RE#TURGENCE: A Deep Dive into Turkish Hackers’ Campaign Targeting MSSQ...
RE#TURGENCE: A Deep Dive into Turkish Hackers’ Campaign Targeting MSSQL Servers Financially motivated Turkish threat actors have emerged with a significant development in cyber threats, introducing a ...

A for APT: Criteria for Classifying Cyber Threats
A for APT: Criteria for Classifying Cyber Threats The term “Advanced Persistent Threat” (APT) has emerged as a critical concept, necessitating a nuanced understanding and accurate classification. APTs...

EU & US Credit Cards, 750M Indian Mobile Data at Risk; Subway Hit by L...
EU & US Credit Cards, 750M Indian Mobile Data at Risk; Subway Hit by LockBit The SOCRadar Dark Web Team identified critical incidents in the cyber threat landscape over the last week. These includ...

Russian APT Operation: Star Blizzard
Russian APT Operation: Star Blizzard [Update] January 30, 2024: “Official Attributions of Star Blizzard” Within the continuously changing cyber threat landscape, the strategies of Star Blizzard unfold...

Dark Peep #9: The McFlurry Bandit
Dark Peep #9: The McFlurry Bandit Welcome to “Dark Peep #9.” This edition takes you behind the scenes of the digital world, where every byte tells a story. Here, we uncover the ongoing sagas of cyberc...

Stealer Malware 101: Understanding the Different Variants and Families
Stealer Malware 101: Understanding the Different Variants and Families In the realm of cybersecurity, malicious software (malware) continues to evolve, with various types targeting sensitive data for ...

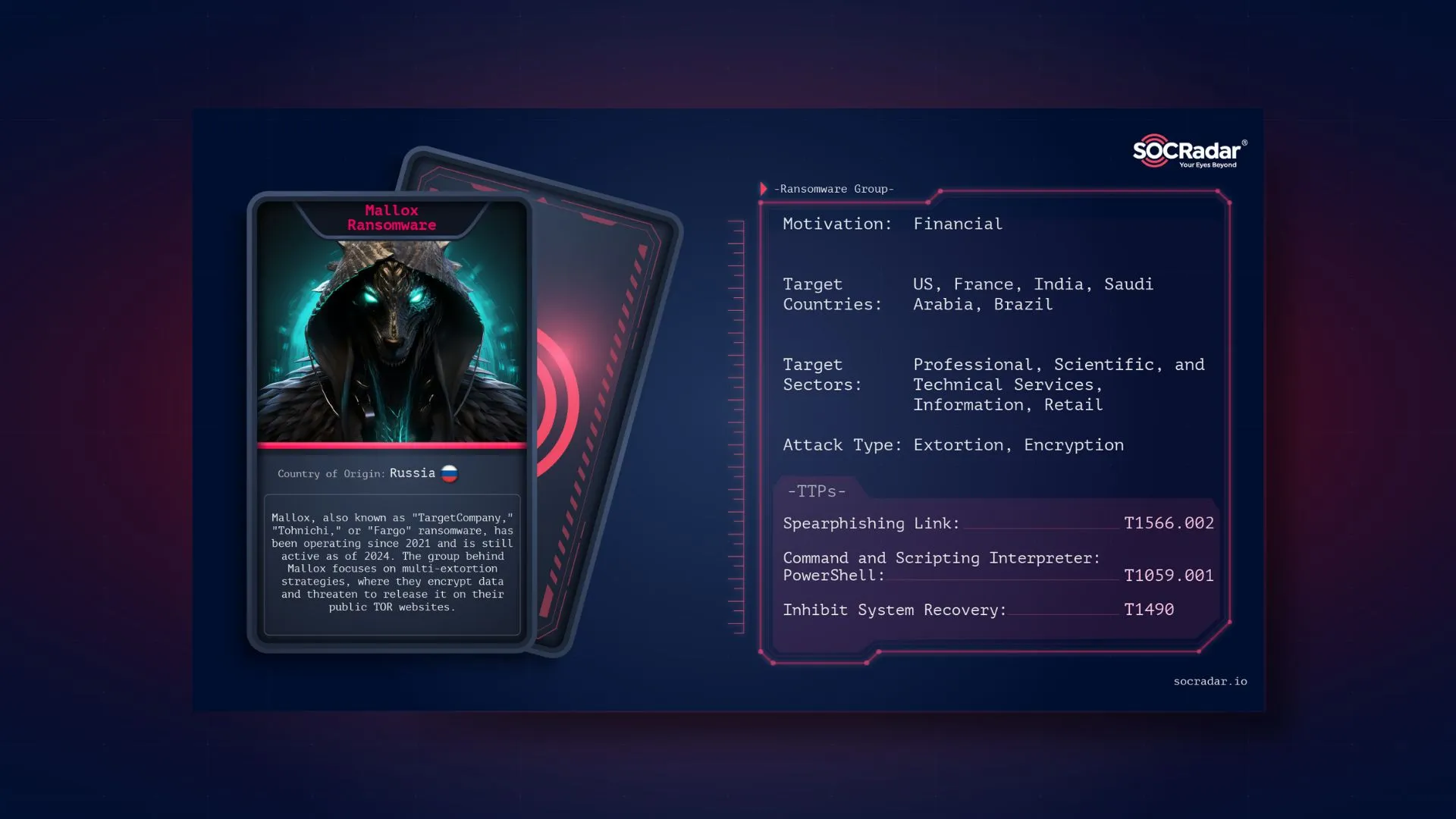
Dark Web Profile: Malek Team
Dark Web Profile: Malek Team In recent months, the Malek Team, a hacker group with alleged links to Iran, has escalated its cyber offensive against key Israeli institutions, marking a significant upti...
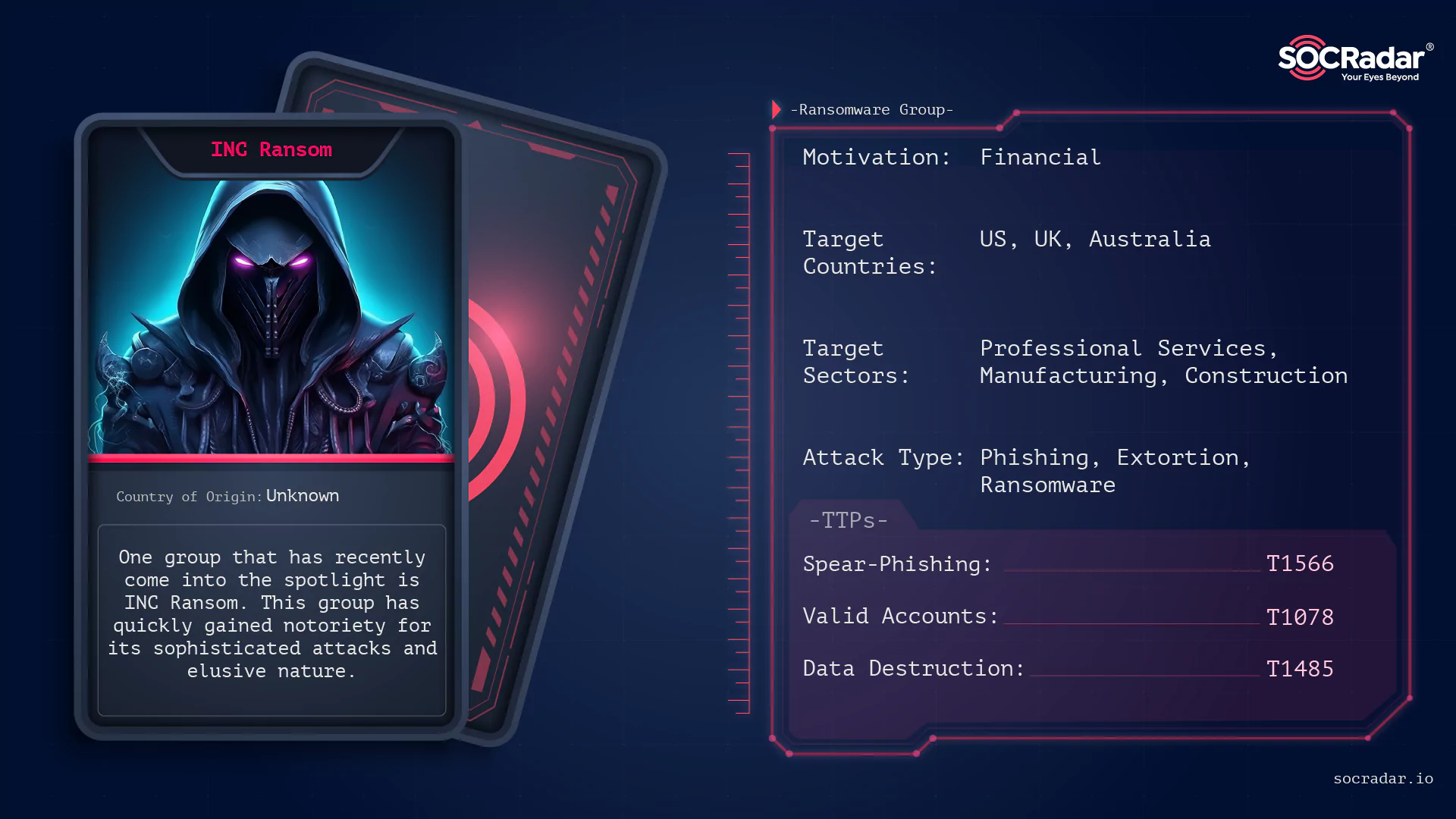
Dark Web Profile: INC Ransom
Dark Web Profile: INC Ransom The digital world is constantly under the threat of cyber attacks, and the emergence of new ransomware groups only intensifies this peril. One such group that has recently...

Dark Web Profile: WereWolves Ransomware
Dark Web Profile: WereWolves Ransomware Emerging as a new group in the cybercrime landscape, this Russian-speaking group, WereWolves Ransomware, has gained notoriety recently for its rapid emergence l...

Sales of Trello Database, Ivanti Zero-Day Exploits, Phantom Loader, US...
Sales of Trello Database, Ivanti Zero-Day Exploits, Phantom Loader, US and Australia Credit Cards In SOCRadar Dark Web Team’s latest findings, from their week-long monitoring of the dark web, an unaut...

Dark Web Profile: Scattered Spider
Dark Web Profile: Scattered Spider One hacker collective continues to confound federal law enforcement and cybersecurity experts — the Scattered Spider. Known by a multitude of aliases such as Muddled...

Dark Peep #8: Pirouetting in the Shadows
Dark Peep #8: Pirouetting in the Shadows In the sprawling digital metropolis, where neon lights cast long shadows and data streams flow like rivers through the cybernetic landscape, a new saga unfolds...

Digital Predators of 2023: Exposing Top Cyber Threat Actors
Digital Predators of 2023: Exposing Top Cyber Threat Actors In 2023, the digital landscape continued to evolve rapidly, but so did the sophistication and audacity of cyber threat actors. From ransomwa...

Dark Web Sales: A New RCE Exploit, US Credit Cards, and 19M Japanese E...
Dark Web Sales: A New RCE Exploit, US Credit Cards, and 19M Japanese Emails In recent discoveries within the cyber threat landscape, the SOCRadar Dark Web Team has identified the sale of access to a c...

Beyond Hacktivism: Deanon Club, KillNet, and the Russian Dark Web Mark...
Beyond Hacktivism: Deanon Club, KillNet, and the Russian Dark Web Market Wars In recent years, the Russian Dark Web has become a fierce battleground, particularly following the shutdown of Hydra, the ...

Mastercard Data Leak, New Fully Undetectable Ransomware, Elusive Steal...
Mastercard Data Leak, New Fully Undetectable Ransomware, Elusive Stealer Source Code Leak, and More In recent discoveries across the cyber threat landscape, the SOCRadar Dark Web Team has identifi...

National Credit Union Administration and GTA 5 Leaks, Craxs RAT, New W...
National Credit Union Administration and GTA 5 Leaks, Craxs RAT, New Windows Stealer The SOCRadar Dark Web Team has detected critical events, including the alleged Grand Theft Auto V source code leak ...

Dark Web Profile: Cactus Ransomware
Dark Web Profile: Cactus Ransomware A new plant has grown in the desert of cyber threats, wielding its thorns to pierce through organizations and individuals alike. The Cactus Ransomware Group, a name...

Operation Triangulation: ‘’Most Sophisticated Attack Chain Ever Seen"...
Operation Triangulation: ‘’Most Sophisticated Attack Chain Ever Seen” The cyber security landscape has recently been abuzz with discussions about Operation Triangulation, a sophisticated and mul...

Excel's Blind Spot: The Strategic Deployment of Agent Tesla Malware by...
Excel’s Blind Spot: The Strategic Deployment of Agent Tesla Malware by Cyberattackers In the ever-evolving landscape of cyber threats, a notable trend has emerged: the exploitation of a longstan...