
How to Protect Yourself Against Shodan, BinaryEdge and ZoomEye?
How to Protect Yourself Against Shodan, BinaryEdge and ZoomEye? Have you ever wondered how hackers find the IPs, ports, and services required for their attacks? Some attacks need thousands of host co...

Dark Web Profile: Netwalker Ransomware
Dark Web Profile: Netwalker Ransomware Today, with the effects of digitalization, most of the information is stored online. This situation creates a vulnerability for organizations because the number ...

NTLM Relay Attack Leads to Windows Domain Takeover
NTLM Relay Attack Leads to Windows Domain Takeover A new DFSCoerce NTLM Relay attack has been discovered on Windows. Threat actors can take over Microsoft Active Directory Certificate Services (AD CS)...

SOCRadar Exhibiting Extended Threat Intelligence Solution at InfoSecur...
SOCRadar Exhibiting Extended Threat Intelligence Solution at InfoSecurity Europe 2022 SOCRadar will be at InfoSecurity Europe, held at London ExCel this week from 21 to 23 June. We are very excited to...

BRATA Malware Becomes an Advanced Threat
BRATA Malware Becomes an Advanced Threat Originally a banking trojan, BRATA acquires new capabilities and becomes a more advanced threat. Malware can now be much more effective at stealing user i...

DriftingCloud APT Group Exploits Zero-Day In Sophos Firewall
DriftingCloud APT Group Exploits Zero-Day In Sophos Firewall Cybersecurity researchers have revealed that Sophos Firewall has been actively exploited by DriftingCloud APT group since early March. Appa...

Cisco Fixed Critical Authentication Bypass Vulnerability Affecting Som...
Cisco Fixed Critical Authentication Bypass Vulnerability Affecting Some Products Cisco fixed a vulnerability discovered in the external authentication functionality of Secure Email and Web Manager. Th...

Microsoft June 2022 Patch Tuesday Fixes 55 Vulnerabilities Including F...
Microsoft June 2022 Patch Tuesday Fixes 55 Vulnerabilities Including Follina Microsoft has released the June 2022 Patch Tuesday. The company announced that it had patched 55 vulnerabilities, including...

Almost Impossible to Detect Symbiote Linux Malware
Almost Impossible to Detect Symbiote Linux Malware The newly discovered Linux malware Symbiote can easily infect and hide in almost any process on compromised systems. The malware steals account ...

What Do You Need to Know About New SAMA Principles?
What Do You Need to Know About New SAMA Principles? The Kingdom of Saudi Arabia (KSA) has launched a digital transformation program focusing on the banking industry. With the growing digitization of f...

Ransomware Groups Target VMware and QNAP Products
Ransomware Groups Target VMware and QNAP Products Linux-based Black Basta ransomware targets VMware ESXi virtual machines, while DeadBolt ransomware targets QNAP NAS (network-attached storage) product...

Top 10 Cybersecurity Events You Must Follow
Top 10 Cybersecurity Events You Must Follow Whether you work at a startup or in the information security department of a well-established company, you need to attend cybersecurity events to meet with ...

Mandiant Leak Alleged: A PR Trial?
Mandiant Leak Alleged: A PR Trial? LockBit ransomware gang claimed that they had stolen Mandiant’s data. The gang posted a countdown on their data leak site earlier today. They c...

What Do You Need To Know About Atlassian Confluence RCE Vulnerability?...
What Do You Need To Know About Atlassian Confluence RCE Vulnerability? After it was disclosed that the RCE vulnerability with the code CVE-2022-26134, which affects Atlassian Confluence and Data Cent...

What are Threat Hunting Tools?
What are Threat Hunting Tools? Threat hunting is how computer security specialists aggressively seek out and eliminate cyber dangers that have infiltrated their computer network invisibly. Threat hunt...

Verizon 2022 DBIR: All Sizes of Businesses Suffer from Ransomware
Verizon 2022 DBIR: All Sizes of Businesses Suffer from Ransomware Verizon has released the 15th Data Breach Investigations Report (DBIR), an in-depth analysis of trends in cyberattacks and data breach...
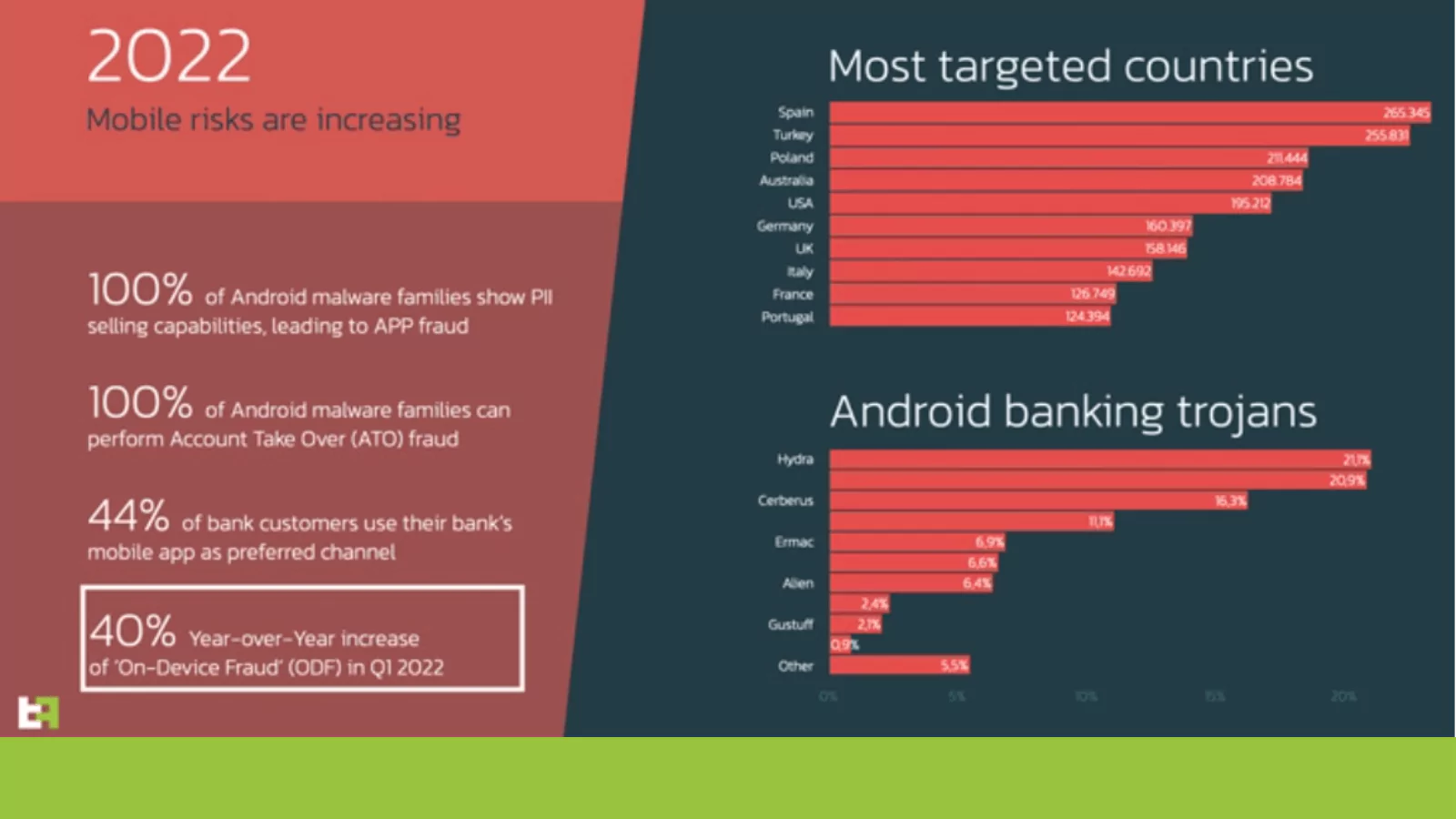
On-Device Fraud Trend in Mobile Malware Campaigns
On-Device Fraud Trend in Mobile Malware Campaigns According to the 2022 mobile threat landscape analysis published byThreatFabric, ODF (on-device fraud) banking trojans targeting A...

Workarounds for Microsoft Office Zero-Day RCE Vulnerability "Follina" ...
Workarounds for Microsoft Office Zero-Day RCE Vulnerability “Follina” has Released The Follina zero-day vulnerability in Microsoft Office allows threat actors to perform remote code e...

GitHub Announces 100,000 npm Users' Credentials Stolen
GitHub Announces 100,000 npm Users’ Credentials Stolen GitHub has announced that 100,000 npm user information was stolen through OAuth tokens linked to Heroku and Travis CI. It was previously&nb...

Deep Web Profile: REvil
Deep Web Profile: REvil REvil is a ransomware hacking group, as its name suggests -REvil = “ransomware” + “evil”-. This ransomware group is thought to be centered in Russia. It is also named “Sodinoki...
































