
How to Detect Reconnaissance Using MITRE ATT&CK Framework
How to Detect Reconnaissance Using MITRE ATT&CK Framework In this article, we will look at the reconnaissance techniques from the MITRE ATT&CK framework’s point of view and discuss how to dete...

Top 5 Free Attack Surface Management Tools
Top 5 Free Attack Surface Management Tools Attack surface management is the continual identification, monitoring, assessment, prioritizing, and remediation of attack vectors within an organization’s I...

What is Domain Hijacking and How to Prevent
What is Domain Hijacking and How to Prevent Domain hijacking attacks can have many damaging consequences, such as the exposure of sensitive data and financial and reputational damage to organizations....

Top 5 Tools for Phishing Domain Detection
Top 5 Tools for Phishing Domain Detection Phishing attacks have victimized many users and companies for years, and it seems they will continue to do so. Many security measures have been taken against ...

What is Deep Web Monitoring?
What is Deep Web Monitoring? There are a variety of network monitoring and perimeter protection solutions available for both personal and commercial networks. Nevertheless, even the most protected bus...

What is BEC Attack and How to Prevent it?
What is BEC Attack and How to Prevent it? BEC attack is a type of social engineering attack that takes place over email and the attacker aims for financial gain. Often, attackers aim to trick employee...

What is Spoofing Attack and How to Prevent It?
What is Spoofing Attack and How to Prevent It? In the context of cybersecurity, spoofing is the act of impersonating another entity to earn our trust, obtain access to our systems, steal data, steal m...
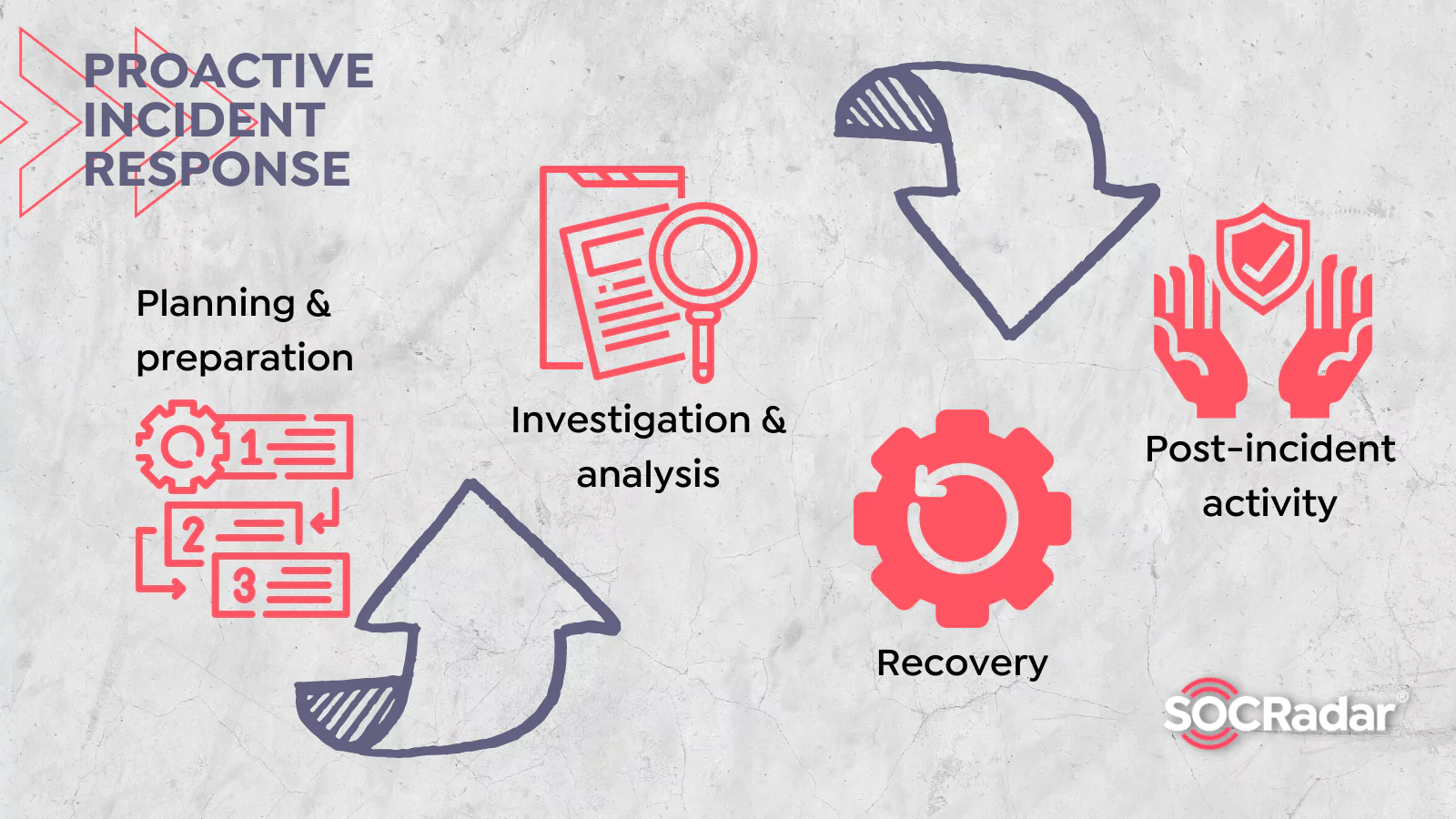
How to Build a Proactive Incident Response Plan?
How to Build a Proactive Incident Response Plan? Some standard cybersecurity measures are endpoint security tools, such as VPNs, proxies, antimalware, and employee cybersecurity awareness training. De...

Cyber Kill Chain Model in Cyber Threat Intelligence
Cyber Kill Chain Model in Cyber Threat Intelligence Cybersecurity helps to reduce the risk of cyber-attacks and to eliminate the risks. Finding out the best solution to prevent the attacks i...

Expectations of SOC Team from CTI
Expectations of SOC Team from CTI Every company with an online component to its business needs cyber awareness; it also requires a Security Operations Center (SOC) if the online part is big enough. A ...

7 Books Every CISO Bookshelf Should Have
7 Books Every CISO Bookshelf Should Have The position of Chief Information Security Officer (CISO) is relatively new and has just received recognition from the CxO community and board of directors at ...

10 Best SIEM Tools, Products & Providers List
10 Best SIEM Tools, Products & Providers List SIEM solutions are vital to log management and complete security. Here is a list of the finest SIEM tools for organizations wanting to add or improve ...

Top 5 Phishing Resources for SOC Teams
Top 5 Phishing Resources for SOC Teams Phishing is a cyber-attack in which attackers defraud their victims through email, text messaging, phone calls, or websites. Attackers redirect their victims to ...

Top 5 Tactics Threat Actors Use for Initial Access
Top 5 Tactics Threat Actors Use for Initial Access A short while ago, combined security advice released by several national cybersecurity agencies highlighted the top ten attack vectors most used by t...

What are DevOps, DevSecOps, and Rugged DevOps?
What are DevOps, DevSecOps, and Rugged DevOps? We are hearing these two buzzwords, DevSecOps and DevOps, more frequently. For example, Gartner predicts DevSecOps will reach mainstream adoption within ...

What is Network Performance Monitoring (NPM)?
What is Network Performance Monitoring (NPM)? Network Performance Monitoring (NPM) is assessing the service quality of a network as experienced by users by measuring, visualizing, monitoring, diagnosi...

How to Protect Yourself Against Shodan, BinaryEdge and ZoomEye?
How to Protect Yourself Against Shodan, BinaryEdge and ZoomEye? Have you ever wondered how hackers find the IPs, ports, and services required for their attacks? Some attacks need thousands of host co...

What Do You Need to Know About New SAMA Principles?
What Do You Need to Know About New SAMA Principles? The Kingdom of Saudi Arabia (KSA) has launched a digital transformation program focusing on the banking industry. With the growing digitization of f...

Top 10 Cybersecurity Events You Must Follow
Top 10 Cybersecurity Events You Must Follow Whether you work at a startup or in the information security department of a well-established company, you need to attend cybersecurity events to meet with ...

What are Threat Hunting Tools?
What are Threat Hunting Tools? Threat hunting is how computer security specialists aggressively seek out and eliminate cyber dangers that have infiltrated their computer network invisibly. Threat hunt...
































