
Recapping Cyberwatch: Insights and Key Takeaways from April’s Webinar
In today’s digital world, cyberattacks are becoming increasingly frequent and sophisticated, posing a significant threat to individuals, businesses, and governments worldwide. In March, we witnessed several high-profile cyber incidents highlighting the need for robust security measures and cybersecurity awareness. The past month has brought attention to the ever-evolving threat landscape, from supply chain attacks to ransomware attacks and phishing campaigns to data breaches.
We are excited to invite you to our monthly SOCRadar Cyberwatch webinar series to further discuss these incidents and provide insights into the cybersecurity world. In this series, we dive into the top ten most noticeable cyber incidents/news of the past month and explore the impact of these incidents and the lessons learned. The webinars are open to everyone and provide an opportunity for a live discussion to answer questions, share insights, and learn from experts in the field.
In this blog, we will highlight the ten most noticeable cyber incidents/news in March, and again we invite you to join us in the upcoming Cyberwatch webinars. Let’s explore the world of cybersecurity and learn from the most significant events of the past month.
DEV-1101 enables high-volume AiTM campaigns with an open-source phishing kit
An open-source phishing kit called DEV-1101 that Microsoft recently discovered. A phishing kit is a set of tools cybercriminals use to create convincing fake websites that mimic legitimate websites, such as banking or e-commerce. The goal is to trick users into entering their personal or financial information, which criminals can use for fraud.
What makes Dev-1101 unique is that it uses machine learning to adapt its phishing tactics to increase its success rate. For example, it can analyze which techniques and content are working to convince users to enter their information and adjust its tactics accordingly. This makes it a particularly dangerous tool in the hands of cybercriminals, as it can generate high-volume AI-powered phishing campaigns that are more likely to succeed.
Dev-1101 is freely available online, and there are concerns that it could lead to an increase in phishing attacks. Organizations should be vigilant and implement robust security measures to protect against such attacks. This includes training employees on how to spot phishing attempts, using multi-factor authentication, and investing in advanced phishing detection technologies.
UK creates fake DDoS-for-hire sites to identify cybercriminals
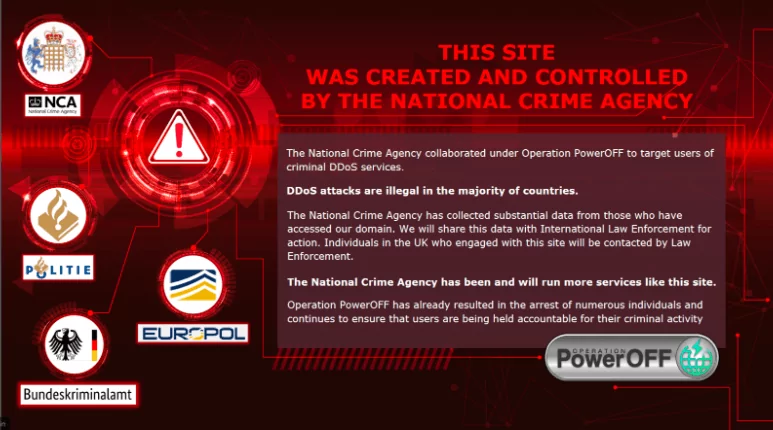
The United Kingdom’s (UK) National Crime Agency (NCA) has created fake distributed denial of service (DDoS) websites to identify cybercriminals who are involved in DDoS attacks.
The NCA created twenty-five fake websites that looked like legitimate DDoS-for-hire services. As expected, these fake websites attracted significant attention from cybercriminals, who were lured in by the promise of low-cost, high-quality DDoS attacks. Visitors to the fake websites were traced by the NCA, and law enforcement identified and analyzed any illegal activity.
The NCA is said to have worked with hosting providers to ensure that the fake websites were not actually capable of launching real DDoS attacks. This was done to ensure that the fake websites did not cause any harm to other legitimate sites on the internet. Instead, the websites were designed to log user activity, IP addresses, and other useful information that investigators could use to identify the criminals.
DDoS attacks are a form of cyberattack where websites are flooded with traffic, making the website unavailable. Cybercriminals commonly use DDoS attacks and can cause significant disruption to websites, businesses, and governments. Using fake DDoS websites by the NCA is a way to deter cybercriminals who may be considering using DDoS attacks in the future.
The strategy of creating fake websites or honey traps is not new. It has been used in the past to catch criminals in a number of fields, including credit card fraud and drug trafficking. However, the use of such techniques in the field of cybercrime investigations is still relatively new. This initiative by the NCA is a significant development in the fight against cybercrime. It shows the authorities are willing to take proactive measures to catch cybercriminals and are eager to think creatively. While it remains to be seen how practical this approach will be in the long run, it is an essential step in tackling the growing problem of cybercrime.
BreachForums out of the equation after pompompurin is arrested by feds
Federal law enforcement officials in the US have brought charges against a man from New York for his alleged involvement in operating the infamous hacking forum, BreachForums. The man, who is known by the online moniker “pompompurin,” is also accused of operating a number of other underground cybercrime services, including credential stuffing tools and remote access trojans (RATs).
The BreachForums website was a popular online platform where cybercriminals could buy, sell, and trade stolen personal data, credentials, and other sensitive information. The website had been active since late 2016 and was known to have traded in a variety of illegal products and services.
The charges against “pompompurin” include conspiracy, racketeering, and various computer fraud and abuse. It is alleged that he was one of the primary administrators of the BreachForums website and was responsible for overseeing its day-to-day operations and maintaining its infrastructure and security.
According to court documents, law enforcement officials identified “pompompurin” after months of analysis of online activity linked to the BreachForums platform. The investigation was reportedly carried out by a task force of federal and international law enforcement agencies, including the FBI, the Department of Justice, and the National Crime Agency in the UK.
The arrest and charging of “pompompurin” are seen as a significant victory for law enforcement agencies in the fight against cybercrime. The BreachForums platform was known to be a hub of cybercriminal activity, and its takedown is expected to particularly impact the broader cybercrime community.
The case also highlights the increasing cooperation and coordination among law enforcement agencies worldwide to combat cybercrime. As cases such as this demonstrate, cybercriminals can no longer hide behind the anonymity of the internet, and law enforcement agencies are becoming increasingly adept at identifying and prosecuting those involved in cybercrime.
Following the recent arrest and charging of the alleged BreachForums administrator by federal law enforcement officials in the United States, there has reportedly been a surge in the number of alternative platforms to BreachForums. While the takedown of BreachForums was expected to significantly impact the wider cybercrime community, other platforms have quickly emerged to fill the void left by BreachForums. These new platforms offer similar services and products, and law enforcement officials are reportedly continuing their efforts to identify and take down these new platforms. The rapid rise of alternative platforms shows that cybercriminals remain very active in their pursuit of illegal activities and highlights the ongoing challenge law enforcement agencies face in combating cybercrime.
Emotet malware distributed as fake W-9 tax forms from the IRS
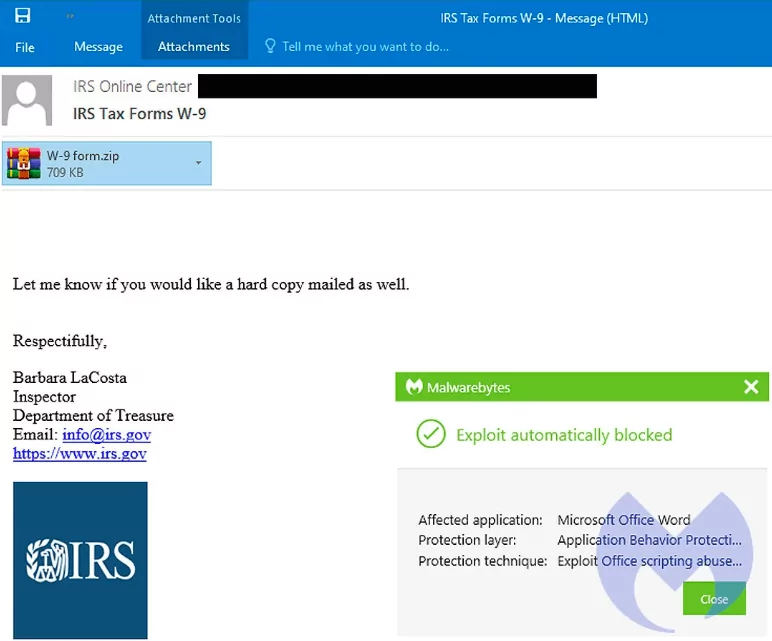
The notorious EMOTET malware is currently being distributed to victims via fake tax forms from the Internal Revenue Service (IRS) in the United States. These fake tax forms are designed to look like W-9 forms, which are used by businesses to gather information from contractors and vendors for tax purposes.
Victims receive an email that appears to be from the IRS requesting them to fill out the attached W-9 tax form. However, the attached form is actually an Emotet malware downloader. Once a victim opens the attachment, Emotet is downloaded to the victim’s computer, and the malware begins to execute malicious code.
As you know, Emotet is a sophisticated banking trojan known for its ability to steal sensitive information from victims, including login credentials and financial information. Cybercriminals often use it to steal money from victims’ bank accounts and carry out other fraudulent activities.
If you like to read a comprehensive analysis of Emotet, here is the link.
The distribution of Emotet via fake W-9 tax forms is just one of many tactics cybercriminals use to spread malware and other forms of cyber attacks. It is crucial for users to exercise caution when receiving unsolicited emails or attachments, particularly those that request sensitive information.
In this case, it is recommended that users verify the authenticity of the email before opening any attachments. Official communications from government agencies, such as the IRS, typically include specific language and formatting that can help users identify whether an email is legitimate or not.
The use of fake tax forms to distribute Emotet is also a reminder of the importance of ensuring that software and security systems are up-to-date and properly configured. Keeping anti-virus software and other security applications up-to-date can help protect against the latest malware and other cyber attacks.
DBatLoader: Actively distributing malware targeting European businesses
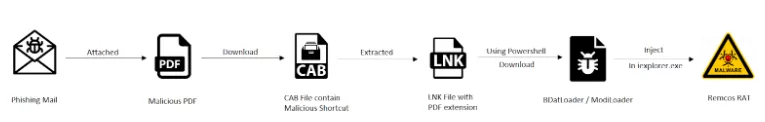
A new type of malware called DBatLoader is currently targeting European businesses by actively distributing malicious code under the guise of SQL management tools. The malware is especially insidious because it uses tactics such as loading executables and creating scheduled tasks. It can run entirely in memory to avoid detection by anti-virus software.
DBatLoader actively targets various types of business systems, including HR and accounting applications, intending to steal sensitive data. The malware is being propagated through spam campaigns and malvertisements and involves obfuscation techniques to prevent detection. The security firm suggests that businesses should remain vigilant to emails that are not expected or from unfamiliar senders and verify files before executing them.
Fake Microsoft SharePoint alerts are being used to share malware
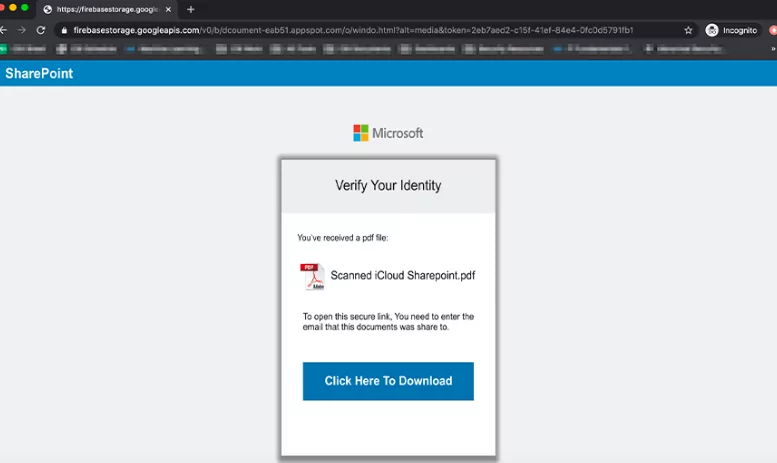
Fraudsters now use fake automated SharePoint messages as a starting point to steal Office 365 login credentials.
A new phishing campaign has been identified that uses fake SharePoint alerts to trick users into revealing their login credentials. The phishing emails look like legitimate SharePoint alerts that request users to ‘Review and sign’ a shared file. The email contains a link that takes users to a phishing page that harvests their login credentials.
The phishing page looks the same as an actual SharePoint online login page and even features a valid SSL certificate. The attacker retrieved the details in the phishing page via a script that sends it to the attacker’s servers. However, it is unclear what the attackers use the stolen login credentials for.
This is not the first time attackers have used SharePoint alerts to launch phishing attacks. In 2020, security researcher Jake Moore warned cybercriminals were using fake SharePoint invitations to distribute malware. It is also a reminder that phishing is still one of the most effective ways cybercriminals use to compromise systems and steal data. Users must remain vigilant and take appropriate steps to protect themselves from phishing attacks, such as checking the authenticity of emails before clicking on any links or downloading attachments.
ChatGPT leaks bits of users’ chat history
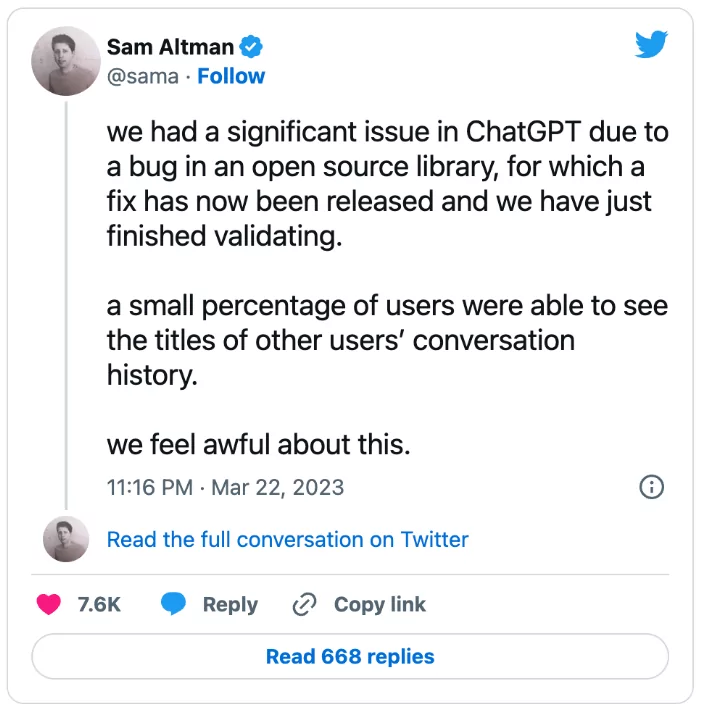
Researchers have uncovered an unsecured Redis instance belonging to OpenAI, which led to a data leak of their GPT-3 language model. The instance allowed anyone with internet access to control more than a single terabyte of data, including training code, testing code, configuration files, models, and model weights. OpenAI confirmed the data leak and stated that the information leaked was about the quality of the machine learning (ML) models but reiterated that no user data had been revealed.
Among the data found was an OpenAI program announcing that researchers had discovered a way of bypassing the company’s filters to get its GPT language model to generate racist, sexist, or otherwise toxic output. Researchers have described OpenAI’s GPT model as having an “unprecedented” capacity to learn patterns in language input and being capable of generating coherent paragraphs of text that are “extremely difficult” to distinguish from text written by humans.
As a result of the leak, OpenAI clarified that the Redis instance was used by staff to submit and collect jobs from Redis. Though remnants of confidential data may still be public and accessible, OpenAI currently perceives no direct security threat to their platform from the leak.
This incident highlights the importance of securing data, especially for companies working with sensitive data like OpenAI. Furthermore, the data leak also reveals the high-stakes risks and ethical considerations when dealing with large volumes of data and AI models that produce language, highlighting the need for better transparency in AI research.
A New APT: BadMagic
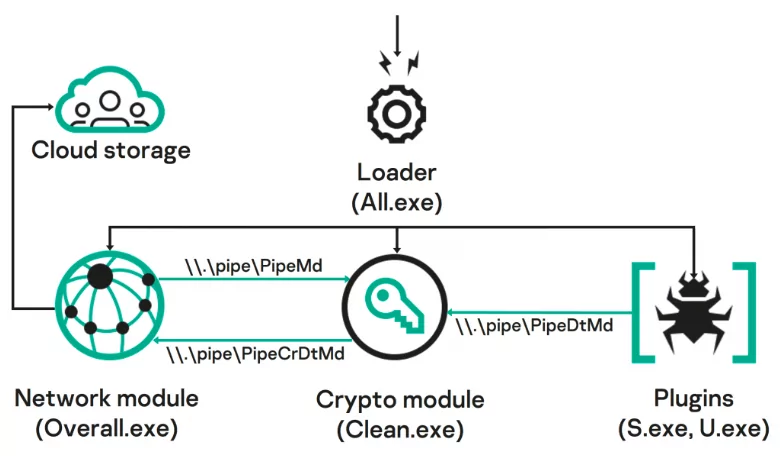
An advanced persistent threat (APT) group dubbed BadMagic was discovered. The group has operated since 2016 and typically targets organizations involved in technology, engineering, and international development. Victims have been found located in South and South-East Asia, Eastern Europe, Central Asia, and Northern Africa.
The modus operandi of the BadMagic group involves a carefully orchestrated series of steps, starting with phishing emails and moving on to using off-the-shelf penetration testing tools to gain a foothold in a network. The group circumvents security measures, flies under the radar, and maintains a low profile using techniques like steganography, packed malware binaries, and conventional encryption.
Once the group has penetrated a network, they focus on gaining privileged access, including domain administrator rights, which enables them to move laterally with less oversight from network security. The group generally avoids deploying malware, relying on built-in tools and publicly available frameworks to achieve their objectives.
BadMagic uses infrastructure, malware, and tactics that resemble those of other threat actor groups, namely Hellsing and Naikon APTs. Researchers have also discovered the group has ties to a group that was working on behalf of an unknown Southeast Asian country’s government. The group was targeting international diplomatic and government agencies.
This discovery highlights the fact that despite being smaller scale, the APT groups like BadMagic can still pose a risk to organizations’ cybersecurity protocols, which may incorporate a combination of different threat models. The use of publicly available tools and the avoidance of custom-made malware might make such groups more difficult to detect, emphasizing the ongoing need for robust security protocols and situational awareness.
More Android and iOS zero-days detected for installing spyware
Google’s Threat Analysis Group (TAG) has discovered a series of zero-day vulnerabilities that were used to target Android and iOS users with malware. The previously unknown vulnerabilities were leveraged by a few exploit developers known to have been involved in nation-state-level mobile surveillance campaigns, including NSO Group of Israel.
The attackers used a variety of exploits, including iMessage, which bypassed the native iOS sandbox to allow for privilege escalation and device persistence. In the Android ecosystem, attackers used Chrome sandbox escapes to install malware without user interaction. The group also used two exploits that impacted devices running on Android 4.4 to 5.0 and another that worked on Android 8.0 and higher.
The campaign was highly targeted, using phishing and messaging lures to redirect victims to malicious websites that hosted the precursor stages of the attack. Once compromised, attackers could monitor and collect victims’ data using various surveillance capabilities.
Google has stated that it has notified Apple and patched the vulnerabilities in the latest iOS update. Nevertheless, the investigation highlights the ongoing presence of zero-day vulnerabilities in the mobile ecosystem and the sophisticated measures used by attackers to compromise devices. The discovery emphasizes the need for users to ensure their mobile operating systems are up to date and that they exercise caution when clicking on suspicious links or opening unsolicited messages.
Twitter takes down source code leaked online, hunts for downloaders
Twitter has confirmed that it was the victim of a security breach, which resulted in the publication of a large amount of the company’s confidential data on various underground forums. Specifically, the situation involves the source code of an old version of Twitter’s iOS app. Although it is outdated, the code may reveal previously unknown exploits or potential weaknesses that attackers could exploit.
The incident highlights the risk of insider threats and the need for appropriate security protocols to maintain the confidentiality of essential information. Twitter has stated that the information was not accessed via a network breach but by an authorized individual who violated policies and misused access privileges.
Twitter has dismissed the possibility of the breach being a state-sponsored hack, instead identifying the culpable employee and taking immediate remedial actions to contain the breach. The company has notified relevant authorities and is investigating the incident more thoroughly. Twitter has also clarified that it took swift action to remove any published data, revoke access to the toolsets involved, and restrict access to its production environments. As part of its investigation, Twitter is also intensifying efforts to identify any downloaders of the code and is taking legal steps to ensure that its customers’ and partners’ confidential information and intellectual property remain protected.
If you want to stay ahead of the latest cyber threat trends and incidents and receive deep analysis, then it’s time to subscribe to our platform. You will receive regular updates on the latest cyber threats, malware, and vulnerabilities by subscribing. Our cybersecurity experts provide up-to-date analysis and reporting on the cyber threat landscape, as well as comprehensive guides to help you protect your network and data. In addition, you will receive access to exclusive content, which will help you stay informed and make better cybersecurity decisions. Don’t wait until it’s too late; click the links now to subscribe and stay protected.

References
- https://www.microsoft.com/en-us/security/blog/2023/03/13/dev-1101-enables-high-volume-aitm-campaigns-with-open-source-phishing-kit/
- https://www.bleepingcomputer.com/news/security/uk-creates-fake-ddos-for-hire-sites-to-identify-cybercriminals/
- https://krebsonsecurity.com/2023/03/feds-charge-ny-man-as-breachforums-boss-pompompurin/
- https://www.bleepingcomputer.com/news/security/emotet-malware-distributed-as-fake-w-9-tax-forms-from-the-irs/
- https://www.zscaler.com/blogs/security-research/dbatloader-actively-distributing-malwares-targeting-european-businesses
- https://www.bankinfosecurity.com/phishing-campaign-uses-fake-sharepoint-alerts-a-14721
- https://securityaffairs-com.cdn.ampproject.org/c/s/securityaffairs.com/144057/data-breach/openai-chatgpt-redis-bug-data-leak.html?amp=1
- https://securelist.com/bad-magic-apt/109087/?utm_source=substack&utm_medium=email
- https://www.bleepingcomputer.com/news/security/google-finds-more-android-ios-zero-days-used-to-install-spyware/
- https://www.bleepingcomputer.com/news/security/twitter-takes-down-source-code-leaked-online-hunts-for-downloaders/


































