
Real-Life Examples of Successful Threat Intelligence Operations
Real-Life Examples of Successful Threat Intelligence Operations Threat intelligence can improve organizations’ overall security posture and reduce the risk of cyber attacks by developing proactive str...

SOCRadar and VirusTotal Join Forces to Supercharge Cybersecurity Commu...
SOCRadar and VirusTotal Join Forces to Supercharge Cybersecurity Community Today, SOCRadar, inventor of the Extended Threat Intelligence concept, and VirusTotal, a well-renowned malware...

Microsoft's June 2023 Patch Tuesday Fixes Six Critical Vulnerabilities
Microsoft’s June 2023 Patch Tuesday Fixes Six Critical Vulnerabilities Microsoft has released the Patch Tuesday update for June 2023, which addresses 78 security vulnerabilities. While six ...

Data Breach at Zacks Investment Research: 8.8M Customer Records are Ex...
Data Breach at Zacks Investment Research: 8.8M Customer Records are Exposed Zacks Investment Research has suffered an undisclosed data breach. As a result, a threat actor has shared the breached datab...

What is New in the MITRE ATT&CK Framework v12 and v13?
What is New in the MITRE ATT&CK Framework v12 and v13? New threat actors are emerging on the dark web daily, and cybercrimes are increasing exponentially. According to some research insights,...

Open-Source RATs Leveraged By APT Groups
Open-Source RATs Leveraged By APT Groups The complexity and continuous evolution of cyber threats make the attack techniques developed by attackers with objectives such as information theft, espionage...

MOVEit Exploit Sales, Doge RAT, and Bandit Stealer Malware
MOVEit Exploit Sales, Doge RAT, and Bandit Stealer Malware As we continue exploring the digital landscape’s obscure corners, the dark web remains an enigmatic yet critical part of the cyberspace...

Fortinet Rolls Out Patches for Critical RCE Vulnerability in SSL VPN D...
Fortinet Rolls Out Patches for Critical RCE Vulnerability in SSL VPN Devices (CVE-2023-27997) [Update] July 04, 2023: Recent findings reveal that despite a recent update from Fortinet, hundreds of tho...
Top 12 Takeaways from Verizon 2023 Data Breach Investigations Report
Top 12 Takeaways from Verizon 2023 Data Breach Investigations Report Verizon’s highly anticipated 16th annual data breach investigation report was released on June 6, 2023. This report, inc...

Google Switches Email Authentication Method Following Exploitation by ...
Google Switches Email Authentication Method Following Exploitation by Scammers Google has patched a vulnerability that allowed a threat actor to pose as UPS on Gmail. The emai...

SOCRadar is Now Officially a dns0.eu Tech Alliance Partner
SOCRadar is Now Officially a dns0.eu Tech Alliance Partner In the ceaseless pursuit of fortifying digital landscapes and strengthening cybersecurity ecosystems, SOCRadar is thrilled to announce its of...

VMware and Cisco Patched Critical RCE and Privilege Escalation Vulnera...
VMware and Cisco Patched Critical RCE and Privilege Escalation Vulnerabilities [Update] June 21, 2023: VMware has revised a recent security advisory regarding a critical vulnerability, CVE-2023-20887,...

Countering Nation-State Cyber Attacks with Threat Intelligence
Countering Nation-State Cyber Attacks with Threat Intelligence In recent years, attacks targeting critical infrastructures and political figures of states have increased. These attacks are o...

Major Cyberattacks in Review: May 2023
Major Cyberattacks in Review: May 2023 Throughout May 2023, the cybersecurity landscape witnessed a surge in notable cyberattacks. These incidents encompassed supply chain attacks, data breaches,...

Cyclops Ransomware: Cross-Platform Threat with RaaS and Advanced Featu...
Cyclops Ransomware: Cross-Platform Threat with RaaS and Advanced Features [Update] August 7, 2023: After officially rebranding as Knight, Cyclops has shared their new stealer named “Knight steal...

The State of Cybersecurity in Healthcare: A Review of SOCRadar's Healt...
The State of Cybersecurity in Healthcare: A Review of SOCRadar’s Healthcare Threat Landscape Report The cybersecurity landscape in the healthcare industry is becoming increasingly treacherous, as deta...

Zyxel Firewall Flaws Exploited: Urgent Action Required
Zyxel Firewall Flaws Exploited: Urgent Action Required [Update] July 24, 2023: Threat actors are targeting several Zyxel devices with CVE-2023-28771. Fortinet has detected a significant rise in botnet...
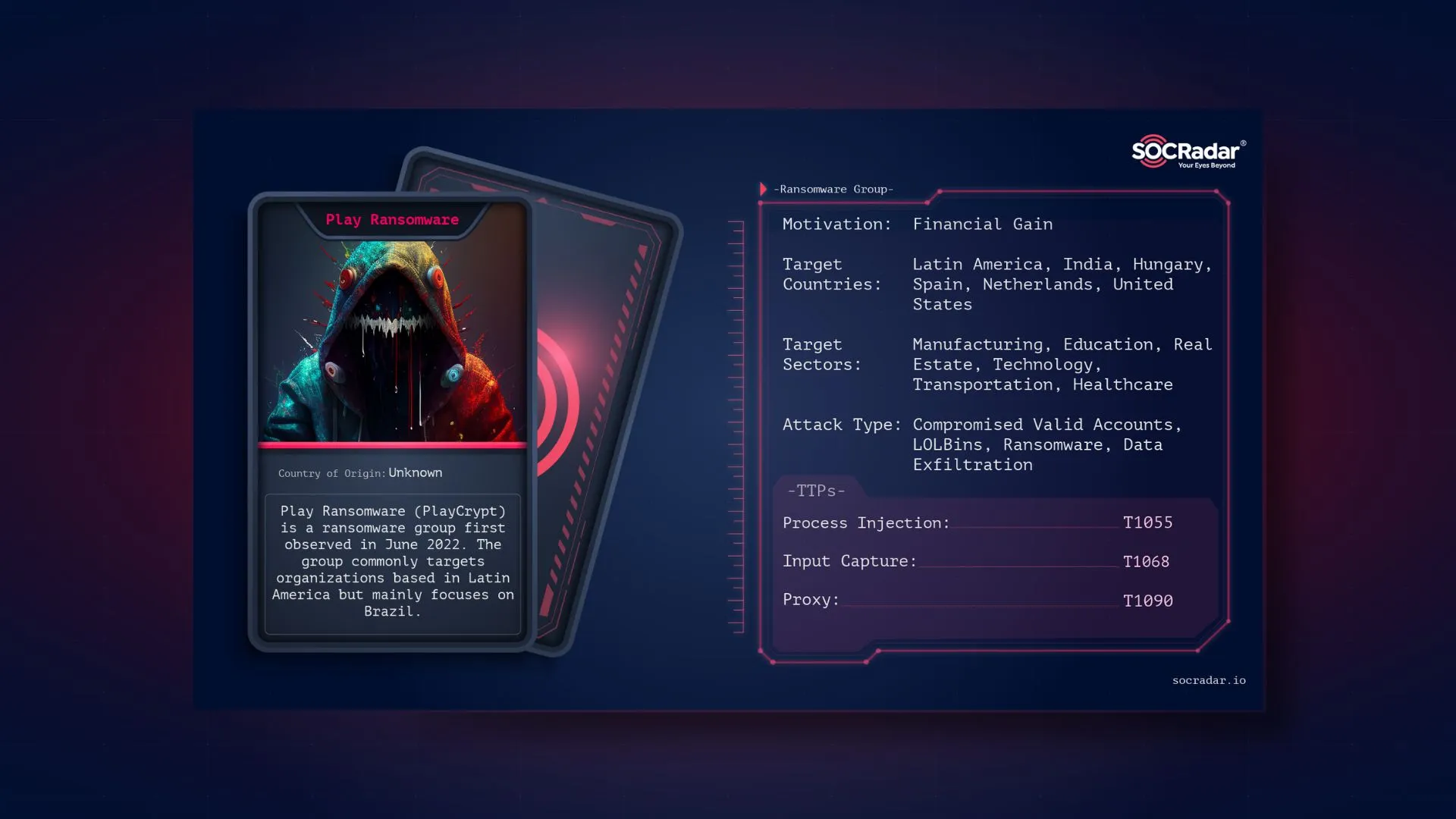
Dark Web Profile: Play Ransomware
Dark Web Profile: Play Ransomware [Update] July 22, 2024: “Play Ransomware Broadens Its Scope with New Linux Variant Targeting ESXi” [Update] December 19, 2023: “Collaborative Advisory on Play Ransomw...

Gigabyte Firmware Code Injection: Persistent Backdoor Leads to Supply ...
Gigabyte Firmware Code Injection: Persistent Backdoor Leads to Supply Chain Risks Researchers have expressed concerns about the UEFI firmware found in numerous motherboards by Gigabyte,...

RaidForums Leak, Breached IT Services, and New LockBit Victim
RaidForums Leak, Breached IT Services, and New LockBit Victim Step into the shadowy world of the dark web as we explore this week’s gripping headlines. From the leaked RaidForum database to unau...

































