
Cyber Threat Intelligence (CTI) Roles for Ransomware Protection
Ransomware attacks remain one of the most significant cyber threats against organizations today. Despite numerous countries launching coordinated efforts to combat ransomware groups through law enforcement takedowns, cryptocurrency seizures, and indictments, the crime continues to proliferate. A key aspect of many anti-ransomware strategies is the enhancement of cyber resiliency. A cyber resilient organization has a high capacity to adapt to known and unknown threats, attacks, adverse situations and challenges. However, this is no easy task. The ability of organizations to strengthen their security posture and boost their core cybersecurity defenses varies across different sectors. The attack surface that ransomware actors can exploit is extensive, diverse, and constantly changing, presenting considerable challenges for defense.
Organizations often detect a ransomware attack only when the attackers have already exfiltrated sensitive data and initiated the final encryption phase. However, there are numerous methods businesses can employ to utilize threat intelligence to discover they may be a target of a ransomware group. The ability to identify such signs can begin long before a network has been compromised. This blog post draws attention to those signals and indicators that could provide a crucial warning before cybercriminals carry out a successful attack and damage digital assets.
Recent Trends in Ransomware Attacks
In recent years, there has been a surge in Ransomware-as-A-Service (RaaS) offerings by threat actors. This development allows less technically proficient threat actors to conduct attacks, as they do not need the expertise required to develop malicious software, maintain infrastructure, or even have technical support.
SOCRadar Dark web analysts continuously monitor and detect ransomware groups targeting organizations worldwide. Their recent observations show that despite all security measures and efforts, activities and variations of ransomware groups continue to grow.
Why do ransomware strains continue to proliferate? To answer this question, let’s consider a typical example. After Babuk, a ransomware strain whose source code was leaked online in June 2021, more than 10 ransomware groups were found to have developed their own Babuk-based malware, namely inspired by the Babuk source code ransomware families.
This trend enhances the ability for individuals to develop malware strains with slight modifications, thereby making the landscape of actors even more diverse. As a result, tracking, detection, and prevention of new ransomware variants effectively becomes increasingly challenging.
According to Trend Micro, there are several significant evolutions in ransomware, such as a focus on data extortion, profiting from data monetization, targeting endpoints in the cloud, aiming for uncommon platforms, scaling up through automation, and exploiting zero-day vulnerabilities.
Why Threat Intelligence is Critical for Ransomware Protection?
Government Policies and Efforts are insufficient.
While governments have made efforts to combat ransomware, including enacting laws, regulations and increasing law enforcement resources, these measures have not been enough to stem the tide of attacks. The takedowns of the Hive’s infrastructure and the Genesis marketplace earlier this year have likely prevented some ransomware attacks and sent a clear message to the ransomware community. Moreover, threat actors’ use of technologies that enable anonymity complicates the task for security forces.
SOCRadar security analysts also support the thesis that ransomware attackers are constantly evolving the infrastructure they use, making it difficult for policymakers and law enforcement to keep pace. As a result, it is up to individuals and organizations to take steps to protect themselves and respond effectively to attacks.
TTPs are changing and evolving to become more sophisticated.
Ransomware groups are known to collaborate with groups identified as Advanced Persistent Threats (APTs), many of which are state-sponsored. Therefore, international cooperation only works to a certain extent.
Against sophisticated attacks, traditional security solutions are not sufficient. Specifically, lagging in vulnerability management and ignorance of possible vulnerabilities (e.g., zero-day) in multiple technological products increases the risk of potential threats. Therefore, in addition to reducing attack surfaces and managing them with Attack Surface Management (ASM) services like SOCRadar EASM , actionable intelligence information becomes essential.
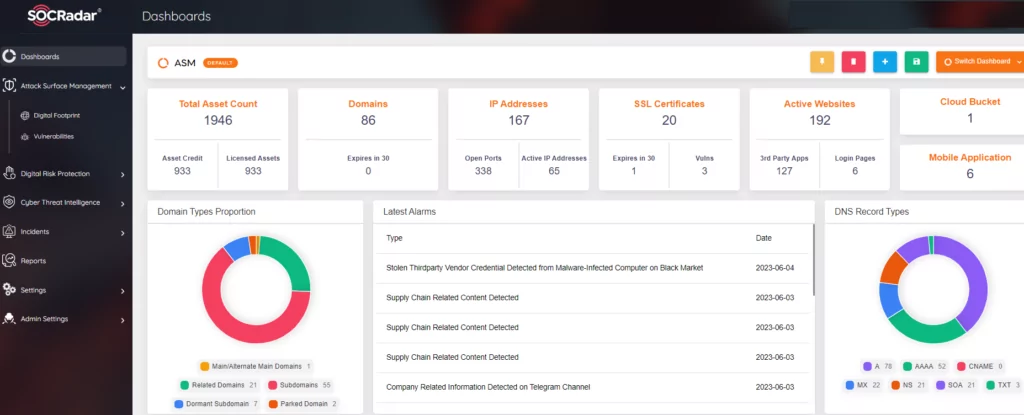
Advanced Extortion Tactics
A significant proportion of data breaches are caused by ransomware extortion. According to the IBM Cost of Data Breach Report 2023, over one-quarter, or 27%, of breaches were disclosed by the attacker as part of a ransomware attack. Data breaches disclosed by the attacker, such as with ransomware, cost significantly more. As a result of the exploitation of CL0P ransomware’s MOVEit zero-day vulnerabilities, not only was the data of more than 500 organizations exposed, but the estimated number of victimized individuals exceeded 40 million.

According to Fortinet’s 2023 Global Ransomware Report, organizations that reported employing a best-of-breed point product approach to security were the most likely (67%) to fall victim to ransomware. In contrast, those that consolidated technologies to adopt a platform-driven approach were the least likely (37%) to be breached. Moreover, these organizations ranked the following attributes as ‘extremely important’ when evaluating new technologies: solutions that include actionable threat intelligence (50%), have AI-driven behavioral detection capabilities (48%), and are designed to work together (45%).
How do ransomware gangs manage to break in?
According to Sophos’ States of Ransomware 2023 Report, exploited vulnerabilities were the most common root causes of ransomware attacks (36%), followed by compromised credentials (29%). These findings align almost precisely with Sophos’ latest retrospective analysis of 152 attacks that the Incident Response and Managed Detection and Response (MDR) teams were brought in to remediate, where 37% started with an exploited vulnerability and 30% with compromised credentials. Phishing emails were the root cause of 30% of ransomware attacks: 18% started with a malicious email and 13% with phishing. 3% began with a brute force attack and just 1% with a download.
What are the Main Attack Vectors Used by Ransomware Groups?
Ransomware can gain access to an organization’s systems in several ways. However, ransomware operators tend to favor specific infection and distribution vectors. Overall results pinpoint most ransomware incidents to just four (4) main categories of attack vectors such as phishing emails and malware infection, RDP/VPN access, exploiting software vulnerabilities, and compromised login credentials.
- Phishing Emails and Malware Infection
A malicious email may consist of a link to a website hosting a malicious download or an attachment that incorporates downloader functionality. If the email recipient falls for the phishing, then the ransomware can be downloaded and executed on the computer.
The goal for threat actors when attacking an organization’s network is to plant malware on a computing system undetected. To accomplish this task, malware is continually evolving and improving. These advancements have forced defenders to detect minute changes and behaviors that may indicate an intrusion. But it is often too late; once malware is on a system, an organization is already at a disadvantage. During the dwell time between intrusion and detection, attackers move laterally into other systems, establishing other points of persistence that allow them to maintain a foothold even if the initial intrusion is discovered. However, it is possible to get ahead of attack groups distributing malware and use that valuable threat intelligence for defense.
One way to do this is by studying how malware behaves and how it is distributed. Malware is often disseminated via botnets or networks of infected computers controlled by a group of attackers. A common precursor to a ransomware attack is the infection of a network with malware. Emotet and Trickbot, both large botnets that sent prolific volumes of malspam, were responsible for the distribution of malicious code that often led to an infection by the Conti and Ryuk ransomware groups.
Botnets are a critical component of the cybercrime-as-a-service economy, acting as the distribution mechanism for malware to capture new victim machines. These machines can be consumer computers, Internet-of-Things (IoT) devices, or machines in corporate networks. Threat actors use bots to send spam, as proxies for intrusions, and for other malicious actions such as distributed Denial-of-Service (DDoS) attacks. The bots themselves can also be exploited for their data, such as login credentials.
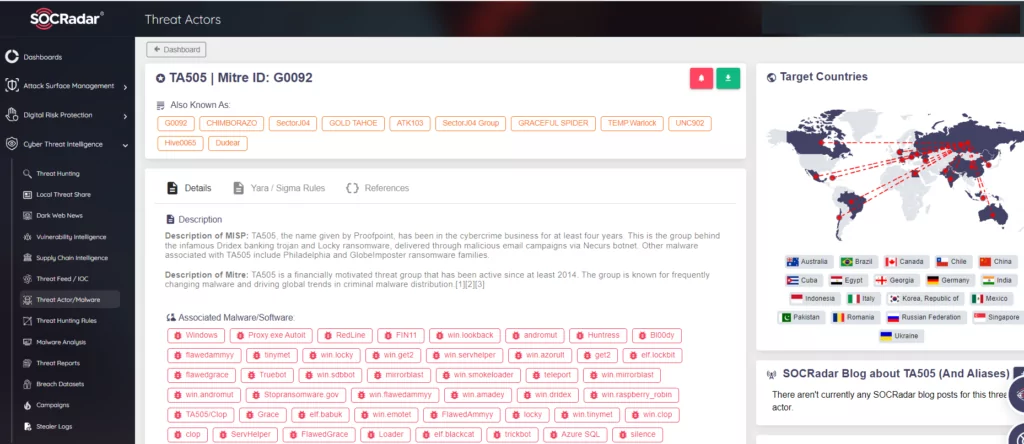
To understand how threat actors are using botnets and the malware they are distributing, SOCRadar’s Threat Actors/Malware module can assist your organization. By programmatically collecting malware and monitoring how it is being distributed, organizations can gain insight into malware campaigns and targeting long before threat actors initiate a ransomware event.
For example, you can gain intelligence that threat actors selectively choose their victims and focus their targets on a country and sector basis. SOCRadar’s Threat Actor Tracking provides intelligence information, enriched with the knowledge obtained from the MITRE ATT&CK database about changing Tactics, Techniques, and Procedures (TTPs), which can be much more crucial than easily replaceable Indicators of Compromises (IoCs), to dynamically understand and track cyber adversaries. Through automated data collection, classification, and AI-powered analysis of hundreds of sources on the surface, deep, and dark web, SOCRadar can alert you about the activities of APT/Ransomware groups, helping you identify use cases to effectively detect and prevent malicious attempts. In the image below, you can see the technical intelligence data on the TA505, aka Cl0p, ransomware gang.
- RDP/ VPN access
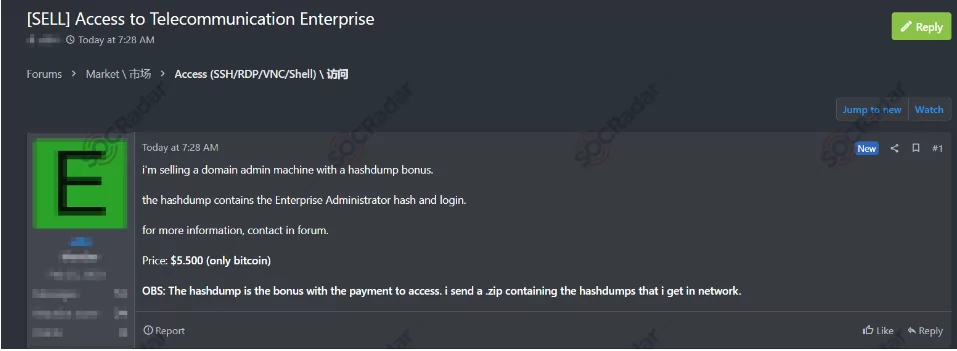
Another prevalent ransomware infection vector capitalizes on services like the Remote Desktop Protocol (RDP) access. With RDP access, an attacker who has stolen or guessed credentials can use an employee’s login to authenticate and remotely access the enterprise network. These logins can be stolen or guessed, or they can be obtained directly from the sale of an RDP or VPN, as in the recent example shared below.
The sale of access, which has become widespread on dark web forums, represents a potential danger that warrants emphasis. These sales can sometimes involve ‘Active Directory’ (AD) or ‘domain admin’ information and signify the ‘Initial Access’ stage, which is the first and most critical entry gate of cyber-attacks. These access sales may also include ‘RDP’ and ‘VPN’ login credentials that threat actors evaluate. It is crucial for businesses to obtain such sensitive and verified threat intelligence information before the weaponization phase of threat actors.
According to a recent analysis by SOCRadar security researchers, ransomware groups are one of the primary affiliations of Initial Access Brokers. With the emergence of the Ransomware-as-a-Service (RaaS) model used by well-known groups such as LockBit 3.0, these two methods have started to intertwine.
On June 25, 2023, in a hacker forum monitored by SOCRadar, an unauthorized network access sale was detected, allegedly belonging to a telecommunications company. Ingesting such actionable information in a timely manner is critical for your business to proactively combat cyber-attacks, especially ransomware.
- Software Vulnerability Exploitation
A powerful method to compromise organizations is by exploiting software vulnerabilities. These attacks may be possible if an organization has not promptly installed patches released by a vendor. Another avenue is zero-day attacks, or exploiting software vulnerabilities that are unknown and do not have patches. An example of a zero-day exploit by a ransomware and extortion group recently occurred with a profound impact. The group known as CLOP ransomware (also referred to as TA505) exploited a vulnerability in the MOVEit file transfer software to devastating effect. The pre-authentication SQL-injection (SQLi) vulnerability (CVE-2023-34362) allowed CL0P to remotely compromise and extract data from governments, cities, universities, and private organizations. CL0P demanded a ransom in exchange for deleting the data. The incident has underscored the risks of using internet-facing applications that may contain unknown vulnerabilities and are easily monitored and reachable by attackers.
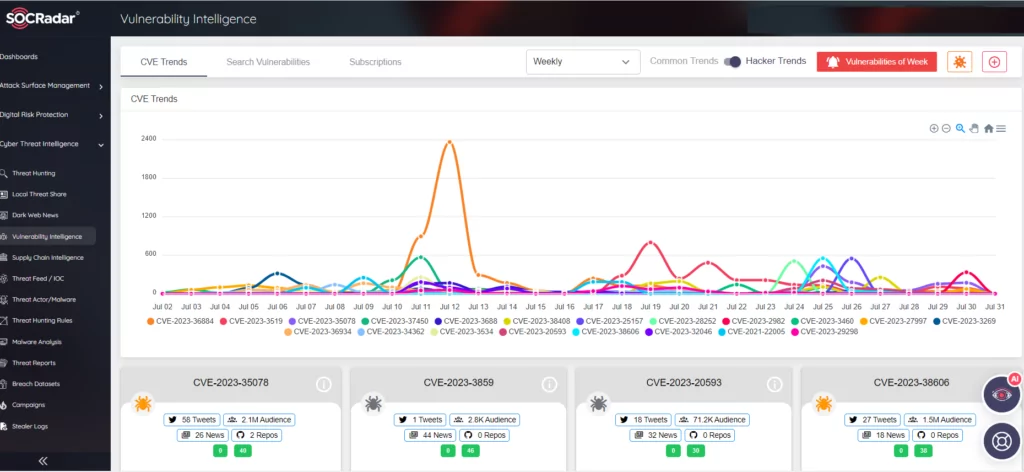
The mass exploitation of a zero-day vulnerability by one group is significant but neither rare nor exceptional. Day-to-day patch management tends to be a trade-off between time and risk. Enterprises that run thousands of applications simply can’t patch them all but do need to patch the vulnerabilities for the most sensitive systems that are at the highest risk of exploitation. Threat actors on underground forums discuss, develop, and monetize exploits for software vulnerabilities. Monitoring these activities can aid in prioritizing patching based on whether, for example, there is a working Proof-of-Concept (PoC) exploit for a vulnerability available or an offer of an exploit for sale on a forum.
Threat actors, especially ransomware groups, are exploiting an increasing number of security vulnerabilities. Thus, prioritizing patch management and deploying patches in a timely manner is essential. Moreover, as the number of known exploited vulnerabilities tends to increase, the SOCRadar Vulnerability Intelligence module constantly monitors and informs you to take action as soon as possible.
- Credential Theft
The theft and subsequent misuse of login credentials remain still one of the biggest challenges for organizations. Cybercriminals capture login credentials in various ways, including phishing methods for various social engineering ploys. Phishing may encompass creating fake websites with login forms that collect entered information. While multifactor authentication (MFA) can prevent the successful misuse of stolen usernames and passwords, it isn’t flawless, and threat actors continually refine social engineering tactics such as bypass techniques to defeat MFA.
There is also a malware side to consider. SOCRadar tracks many strains of information stealers whose distribution begins with malicious spam. These info-stealers collect login credentials and session cookies stored in web browsers. Session cookies enable users to remain logged in to a service. If an attacker can replay a session cookie, they don’t need to log in to a service, thereby bypassing MFA.
Login credentials are sold in underground marketplaces and through private sales via initial access brokers (IABs). Cybercrime-as-a-service refers to the way sections of the criminal underworld have developed their own unique products and tools, which they sell to other cybercriminals. This is one reason why cybercrime continues to grow in scale. Threat actors, including ransomware gangs, don’t have to develop their own capabilities for stealing login credentials. Instead, they can rely on specialized markets to buy those sensitive data. For instance, botnet operators distributing info-stealer malware sell packages of stolen data—referred to as stealer logs—to other fraudsters for monetization.
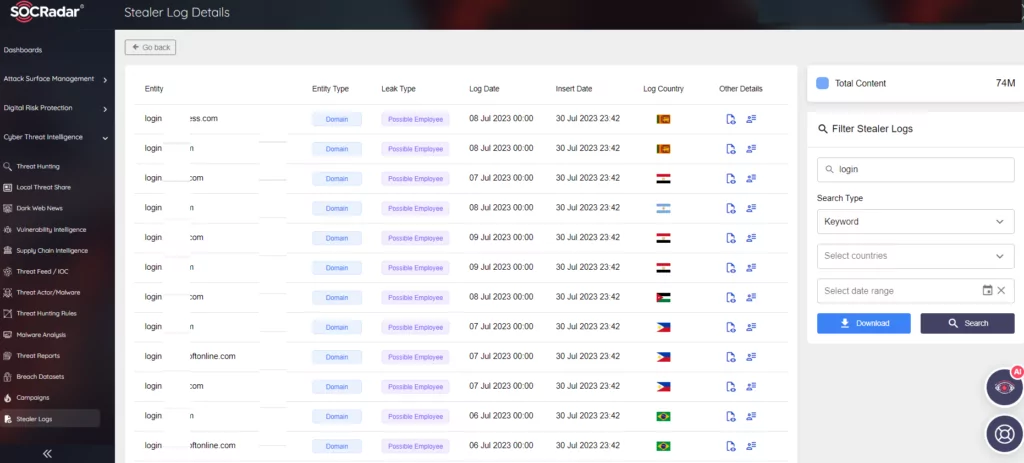
Cyber Threat Intelligence (CTI) can help at several points in this process. SOCRadar collects login credentials from many sources, such as info-stealer logs, database dumps, and breaches, with the aim of early warning organizations when credentials appear on the so-called deep or dark web. Most of the sales of credentials are made by pests called stealers, which are small in size but significant in what they do. A market known as ‘stealer-as-a-service‘ has emerged where these stealers are sold. SOCRadar has recently launched the stealer logs module, obtained and analyzed by dark web analysts, available to its customers for access and search in a structured data format.
Conclusion
While most traditional measures against ransomware attacks prove inadequate, there have been many incidents earlier in the cyber event chain. The effective use of cyber threat intelligence can provide the early warning necessary to understand and mitigate these types of risks.
No area of cybersecurity is immune to the threat of ransomware. International cooperation appears to be vital in the collective fight against ransomware gangs. Otherwise, we can expect these actors to be dismantled from inside, as exemplified by the U.S. Government’s announcement of a ten-million-dollar reward for information related to the CL0P ransomware gang.
Whether independent actors or nation-states are behind the ransomware attacks, it remains a threat that cannot be easily overcome. A platform like SOCRadar XTI can aid in proactive and predictive security by accelerating detection and response to defend against evolving threats. The human factor, which is generally accepted as the weakest link, also plays a role in reducing the effectiveness of offensive and defensive security measures in ransomware attacks. A far more effective approach is proactive protection that leverages cyber threat intelligence to quickly identify and address potential threats. This gives us hope that we can win the cyber battle.




































