
How Can Extended Threat Intelligence Help CISO’s First 100 Days?
When the expression “first 100 days” is mentioned, we all immediately think of what a leading politician has done from the first day to the hundredth day. These “first 100 days” became iconic during Franklin D. Roosevelt’s first term as the 32nd president of the United States and were considered a way to measure a president’s early success.
Well, can we adapt this success criterion to different sectors and C-level executives? In its May 24, 2021 study, Gartner did just that, detailing what a newly hired CISO should look out for in their first 100 days and how to strike a balance between management’s expectations and the company’s needs.
Challenges of the First 100 Days

The first 100 days of a CISO should be seen as the early process where credibility and leadership qualities are demonstrated. Considering that CISOs are professionals who have advanced their management and communication skills, not in a technical position, it is of great importance for the CISO to position itself correctly by considering the internal balances.
The CISO’s success in communication will be its most crucial ability while meeting the ROI expectations of the company. To evaluate the current security situation, it has to interview different departments, meet with team leaders and correctly understand the attitudes of the staff. The challenge is that some staff minimize existing gaps, while others exaggerate gaps in order to gain more support for their department. Unless the CISO is a good listener and does not make sure it understands the processes correctly, it may be inevitable for the company to produce inconsistent results with ROI expectations and budget efficiency plans.
SOCRadar’s Extended Threat Intelligence solution helps CISOs get the most accurate understanding of ROI expectations in their first 100 days. It provides regional, industrial, and geopolitical-based, actionable intelligence that helps prevent attacks and take a holistic view of the threat landscape. Thus, the CISO can gain insight while assessing current cybersecurity investments and invest in priority areas with high ROI.
What to Expect from a CISO Today?
In a cyber security environment, the most expected attitude from a CISO these days is to be as responsive as possible to future threats and even to act proactively. This approach will be the most important indicator of success, regardless of the company’s size, the industry in which it operates, and its organizational structure.
Today’s organizations operate with complex systems intertwined with many products and services. Therefore, the responsibilities of CISOs spread over a wide area, such as ensuring data security, controlling disruptive situations, and managing third-party cyber risks. You can get a detailed look at the duties and powers of today’s information security professionals by examining the CISO MindMap 2022 prepared by Rafeeq Rahman below.
As can be seen from the mind map above, the CISO has a lot to consider. Good relationships with other departments will help handle these responsibilities, of course. But the CISO will also need an objective perspective. With the support of real-time and data-driven threat intelligence, it will gain powerful insights into which task has which priority.
The Road to a Stronger Security Posture
Speaking of investment expectations, the effect of the first 100 days on the balance sheet should not be overlooked. The CISO must demonstrate how much it can help the company maintain a more robust security posture in the first 100 days of its role. It should clarify that it establishes a proactive security approach, thus preventing some critical attacks and saving the company from a significant loss. At the end of the first 100 days, CISO will be able to prove its success in the ROI report it will give to the board, with data on these prevented attacks and savings.
1. First Things First: Gain Visibility on Your Attack Surface
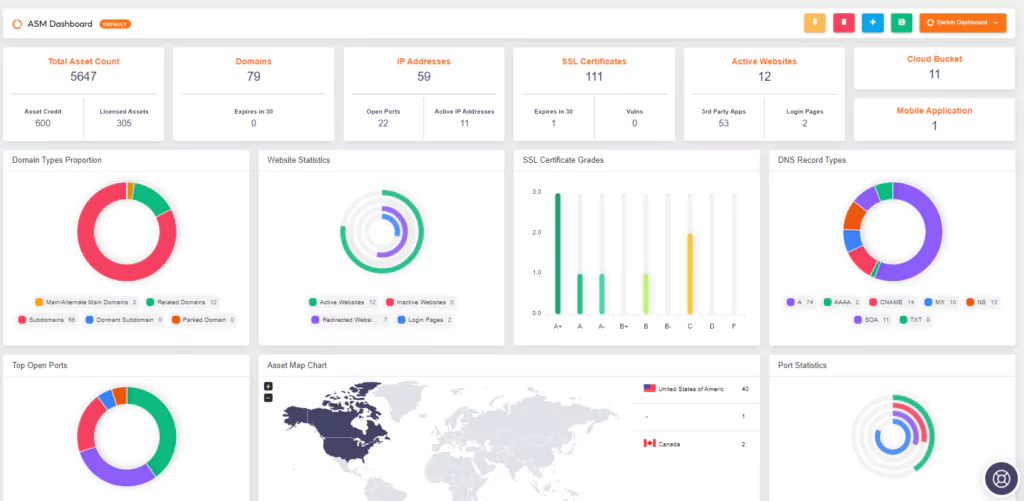
From an information security perspective, a company’s digital assets are everything. The CISO must first take inventory. Listing everything the company owns (domains, social media accounts, employee emails, C-level emails, etc.) is tedious and time-consuming. However, the CISO cannot establish a solid security posture without knowing what to protect. This is where a great dilemma arises. It shouldn’t waste time taking inventory in its first 100 days of success, but it’s also an unmissable issue.
SOCRadar’s External Attack Surface Management suite saves CISOs this chore. With cyber security analysts with a hacker mindset, it takes out the entire inventory within 1-2 days without asking the company for any information about its digital assets. You gain visibility into your internet-facing assets without needing a checklist like in the other ASM services.
SOCRadar EASM has an AI-powered asset identification and classification algorithm. It automatically detects all public infrastructure, including IP addresses, DNS configurations, and cloud applications. It helps prevent financial losses by ensuring successful risk management and preparedness for potential threats.
2. Identify Third Party Threats
Third parties have become inevitably necessary as they provide essential facilitating services in the financial and many other industries. It can be said that many businesses and companies depend on third parties for the processes of their customers and employees.
Exploitation by third parties can be a major threat to the security and financial stability of the company. We saw an example of this in the SolarWinds case. As a result of the attack, the networks of many government organizations and industries were infiltrated.
CISO’s other priority, other than taking an inventory of the company’s digital assets, should be third parties because the supply chain and third parties can create an ungovernable increase in the attack surface of organizations.
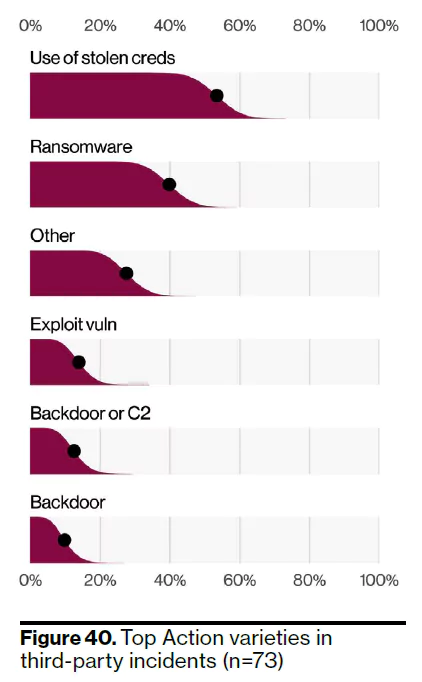
According to Verizon 2022 DBIR, although only a tiny fraction of the total data breaches are third-party breaches, some key findings stand out. Research shows that credentials captured in third-party and supply-chain breaches are used as infection vectors in ransomware attacks.
SOCRadar’s Extended Threat Intelligence solution helps you minimize third-party threats with a holistic approach. Providing real-time intelligence about security vulnerabilities or data breaches of partners in the company’s supply chain makes it easy for CISOs to handle key cyber events. Thus, it provides a strong defense against existing threats and a contextual perspective on risk management.
3. Support Your Arguments About Priorities
After taking the company’s inventory of digital assets, the CISO needs to set priorities for the first 100 days of an action plan. What are the investments planned by the company in the upcoming period? In which region or country do they have stakeholders? What are the predictions about the return on investments to be made here? Questions that fundamentally affect the CISO’s relationship with the board.
Let’s go through a scenario. Let’s say the company plans to invest in the Asian region and realizes its long-term budget accordingly. SOCRadar’s dark web monitoring module provides intelligence that Chinese threat actors are increasing RDP uptake. The CISO’s ability to obtain such broad perspectives on the threat landscape will be instrumental in guiding the company’s initiatives.
The CISO’s implementation of information security practices, both financially and cyclically, with an interdisciplinary approach will play a significant role in the success they will achieve in the first 100 days.
4. Fill the Skill Gap
The efficiency of the SOC team is decisive in the success of the CISO. The fact that the SOC team is not the priority in the investment plans of some companies may complicate the CISO’s job. In such cases, the dilemma of “fewer employees, more needs” arises.
Even though there are enough employees in the SOC team, efficiency problems may occur. It would be more suitable to call it a “shortage of cyber skills.” While threat actors are always busy exploiting a new vulnerability, developing additional features to ransomware, and updating their malware, it can be difficult for the SOC team to keep up with everything.
Cybersecurity teams’ handling of routine manual tasks reduces their efficiency and may cause some things to be overlooked. Automation is critical for personnel to avoid burnout and focus on high-impact situations.
By controlling the attack surface with SOCRadar’s EASM, the CISO receives instant notifications of where the company may be at risk. These notifications are based on contextualized data and are actionable. It works more effectively thanks to the automation that helps reduce the threat surface.
5. Prevent the Human Element from Bringing Up Data Breaches
The human element continues to play the biggest role in data breaches. Verizon’s report shows that the human element is involved in 82% of breaches. Statistic proves social engineering methods are still the most successful way to breach a company’s security.
Aside from the fact that companies need to plan more effective cybersecurity awareness training for their employees, the CISO’s primary duty is to take the necessary measures to avoid data breaches.
The human element can sometimes be caused by forgetfulness, distraction, and lack of awareness. For example, a phishing email ingested by a company employee due to absent-mindedness and lack of knowledge may result in the disclosure of sensitive data or a ransomware infection.
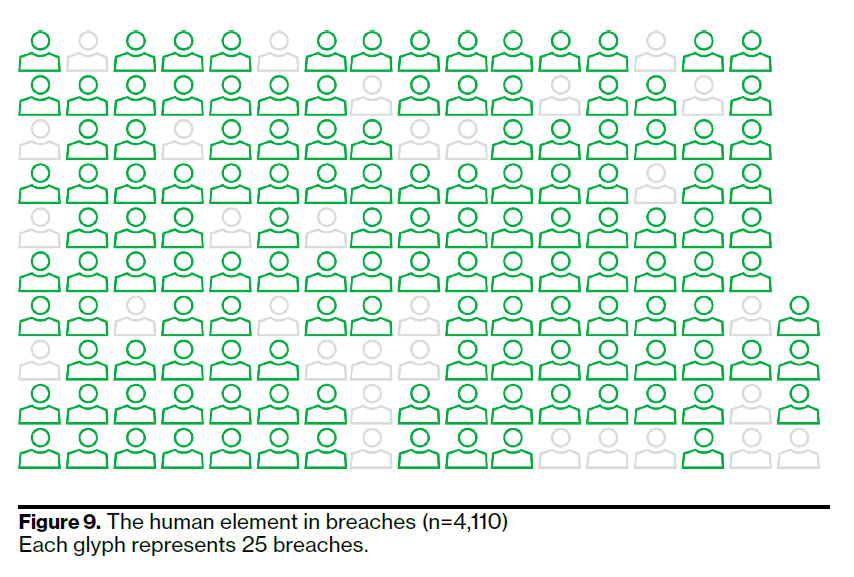
Business Email Compromise (BEC) attacks or phishing attacks by intercepting personal emails of the company’s C-level executives are also cyber incidents in which the human element plays a role.
This nature, which the CISO cannot control alone, can be easily eliminated with SOCRadar’s Digital Risk Protection suite. Providing protection against misconfigured cloud buckets, repositories, expired SSL certificates, threatened emails, phishing domains, and more, SOCRadar DRP helps the CISO save the company millions of dollars in losses.
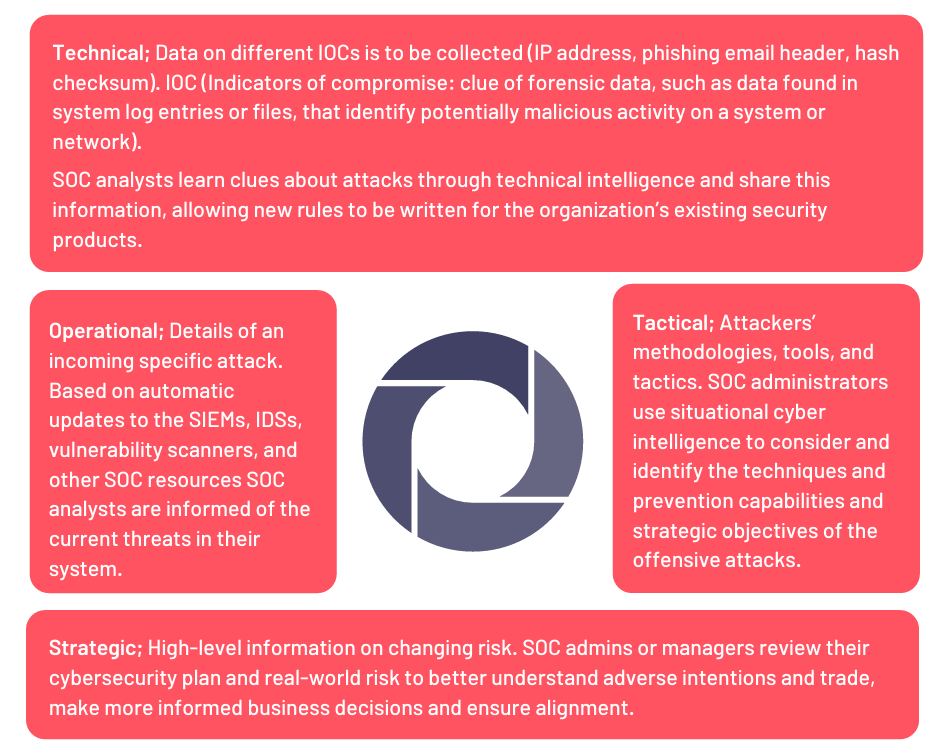
6. The Importance of Cyber Threat Intelligence
Cyber threat intelligence will be the CISO’s most common reference in its first 100 days. It must take all its steps by taking the contextual intelligence and interpreting it correctly because cyber threat intelligence provides the analysis of the current situation and the basis of projection for the future.
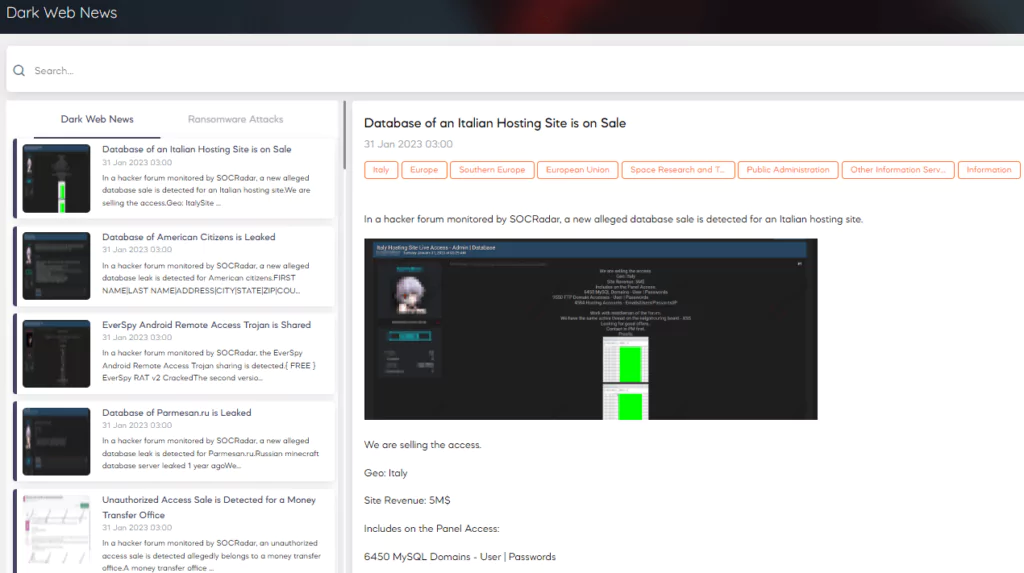
SOCRadar functions like the CISO’s eye on the dark web and is an assistant to the SOC team. It allows the company to find out how popular it is on dark web forums and hackers’ Telegram channels, who is talking about the company, and how.
SOCRadar’s hacker mindset allows immediate detection and intervention with the takedown service when a new script or phishing domain emerges.
Integrated Takedown Service
SOCRadar’s Integrated Takedown is a module of the SOCRadar DRP suite designed to minimize the impact of threat actors on the company’s brand reputation. SOCRadar’s cybersecurity analysts accelerate the takedown process of illegal/fake content and remove procedural barriers using the pervasive communications network.
In Lieu of Conclusion
CISOs are required to establish a threat intelligence-supported cybersecurity posture both in their first 100 days and throughout their careers. Especially when major attacks like SolarWinds or Colonial Pipeline have made it clear that threat actors are always evolving, the understanding of cybersecurity is holding up.
On the other hand, with the permanent introduction of remote working processes into our lives, companies have an expanding attack surface. All this greatly increases the workload of the CISOs and the expectations of the board from them. It is no longer possible for CISOs to persuade management by acquiring various cybersecurity technologies. Now they need to demonstrate that they can understand threat actors’ behavior patterns and calculate potential risks.
Still, CISOs should not despair. SOCRadar is the team player they need for an effective information security program. Take the action you need as an antidote for despair and achieve success after the first 100 days.



































