
LockBit’s New Regulations Sets Minimum For Ransom Demands
LockBit’s New Regulations Sets Minimum For Ransom Demands Recently, the notorious LockBit ransomware group has initiated a significant discussion among its affiliates regarding potential cha...

Why are Threat Actors Targeting Indonesia?
Why are Threat Actors Targeting Indonesia? On September 3, Indonesia hiked fuel prices by 30%, stating that petrol and diesel prices are still low by world standards, but subsidies are unsustainable. ...

MGM Resorts Hacked by BlackCat Affiliate, ‘Scattered Spider’
MGM Resorts Hacked by BlackCat Affiliate, ‘Scattered Spider’ [Update] January 31, 2025: “Preliminary Approval of $45 Million Settlement in MGM Data Breach Class Action” A cybercriminal gang employing ...

Overview of TIBER-EU From Threat Intelligence Perspective
Overview of TIBER-EU From Threat Intelligence Perspective Financial institutions are crucial for the global economy. They hold trillions of dollars in assets and billions of customer records. As such,...

LockBit Attack Fails, 3AM Ransomware Steps In as Plan B
LockBit Attack Fails, 3AM Ransomware Steps In as Plan B Researchers have recently identified a new strain of ransomware called 3AM. Their investigation revealed that the first known usage of this rans...
Top 10 Facts About MOVEit Breach
Top 10 Facts About MOVEit Breach In the ever-evolving cybersecurity landscape, breaches have become all too common, sending shockwaves through industries and leaving organizations scrambling to recove...

September 2023 Patch Tuesday by Microsoft Fixes Five Critical, Two Zer...
September 2023 Patch Tuesday by Microsoft Fixes Five Critical, Two Zero-Day Vulnerabilities [Update] September 15, 2023: See the subheading: “Proof-of-Concept (PoC) Exploit Available for CVE-2023-3814...

Mother of the Threats: Threat as a Service
Mother of the Threats: Threat as a Service Anonymous Russia’s botnet service Tesla-bot announced a new malicious service model on its Telegram channel. This new type of service and concept, whic...

Cisco Zero-Day Vulnerability Exploited by LockBit and Akira (CVE-2023-...
Cisco Zero-Day Vulnerability Exploited by LockBit and Akira (CVE-2023-20269) Cisco recently issued an advisory regarding a zero-day vulnerability, CVE-2023-20269, in its Adaptive Security Appliance (A...

Cobalt Strike Leak, Sales of Unauthorized Access and Credit Card Data
Cobalt Strike Leak, Sales of Unauthorized Access and Credit Card Data The SOCRadar Dark Web Team conducts continuous monitoring of the dark web, uncovering the latest threats that require your attenti...

Telegram Hit by a DDoS Attack: What Is the Cause Behind It?
Telegram Hit by a DDoS Attack: What Is the Cause Behind It? In a recent update, a well-known and notorious threat actor declared their targeting of Telegram. This group initiated the attack after Tele...

Major Cyberattacks in Review: August 2023
Major Cyberattacks in Review: August 2023 August 2023 has not passed without its share of significant cyberattacks. Among the incidents of last month, we have observed multiple data breaches involving...

‘Classified’ Intel on the ‘Public’ Telegram Channel: Pentagon US Leak...
‘Classified’ Intel on the ‘Public’ Telegram Channel: Pentagon US Leak In the rapidly evolving landscape of digital communication, Telegram has emerged as a prominent platform for various user groups f...

Microsoft Reveals How Storm-0558 Acquired the Signing Key: They Stole ...
Microsoft Reveals How Storm-0558 Acquired the Signing Key: They Stole From a Crash Dump Microsoft previously disclosed the successful thwarting of an attack orchestrated by Storm-0558, a threat actor ...

Main Analytical Frameworks for Cyber Threat Intelligence
Main Analytical Frameworks for Cyber Threat Intelligence Threat intelligence is a cyber-security discipline focusing on detailed knowledge about the cyber threats targeting an organization. Threat Int...

ASUS Routers Under Risk of RCE Attacks: Critical Vulnerabilities Found...
ASUS Routers Under Risk of RCE Attacks: Critical Vulnerabilities Found (CVE-2023-39238, CVE-2023-39239, CVE-2023-39240) Security researchers have recently unearthed three security vulnerabilities affe...
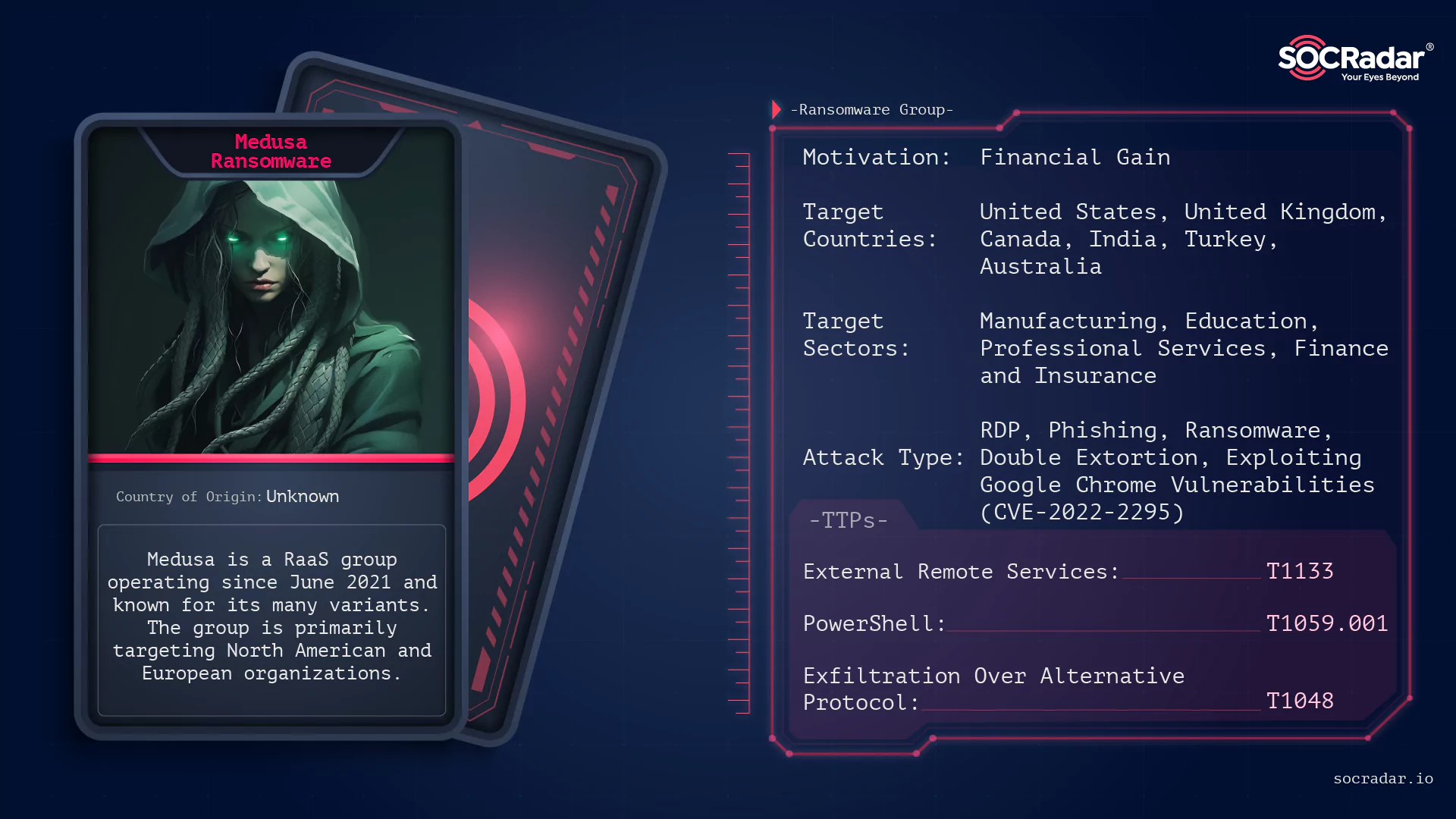
Dark Web Profile: Medusa Ransomware (MedusaLocker)
Dark Web Profile: Medusa Ransomware (MedusaLocker) [Update] March 13, 2025: CISA, FBI, and MS-ISAC Warn of Medusa Ransomware Threats in New Advisory In ancient Greek mythology, Medusa stands as one of...

Sales of International IDs, UK Bank Leads, Fully Undetectable Crypter,...
Sales of International IDs, UK Bank Leads, Fully Undetectable Crypter, US Instagram Database Leak Introducing our weekly Dark Web digest, where we explore the most recent occurrences in the online und...

Threat Actors Accessed UK Military Data From Weakest Link
Threat Actors Accessed UK Military Data From Weakest Link On the 13th of August, The LockBit Ransomware group added a new victim to its list. The victim supplier, manufacturing company Zaun, expressed...

MalDoc in PDF: A Novel Method to Distribute Malicious Macros
MalDoc in PDF: A Novel Method to Distribute Malicious Macros Since Microsoft disabled Macros by default, threat actors have actively experimented with alternative attack methods. They utilize various ...
































