
Verizon 2022 DBIR: All Sizes of Businesses Suffer from Ransomware
Verizon 2022 DBIR: All Sizes of Businesses Suffer from Ransomware Verizon has released the 15th Data Breach Investigations Report (DBIR), an in-depth analysis of trends in cyberattacks and data breach...

Stop BEC Attacks with SOCRadar Takedown Processes
Stop BEC Attacks with SOCRadar Takedown Processes Attacks such as phishing, business e-mail compromise (BEC), and malware infection, which are among the fraud activities, increasingly pose a serious t...

Attack Surface Management (ASM) in 10 Questions
Attack Surface Management (ASM) in 10 Questions The rise of working from home and access to cloud services and the expansion of businesses have increased attack surfaces. The attack surface ...

Top 10 Twitter Accounts to Follow for Threat Intelligence
Top 10 Twitter Accounts to Follow for Threat Intelligence Threat intelligence feeds on such a broad spectrum that sometimes you’d be surprised to hear where you can get relevant information. Oft...

New Playground for Fraudsters: How Do I Get WhatsApp Scam IoCs?
New Playground for Fraudsters: How Do I Get WhatsApp Scam IoCs? SOCRadar analysts, while investigating phishing attacks via WhatsApp, recently found a significant increase in an attack with the same t...

Common IoT Attacks that Compromise Security
Common IoT Attacks that Compromise Security With the development of technology, nowadays, we can connect various everyday devices, such as cars, kitchen appliances, TV, to the internet, or other wirel...
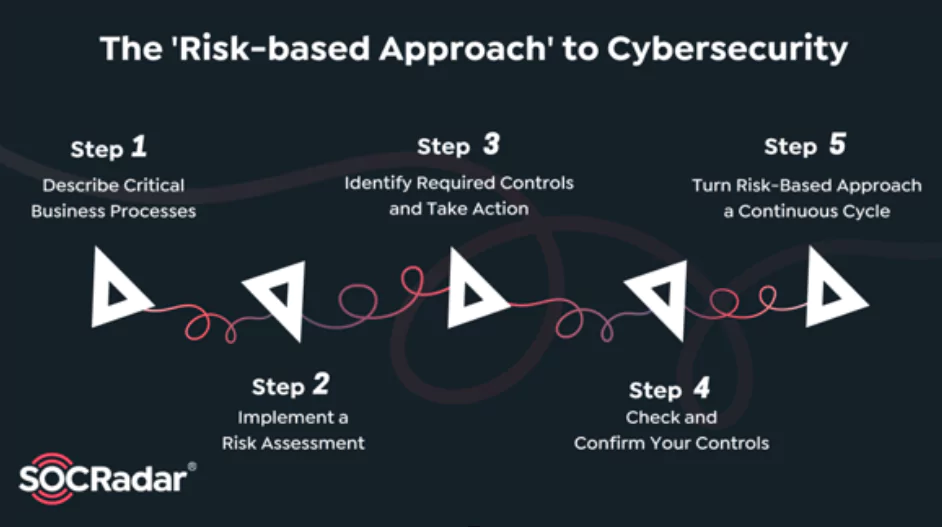
What is the Risk-Based Approach to Cybersecurity?
What is the Risk-Based Approach to Cybersecurity? Cybersecurity is one of the main topics for business managers in today’s world. The approach to cyber risks has changed from “maturity bas...

What are the Top Ten Data Breaches of All Times?
What are the Top Ten Data Breaches of All Times? In the cyber world that grows and develops with cumulative data accumulation, “small” and short-term data breaches that we think we can ignore from tim...

What are STIX/TAXII?
What are STIX/TAXII? The industry standard for sharing threat intelligence, STIX/TAXII is a great starting point for anyone new to threat intelligence. Technically speaking, STIX and TAXII a...

Real-Life Examples of Machine Learning in Cybersecurity
Real-Life Examples of Machine Learning in Cybersecurity ...

Behind the Experts’ Perspective: Ethical Issues Behind Cybersecurity
Behind the Experts’ Perspective: Ethical Issues Behind Cybersecurity Since the beginning of internet history, hackers have sought to exploit it for various purposes, ranging from pranks to theft and e...

How to Use SOCRadar Integrations?
How to Use SOCRadar Integrations? SOCRadar provides integrations with product groups such as SIEM, SOAR, EDR, firewalls, Threat Intelligence Platforms, Vulnerability Management, Ticketing, and Team Me...

Comparing Benefits from Different Security Monitoring Services
Comparing Benefits from Different Security Monitoring Services By 2021, it is estimated that the total cost of cybercrime was 6 trillion USD making threat actors the third-largest economy after the U....

What Do You Need To Know About Cybersecurity in Power Grids
What Do You Need To Know About Cybersecurity in Power Grids Cyberattacks on the electrical power system are becoming as disruptive as natural disasters, and the danger is growing as power grids become...

20 SOCRadar Notifications That Will Make You Feel Safer
20 SOCRadar Notifications That Will Make You Feel Safer SOCRadar presents its detections through the alarm mechanism and adds new alarms to the system every day to provide safer conditions. In additio...

What are the Biggest Cybersecurity Risks in North America?
What are the Biggest Cybersecurity Risks in North America? The ongoing Russian invasion attempt of Ukraine has changed priorities on the global cyberattack surface. Experts talk about the necessity of...

Microsoft Exchange Server Cyberattack Timeline
Microsoft Exchange Server Cyberattack Timeline Microsoft Exchange Server is a mail calendaring server developed by Microsoft. Microsoft Exchange is considered an essential goal for hackers to control ...

5 Things You Should Know About the Genesis Marketplace
5 Things You Should Know About the Genesis Marketplace [April 5, 2023] Update: Law enforcement has seized the Genesis Market domains. The FBI has taken down the domains for the major marketplace Genes...

What is Extended Threat Intelligence (XTI) and How Does it Make a Diff...
What is Extended Threat Intelligence (XTI) and How Does it Make a Difference? Every day we hear news about industries negatively impacted by cyberattacks. It seems that conventional threat intell...

What Do You Need To Know About Vulnerability Intelligence
What Do You Need To Know About Vulnerability Intelligence A vulnerability is a weakness in computer software or hardware that allows an attacker to gain access to higher privilege levels. This could l...
































