
0-Day Exploit Sales for Outlook and Jenkins, Insurance and Banking Dat...
0-Day Exploit Sales for Outlook and Jenkins, Insurance and Banking Data Leaks, and More Journey through the sinister realms of cyberspace with SOCRadar’s Dark Web Team. The sale of critical 0-day expl...

Intelligence Pioneers: Meet the Top 10 CTI Experts
Intelligence Pioneers: Meet the Top 10 CTI Experts The expertise of Cyber Threat Intelligence (CTI) professionals is essential in strengthening digital defenses against ever-evolving threats. Within t...

Business Email Compromise (BEC) Attacks: A Sneaky Threat to Organizati...
Business Email Compromise (BEC) Attacks: A Sneaky Threat to Organizations The pandemic has brought about radical changes in business models. Alongside digital transformation, the increased efficiency ...

What is YARA, YARA v4.5.0 and YARA-X
What is YARA, YARA v4.5.0 and YARA-X Effective threat detection and analysis are essential for safeguarding digital assets in cybersecurity. YARA stands as a key tool in the arsenal of cybersecurity p...

Exploring the Threat Landscape of Adversarial AI with MITRE ATLAS
Exploring the Threat Landscape of Adversarial AI with MITRE ATLAS Navigating the complex landscape of cybersecurity threats requires constant vigilance, especially with the rise of Artificial Intellig...

DarkGate Malware: Exploring Threats and Countermeasures
DarkGate Malware: Exploring Threats and Countermeasures As we get increasingly digitized, the threat posed by malware has reached unprecedented levels in parallel. From individual users to large corpo...

CISA’s Weekly Summary – CVSS 10 Vulnerabilities in Progress’ LoadMaste...
CISA’s Weekly Summary – CVSS 10 Vulnerabilities in Progress’ LoadMaster and OpenEdge, Myriad Critical Flaws [Update] March 29, 2024: “Threat Actors Exploit LoadMaster Vulnerability (CVE-2024-1212)” [U...

How SOCRadar Helps You Improve Your CTEM Program
How SOCRadar Helps You Improve Your CTEM Program Gartner published a report at the beginning of December 2022 and predicted how enterprises should implement a cybersecurity understanding for 2023 and ...
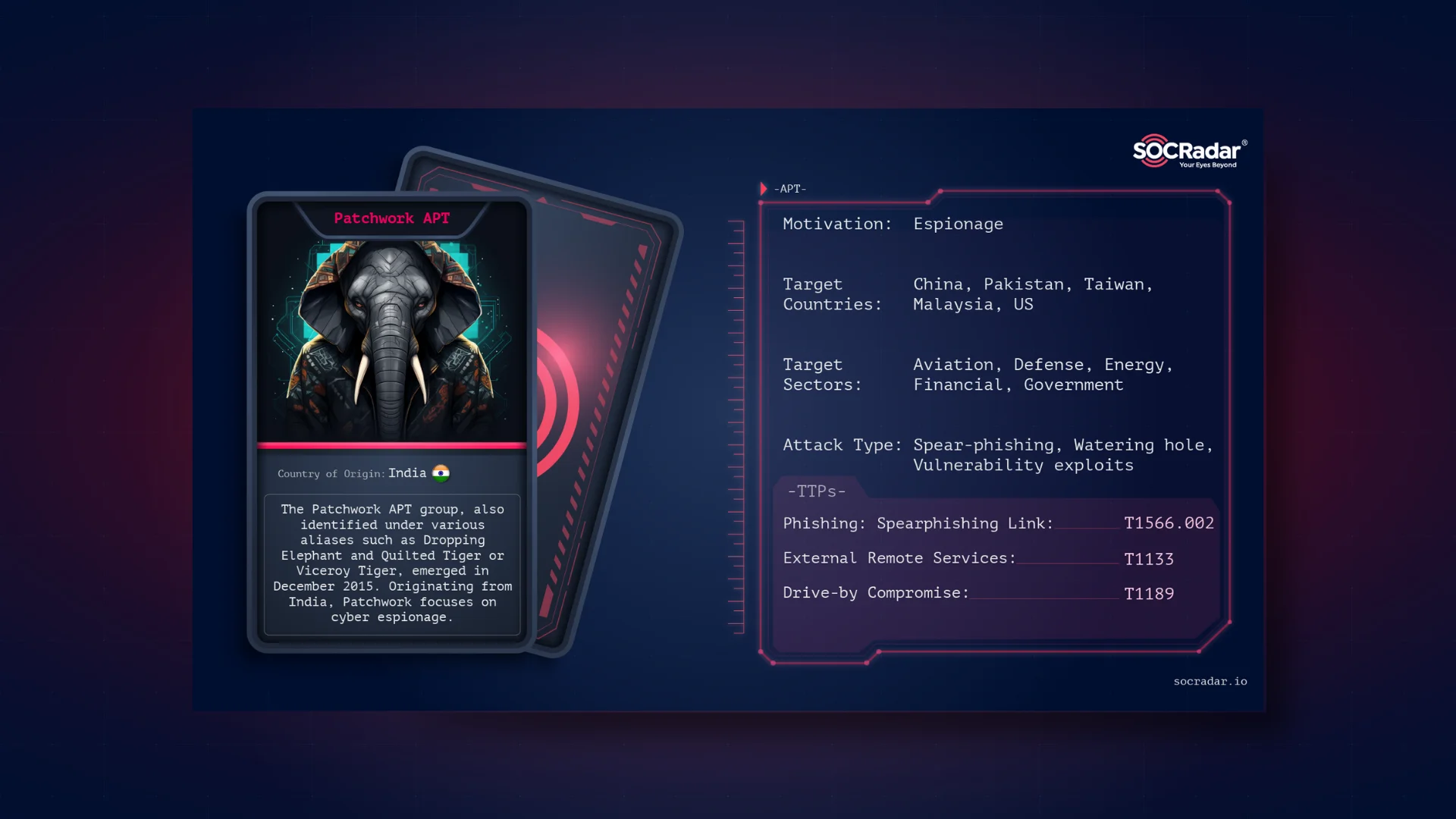
Dark Web Profile: Patchwork APT
Dark Web Profile: Patchwork APT The Patchwork APT group, identified in December 2015 but probably active since 2009, is a cyber espionage entity suspected to be based in India. It targets a variety of...

LAX and Generali Database Leaks, US Credit Card Sales, Unauthorized Ac...
LAX and Generali Database Leaks, US Credit Card Sales, Unauthorized Accesses, and Recruitment Posts Discover the latest revelations from the SOCRadar Dark Web Team, exposing a myriad of security breac...

Attack Surface Management with Open-Source Tools and Services
Attack Surface Management with Open-Source Tools and Services As the first line of defense against cyber attacks, adept attack surface management is critical in reducing the chance of a successful bre...

Top 10 Deep Web and Dark Web Forums
Top 10 Deep Web and Dark Web Forums [Update] May 14, 2024: “Bonus: Daily Dark Web” The dark web hosts a myriad of forums that operate beyond the reach of conventional internet users, serving as epicen...

Dark Peep #11: The Final Curtain for LockBit Ransomware (Operation Cro...
Dark Peep #11: The Final Curtain for LockBit Ransomware (Operation Cronos) Digital Olympians and seekers of cyber lore! “Dark Peep #11” unfurls its scroll to reveal tales of cunning, courage, an...

Shadow Ops Exposed: Inside the Leak of China's i-Soon Cyber Espionage ...
Shadow Ops Exposed: Inside the Leak of China’s i-Soon Cyber Espionage Empire Chinese authorities, law enforcement agencies, cybersecurity researchers, and a whole lot of other people are investi...

Critical Vulnerabilities in ConnectWise ScreenConnect, PostgreSQL JDBC...
Critical Vulnerabilities in ConnectWise ScreenConnect, PostgreSQL JDBC, and VMware EAP (CVE-2024-1709, CVE-2024-1597, CVE-2024-22245) [Update] March 5, 2024: “Kimsuky Takes Advantage of ScreenConnect ...

Using Jupyter Notebook for CTI using PyMISP
Using Jupyter Notebook for CTI using PyMISP In Cyber Threat Intelligence (CTI), Jupyter Notebook and PyMISP are transformative tools. Just as Bash commands empower defenders, these platforms offer dyn...

Weekly Vulnerability Summary by CISA – February 12, 2024; New ICS Advi...
Weekly Vulnerability Summary by CISA – February 12, 2024; New ICS Advisories The Cybersecurity and Infrastructure Security Agency (CISA) has once again issued a summary of the latest vulnerabilities. ...
Power of AI: Dark Web Monitoring with ChatGPT
Power of AI: Dark Web Monitoring with ChatGPT The dark web, often shrouded in mystery and intrigue, is a part of the internet that remains hidden from conventional search engines and browsers. It̵...

Multiple Zero-Day and RCE Vulnerabilities Aboard: AutoCAD, SolarWinds ...
Multiple Zero-Day and RCE Vulnerabilities Aboard: AutoCAD, SolarWinds ARM, Bricks Builder Under Risk The Zero Day Initiative (ZDI) has reported several vulnerabilities affecting Autodesk AutoCAD; thes...
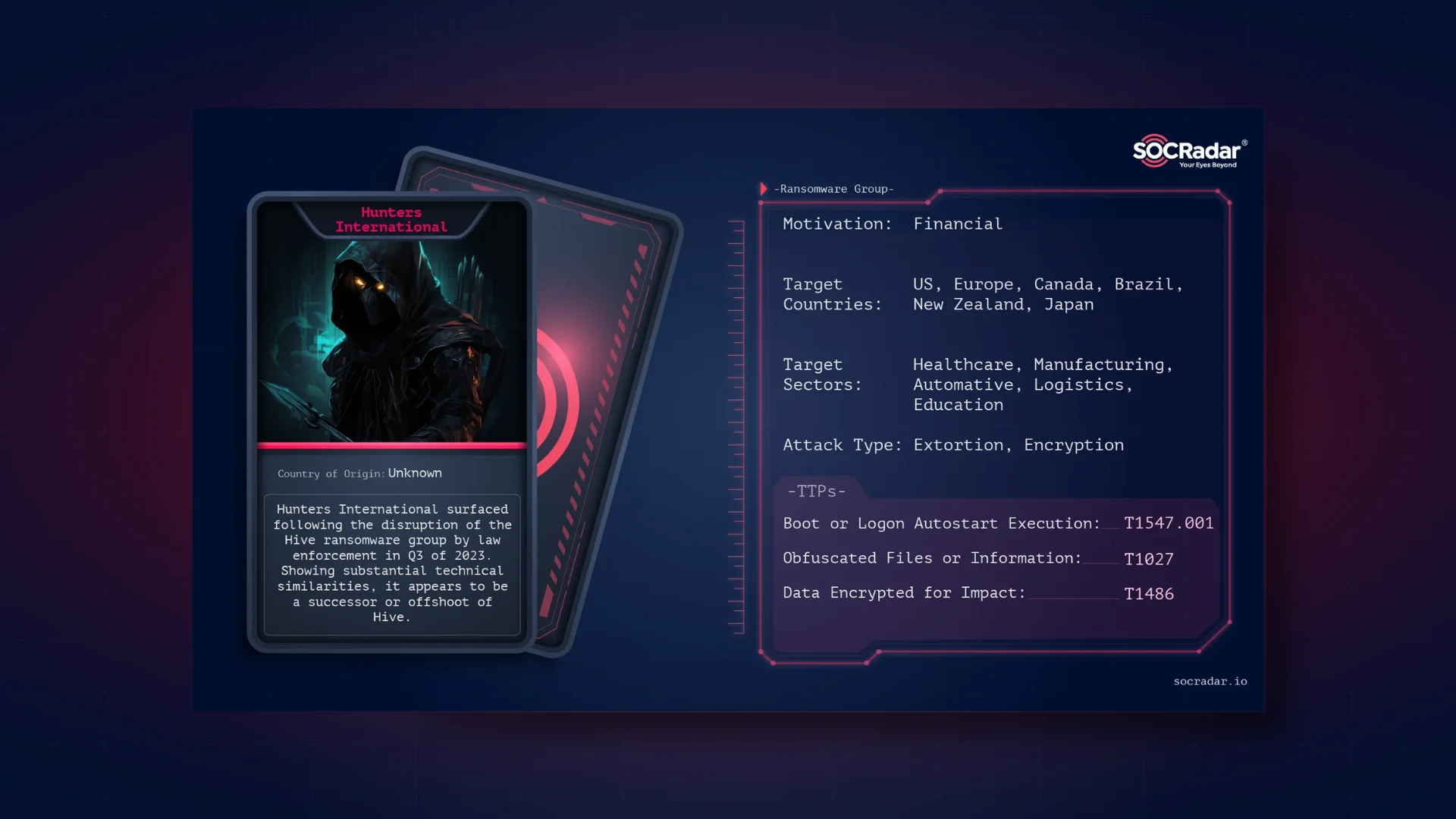
Dark Web Profile: Hunters International
Dark Web Profile: Hunters International Originating in the latter part of 2023, this Ransomware-as-a-Service (RaaS) operation has drawn attention due to its technical lineage and operational tactics r...































