
Dark Web Profile: BlackCat (ALPHV)
[Update] December 19, 2023: As we speculated recently, law enforcement agencies have successfully taken control of the official site of the ALPHV.** Read more under the title: “BlackCat (ALPHV) Went Down, Possible Law Enforcement Intervention.”
[Update] December 11, 2023: “BlackCat (ALPHV) Went Down, Possible Law Enforcement Intervention.”
[Update] August 18, 2023: Microsoft has detected a recent version of BlackCat ransomware equipped with the Impacket communication framework tool. Added the subheading “New BlackCat Ransomware Variant Using Impacket.”
[Update] July 05, 2023: BlackCat has claimed responsibility for stealing 7TB of data from Barts Health NHS Trust. Added to the subheading: “Latest Attacks of the BlackCat.”
[Update] June 19, 2023: BlackCat (ALPHV) Ransomware group has listed Reddit as a victim following the Reddit blackout. Added to the subheading: “Latest Attacks of the BlackCat.”
On April 19, 2022, The Federal Bureau of Investigation (FBI) published a FLASH alert about the BlackCat (ALPHV)’s activities during March 2022. According to the FBI’s report, BlackCat is believed to be the successor of REvil, DarkSide, and BlackMatter ransomware operators.
In May 2021, Colonial Pipeline was targeted by a ransomware attack, which resulted in the shutdown of the entire pipeline system responsible for distributing gasoline and jet fuel to the east coast of the United States. This caused fuel shortages and price increases in several states along the East Coast of the United States. Colonial Pipeline had to pay nearly $5 Million for the ransom, and after the investigations, the FBI confirmed that DarkSide ransomware was responsible for the compromise.
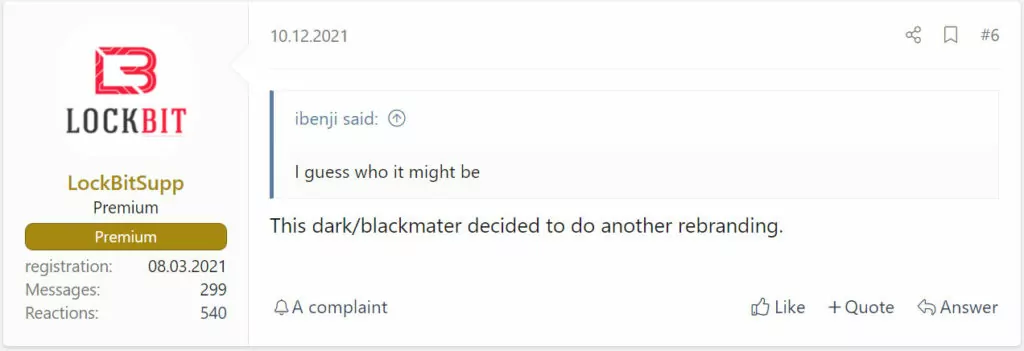
A member of the LockBit ransomware group revealed the connection between BlackCat and Darkside/BlackMatter in a dark web forum a month after the launch of BlackCat ransomware in November 2021:
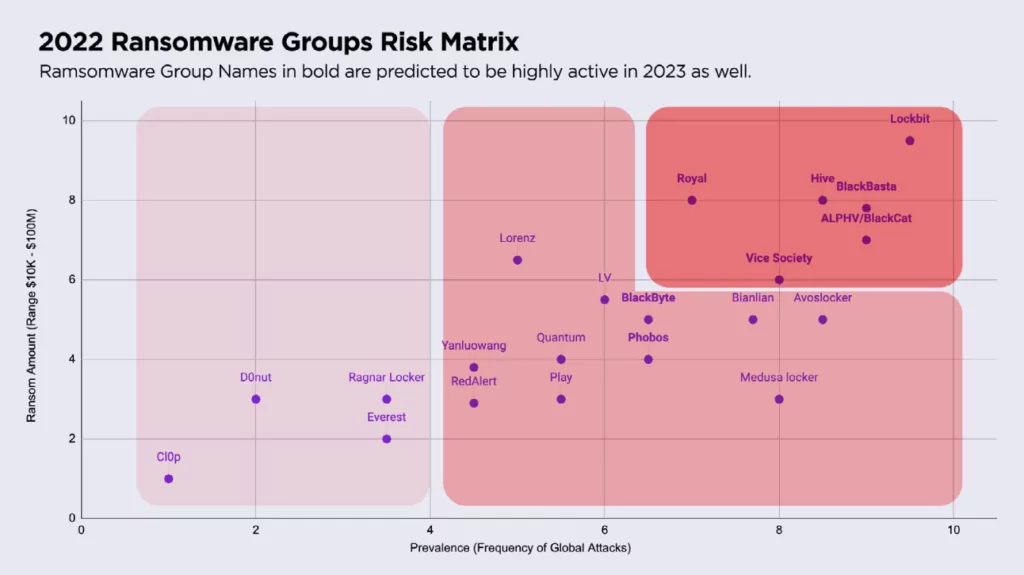
In addition, as seen on SentinelOne’s OverWatch 2022 report, BlackCat was placed in the red line of the 2022 Ransomware Groups Risk Matrix, which makes it counted as a serious danger.
Who is BlackCat Ransomware Group?

BlackCat, or ALPHV, is a ransomware group known for being the first to use Rust -a cross-platform language programming language that allows for easy malware customization for different operating systems, such as Windows and Linux- successfully. The group has been able to evade detection and successfully encrypt their victims’ files by using Rust, which allows them to target multiple operating systems and bypass security controls that are not designed to analyze malware written in Rust. This highlights the importance of staying vigilant and protecting against such attacks.
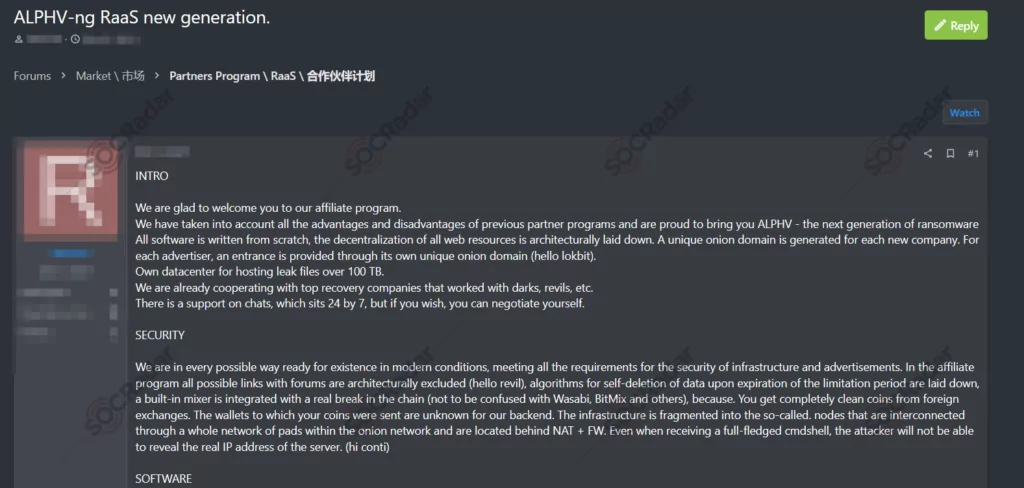
The group first announced its RaaS (Ransomware-as-a-Service) affiliate program in a dark web forum in December 2021 with its original name ALPHV. The group has been operating since approximately December 2021 and uses a lucrative Ransomware-as-a-Service model, which could make it preferable for potential affiliates. According to the forum post, affiliates take:
- 80% if the value of the ransom is up to $1.5M,
- 85% if the value of the ransom is up to $3.0M,
- 90% if the value of the ransom is from $3.0M.
Also, each new victim has its unique onion domain, and ALPHV provides 100 TBs of space for each exfiltration.
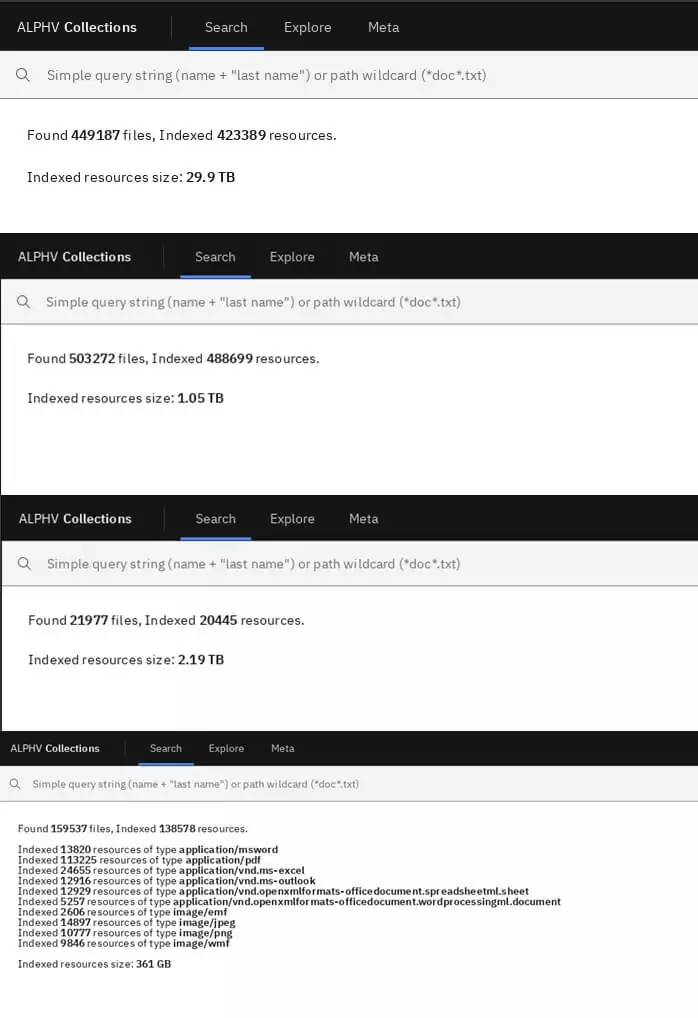
Also, the post alludes to Conti and LockBit. In addition, we could see that the group forces their affiliates to continue their operations by including the phrase, “If there is no activity for two weeks, your account will be frozen and subsequently deleted. To avoid this, we recommend you notify the administration about possible vacations, pauses, and other things.”
SOCRadar dark web researchers found a response from Conti about ALPHV that they are stealing chats and deceiving their advertisers.
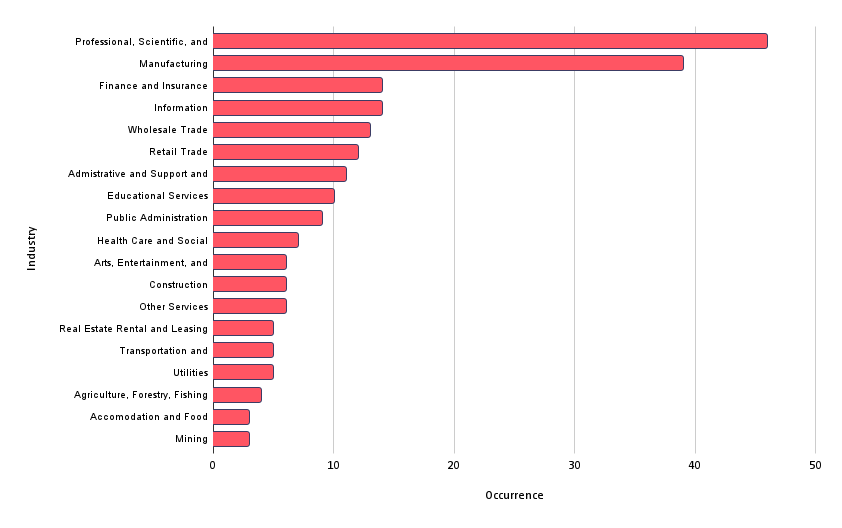
SOCRadar researchers have analyzed over 210 BlackCat victim announcements and found that “Professional, Scientific, and Technical Services” and “Manufacturing” are the most targeted industries by BlackCat ransomware.
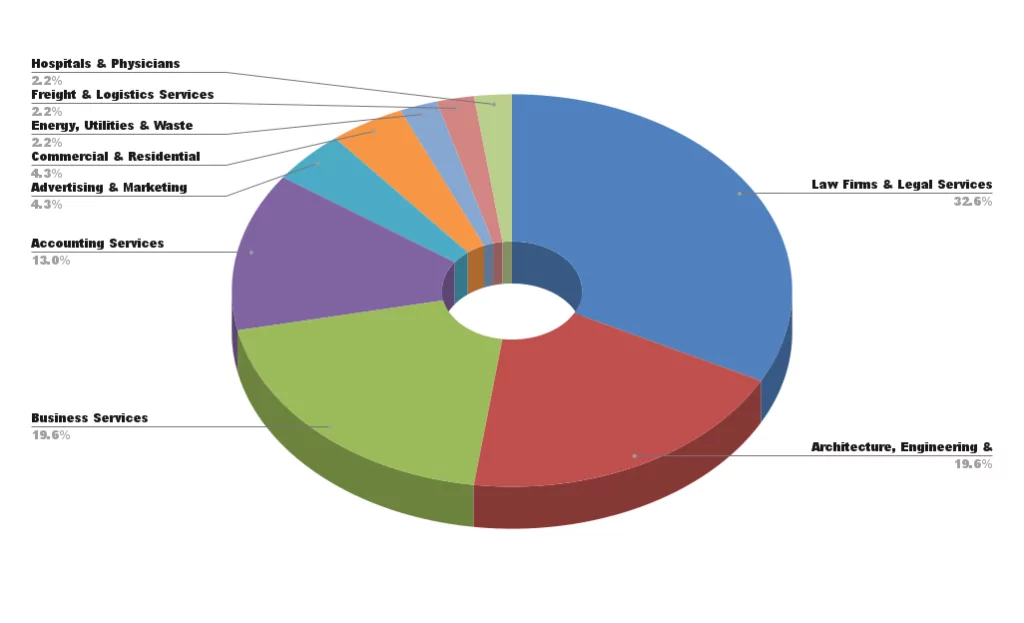
Law firms and legal services are the most affected organizations in the Professional, Scientific, and Technical Services industry.
How does BlackCat Ransomware Group Attack?
According to the FBI’s FLASH alert, the group gains initial access to targeted systems by using stolen user credentials or exploiting known Microsoft Exchange vulnerabilities. The Blackcat group utilized the following vulnerabilities in Microsoft Exchange Server:
Once they have access, they compromise user and administrator accounts within the Active Directory. This allows them to set up malicious Group Policy Objects (GPOs) using the Windows Task Scheduler, enabling them to deploy the ransomware payload.
Also, once the threat actor accesses the network, it disables the security measures of a target organization by removing antivirus software. After that, the actor obtains domain accounts using AdFind and ADRecon tools and gathers information about the victim network using SoftPerfect. Lastly, the attacker uses Process Hacker and Mimikatz to obtain and extract the victim’s login credentials.
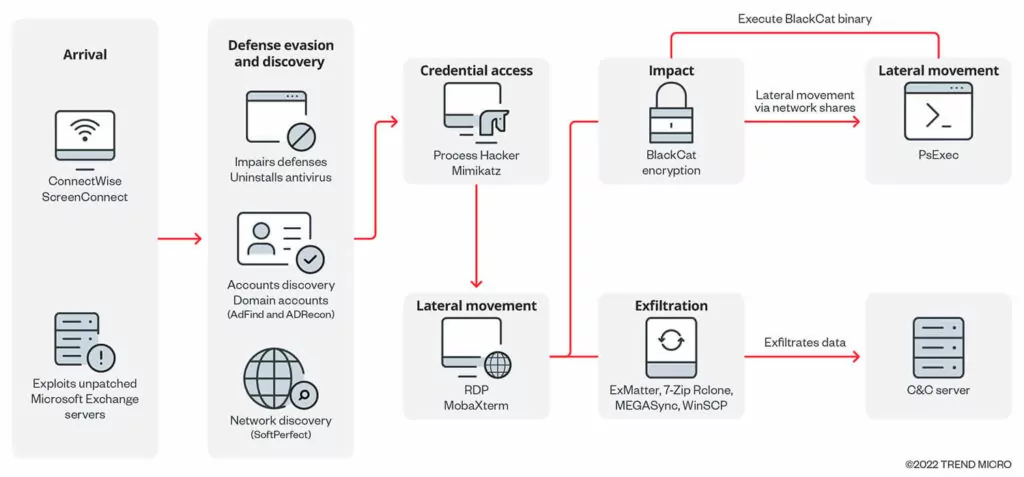
In September 2022, threat researchers reported that the group had utilized an improved version of the ExMatter data exfiltration tool and Eamfo, a malware specifically created to obtain login credentials saved by Veeam backup software.
In addition, triple extortion is being used in which, in addition to the common practice of stealing sensitive data before encrypting the victim’s files and threatening its public release (double extortion), the ransomware group also threatens to launch a distributed denial-of-service (DDoS) attack if their demands are not met.
Findings on BlackCat Ransomware
BlackCat has known two variants for both Windows and Linux.
Let’s look at an existing analysis result by searching for a hash available from open sources on Any.run. The analysis example shows that certain parameters are entered while running the sample in the command line (cmd[.]exe).
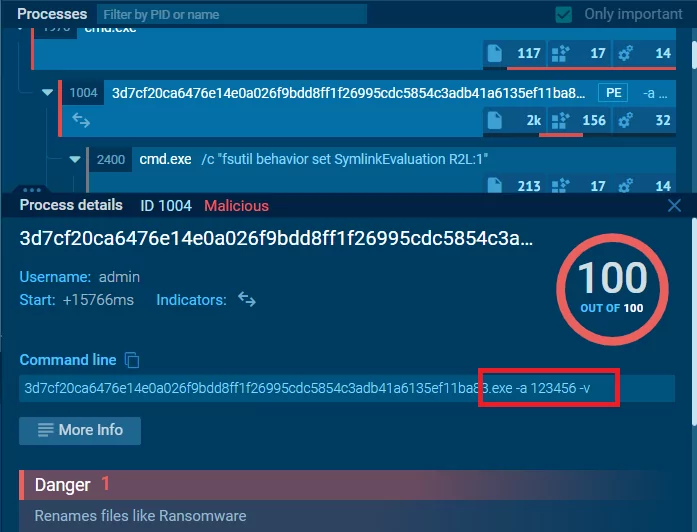
For this reason, we tried the “help” command to see whether it worked, which seems to work successfully.
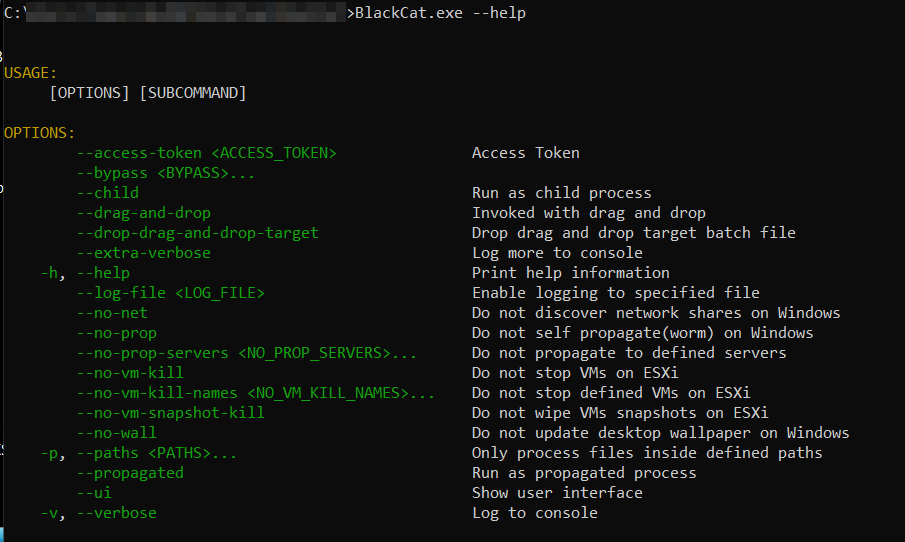
SecureScorecard’s dynamic analysis discovered that the access token needs to be a 32-byte value, and it does not have to be unique. This means that the access token could be around 43 characters long and consist of randomly selected alphanumeric characters.

An “Invalid access token” error is encountered when we try a random key. However, when other parameters are given, the error returns as “Invalid config,” although there is no activity.
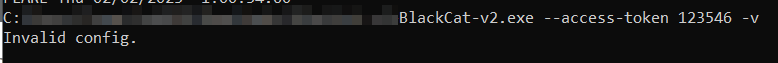
Because of this, we can check whether the same situation occurred with the first variant of the BlackCat.
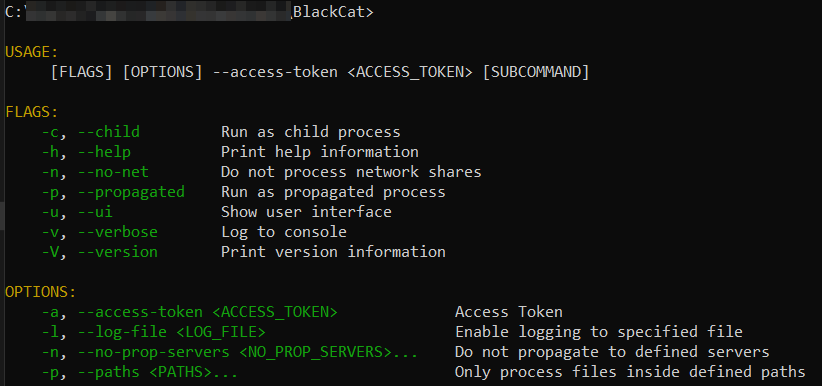
It can be seen that there are interface differences between v1 and v2; it seems that the v2 variant has Virtual Machine and network config settings.
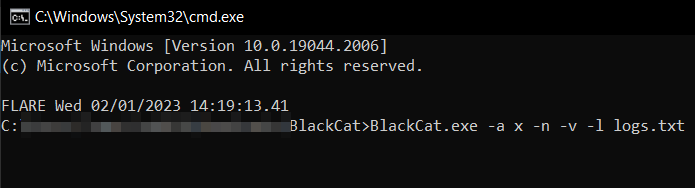
As tested with the available parameters, with the arbitrarily chosen access-token “x,” the v1 of the ransomware itself successfully starts running.
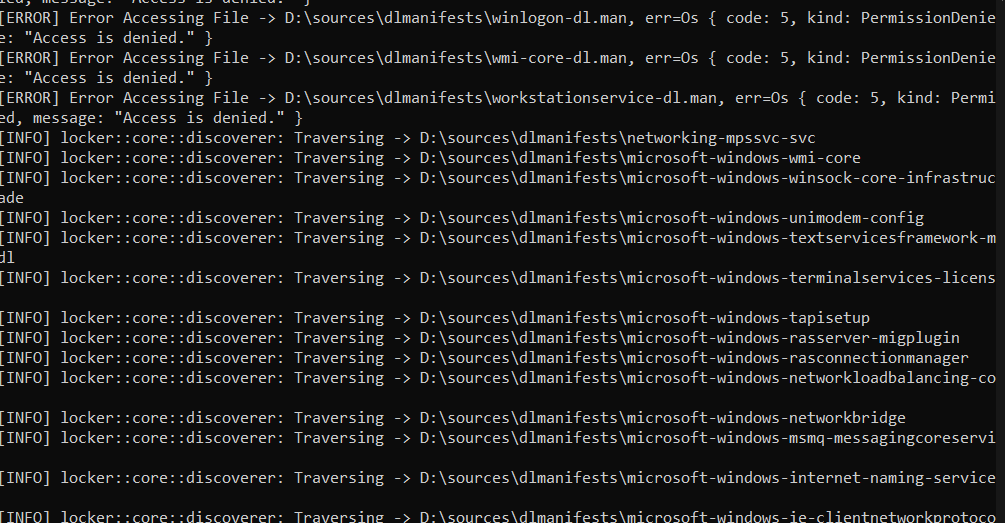
In the file named logs.txt, the outputs reflected on the command line while the ransomware is running are recorded.
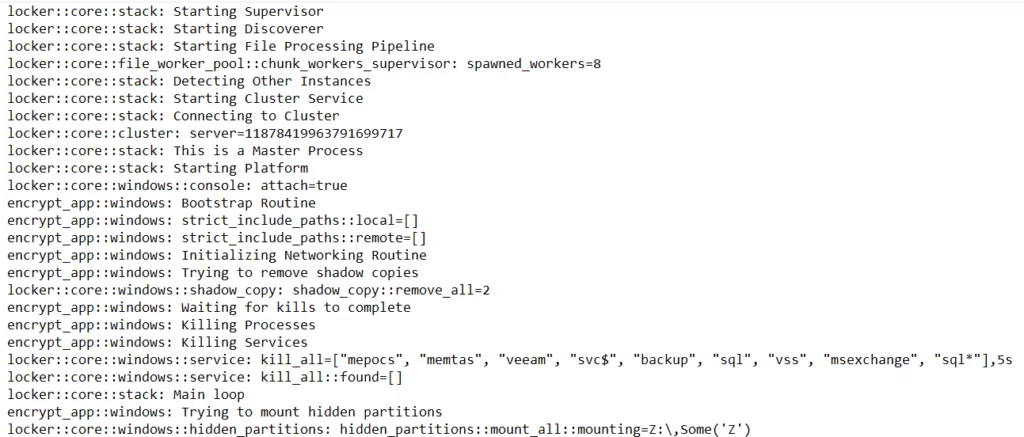
During its execution, the BlackCat ransomware names each file’s extension with a word of randomly chosen letters, drops the ransom note in each folder and desktop, and finally changes the desktop background to the image below.
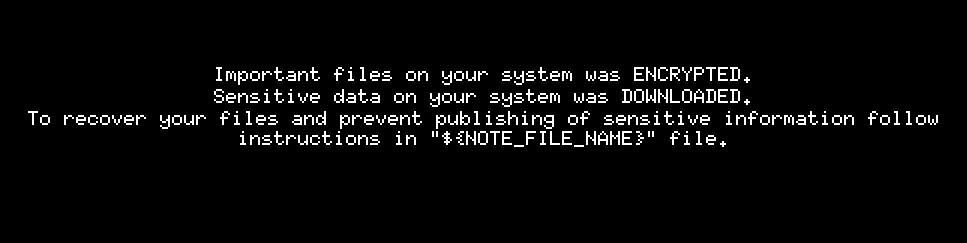
You can see the ransom note in the URL it left for negotiation below.
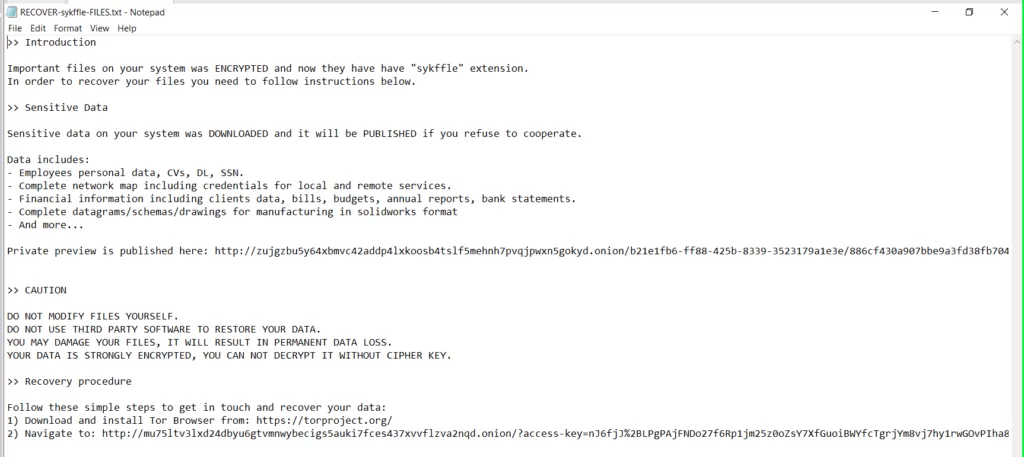
The IoCs obtained through the ransomware we examined with the BlackCat v1 hash (3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83) can be found in the appendix section.
Also, the BlackCat page in the Threat Actors panel is constantly updated when new IoCs are found.
BlackCat Ransomware Uses Malicious Windows Kernel Driver POORTRY to Avoid Detection
The BlackCat (ALPHV) ransomware operation used signed malicious Windows kernel drivers to avoid detection during an attack in February 2023. These drivers are an improved version of the “POORTRY” malware previously discovered by security researchers.
The POORTRY malware is signed with stolen keys from legitimate Microsoft Windows Hardware Developer Program accounts. It has also been used by the UNC3944 threat group (aka 0ktapus, Scattered Spider) to terminate security software on Windows devices. These drivers have the highest privileges in the Windows operating system and can terminate almost any process.
The BlackCat ransomware group’s use of the POORTRY malware potentially connects them to the UNC3944 threat group.
Unveiling BlackCat’s Tactics: Capabilities of the POORTRY Malware
BlackCat tried to utilize a POORTRY driver signed by Microsoft; however, due to widespread attention and the subsequent revocation of code-signing keys, the driver was highly detectable. The hackers then resorted to using an upgraded version of the POORTRY kernel driver, which was signed using a cross-signing certificate that had been either stolen or leaked.
In February 2023, researchers found the signed driver “ktgn.sys,” which was dropped in the victim’s %Temp% folder and loaded by a user mode program called “tjr[.]exe.”
The digital signature for ktgn.sys has been revoked, but it still loads on 64-bit Windows systems with enforced signing policies. The malicious kernel driver exposes an IOCTL (Device Input and Output Control) interface, allowing tjr[.]exe to issue commands. Researchers discovered that only the “Kill Process” command was used to terminate security agent processes on the system.
Researchers from Trend Micro discovered several other exposed commands that threat actors could issue to the driver. The commands allow activation/deactivation of the driver, delete/copy files, register/unregister processes, and reboot the system. However, they noted that two commands used for Process/Thread Notification callbacks are not working, implying that the driver is still under development or testing.
Indicators of Compromise (IoC) Related to POORTRY
Windows administrators should ensure that Driver Signature Enforcement is enabled to prevent the installation of drivers that lack a valid digital signature. They are also advised to add malicious drivers to the Windows driver blocklist.
| File Name | Hash (SHA1) | Detection Name |
| yixowv[.]exe | 17bd8fda268cbb009508c014b7c0ff9d8284f850 | Ransom.Win32.BLACKCAT.SMYPCC5 |
| cor[.]exe | 78cd4dfb251b21b53592322570cc32c6678aa468 | Ransom.Win32.BLACKCAT.SMYPCC5 |
| trj[.]exe | c2387833f4d2fbb1b54c8f8ec8b5b34f1e8e2d91 | Trojan.Win64.STONESTOP.A |
| dkrtk.sys | 91568d7a82cc7677f6b13f11bea5c40cf12d281b | Trojan.Win64.VMPROTECT.R002C0RA |
| fgme.sys | 0bec69c1b22603e9a385495fbe94700ac36b28e5 | Troj.Win32.TRX.XXPE50F13019 |
| ktes.sys | 5ed22c0033aed380aa154e672e8db3a2d4c195c4 | Troj.Win32.TRX.XXPE50F13019 |
| kt2.sys | cb25a5125fb353496b59b910263209f273f3552d | Troj.Win32.TRX.XXPE50F13019 |
| ktgn.sys | 994e3f5dd082f5d82f9cc84108a60d359910ba79 | Rootkit.Win64.POORTRY.A |
Which Countries Did BlackCat Target?
From observed victim announcements, SOCRadar researchers found that the group mostly targets organizations based in the United States.
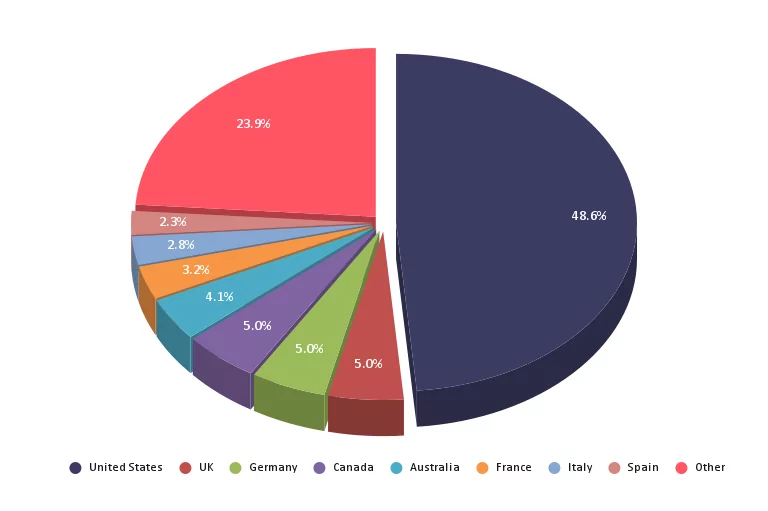
However, they don’t specifically target the United States. As SOCRadar Researchers’ observations, the group has compromised organizations in more than 40 countries.
Latest Attacks of the BlackCat
Due to Reddit’s API price hike on May 31, 2023, which is expected to challenge most free third-party apps such as Reddit Is Fun and Apollo, about 9000 subreddits have started a Reddit blackout by taking their subreddits private in protest. This movement can be followed on Reddark. Additionally, Reddit’s average daily traffic dropped by 6.6% as a result of this incident.
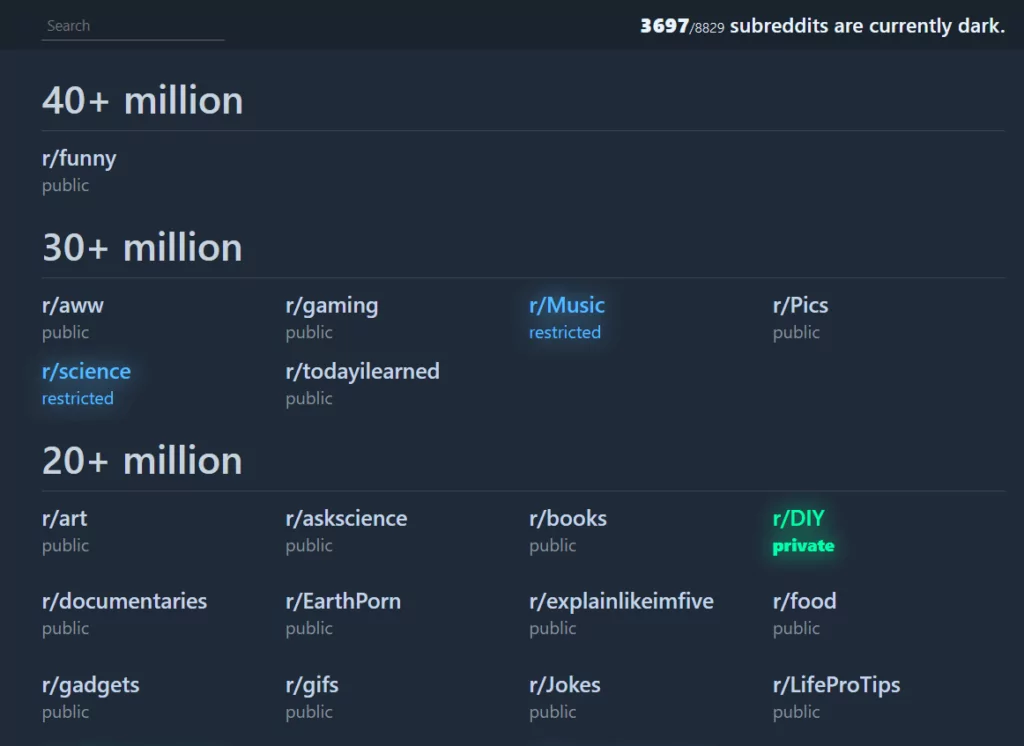
While this was going on, the BlackCat Ransomware group added Reddit to its list of victims in a timely second blow to Reddit, although its connection to the blackout incident is unknown.
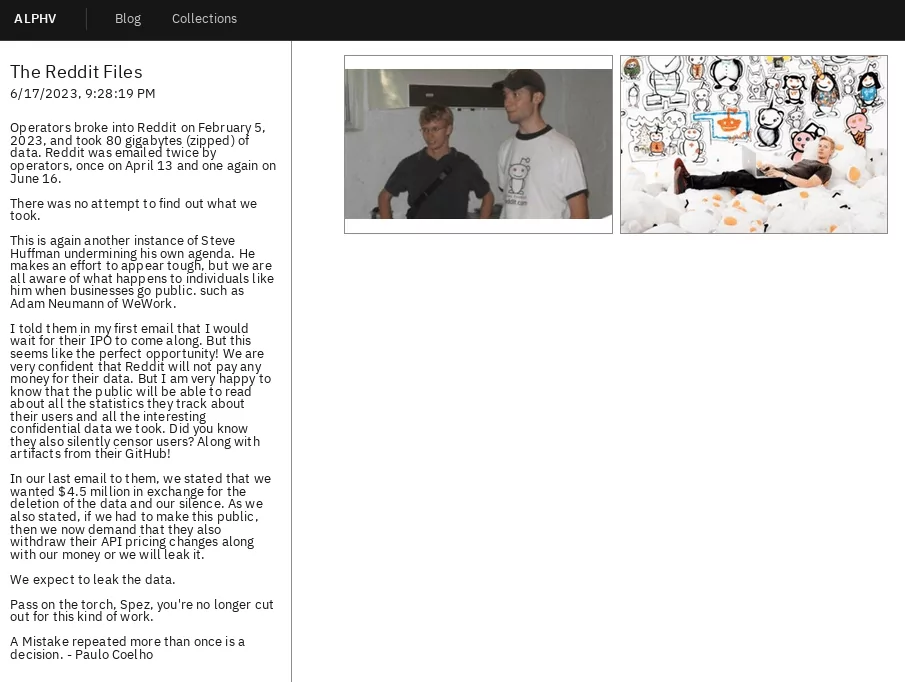
According to their statement, BlackCat operators infiltrated Reddit and stole 80 GB of data in early February; Reddit discovered a spear-phishing campaign targeting their employees on February 5.
The phishing campaign involved directing employees to a website replicating Reddit’s intranet gateway to steal credentials and 2FA tokens. After successfully acquiring an employee’s credentials, the attacker gained access to internal documents, dashboards, code, and business systems.
The BlackCat announcement stated that on April 13 and June 16, they reached out twice by email and demanded 4.5 million dollars as a ransom. There is no information about the stolen data at the moment, but user passwords and accounts were not compromised, as Reddit announced.
BlackCat posts its victim announcements on its onion site, mostly with proof documents, and adds a short description of the situation that sometimes contains threatening messages through the victim.
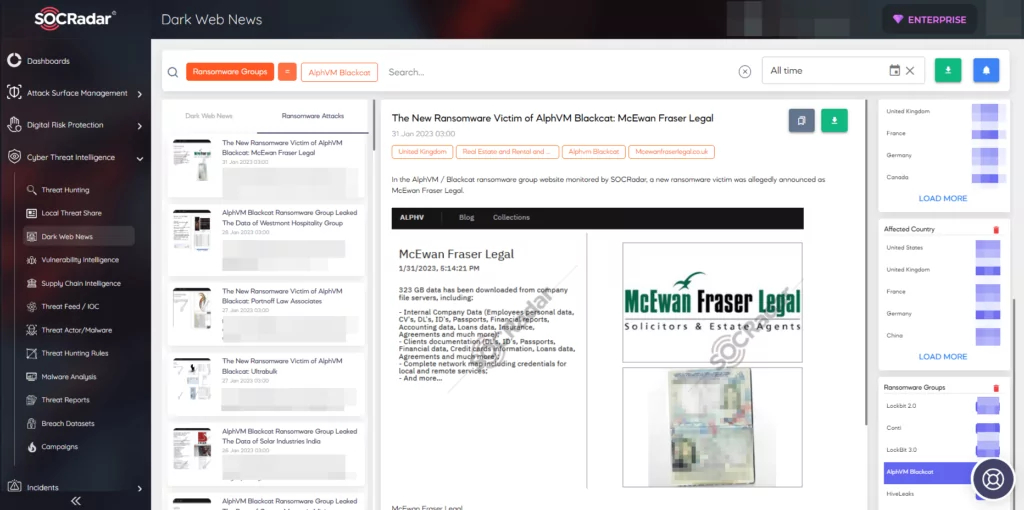
From its latest attacks, the group has announced that they compromised Crescent Crown Distributing and published their 1TB size of data within the announcement.
Nowadays, BlackCat’s affiliates target pharmaceutical companies. One of the recently compromised companies is Pharmacare short after their attack on an Electronic Health Record (EHR) vendor NextGen Healthcare.
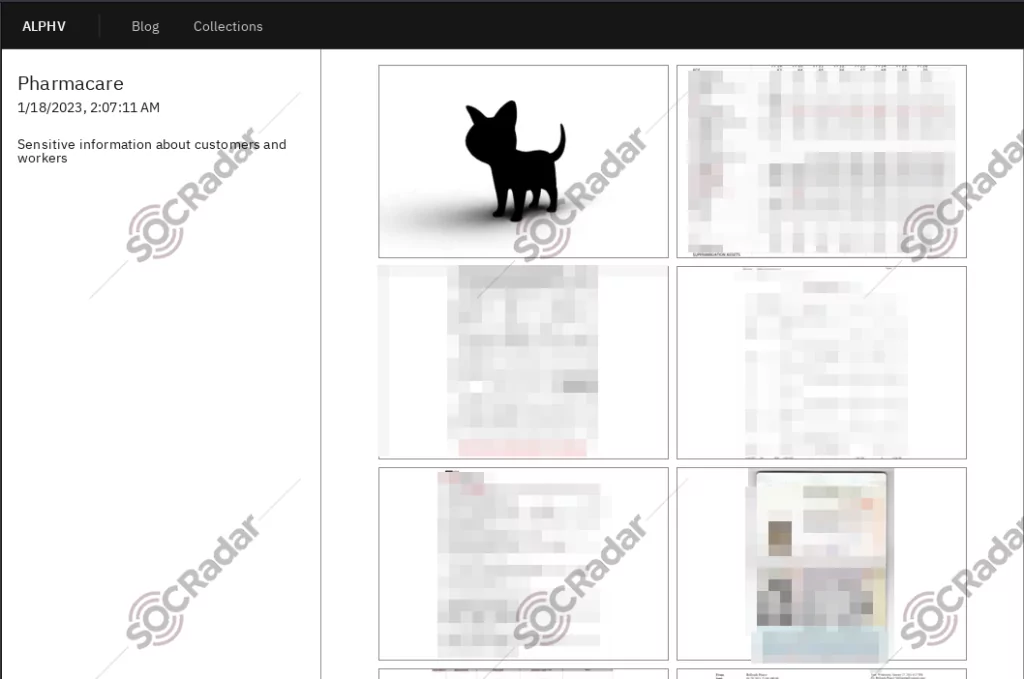
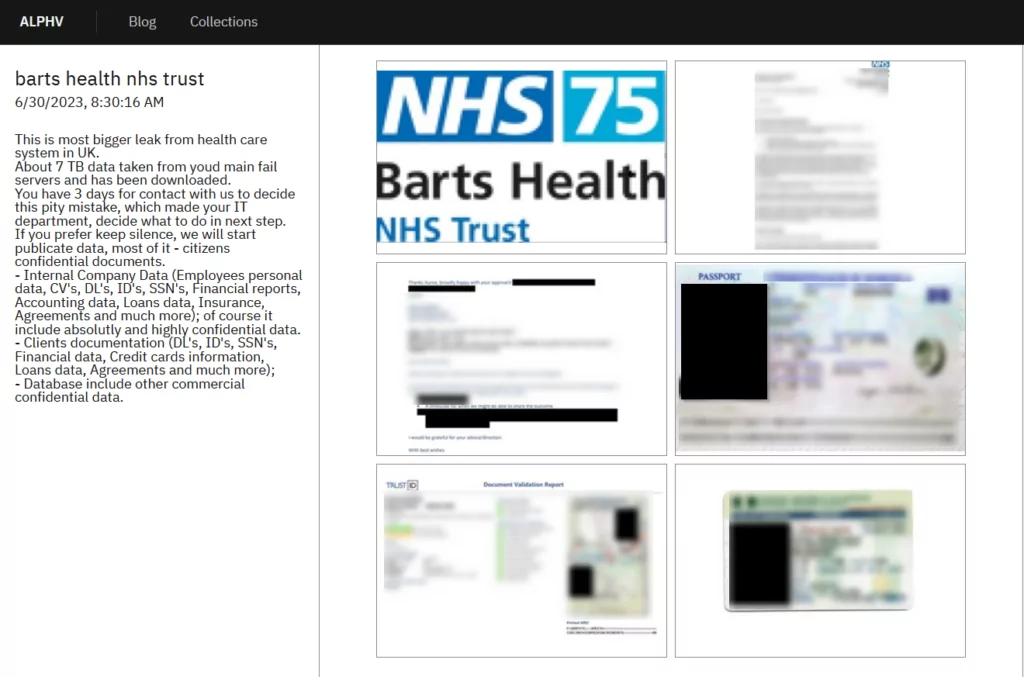
BlackCat has recently claimed responsibility for stealing 7TB of data from Barts Health NHS Trust. In a post on its dark web data leaks site on June 30, the gang referred to the cyber attack as the “most significant leak from the healthcare system in the UK.” BlackCat threatened to publish the stolen data if the Trust did not contact them within three days.
The data supposedly includes confidential documents containing personally identifiable information, such as National Insurance numbers, financial data, client documentation, credit card information, financial reports, accounting and loan data, and insurance agreements. Barts Trust has stated that it is treating the allegations with utmost urgency and is actively investigating the incident.
New BlackCat Ransomware Variant Using Impacket
Microsoft has identified a recent version of BlackCat ransomware that utilizes the Impacket communication framework tool. This tool assists threat actors in moving laterally within targeted environments.
Microsoft first noticed the new version being utilized by a BlackCat affiliate in July 2023.
Moreover, the new version incorporates the Remcom hacktool to execute remote code and includes compromised target credentials, which are hardcoded. These credentials not only enable lateral movement capability but also streamline subsequent ransomware deployment.
BlackCat (ALPHV) Went Down, Possible Law Enforcement Intervention
ALPHV’s leak site went offline on December 7 and remained down until today. Rumors suggest that a law enforcement operation is responsible for the recent outage of ALPHV ransomware gang’s websites, including negotiation and data leak sites. While the ALPHV admin initially mentioned the sites might be back online soon to Bleeping Computer and told RedSense that “Everything will work soon,” they remain down.
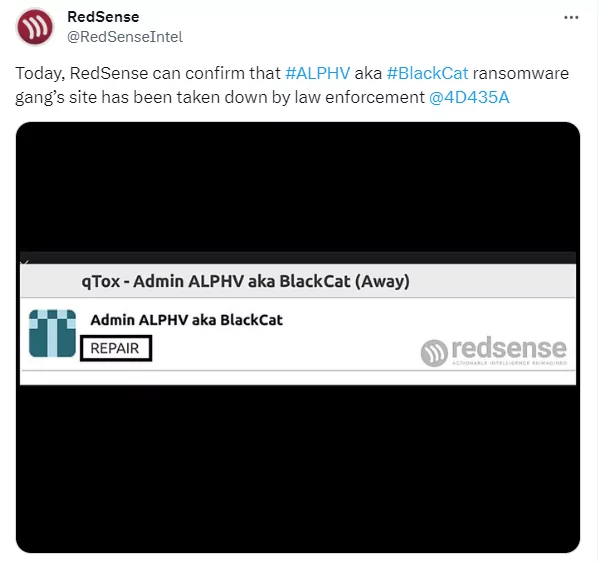
There are claims that the FBI has taken action against the ransomware gang, similar to past disruptions caused by law enforcement operations targeting other groups. The ALPHV/BlackCat ransomware operation, believed to be a rebrand of the DarkSide gang, has faced previous seizures of infrastructure, leading to temporary shutdowns and rebrands.
*After a significant period, the data leak site of the ALPHV/BlackCat Ransomware gang is back online as of December 12, 2023.
**As we speculated recently, law enforcement agencies, including the FBI, the US Department of Justice, and various European security organizations under the umbrella of Europol, have successfully taken control of the official site of the ALPHV.
This action justified earlier speculations that emerged when the ALPHV group temporarily disappeared from the web.
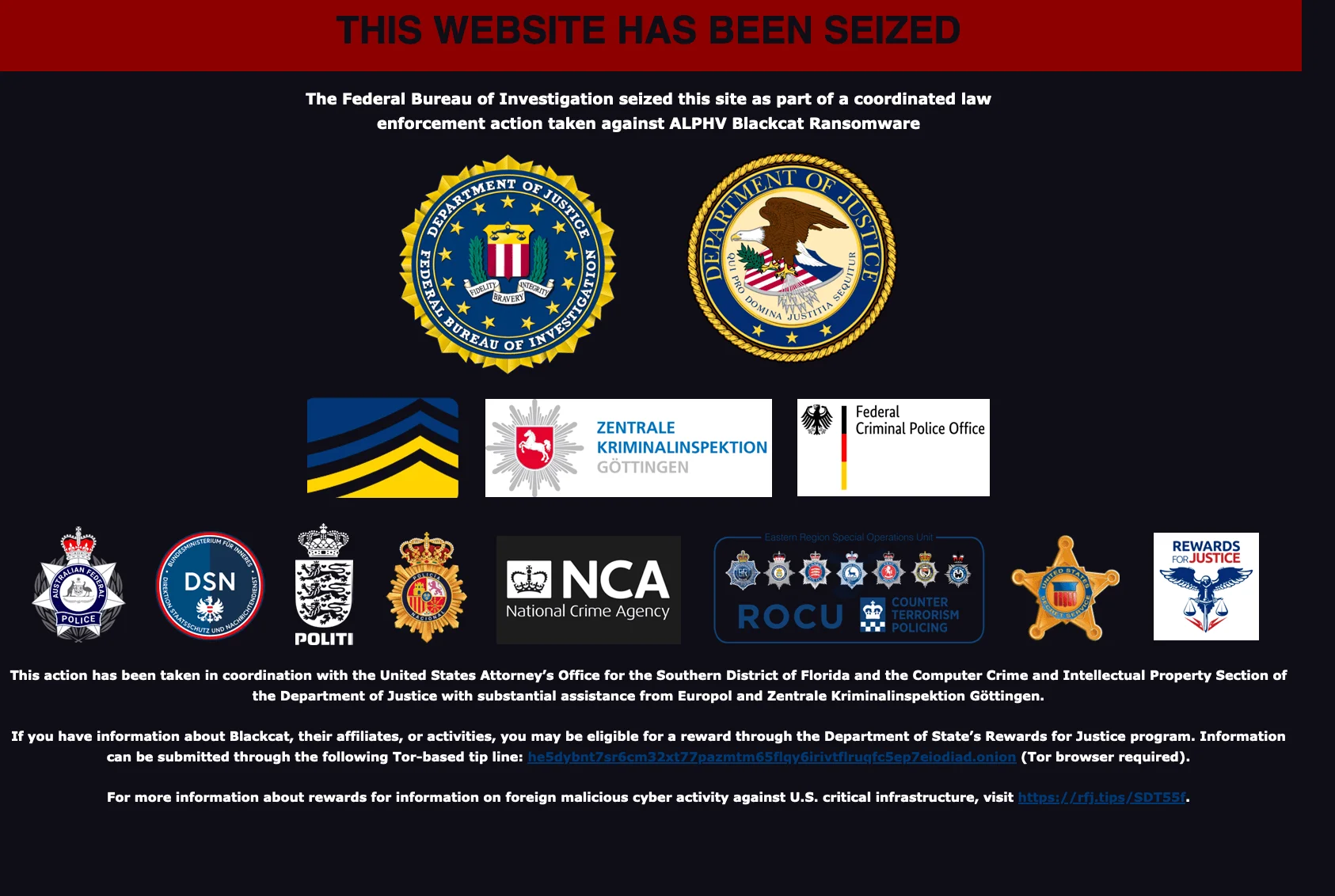
ALPHV’s leak site, seized by Law Enforcement
Initially, the group refused these suggestions. However, the recent seizure of their website shows the real deal. We can say that the group seems to have made the first statement to not lose its affiliates. However, we should also add that seizing their domains may not mean that their operations will stop.
Conclusion
BlackCat, also known as ALPHV, is a ransomware group that was the first to use Rust, a versatile programming language, to create malware that can be customized for different operating systems and evade detection. They have successfully encrypted victims’ files using Rust, emphasizing the need for protection against such attacks. According to Health Sector Cybersecurity Coordination Centre’s (HC3)report about BlackCat, it is believed that BlackCat is focusing its efforts on attacking the healthcare industry, and it is predicted that this trend will continue in the future.
Also, Blackcat operates with triple extortion, which is in addition to double extortion. The threat actor can threaten the victim with DDoS attacks to pay the ransom. When a ransomware attack hits an organization, the attackers gain control of their data, utilizing a double-extortion method. This makes it difficult for organizations to avoid paying the ransom, even if they have offline backups. Organizations need to be aware of potential vulnerabilities in their systems and take steps to address them in order to prevent falling victim to this type of attack.
Threat actors offering Ransomware as a Service can reach high attack volumes quickly and cause greater damage to organizations. Still, this service model can also be a disadvantage because they share their samples with their affiliates, so they may be considered more trackable.
As an example of this, on January 26, 2023, the US Justice Department announced a successful operation against the Hive ransomware group; the FBI seized the website of Hive in coordination with German law enforcement (the German Federal Criminal Police and Reutlingen Police Headquarters-CID Esslingen) and the Netherlands National High Tech Crime Unit.
This disruption by the Justice Department has prevented further extortion and data theft. The operation allowed agents to secretly share decryption keys with more than 300 Hive victims. According to the announcement, the keys helped the victims save an estimated $130 million in payouts.

Security Recommendations Against BlackCat are:
- BlackCat uses previously obtained login information to gain initial access. Implementing multi-factor authentication (MFA) as a requirement for access could potentially block entry points from being compromised.
- The most crucial recommendation is to maintain offline backups when dealing with ransomware. Having offline backups can significantly shorten the time required to return to normal operations and may also save a large number of organizational resources. However, BlackCat has included the DDoS method in addition to encryption and theft of data. Organizations should utilize DDoS protection services to prevent this situation.
BlackCat exploits known Microsoft Exchange server vulnerabilities such as CVE-2021-26855 and CVE-2021-26857 to gain initial access. SOCRadar provides Attack Surface Management which helps gain visibility into external-facing digital assets. With it, security teams can track the vulnerabilities in the environment. Knowing which vulnerabilities are present in the organization can limit the possible attack surface Ransomware operators may exploit.
MITRE ATT&CK TTPs Used by the Blackcat v1
| Tactics | Technique | Technique ID |
| Execution | Malicious File | T1204.002 |
| Execution | Windows Command Shell | T1059.003 |
| Privilege Escalation | Process Injection | T1055 |
| Defense Evasion | Disable or Modify Tools | T1562.001 |
| Discovery | Query Registry | T1012 |
| Discovery | System Information Discovery | T1082 |
| Impact | Inhibit System Recovery | T1490 |
| Impact | Defacement | T1491 |
| Impact | Data Encrypted for Impact | T1486 |
Appendix
BlackCat v1 IoCs:
Hashes:
- MD5:aea5d3cced6725f37e2c3797735e6467
- SHA-1:087497940a41d96e4e907b6dc92f75f4a38d861a
- SHA-256:3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83
Names:
- malware_sample_4.exe
- 220.vir
- 3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83.sample
- 3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83.exe
- keller-exe-3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83.bin.sample
Contacted IPs:
- 13.107.4.50:80 (TCP)
- 192.168.0.40:137 (UDP)
- 192.168.0.71:137 (UDP)
- 20.80.129.13:443 (TCP)
- 20.99.132.105:443 (TCP)
- 20.99.133.109:443 (TCP)
- 20.99.184.37:443 (TCP)
- 23.215.176.115:80 (TCP)
- 23.216.147.64:443 (TCP)
- 23.216.147.76:443 (TCP)
- 23.40.197.184:443 (TCP)
- a83f:8110:0:0:100:0:1800:0:53 (UDP)
- a83f:8110:0:0:6788:21:0:0:53 (UDP)
- a83f:8110:0:0:a800:0:0:0:53 (UDP)
- a83f:8110:492a:d801:d1df:1328:492a:d801:53 (UDP)
- a83f:8110:517c:adff:527d:aeff:507e:aeff:53 (UDP)
- a83f:8110:6a00:0:8803:af1e:5602:0:53 (UDP)
Contacted Domains:
- login.live.com
- prda.aadg.msidentity.com





































