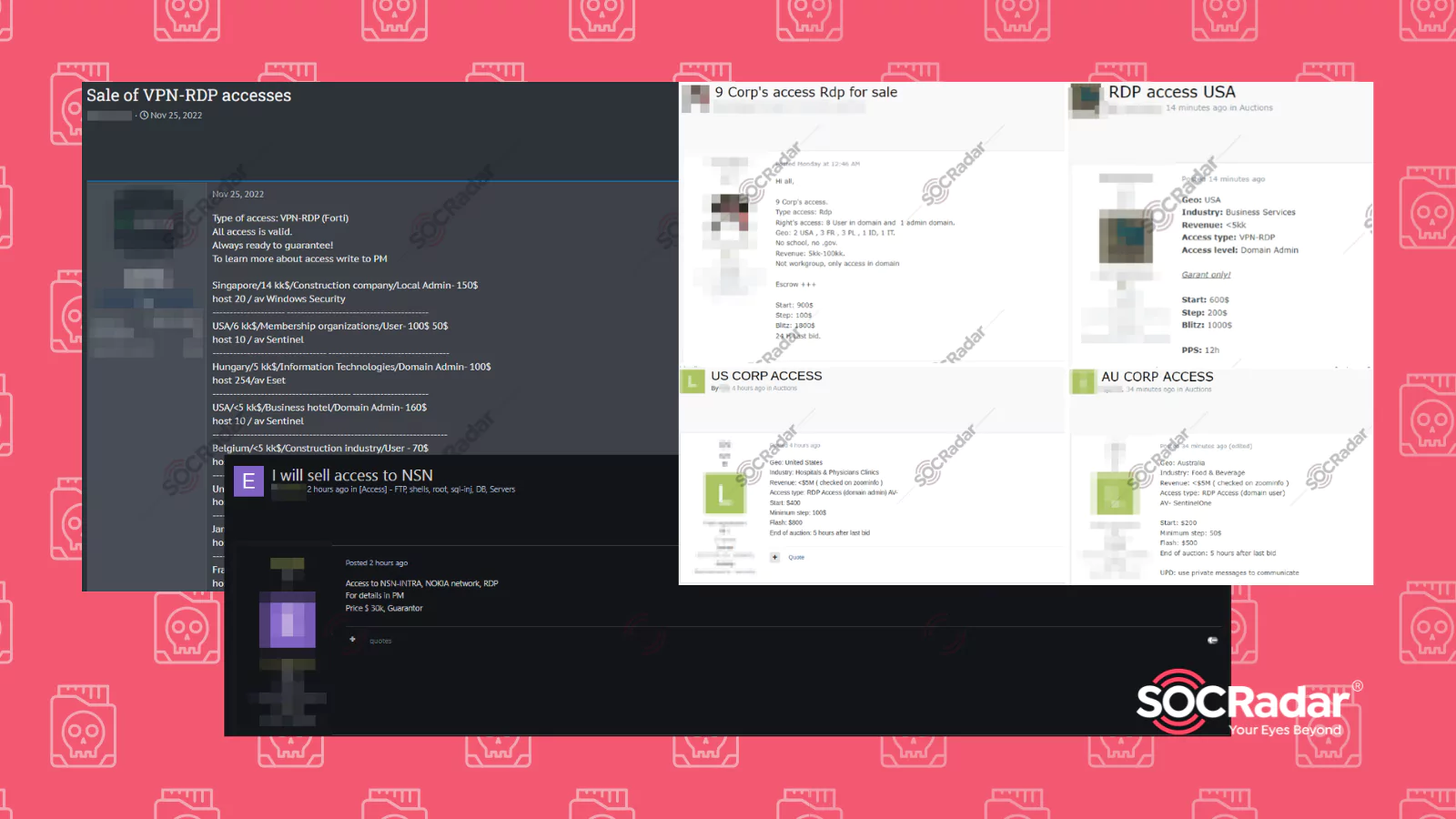
RDP Access Sales on Dark Web Forums Detected by SOCRadar
RDP Access Sales on Dark Web Forums Detected by SOCRadar Remote Desktop Protocol, or RDP, is a protocol developed by Microsoft. It allows the user to control another computer over a network connection...

APT Profile: Turla
APT Profile: Turla In the digital age, war has transitioned into the virtual world, where many types of cybercriminals, such as hacktivists and nation-state actors, are called Advanced Persistent Thre...

Using OSINT to Strengthen Organizational Security
Using OSINT to Strengthen Organizational Security Open-source intelligence or “OSINT” is collecting and analyzing data gathered from publicly available open sources (social media, news, dark web, etc....

Exploring the Dark Web Job Market
Exploring the Dark Web Job Market The dark web, notorious for its illicit activities, has evolved into a bustling marketplace for various illegal purposes. It serves as a hub for cybercriminals, offer...

The Surge in Cyber Attacks on Latin American Governments
The Surge in Cyber Attacks on Latin American Governments Latin America, a region bustling with potential and promise, has witnessed a worrying trend of escalating cyber threats directed at government ...

Internet-Exposed Devices within Federal Networks
Internet-Exposed Devices within Federal Networks As technology evolves and becomes increasingly integral to all aspects of society, the need for robust cybersecurity measures becomes more pressing. On...

Fake Extortion: How to Tackle and How to Verify?
Fake Extortion: How to Tackle and How to Verify? Today, one of the most critical aspects of maintaining a respectable business is to have resistance against cyber attacks. To that aim, organizations t...

Credential Theft Attacks Surge: Microsoft Raises Red Flag on Midnight ...
Credential Theft Attacks Surge: Microsoft Raises Red Flag on Midnight Blizzard (APT29) Microsoft has identified Midnight Blizzard, a Russian state-affiliated hacking group also known as APT29, as the ...

High-Severity Vulnerabilities Identified and Patched in BIND 9 DNS Sof...
High-Severity Vulnerabilities Identified and Patched in BIND 9 DNS Software The BIND 9 DNS software suite, an integral part of the Domain Name System (DNS), has recently received updates to neutralize...

A New RAT Tool, Unauthorized VPN-RDP Access Sale, and New Database Lea...
A New RAT Tool, Unauthorized VPN-RDP Access Sale, and New Database Leaks Brace yourself for this week’s thrilling snapshot of the dark web, where secrets are the common currency, and anonymity r...

Exploring Cyber Threats During the Hajj Season
Exploring Cyber Threats During the Hajj Season “More than 2 million cyber attacks were recorded from all over the world within a month” That is the summary of the cyber struggle during the last Hajj s...

Grafana Fixes Critical Auth Bypass, CISA Warns for VMware Vulnerabilit...
Grafana Fixes Critical Auth Bypass, CISA Warns for VMware Vulnerabilities Grafana and VMware have recently released security updates for their products in response to high severity vulnerabilities. Th...

What Do You Need to Know About CVE-2023-33299 Vulnerability in FortiNA...
What Do You Need to Know About CVE-2023-33299 Vulnerability in FortiNAC? ...

The IDOR Vulnerability in Microsoft Teams: Risks in Your Collaboration...
The IDOR Vulnerability in Microsoft Teams: Risks in Your Collaboration Environment [Update] July 5, 2023: A new tool called TeamsPhisher has been released by a member of the U.S. Navy’s red team...

Stealing the Spotlight: Unraveling the Surge of Stealer Malware in Bra...
Stealing the Spotlight: Unraveling the Surge of Stealer Malware in Brazil As we dive into the intricate web of the cyber threat landscape, one particular strain of malicious software continues to rais...

CISA Lists New ICS Advisories, Exploited Vulnerabilities, and Patch Al...
CISA Lists New ICS Advisories, Exploited Vulnerabilities, and Patch Alerts On June 22, 2023, CISA issued a series of important alerts, underscoring critical vulnerabilities present in industrial ...

NordVPN Report Shares Insights on 6 Million Payment Card Data on Dark ...
NordVPN Report Shares Insights on 6 Million Payment Card Data on Dark Web With the surge in digital payment methods and the widespread use of online transactions, payment card data has become a prime ...

Gartner: SOCRadar is Now a Customer First Technology Provider
Gartner: SOCRadar is Now a Customer First Technology Provider SOCRadar is now a Customer First Technology Provider in the Security Threat Intelligence Products and Services market with the prestigious...

May 2023 Cyberwatch Recap: A Month in Cybersecurity
May 2023 Cyberwatch Recap: A Month in Cybersecurity Welcome to our May Cyberwatch blog post. Following our latest webinar, we delve into the notable cyber incidents from the past month. May 2023 saw a...

Journey into the Top 10 Vulnerabilities Used by Ransomware Groups
Journey into the Top 10 Vulnerabilities Used by Ransomware Groups Once upon a time, in cyberspace, a menacing threat emerged. It would forever change the landscape of digital security. This threat was...

































