Threat Actors Use GitHub Codespaces Feature to Distribute Malicious Co...
Threat Actors Use GitHub Codespaces Feature to Distribute Malicious Content Since its public release in November 2022, GitHub Codespaces has been a popular environment among developers; howe...

What Do You Need to Know About the Critical RCE Vulnerability in Zoho’...
What Do You Need to Know About the Critical RCE Vulnerability in Zoho’s ManageEngine? (CVE-2022-47966) CVE-2022-47966, a critical vulnerability in a number of Zoho’s products, allows remote code execu...

Attackers Infected a CircleCI Employee with Malware to Steal Customer ...
Attackers Infected a CircleCI Employee with Malware to Steal Customer Session Tokens Software provider CircleCI confirmed that a data breach in December resulted in the theft of some of its ...

Threat Actors Exploit CVE-2022-44877 RCE Vulnerability in CentOS Web P...
Threat Actors Exploit CVE-2022-44877 RCE Vulnerability in CentOS Web Panel (CWP) Update (16.01.2023): According to data gathered by researchers, the CVE-2022-46169 vulnerability in Cacti saw an increa...

Cacti Patched CVE-2022-46169 Critical RCE Vulnerability
Cacti Patched CVE-2022-46169 Critical RCE Vulnerability Cacti patched a critical security flaw to prevent arbitrary code execution on Cacti-running servers. Cacti is an open-source, we...

Ransomware Gangs Leak Large Amounts of Data in Recent Attacks: Hive an...
Ransomware Gangs Leak Large Amounts of Data in Recent Attacks: Hive and Vice Society Ransomware gangs are known to release stolen data in retaliation if the ransom is not paid after successful encrypt...

200M+ Twitter Users' Email Addresses and 250M+ Deezer Users' Informati...
200M+ Twitter Users’ Email Addresses and 250M+ Deezer Users’ Information Leaked Online On a well-known hacker forum, a data leak containing the email addresses of 235 million Twitter users was made pu...

Synology Fixes a Max Severity RCE Vulnerability in VPN Server Products
Synology Fixes a Max Severity RCE Vulnerability in VPN Server Products Taiwanese NAS device manufacturer Synology has released a security update to address a critical vulnerability with a&nb...

RCE Vulnerability (CVE-2022-45359) in Yith WooCommerce Gift Cards Plug...
RCE Vulnerability (CVE-2022-45359) in Yith WooCommerce Gift Cards Plugin Exploited in Attacks In late November, security researchers found a critical vulnerability in Yith’s WooCommerce Gif...

CVE-2022-47633 Vulnerability Allows Attackers to Bypass Kyverno Signat...
CVE-2022-47633 Vulnerability Allows Attackers to Bypass Kyverno Signature Verification The Kyverno admission controller for container images has been found to have a high-severity security v...

All You Need to Know About the Linux Kernel ksmbd Remote Code Executio...
All You Need to Know About the Linux Kernel ksmbd Remote Code Execution (ZDI-22-1690) Vulnerability Five new vulnerabilities, one of which has a severity rating of 10 according to the Common Vulnerabi...

400 Million Twitter Users Data Allegedly Breached for Extortion
400 Million Twitter Users Data Allegedly Breached for Extortion On December 23, 2022, a threat actor shared a post on a dark web forum monitored by SOCRadar, claiming to possess 400 million Twitter u...
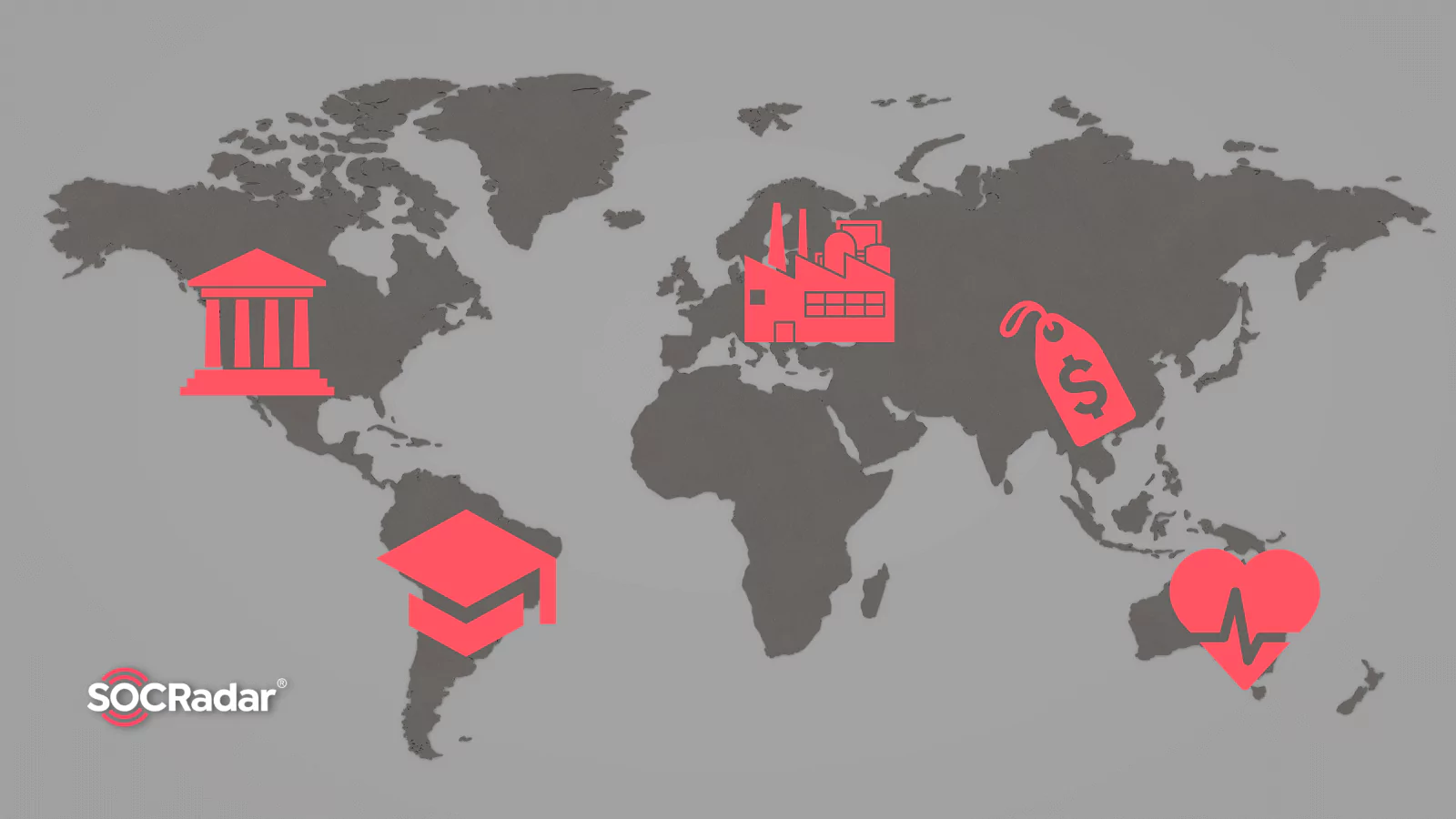
Top 10 Targeted Industries and Countries in 2022
Top 10 Targeted Industries and Countries in 2022 No matter the industry, cyberattacks can cause various problems, ranging from minor disruptions to significant losses or, even worse, lawsuits against ...

AWS Elastic IP Transfer Feature Could Be Exploited in Attacks
AWS Elastic IP Transfer Feature Could Be Exploited in Attacks Researchers have discovered a new security risk to a recently added feature in Amazon Web Services (AWS). Elastic IP transfer, ...

Top 10 Cyber Incidents in 2022
Top 10 Cyber Incidents in 2022 2022 was a year in which everyone worked to overcome the COVID-19 pandemic and a year in which threat actors simply tried to profit more from it. Threat actors...

Reports of ProxyNotShell Vulnerabilities Being Actively Exploited (CVE...
Reports of ProxyNotShell Vulnerabilities Being Actively Exploited (CVE-2022-41040 and CVE-2022-41082) According to reports, the zero-day vulnerabilities CVE-2022-41040 and CVE-2022-4108...

Top 10 Data Leaks in 2022
Top 10 Data Leaks in 2022 Threat actors need sensitive information to carry out most of their malicious activity. They typically obtain the information by conducting various cyberattacks or simply gat...

Veeam Fixes Critical Vulnerabilities in Backup & Replication Software ...
Veeam Fixes Critical Vulnerabilities in Backup & Replication Software (CVE-2022-26500 & CVE-2022-26501) Veeam has recently fixed two security vulnerabilities (CVE-2022-26500 and CV...

Microsoft Reevaluates SPNEGO NEGOEX Vulnerability CVE-2022-37958 as Cr...
Microsoft Reevaluates SPNEGO NEGOEX Vulnerability CVE-2022-37958 as Critical Microsoft reassessed the severity score of a vulnerability fixed in September 2022 Patch Tuesday. The vulnerabi...

APT5 Exploits Zero-Day Vulnerability on Citrix ADC and Gateway Devices
APT5 Exploits Zero-Day Vulnerability on Citrix ADC and Gateway Devices Citrix has just released a patch to address a critical zero-day vulnerability affecting its products. The vulnerability...