Top 10 Threat Actors of 2024: Beyond the Numbers
Although 2024 isn’t over yet, the cyber landscape has already witnessed significant developments. This year has been shaped by a complex network of threat actors, each leaving a mark not just through the volume of their attacks but also through their popularity, scandals, and unique tactics. This blog post highlights the top 10 threat actors of the year, especially those featured on the SOCRadar blog, shedding light on their impact and the noise they’ve created in global cybersecurity.
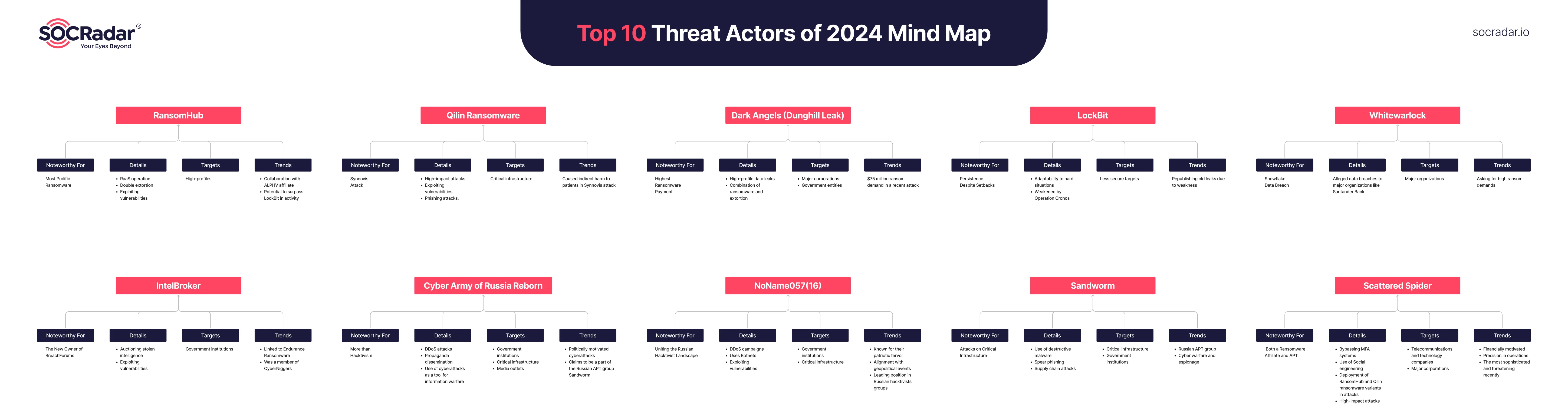
Mind Map of Top 10 Threat Threat Actors in 2024
1. RansomHub
Noteworthy For: Most Prolific Ransomware
RansomHub is a Ransomware-as-a-Service (RaaS) operation that surfaced in early 2024, swiftly gaining attention due to its unique business model. Unlike traditional ransomware groups, RaaS platforms like RansomHub function as decentralized hubs, providing customized ransomware services to various cybercriminals. Their adaptability, use of double extortion techniques, and focus on high-profile targets have positioned them as a significant force in the cybercrime landscape this year. RansomHub’s rapid ascent mirrors the broader trend of ransomware’s rise and the decline of several major players.
With LockBit’s decline, RansomHub is on track to become this year’s most prolific ransomware operator. Their initial collaboration with an ALPHV affiliate drew public attention, and they continue to pose an increasing threat.
Check out our blog post on RansomHub.
2. Qilin Ransomware
Noteworthy For: Synnovis Attack
Qilin Ransomware began operations before 2024 and swiftly gained notoriety by targeting critical infrastructure sectors such as energy, transportation, and more recently, healthcare. Their strategic focus on these high-impact areas has drawn significant attention. Qilin’s sophisticated tactics and the severe consequences of their attacks this year have established them as a top-tier threat actor in 2024.
Their attacks on Synnovis, in particular, made headlines and caused significant disruption to many healthcare institutions across the UK. These ransomware attacks even indirectly harmed patients, highlighting the group’s dangerous impact.
3. Dark Angels
Noteworthy For: Highest Ransomware Payment
Dark Angels or Dunghill Leak group has made waves with a series of high-profile data leaks, targeting major corporations and government entities. Their modus operandi involved a now became a traditional combination of ransomware and extortion, where they publicly leak sensitive data if their demands are not met. This tactic has not only caused significant financial and reputational damage but has also made them a household name in the cybersecurity world.
In a recent high-profile attack, Dark Angels demanded an astonishing $75 million ransom from their victim, marking one of the largest ransom demands in ransomware history.
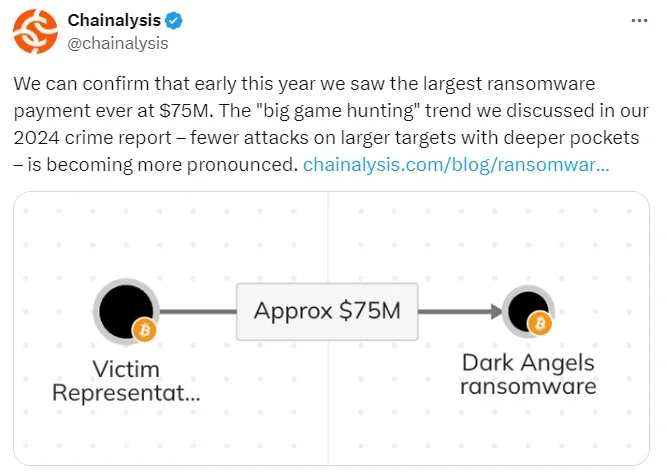
Chainalysis confirmed the transaction (X)
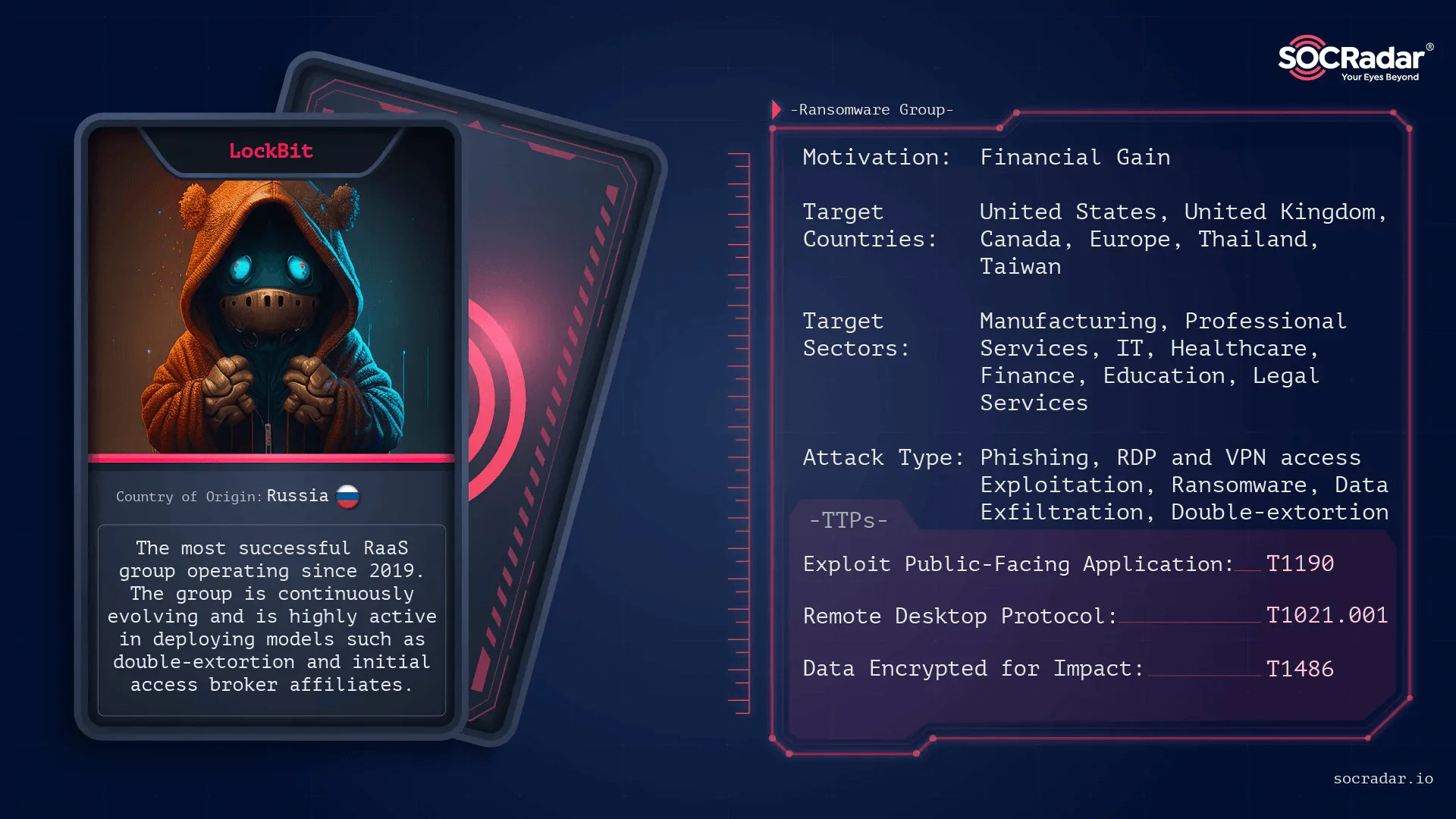
4. LockBit
Noteworthy For: Persistence Despite Setbacks
LockBit remains a formidable player in the ransomware landscape. Despite significant setbacks, including heightened law enforcement scrutiny and internal challenges, they have managed to persist. Their adaptability, particularly in shifting focus to less secure targets, has allowed them to stay among the most active and feared ransomware groups of 2024.
However, it’s clear that LockBit is losing ground. Recently, they’ve resorted to republishing old leaks and claims, indicating the impact of Operation Cronos once again. This operation has dealt a significant blow to LockBit’s activities. For more details, check out our blog post on Operation Cronos.
5. Whitewarlock
Noteworthy For: Snowflake Data Breach
Snowflake, a leading cloud-based data storage and analytics provider, recently faced a cybersecurity controversy. Reports revealed that unauthorized access to its systems may have exposed sensitive data from several prominent clients.
The incident was notably linked to a threat actor using the alias “Whitewarlock.” This individual first appeared on the Russian dark web forum Exploit.in on May 23, 2024, claiming to have released data obtained from the breach on that same day. The threat actor alleged that they had accessed sensitive information from major organizations such as Santander Bank and Ticketmaster.
Check out our blog post about the whole timeline of Snowflake and many other threat actors involved.
6. IntelBroker
Noteworthy For: The New Owner of BreachForums
IntelBroker has established a niche by auctioning stolen intelligence, including government secrets and corporate trade secrets, to the highest bidder. Its activities have highlighted vulnerabilities in both public and private sector defenses, with significant consequences for numerous organizations.
IntelBroker, Owner of the BreachForums
One of the most prominent members of BreachForums, IntelBroker, who is also linked to ransomware operations under the name Endurance Ransomware, emerged in late 2022 and gained notable infamy by early 2023. Recently, IntelBroker even acquired ownership of BreachForums amid ongoing debates about the forum’s legitimacy and repeated seizures. For more details, check out our blog post on IntelBroker.
7. Cyber Army of Russia Reborn
Noteworthy For: More than Hacktivism
The Cyber Army of Russia has reemerged in 2024 as a key player in the realm of cyber hacktivism, driven by strong nationalist motives. This group, often linked to Russian state interests, has focused on launching politically charged cyberattacks against entities opposing Russian policies. Their operations are a mix of propaganda dissemination and disruptive attacks, targeting government institutions, media outlets, and critical infrastructure in Western nations.
What sets the Cyber Army of Russia apart is their use of cyberattacks as a tool for information warfare, aiming to influence public opinion and sow discord aligning to Russia’s interest amongst the claims to be a part of Russian APT group Sandworm. In 2024, the group was particularly active during geopolitical crises, where they orchestrated DDoS attacks and defaced websites with pro-Russian messages. Their ability to quickly mobilize and adapt to shifting political landscapes has made them a formidable force in the cyber arena this year.
8. NoName057(16)
Noteworthy For: Uniting the Russian Hacktivist Landscape
NoName057(16) has made headlines throughout 2024 for its relentless DDoS campaigns, primarily targeting government websites and critical infrastructure in Western countries. Known for their patriotic fervor, this group has been associated with pro-Russian hacktivist activities, often aligning their attacks with geopolitical events.
NoName057(16) has demonstrated a remarkable ability to disrupt services and create chaos, making them a significant nuisance on the cyber stage. Their attacks have grown more sophisticated over the years, leveraging botnets and exploiting vulnerabilities to maximize impact. Despite facing multiple takedown attempts, the group continues to adapt and evolve, maintaining its position as a top threat actor of 2024. Thus, that’s not all, this year many Russian groups aligned their activities and NoName057(16) seems to be in the leading position.
Check out our blog post on NoName057(16).
9. Sandworm
Noteworthy For: Attacks on Critical Infrastructure
Sandworm, a notorious Russian APT group, is renowned for its cyber warfare and espionage activities. In 2024, they remained a major player in executing significant cyber operations against critical infrastructure and government entities across Europe and beyond. Sandworm’s trademark is its use of destructive malware, which has led to widespread disruption and damage.
In 2023, Sandworm was notably involved in a high-profile campaign against energy grids in Ukraine. This attack highlighted the severe vulnerabilities in critical infrastructure and drew considerable attention to the group’s capabilities. Known for their sophisticated spear phishing and supply chain attacks, Sandworm has proven to be a persistent and dangerous threat actor on the global stage. For further readings you may check out our blog post about Sandworm.
10. Scattered Spider
Noteworthy For: Both a Ransomware Affiliate and APT
Scattered Spider, a financially motivated cybercrime group, has gained infamy in 2024 for its targeted attacks on telecommunications and technology companies. Their operations are marked by precision and their ability to bypass Multi-Factor Authentication (MFA) systems, enabling them to infiltrate networks and exfiltrate sensitive data.
The group’s tactics often involve social engineering and exploiting human vulnerabilities, making them particularly effective against large corporations. Recently, Scattered Spider has been deploying RansomHub and Qilin ransomware variants in its attacks, signaling a potential power shift among hacking groups. According to Microsoft’s incident response engagements from the second quarter of the year, Scattered Spider is now recognized as one of the most sophisticated and threatening groups currently in operation.
Scattered Spider’s ability to stay under the radar while executing high-impact attacks has solidified their place as one of the top threat actors of the year. Their relentless approach, especially in targeting critical industries, highlights their significant threat to cybersecurity in 2024.
Explore the Threat Actors and Their Tactics With SOCRadar
SOCRadar’s Operational Intelligence Trends Dashboard offers unparalleled, real-time insights to empower your defense strategies. With this tool, you can track the rise and fall of major ransomware groups, identify geographical trends in threat actor activities, and target regions with precision. The dashboard also provides comprehensive threat reports, allowing you to grasp the broader context of the evolving threat landscape.
SOCRadar Operational Intelligence, Threat Actors Intelligence
Additionally, it highlights the most frequently exploited vulnerabilities by cybercriminals, giving you foresight into potential attack vectors. Stay informed about the most recent victims and campaigns, ensuring you’re always a step ahead. With SOCRadar, you gain the intelligence needed to navigate the complexities of today’s cyber threats. For further analysis and continuous updates, explore our Threat Actors page and fortify your cybersecurity posture.