Almost Impossible to Detect Symbiote Linux Malware
Almost Impossible to Detect Symbiote Linux Malware The newly discovered Linux malware Symbiote can easily infect and hide in almost any process on compromised systems. The malware steals account ...

Ransomware Groups Target VMware and QNAP Products
Ransomware Groups Target VMware and QNAP Products Linux-based Black Basta ransomware targets VMware ESXi virtual machines, while DeadBolt ransomware targets QNAP NAS (network-attached storage) product...

Mandiant Leak Alleged: A PR Trial?
Mandiant Leak Alleged: A PR Trial? LockBit ransomware gang claimed that they had stolen Mandiant’s data. The gang posted a countdown on their data leak site earlier today. They c...

What Do You Need To Know About Atlassian Confluence RCE Vulnerability?...
What Do You Need To Know About Atlassian Confluence RCE Vulnerability? After it was disclosed that the RCE vulnerability with the code CVE-2022-26134, which affects Atlassian Confluence and Data Cent...
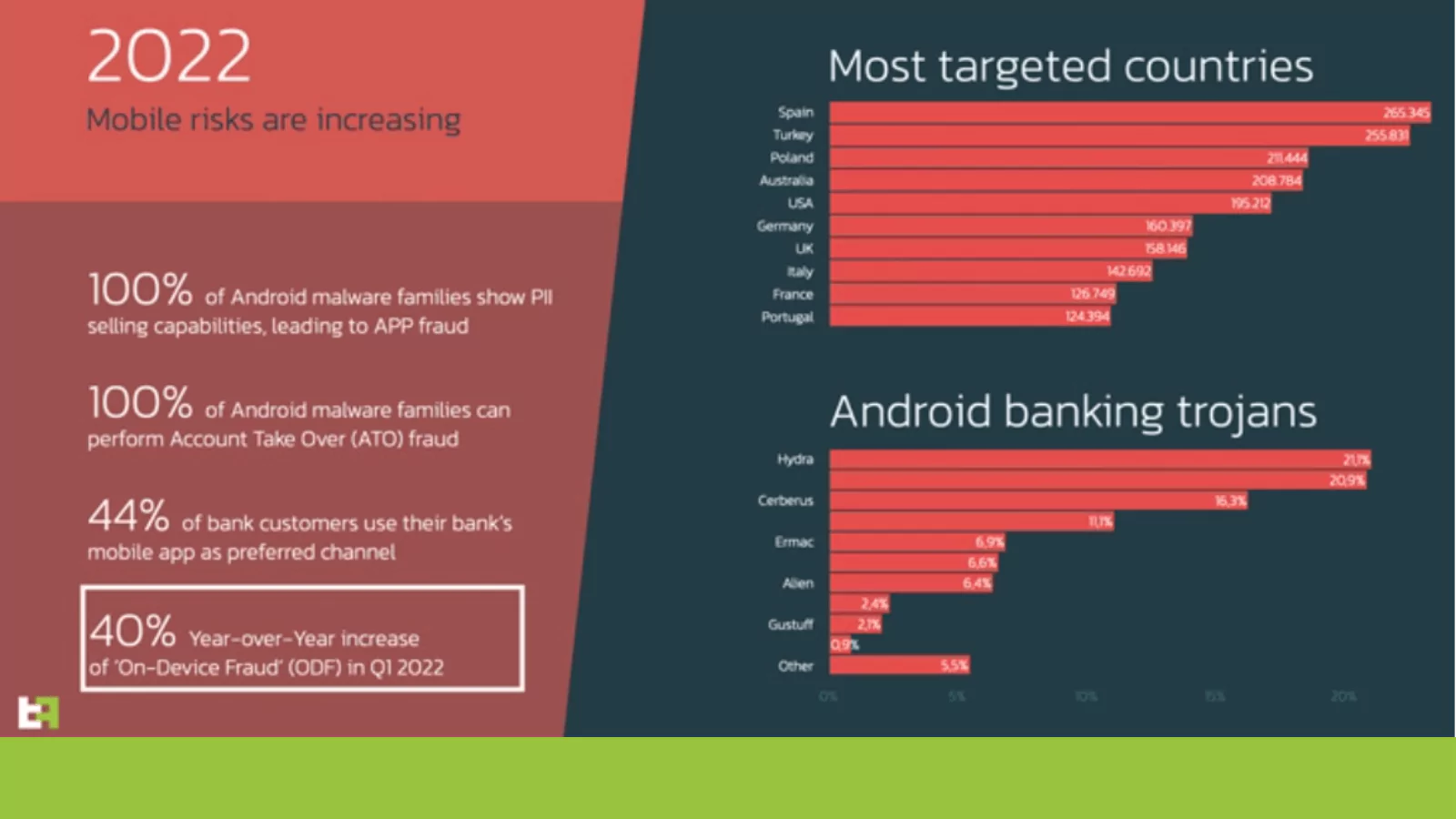
On-Device Fraud Trend in Mobile Malware Campaigns
On-Device Fraud Trend in Mobile Malware Campaigns According to the 2022 mobile threat landscape analysis published byThreatFabric, ODF (on-device fraud) banking trojans targeting A...

Workarounds for Microsoft Office Zero-Day RCE Vulnerability "Follina" ...
Workarounds for Microsoft Office Zero-Day RCE Vulnerability “Follina” has Released The Follina zero-day vulnerability in Microsoft Office allows threat actors to perform remote code e...

GitHub Announces 100,000 npm Users' Credentials Stolen
GitHub Announces 100,000 npm Users’ Credentials Stolen GitHub has announced that 100,000 npm user information was stolen through OAuth tokens linked to Heroku and Travis CI. It was previously&nb...

PoC Released for Authentication Bypass Vulnerability in VMware
PoC Released for Authentication Bypass Vulnerability in VMware Vulnerability-related PoC has been published that allows threat actors to bypass authentication across multiple VMware products. VMw...

What Do You Need To Know and Do About Compromised CTX Module in Python...
What Do You Need To Know and Do About Compromised CTX Module in Python Package Repositories? According to a post on Reddit, evidence was presented that the CTX module in the Python package repositorie...

Turla Reconnaissance Campaign Targets Eastern Europe
Turla Reconnaissance Campaign Targets Eastern Europe The reconnaissance and espionage campaign of the Russia-linked Turla hacker group against the Austrian Economic Chamber, Baltic Defense College, an...

Conti Ransomware Ended: They Operate With Other Groups Now
Conti Ransomware Ended: They Operate With Other Groups Now The Conti ransomware gang had taken its infrastructure offline and ceased operations. According to the news of Advanced Intel’s Yelisey...

New Botnet Discovered Exploiting Critical VMware Vulnerability
New Botnet Discovered Exploiting Critical VMware Vulnerability The critical VMware vulnerability with code CVE-2022-22954 was discovered to be used by threat actors for remote code execution in botnet...

Critical Vulnerability in Zyxel Firewall and VPN Products Exploited
Critical Vulnerability in Zyxel Firewall and VPN Products Exploited Threat actors exploit the critical vulnerability affecting Zyxel’s firewall and VPN devices. The vulnerability allows attacker...

BPFdoor Malware Targets Linux Systems Unnoticed for Five Years
BPFdoor Malware Targets Linux Systems Unnoticed for Five Years It turned out that the backdoor malware called BPFdoor, which cybersecurity researchers recently discovered, has been targeting Linux and...

10GB Database of Popular VPN Apps Leaked
10GB Database of Popular VPN Apps Leaked Threat actors shared a 10GB database allegedly belonging to popular VPN apps such as SuperVPN, GeckoVPN, and ChatVPN companies in a Telegram group. The databas...

Microsoft May 2022 Patch Tuesday: Three Zero-Days Total 75 Vulnerabili...
Microsoft May 2022 Patch Tuesday: Three Zero-Days Total 75 Vulnerabilities Fixed Microsoft has released the May 2022 Patch Tuesday. The patches fix three zero-day vulnerabilities, one of which is...

Critical Azure Vulnerability Creates a Massive Attack Surface
Critical Azure Vulnerability Creates a Massive Attack Surface Microsoft has released patches for a vulnerability that affects Azure Synapse and Azure Data Factory products, allowing threat actors to R...
Critical BIG-IP iControl REST Vulnerability Allows Arbitrary Code Exec...
Critical BIG-IP iControl REST Vulnerability Allows Arbitrary Code Execution A critical vulnerability discovered by F5 on May 4 allows threat actors to bypass iControl REST authentication. The flaw whi...

Why do Companies Need Cybersecurity?
Why do Companies Need Cybersecurity? Cybersecurity encompasses all technologies and techniques that ensure the integrity of computer systems and electronic data. And, at an age where more and more of ...

Critical Vulnerability in WSO2 Products Could Allow RCE
Critical Vulnerability in WSO2 Products Could Allow RCE It turned out that a critical vulnerability that affects the products of WSO2 and enables RCE has been actively exploited. WSO2 has a wide portf...