
Windows 0-Day Exploit and RDP Access Sales, Database Leaks for Domasa ...
Windows 0-Day Exploit and RDP Access Sales, Database Leaks for Domasa City and Jeevess Ayurveda Threat actors persist in engaging in illicit activities within the enigmatic realm of the dark web. The ...

New Botnet Sale and Recruitment Post, US and Canada RDP Access Sale, D...
New Botnet Sale and Recruitment Post, US and Canada RDP Access Sale, Dymocks Database In this week’s dark web update, the SOCRadar Dark Web Team has revealed a series of troubling developments; ...

Dark Web Profile: NoEscape Ransomware
Dark Web Profile: NoEscape Ransomware Avaddon, a notorious Ransomware-as-a-Service (RaaS) that emerged in early 2019 was known for its double-extortion tactics. It not only encrypted victims’ files bu...

Dark Web Profile: USDoD
Dark Web Profile: USDoD [Update] October 17, 2024: See the subheading: “Brazilian Arrest Tied to USDoD” [Update] August 26, 2024: See the subheading: “Is USDoD’s Identity Revealed?” [Update] April 22,...

Remote Administration Tool Sale, Ledger Database Leak, and Dark Strom ...
Remote Administration Tool Sale, Ledger Database Leak, and Dark Strom DDoS Attack In this week’s dark web roundup, we bring you a series of concerning developments that the SOCRadar Dark Web Tea...

LockBit’s New Regulations Sets Minimum For Ransom Demands
LockBit’s New Regulations Sets Minimum For Ransom Demands Recently, the notorious LockBit ransomware group has initiated a significant discussion among its affiliates regarding potential cha...

Cobalt Strike Leak, Sales of Unauthorized Access and Credit Card Data
Cobalt Strike Leak, Sales of Unauthorized Access and Credit Card Data The SOCRadar Dark Web Team conducts continuous monitoring of the dark web, uncovering the latest threats that require your attenti...

Major Cyberattacks in Review: August 2023
Major Cyberattacks in Review: August 2023 August 2023 has not passed without its share of significant cyberattacks. Among the incidents of last month, we have observed multiple data breaches involving...
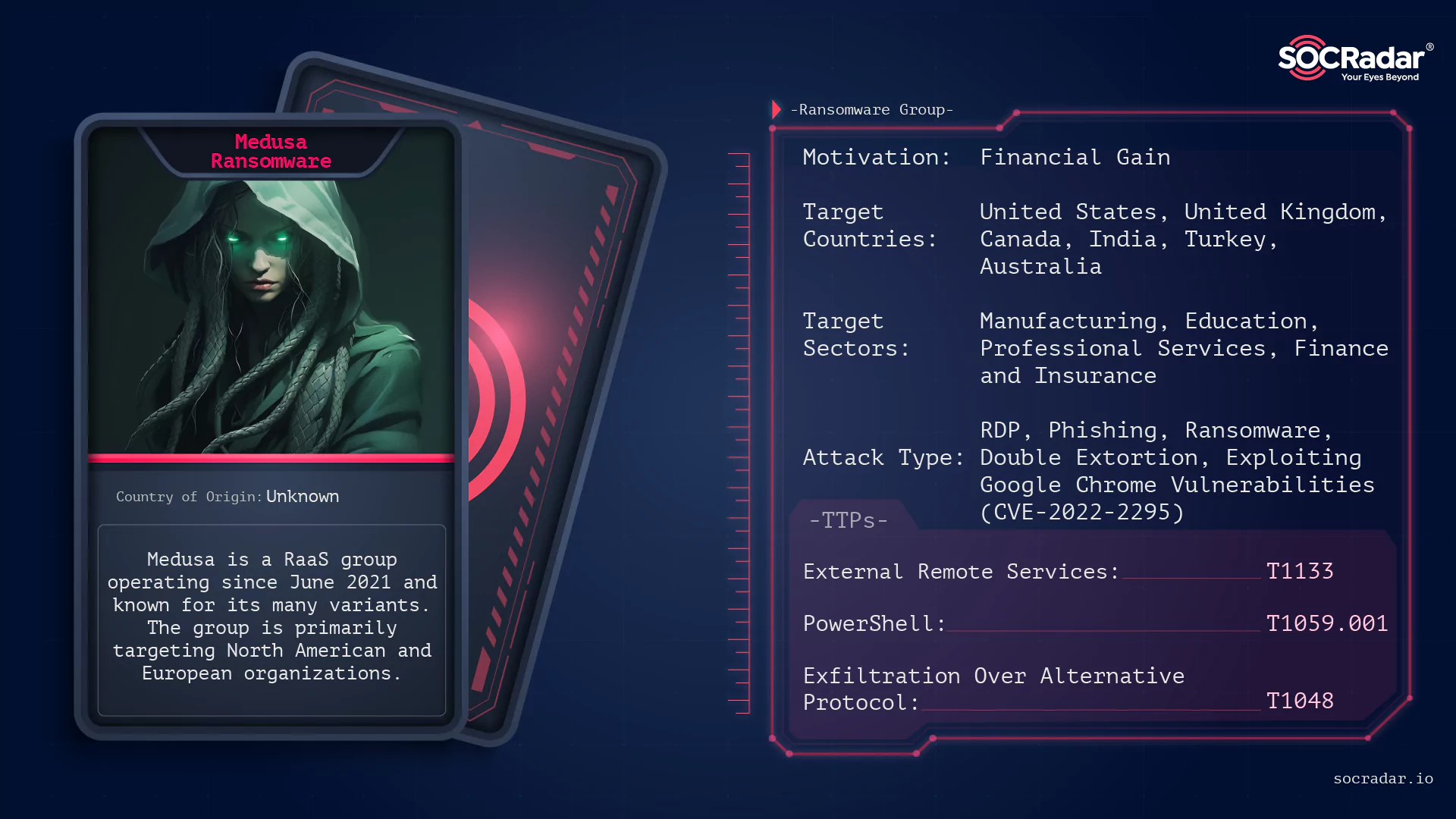
Dark Web Profile: Medusa Ransomware (MedusaLocker)
Dark Web Profile: Medusa Ransomware (MedusaLocker) [Update] March 13, 2025: CISA, FBI, and MS-ISAC Warn of Medusa Ransomware Threats in New Advisory In ancient Greek mythology, Medusa stands as one of...

Sales of International IDs, UK Bank Leads, Fully Undetectable Crypter,...
Sales of International IDs, UK Bank Leads, Fully Undetectable Crypter, US Instagram Database Leak Introducing our weekly Dark Web digest, where we explore the most recent occurrences in the online und...

Ferrari Breach, 8.3M French Citizen Data Leak, Jeeves Card Leak & ...
Ferrari Breach, 8.3M French Citizen Data Leak, Jeeves Card Leak & More Welcome to this week’s Dark Web roundup, where we delve into the latest unsettling incidents that have emerged from the...

On the Horizon: Ransomed.vc Ransomware Group Spotted in the Wild
On the Horizon: Ransomed.vc Ransomware Group Spotted in the Wild [Update] November 9, 2023: “End of an Era, the Sinking of Ransomed.VC” [Update] October 5, 2023: See the subheading: “RansomedVC De-ano...

Dark Web Sales: Anti Red Page Service, France Phone Database, Leads fo...
Dark Web Sales: Anti Red Page Service, France Phone Database, Leads for Payment Processor The SOCRadar Dark Web Team continuously monitors the hidden corners of the dark web to uncover new incidents t...

Mastering the Art of Monitoring the Dark Web for CISOs: Tips and Trick...
Mastering the Art of Monitoring the Dark Web for CISOs: Tips and Tricks In the ever-evolving landscape of cybersecurity, Dark Web monitoring has emerged as a significant area of concern for Chief Info...

Telegram Channels Unveiled: The Hidden Dangers Lurking in Shared Files
Telegram Channels Unveiled: The Hidden Dangers Lurking in Shared Files In today’s interconnected world, cyberspace has become a breeding ground for legitimate and malicious activities; Telegram, a pop...

Dark Web Profile: Bjorka
Dark Web Profile: Bjorka In the ever-evolving landscape of cyber threats, understanding the profiles of individual threat actors is crucial for both governments and private organizations to take actio...

SMS Bomber: How Dangerous Can a Text Be?
SMS Bomber: How Dangerous Can a Text Be? Among the ever-evolving threats in the world of cybersecurity, SMS Bomber attacks are emerging as a modern danger that can have significant and disturbing cons...

Top 5 Dark Web Search Engines
Top 5 Dark Web Search Engines For the latest version check Top 10 Dark Web Search Engines in 2025. Shadowy depths of the internet, where anonymity reigns, and curiosity intertwines with caution. In th...

Evil-GPT Sale, Paramount Plus and Casio Data Leak & Unauthorized A...
Evil-GPT Sale, Paramount Plus and Casio Data Leak & Unauthorized Access Sales The SOCRadar Dark Web Team continuously uncovers incidents that endanger various entities by monitoring the hidden rec...
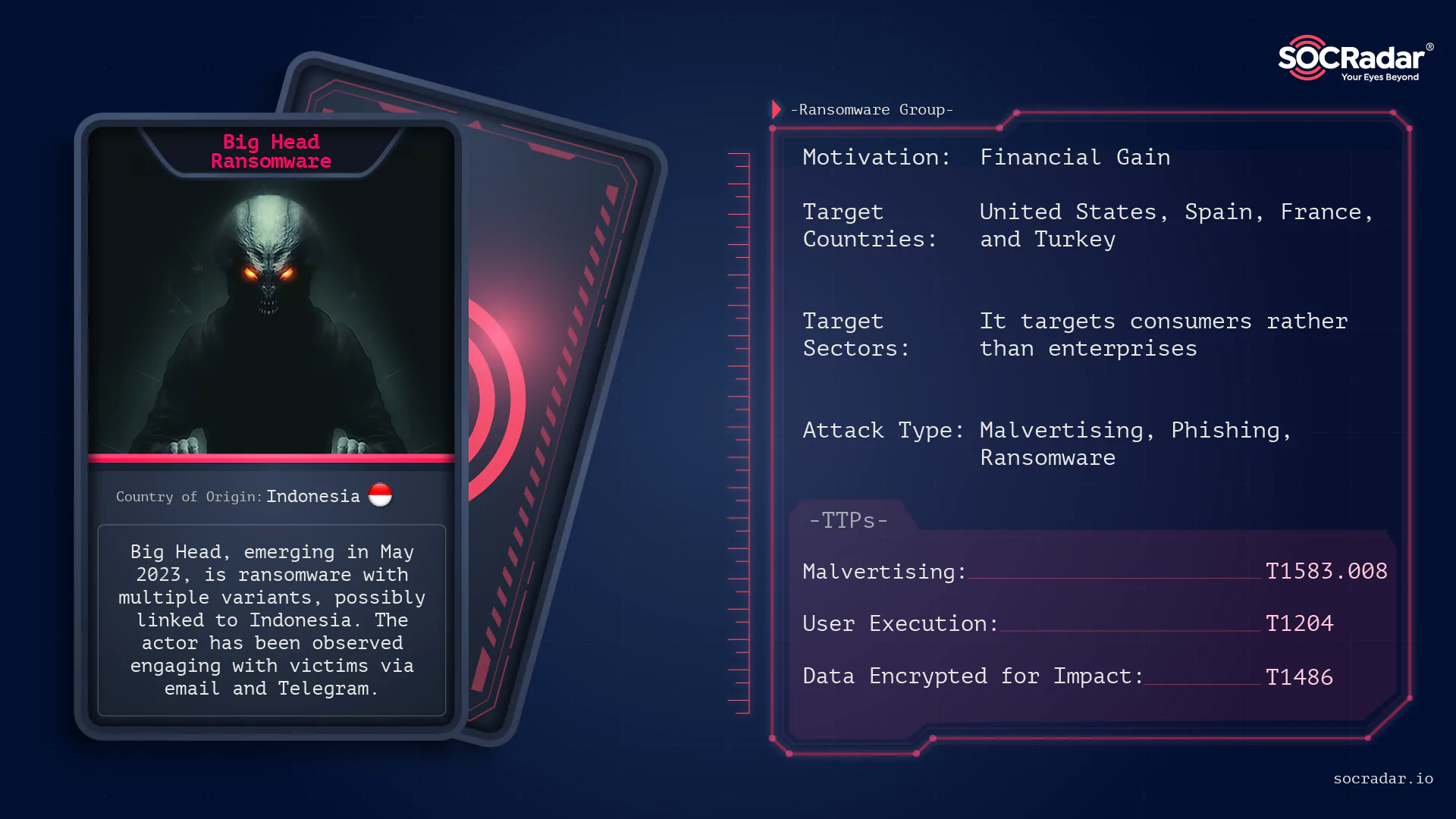
Dark Web Profile: Big Head Ransomware
Dark Web Profile: Big Head Ransomware While ransomware groups such as ALPHV and Lockbit 3.0 continue to hit big companies and make headlines with the large-sized files they steal, there are also actor...































