
Analysis of UK Password Dictionary: The Ultimate Wordlist
Analysis of UK Password Dictionary: The Ultimate Wordlist Passwords should be strong and unique. They act as the first line of defense in safeguarding our personal and business digital assets. As we e...

Password Dictionary Analysis: Ultimate Wordlist of USA Passwords
Password Dictionary Analysis: Ultimate Wordlist of USA Passwords In the digital age, where our lives are increasingly connected with technology, the importance of securing our online accounts cannot b...

Inevitable Tool in Pentesters’ Arsenal: Password Dictionary Lists
Inevitable Tool in Pentesters’ Arsenal: Password Dictionary Lists Newbie penetration testers often struggle to grasp the significance of the initial findings reported by most Dynamic Application Scann...

DarkGate Malware: Exploring Threats and Countermeasures
DarkGate Malware: Exploring Threats and Countermeasures As we get increasingly digitized, the threat posed by malware has reached unprecedented levels in parallel. From individual users to large corpo...

Using Jupyter Notebook for CTI using PyMISP
Using Jupyter Notebook for CTI using PyMISP In Cyber Threat Intelligence (CTI), Jupyter Notebook and PyMISP are transformative tools. Just as Bash commands empower defenders, these platforms offer dyn...

‘Classified’ Intel on the ‘Public’ Telegram Channel: Pentagon US Leak...
‘Classified’ Intel on the ‘Public’ Telegram Channel: Pentagon US Leak In the rapidly evolving landscape of digital communication, Telegram has emerged as a prominent platform for various user groups f...

QakBot, One of The Most Observed Malware
QakBot, One of The Most Observed Malware [Update] February 16, 2024: “New Qbot Malware Variant Uses Evasion Techniques” [Update] November 22, 2023: See the subheading “Possible Successors of QakBot: D...

Raccoon Stealer Resurfaces with New Enhancements
Raccoon Stealer Resurfaces with New Enhancements The developers behind the information-stealing malware, Raccoon Stealer, have broken their six-month silence on hacker forums. They are now promoting a...

Telegram Channels Unveiled: The Hidden Dangers Lurking in Shared Files
Telegram Channels Unveiled: The Hidden Dangers Lurking in Shared Files In today’s interconnected world, cyberspace has become a breeding ground for legitimate and malicious activities; Telegram, a pop...

Possible Cyber Threats in the 2024 Olympics
Possible Cyber Threats in the 2024 Olympics The design of the Paris 2024 Olympic and Paralympic torch, introduced on July 25, 2023, struck the first gong for The Paris 2024 Summer Olympic and Paralymp...

What is EMOTET Malware and How to Protect Yourself
What is EMOTET Malware and How to Protect Yourself According to Arne Schoenbohm, who leads the German Federal Office of Information Security (BSI), EMOTET is the king of malware. EMOTET actively attac...

The Mindset Behind Phishing Campaigns
The Mindset Behind Phishing Campaigns Phishing attacks are cybercrimes that target individuals, businesses, and organizations. These attacks use deception and manipulation techniques to trick victims ...
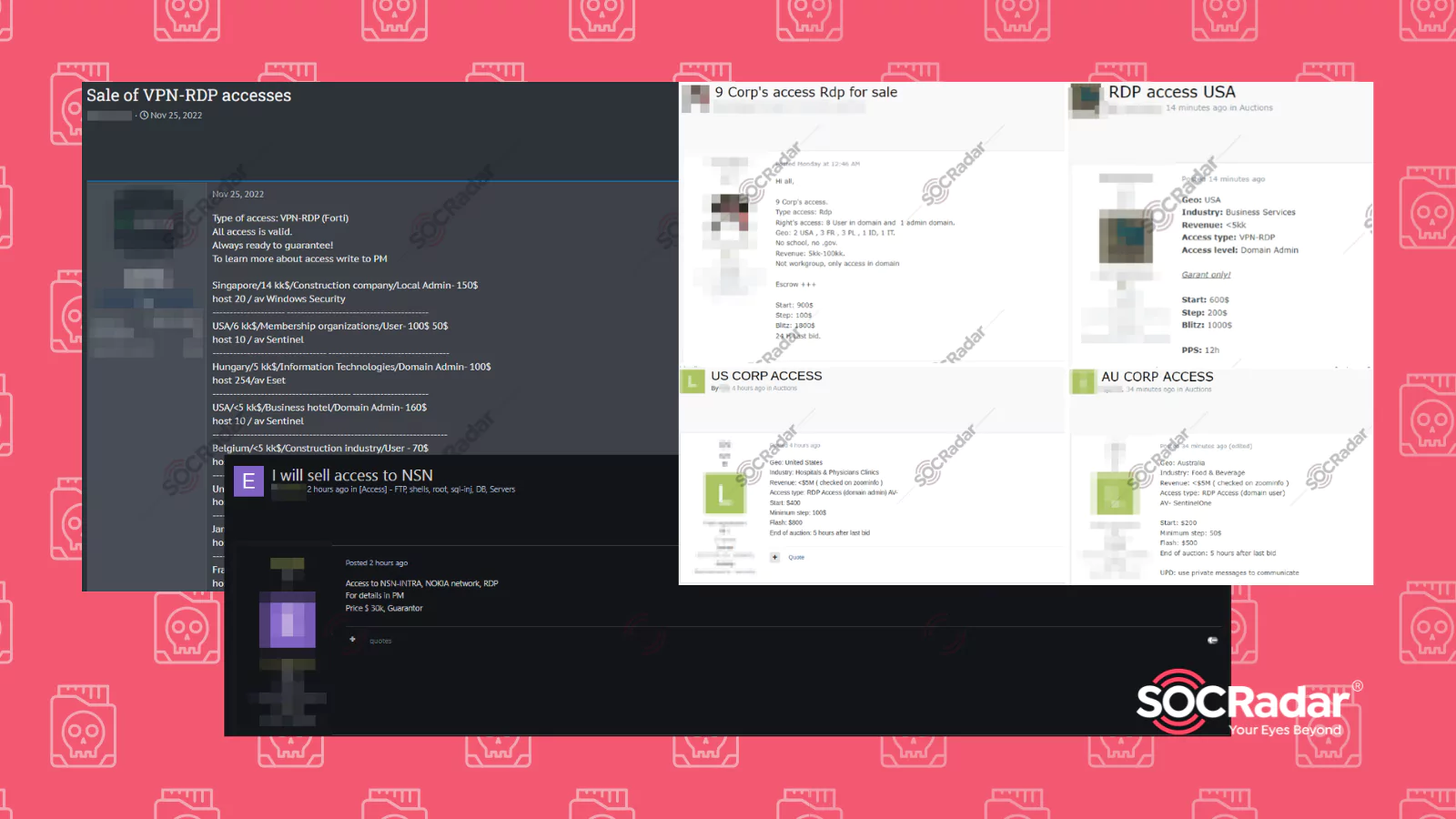
RDP Access Sales on Dark Web Forums Detected by SOCRadar
RDP Access Sales on Dark Web Forums Detected by SOCRadar Remote Desktop Protocol, or RDP, is a protocol developed by Microsoft. It allows the user to control another computer over a network connection...

CSP Bypass Unveiled: The Hidden Threat of Bookmarklets
CSP Bypass Unveiled: The Hidden Threat of Bookmarklets A bookmarklet is a primitive version of browser extensions commonly used today. It consists of a bookmark that contains JavaScript code. These bo...

Google's New ZIP Domain Could Be Used for Phishing and Malware Attacks
Google’s New ZIP Domain Could Be Used for Phishing and Malware Attacks Security researchers have found how attackers could potentially exploit the new ZIP TLD offered by Google. A new ...

What is a Phishing Kit?
What is a Phishing Kit? A phishing kit is a set of software tools, such as HTML, pictures, and code that fraudsters can use to construct and launch phishing attacks. Phishing kits allow anyone with li...

How SOCRadar Can Help Fraud Teams?
How SOCRadar Can Help Fraud Teams? Fraud refers to transactions made using card information without the knowledge of cardholders in the card payment sector in cybersecurity or purchases made...

How to Stop a DDoS Attack? (2023 Edition)
How to Stop a DDoS Attack? (2023 Edition) ...

Top Cyber Threats Faced in Fintech and Cryptocurrency Industries
Top Cyber Threats Faced in Fintech and Cryptocurrency Industries People are more inclined to move their financial assets to a digital environment due to the ongoing advancements in technology and ...

What Do You Need to Know About New SAMA Principles?
What Do You Need to Know About New SAMA Principles? The Kingdom of Saudi Arabia (KSA) has launched a digital transformation program focusing on the banking industry. With the growing digitization of f...

































