What is a Security Operations Center (SOC)? (Ultimate Guide)
What is a Security Operations Center (SOC)? (Ultimate Guide) A Security Operation Center (SOC) is a centralized function inside an organization that uses people, processes, and technology to continual...

How Does Cyber Security Support Business Intelligence?
How Does Cyber Security Support Business Intelligence? The second guide that we have prepared for cyber security experts and administrators is about “business intelligence”. Cybercrime has catastrophi...

Using Artificial Intelligence in Cybersecurity (Ultimate Guide)
Using Artificial Intelligence in Cybersecurity (Ultimate Guide) Welcome to the first of our ultimate guides on some topics related to cybersecurity: AI vs. cybersecurity. In these compilations, we wil...

What Do You Need To Know About Cloud Web Application Firewall (WAF)
What Do You Need To Know About Cloud Web Application Firewall (WAF) A cloud Web Application Firewall (WAF) is a security application running on the cloud that tracks the traffic between the user and t...

What is Operational Cyber Threat Intelligence and How to Use It
What is Operational Cyber Threat Intelligence and How to Use It Organizations of all sizes are building security teams to deploy network solutions and address threats. A key component to the success o...

What is Technical Cyber Threat Intelligence and How to Use It
What is Technical Cyber Threat Intelligence and How to Use It As cyber threats become more sophisticated, many organizations pay more attention to their security programs. Organizations of all sizes b...

Quick Facts on the World's Top InfoStealer Malware Threats
Quick Facts on the World’s Top InfoStealer Malware Threats An info stealer is a piece of malicious software (malware) that tries to steal your information. In most cases, this means stealing inf...

What is Vulnerability Management?
What is Vulnerability Management? The increasing number of vulnerabilities that security teams have to deal with makes it impossible to try to remediate all critical vulnerabilities. In fact, a small ...

How Can OSINT Tools be Used and What is External Attack Surface Manage...
How Can OSINT Tools be Used and What is External Attack Surface Management? SOCRadar defines itself as a platform providing an early warning system with extended threat intelligence. In other words, S...

What is Operational Cyber Threat Intelligence?
What is Operational Cyber Threat Intelligence? As cyber threats become more sophisticated, many organizations are paying more attention to their security programs. Organizations of all sizes are build...

What is Tactical Cyber Threat Intelligence and How to Use it
What is Tactical Cyber Threat Intelligence and How to Use it As cyber threats become more complex than ever, many organizations devote more resources to their security programs. Almost every organizat...

Detecting IoT Devices For Your Company
Detecting IoT Devices For Your Company From smart wearables to interconnected industrial devices the IOT is becoming a larger part of our lives since the first coinage of the term in 1999 at a P&G...

Is RDAP (Registration Data Access Protocol) Going to Replace WHOIS?
Is RDAP (Registration Data Access Protocol) Going to Replace WHOIS? RDAP was created as a WHOIS system successor and is ultimately expected to replace WHOIS as the official source for IP addresses, Do...

Using Cyber Kill Chain for Threat Intelligence
Using Cyber Kill Chain for Threat Intelligence To block the attack vector, you need to know how an attacker thinks. The same idea applies to organizations that want to prevent cybercrimes. The conseq...

Why Is It Important? East-West and North-South Traffic Security
Why Is It Important? East-West and North-South Traffic Security Data centers are physical facilities designed to support your business applications, AI activities, file sharing, communications and col...

Different Types of Threat Intelligence: What is It & Who is It for?
Different Types of Threat Intelligence: What is It & Who is It for? The information provided by the threat intelligence, it makes a significant contribution to various business decisions in organ...
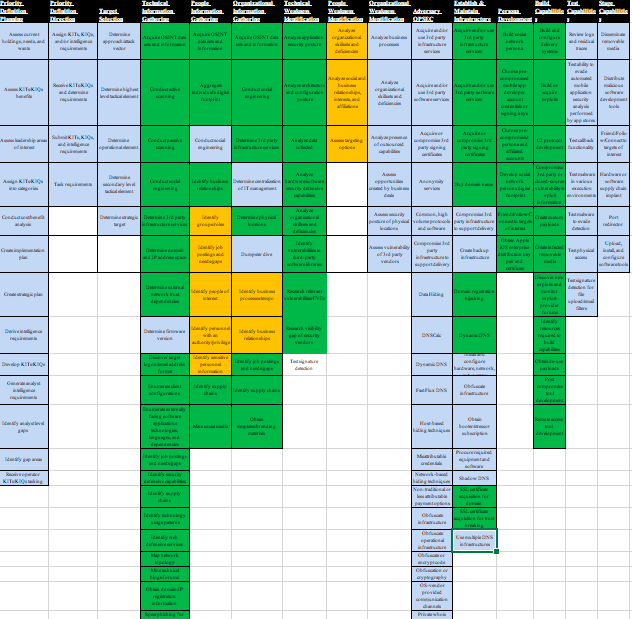
What’s MITRE PRE-ATT&CK and How To Use It in Threat Intelligence?
What’s MITRE PRE-ATT&CK and How To Use It in Threat Intelligence? Founded in 1958, MITRE is a non-profit company whose mission is to solve the problem of a safer world. A new curated knowledge ba...

What You Need To Know About Traffic Light Protocol Usage in Threat Int...
What You Need To Know About Traffic Light Protocol Usage in Threat Intelligence There are a few standards and formats for timely and more effective exchange of sensitive intelligence, and Traffic Ligh...
Open Source Intelligence (OSINT) 101
Open Source Intelligence (OSINT) 101 Open Source Intelligence, better known as OSINT, is a technology that refers publicly available and open sources of information (as opposed to covert or secret sou...

Types of Threat Intelligence Gathering
Types of Threat Intelligence Gathering For better security functioning, all organizations need reliable but also real-time cyber threat intelligence. Producing threat intelligence is a complex process...