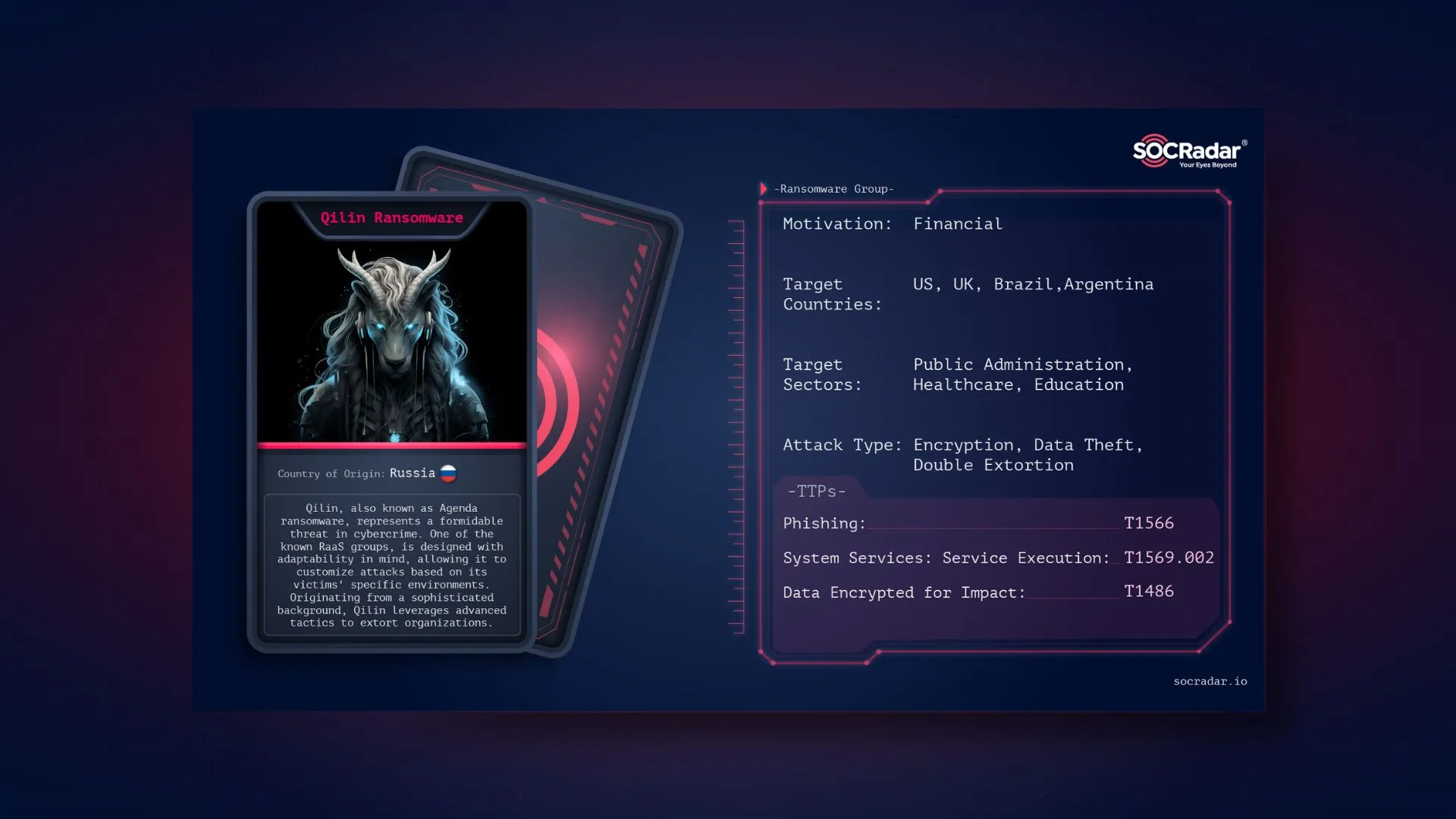
Dark Web Profile: Qilin (Agenda) Ransomware
Dark Web Profile: Qilin (Agenda) Ransomware [June 21, 2024] “Qilin Started Leaking Synnovis Data” Qilin, also known as Agenda ransomware, represents a formidable threat in cybercrime. This ransomware,...

Zyxel NAS Devices’ EoL Models Patched for Critical Code Execution Vuln...
Zyxel NAS Devices’ EoL Models Patched for Critical Code Execution Vulnerabilities: CVE-2024-29972, CVE-2024-29973, CVE-2024-29974 [Update] June 24, 2024: “Critical Zyxel NAS Vulnerability (CVE-2024-29...
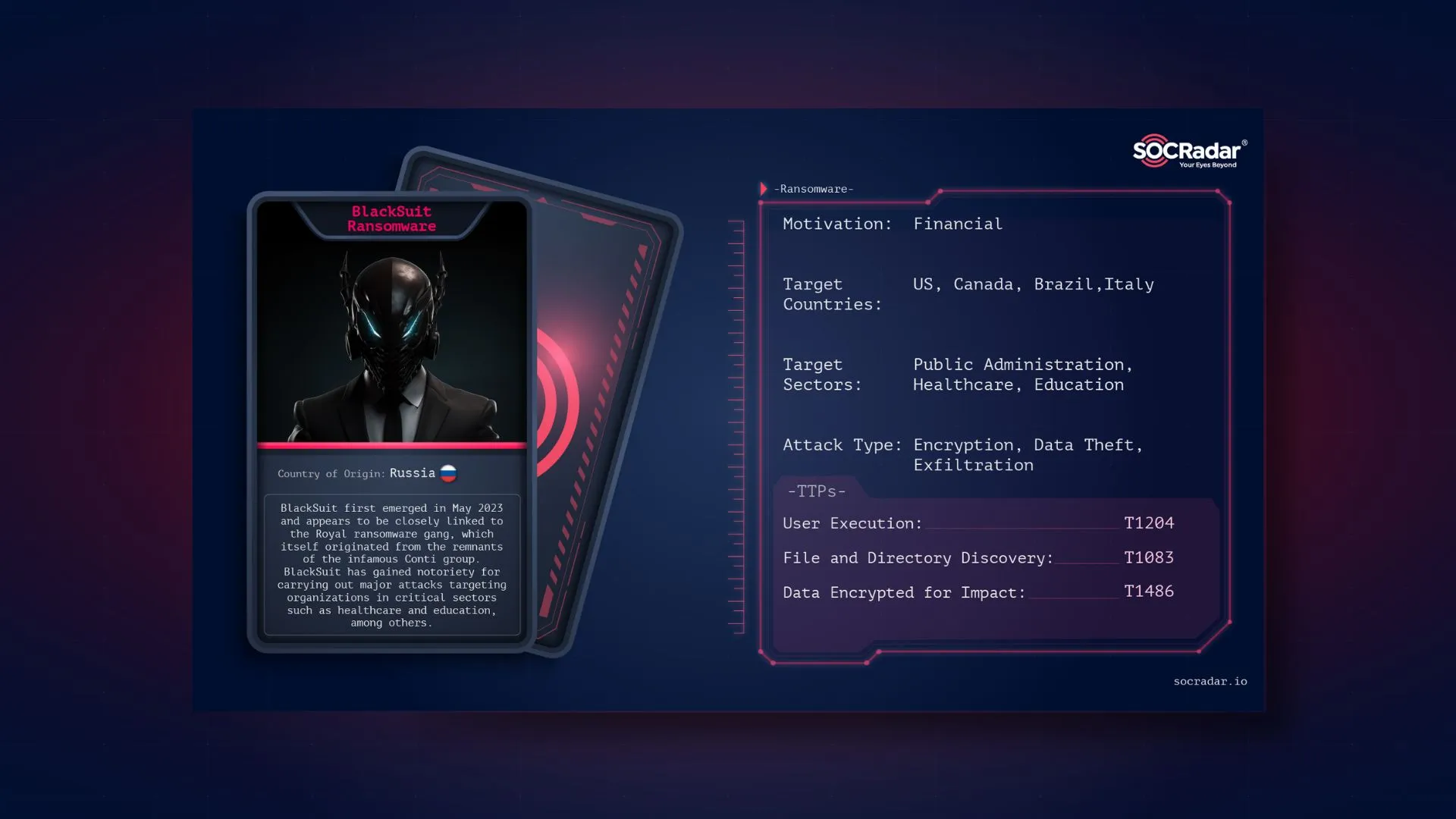
Dark Web Profile: BlackSuit Ransomware
Dark Web Profile: BlackSuit Ransomware [Update] August 8, 2024: “BlackSuit Ransomware Extorts Over $500 Million in Ransom Demands” BlackSuit ransomware is a rebranded version of the notorious Royal ra...

Alleged Data Leaks Across Major Industries; PwC, Shell, Decathlon Amon...
Alleged Data Leaks Across Major Industries; PwC, Shell, Decathlon Among Firms Facing Compromise The SOCRadar Dark Web Team has uncovered multiple high-profile data breaches involving major corporation...

A Look at the Security Challenges Threatening E-Commerce Websites – Vu...
A Look at the Security Challenges Threatening E-Commerce Websites – Vulnerabilities, Skimmers, Phishing In the fast-paced world of e-commerce, cyber threats rise as much as the sector’s expandin...

Overview of the Snowflake Breach: Threat Actor Offers Data of Cloud Co...
Overview of the Snowflake Breach: Threat Actor Offers Data of Cloud Company’s Customers This blog actively documents significant updates related to the Snowflake Breach. Latest update: “DOJ Indictment...

New in CISA KEV: Check Point VPN Zero-Day CVE-2024-24919 & Linux Kerne...
New in CISA KEV: Check Point VPN Zero-Day CVE-2024-24919 & Linux Kernel Flaw CVE-2024-1086 The U.S. Cybersecurity and Infrastructure Agency (CISA) updated its Known Exploited Vulnerabilities (KEV)...

GuptiMiner Campaign: The Trojan Tango of Infiltrating Antivirus Update...
GuptiMiner Campaign: The Trojan Tango of Infiltrating Antivirus Updates for Deception The GuptiMiner malware campaign is creating significant disruption in the cybersecurity landscape by exploiting a ...

Top 10 Supply Chain Monitoring Platforms
Top 10 Supply Chain Monitoring Platforms In today’s globalized business environment, nearly every organization is part of a complex web of interdependencies. This interconnectedness, while enabl...

Unleashing AI's Potential: Top 10 Tools for CISO for Security (Part-1)
Unleashing AI’s Potential: Top 10 Tools for CISO for Security (Part-1) One of the most important shifts in the dynamic, modern cyber warfare space is the changing role of the CISO. Advanced threats fo...

Detecting Leaked Credentials with Identity & Access Intelligence
Detecting Leaked Credentials with Identity & Access Intelligence Stealers are malicious software engineered by threat actors to compromise systems. Comparable to burglars, these trojans covertly e...

Top 5 Phishing Domain Takedown Service
Top 5 Phishing Domain Takedown Service Phishing attacks continue to pose a significant threat to both individuals and organizations. As cyber criminals continue to improve their strategies for exploit...

Progress Telerik Report Server Receives Security Update for Critical A...
Progress Telerik Report Server Receives Security Update for Critical Auth Bypass Vulnerability, CVE-2024-4358 [Update] June 14, 2024: “CISA Adds CVE-2024-4358 to Known Exploited Vulnerabilities Catalo...

PoC Exploit for CVE-2024-4956 in Sonatype Nexus Repository 3 Draws Thr...
PoC Exploit for CVE-2024-4956 in Sonatype Nexus Repository 3 Draws Threat Actors’ Attention Sonatype recently released a security advisory alerting users to a high-severity security vulnerabilit...

False Positives: Million Dollars Worth Issues – Spoiler: It is not eve...
False Positives: Million Dollars Worth Issues – Spoiler: It is not even an issue. Fairy tales for adults: from the boy who cried wolf to alert fatigue. Once upon a time, a shepherd boy, bored with his...
Top 10 Stealer Logs
Top 10 Stealer Logs Stealer logs are a critical concern as they involve the theft of sensitive information from infected systems. These digital threats, primarily aimed at acquiring data such as passw...

New Cyber Attack Campaign Bombarding Organizations with Fake Emails an...
New Cyber Attack Campaign Bombarding Organizations with Fake Emails and Phone Calls The cyber threat landscape is always changing, with attackers using new methods to get into organizations and exploi...

VPN Exploit, ATM Malware, and Database Leaks of MediSecure, Indian Vot...
VPN Exploit, ATM Malware, and Database Leaks of MediSecure, Indian Voter Portal, and PetroERP The SOCRadar Dark Web Team has uncovered several critical cyber threats within the past week. Among these ...

Freely Discover Dark Web Threats of Your Organization: Dark Web Report
Freely Discover Dark Web Threats of Your Organization: Dark Web Scan Report The dark web is a hotbed of dangers, a host for various cyber threats due to its nature. Each day, illicit markets overflow ...

CVE-2020-17519 in Apache Flink Enters CISA’s KEV Catalog & GitLab ...
CVE-2020-17519 in Apache Flink Enters CISA’s KEV Catalog & GitLab Patches XSS Flaw, CVE-2024-4835 The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its Known Ex...
































