
Ducktail Malware Targets Facebook Business Accounts via LinkedIn Phish...
Ducktail Malware Targets Facebook Business Accounts via LinkedIn Phishing Attack A new phishing attempt with the codename Ducktail is in progress and targets LinkedIn users who work in the field to hi...

What is Domain Hijacking and How to Prevent
What is Domain Hijacking and How to Prevent Domain hijacking attacks can have many damaging consequences, such as the exposure of sensitive data and financial and reputational damage to organizations....

Zero-Day Security Flaw Exploited in PrestaShop Websites
Zero-Day Security Flaw Exploited in PrestaShop Websites Attackers discovered a way to exploit a vulnerability in PrestaShop servers. The actively exploited zero-day, CVE-2022-36408, allows attackers t...

Top 5 Tools for Phishing Domain Detection
Top 5 Tools for Phishing Domain Detection Phishing attacks have victimized many users and companies for years, and it seems they will continue to do so. Many security measures have been taken against ...

SonicWall Released Hotfix for Critical SQL Injection Flaw
SonicWall Released Hotfix for Critical SQL Injection Flaw A severe SQL injection vulnerability has been reported by network security vendor SonicWall in their security advisory. It affects the&nb...

What is Deep Web Monitoring?
What is Deep Web Monitoring? There are a variety of network monitoring and perimeter protection solutions available for both personal and commercial networks. Nevertheless, even the most protected bus...

Cisco Released Patches for Multiple Nexus Dashboard Vulnerabilities
Cisco Released Patches for Multiple Nexus Dashboard Vulnerabilities Cisco announced that it has released security updates for vulnerabilities detected in the Nexus Dashboard. The security flaws i...

Dark Web Threat Profile: pompompurin
Dark Web Threat Profile: pompompurin [Update] June 26, 2023: BreachForums was seized by the FBI three months after the arrest of its administrator. Added the subheading “FBI Seizes BreachForums After ...

What is BEC Attack and How to Prevent it?
What is BEC Attack and How to Prevent it? BEC attack is a type of social engineering attack that takes place over email and the attacker aims for financial gain. Often, attackers aim to trick employee...

Atlassian Patched Critical Vulnerability That Affects Confluence Serve...
Atlassian Patched Critical Vulnerability That Affects Confluence Servers Atlassian announced that it has released an update for a critical vulnerability affecting its Confluence Server and Data Center...

What is Spoofing Attack and How to Prevent It?
What is Spoofing Attack and How to Prevent It? In the context of cybersecurity, spoofing is the act of impersonating another entity to earn our trust, obtain access to our systems, steal data, steal m...

Black Basta Ransomware Victim Knauf Forced to Stop Their Services
Black Basta Ransomware Victim Knauf Forced to Stop Their Services Construction materials manufacturer Knauf announced it was the target of a cyberattack by the Black Basta ransomware. The company decl...
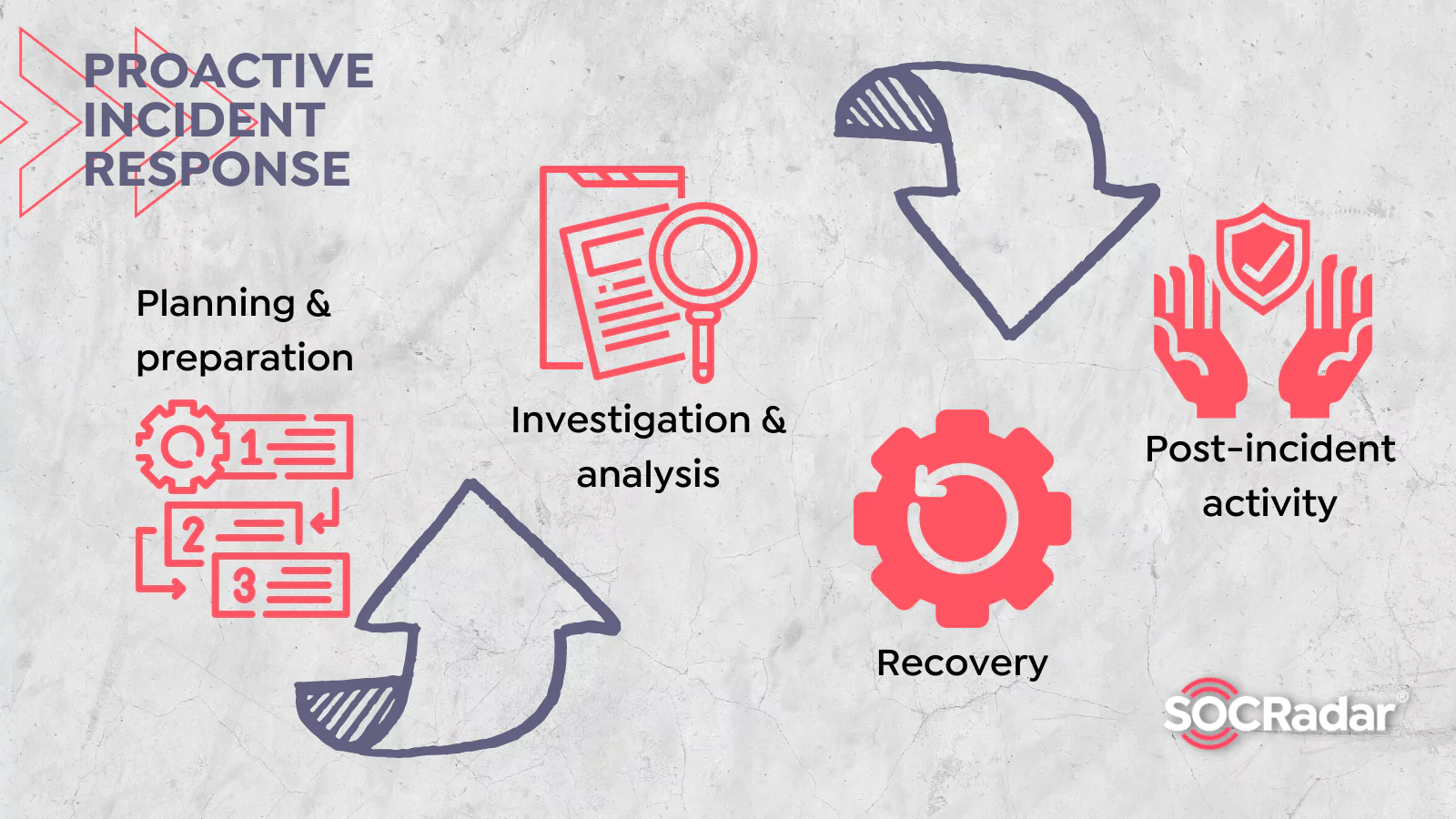
How to Build a Proactive Incident Response Plan?
How to Build a Proactive Incident Response Plan? Some standard cybersecurity measures are endpoint security tools, such as VPNs, proxies, antimalware, and employee cybersecurity awareness training. De...

CISA Warned To Patch Actively Exploited Privilege Escalation Vulnerabi...
CISA Warned To Patch Actively Exploited Privilege Escalation Vulnerability On Windows Microsoft discovered a new zero-day vulnerability in Windows products and released a patch. The vulnerability lets...

Juniper Networks Released Fixes For Critical Vulnerabilities
Juniper Networks Released Fixes For Critical Vulnerabilities CISA advised users and administrators to apply recently released fixes in Juniper Networks products due to several critical vulnerabil...

What is Dark Web Monitoring?
What is Dark Web Monitoring? As the most extensive worldwide system that stores information on everything (and almost everyone), the Internet comprises three distinct layers: the visible, the deep, an...

Cyber Kill Chain Model in Cyber Threat Intelligence
Cyber Kill Chain Model in Cyber Threat Intelligence Cybersecurity helps to reduce the risk of cyber-attacks and to eliminate the risks. Finding out the best solution to prevent the attacks i...

Expectations of SOC Team from CTI
Expectations of SOC Team from CTI Every company with an online component to its business needs cyber awareness; it also requires a Security Operations Center (SOC) if the online part is big enough. A ...

Top 5 Dark Web Forums
Top 5 Dark Web Forums There are many hacker forums in the dark web world. Apart from the forums that first come to mind for illegal drug sales, human trafficking, and pornographic content, i...

7 Books Every CISO Bookshelf Should Have
7 Books Every CISO Bookshelf Should Have The position of Chief Information Security Officer (CISO) is relatively new and has just received recognition from the CxO community and board of directors at ...
































