
Cactus Ransomware Employs Unique Encryption Techniques to Avoid Detect...
Cactus Ransomware Employs Unique Encryption Techniques to Avoid Detection Researchers discovered a new ransomware group called Cactus, operating since at least March 2023. Cactus steals data and ...

Top 7 Must-watch Talks at RSA Conference 2023
Top 7 Must-watch Talks at RSA Conference 2023 The RSA Conference 2023 is set to be one of the biggest and most exciting cybersecurity events of the year. With over 500 sessions scheduled, attendees wi...

Cyber Attackers Continue Threatening Education and Healthcare Organiza...
Cyber Attackers Continue Threatening Education and Healthcare Organizations The recent cyber attacks on Bluefield University and University Urology highlight the increasing risk of...

The .bank TLD: Benefits and Downsides
The .bank TLD: Benefits and Downsides The world has changed rapidly since the invention of the Internet. One of the most important aspects it affected is using the Internet for banking. According to&n...

Sandworm Attackers Use WinRAR to Wipe Data from Government Devices
Sandworm Attackers Use WinRAR to Wipe Data from Government Devices Sandworm (UAC-0165), a Russian hacking group, has been linked to an attack on Ukrainian state networks that involved wiping data from...

GoAnywhere MFT Vulnerability Contributes to 91% Increase in Ransomware...
GoAnywhere MFT Vulnerability Contributes to 91% Increase in Ransomware Attacks [May 4, 2023] Update: Brightline, a mental health provider, was among the organizations targeted by the Clop ransomware g...

LOBSHOT hVNC Malware: A New Threat Distributed Through Google Ads
LOBSHOT hVNC Malware: A New Threat Distributed Through Google Ads Cybersecurity researchers have discovered a new malware, called ‘LOBSHOT,’ distributed through Google ads. This malware al...
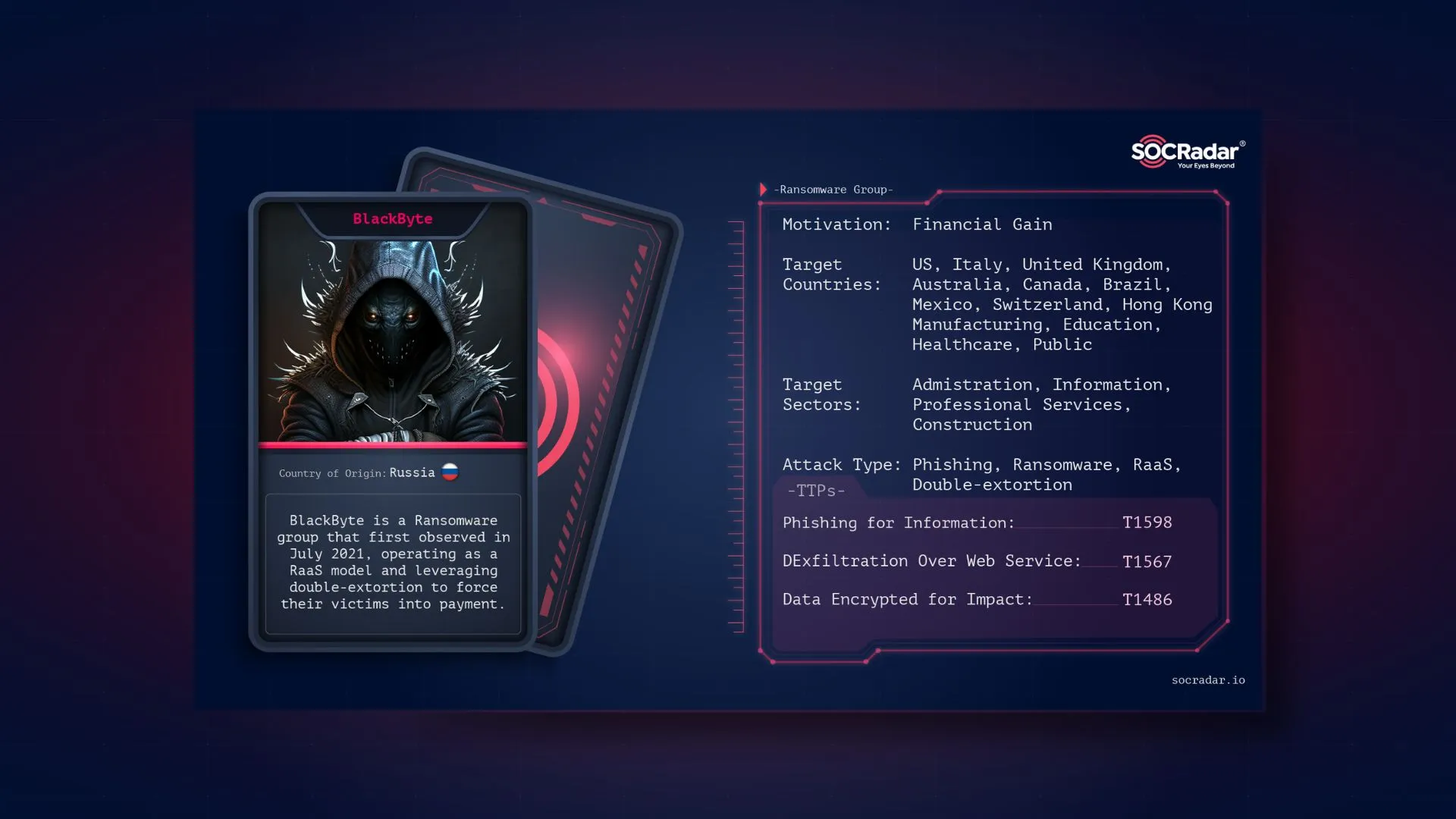
Dark Web Profile: BlackByte Ransomware
Dark Web Profile: BlackByte Ransomware Ransomware has been one of the most glaring threats against organizations in recent years. Since 2021 SOCRadar has detected around 5,600 ransomware attacks. Ther...

SOCRadar Technical Whitepaper: ‘Snapshot of 70 Million Stealer...
SOCRadar Technical Whitepaper: ‘Snapshot of 70 Million Stealer Logs’ SOCRadar’s first technical white paper is out! Here are some highlights: Threat actors created fake data to increase the num...

Global Malverposting Campaign Infecting Over 500,000 Devices
Global Malverposting Campaign Infecting Over 500,000 Devices A global malverposting campaign that has been ongoing for the past three months has been traced back to a Vietnamese threat actor...

Salesforce Credentials Leak, Admin, and Webshell Access Sales, Partner...
Salesforce Credentials Leak, Admin, and Webshell Access Sales, Partnership Announcements We are experiencing a period in which threat actors are increasingly outsourcing and growing the cybercrime net...

An Inherent Weakness: Critical Infrastructures in Gulf Countries
An Inherent Weakness: Critical Infrastructures in Gulf Countries One of the most devastating cyberattacks on critical infrastructure was the Colonial Pipeline attack in the United States in May 2021. ...

Active Exploitation of Serious Vulnerabilities in PaperCut, Veeam, and...
Active Exploitation of Serious Vulnerabilities in PaperCut, Veeam, and TP-Link [Update] July 11, 2024: “EstateRansomware Exploits CVE-2023-27532 in Veeam Systems” [Update] April 18, 2024:...
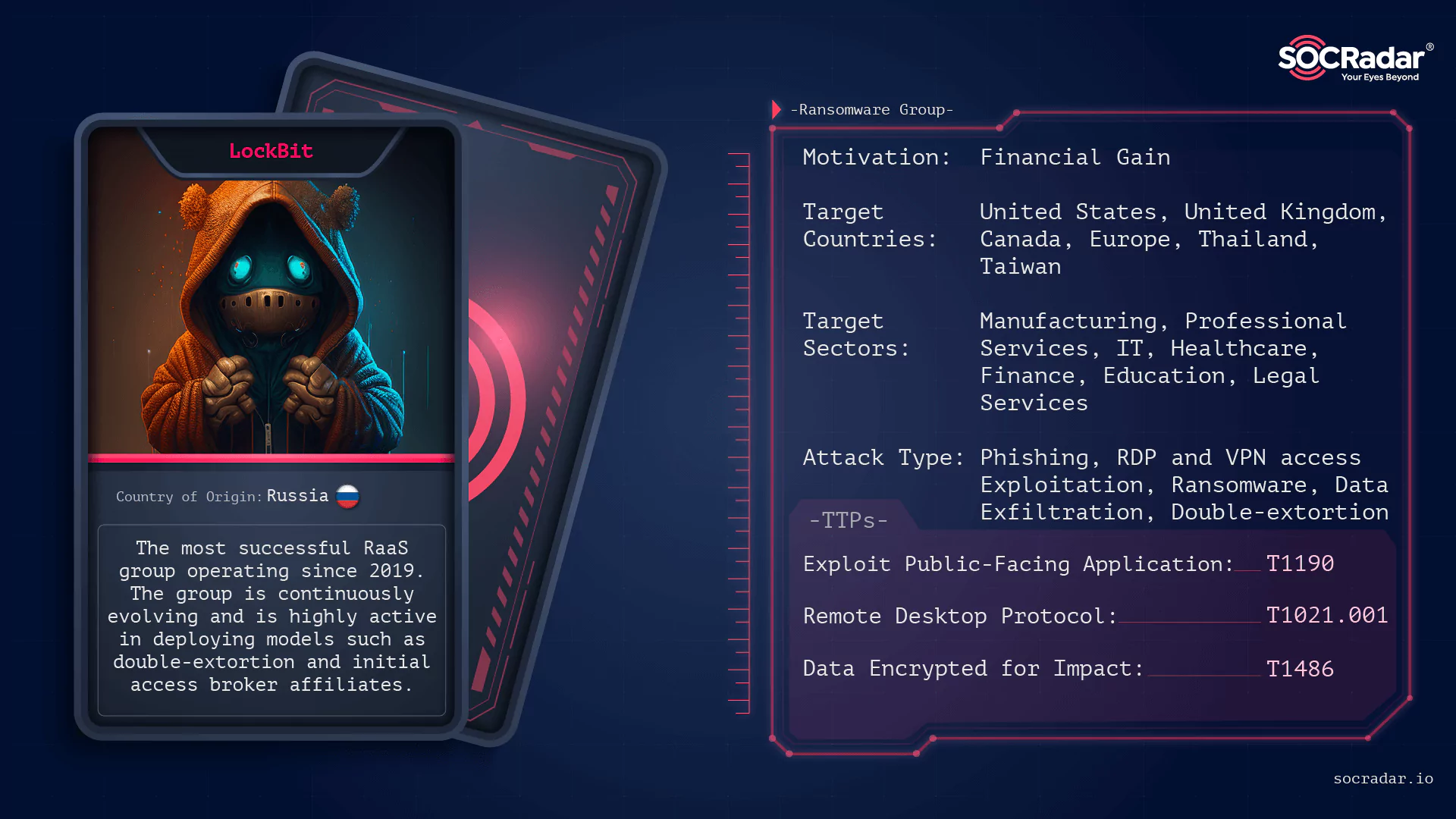
Dark Web Profile: LockBit 3.0 Ransomware
Dark Web Profile: LockBit 3.0 Ransomware [Update] August 31, 2023: See the subheading: “LockBit’s Operational Struggles, Empty Threats, and Sudden Surge.” [Update] July 03, 2023: LockBit claimed to h...

Apache Superset Default Configuration Vulnerability Could Lead to RCE
Apache Superset Default Configuration Vulnerability Could Lead to RCE [Update] January 9, 2024: “CISA Added Apache Superset Vulnerability (CVE-2023-27524) to the Known Exploited Vulnerabilities (KEV)...

AI vs. AI: Future of the Cybersecurity Battles
AI vs. AI: Future of the Cybersecurity Battles Attacks and security solutions tailored with the help of artificial intelligence (AI) have become a trending subject in the security industry as AI bots ...

Severe SLP Vulnerability Could Lead to Large DDoS Amplification Attack...
Severe SLP Vulnerability Could Lead to Large DDoS Amplification Attacks A new high-severity vulnerability was discovered, affecting Service Location Protocol (SLP). The vulnerability could allow ...

PyPI Packages Found Distributing Payloads in WhiteSnake Malware Campai...
PyPI Packages Found Distributing Payloads in WhiteSnake Malware Campaign Security researchers recently uncovered a new malware payload in the PyPI repository for Python packages. The payload...

AWS S3 Bucket Takeover Vulnerability: Risks, Consequences, and Detecti...
AWS S3 Bucket Takeover Vulnerability: Risks, Consequences, and Detection As the amount of data companies possesses grow, their costs can be optimized more efficiently. Thanks to the emergence of stora...

New Victims of BlackCat and LockBit, Gentex Data Breach, and Education...
New Victims of BlackCat and LockBit, Gentex Data Breach, and Education Institution Access Sales Powered by DarkMirror™ Ransomware is on the headlines again in SOCRadar’s weekly dark web summary....

































