
Cisco Fixes Numerous DoS Vulnerabilities in IOS, IOS XE, and Access Po...
Cisco Fixes Numerous DoS Vulnerabilities in IOS, IOS XE, and Access Point Software Cisco recently addressed multiple Denial-of-Service (DoS) vulnerabilities across its product range, including Cisco I...

The Importance of Supply Chain Security for Safeguarding Business Ecos...
The Importance of Supply Chain Security for Safeguarding Business Ecosystems In today’s interconnected digital ecosystem, the security of a single organization doesn’t solely depend on its internal de...

High-Severity Vulnerability in Popular WordPress Plugin ‘File Manager’...
High-Severity Vulnerability in Popular WordPress Plugin ‘File Manager’ Could Lead to CSRF Attacks (CVE-2024-1538) A high-severity security vulnerability, identified as CVE-2024-1538, has recently come...

CHAVECLOAK: A Complex Cyber Threat to Brazil’s Financial Security
CHAVECLOAK: A Complex Cyber Threat to Brazil’s Financial Security The Brazilian financial sector is facing a formidable cyber threat known as CHAVECLOAK, a banking trojan that has emerged as a signifi...

Unlock the Secrets to Safeguarding Your Digital Frontier: A Sneak Peek...
Unlock the Secrets to Safeguarding Your Digital Frontier: A Sneak Peek into the Singapore Threat Landscape In the ever-evolving realm of cybersecurity, knowledge is not just power—it’s your best defen...

OpenVPN Fixed Multiple Vulnerabilities on Windows Version: Risk of Pri...
OpenVPN Fixed Multiple Vulnerabilities on Windows Version: Risk of Privilege Escalation, Remote Access OpenVPN, with the release of a new version, addressed severe security vulnerabilities, specifical...

New DDoS Service, Windows 0-Day Exploit, and US Credit Cards Sale
New DDoS Service, Windows 0-Day Exploit, and US Credit Cards Sale Discover the latest findings by SOCRadar’s Dark Web Team. A new DDoS service promises extended attacks, challenging defenses from Clou...

Critical SQL Injection Vulnerability in PgJDBC Affects Atlassian Bambo...
Critical SQL Injection Vulnerability in PgJDBC Affects Atlassian Bamboo Data Center and Server (CVE-2024-1597) Atlassian recently patched a critical vulnerability and 24 high-severity vulnerabilities,...
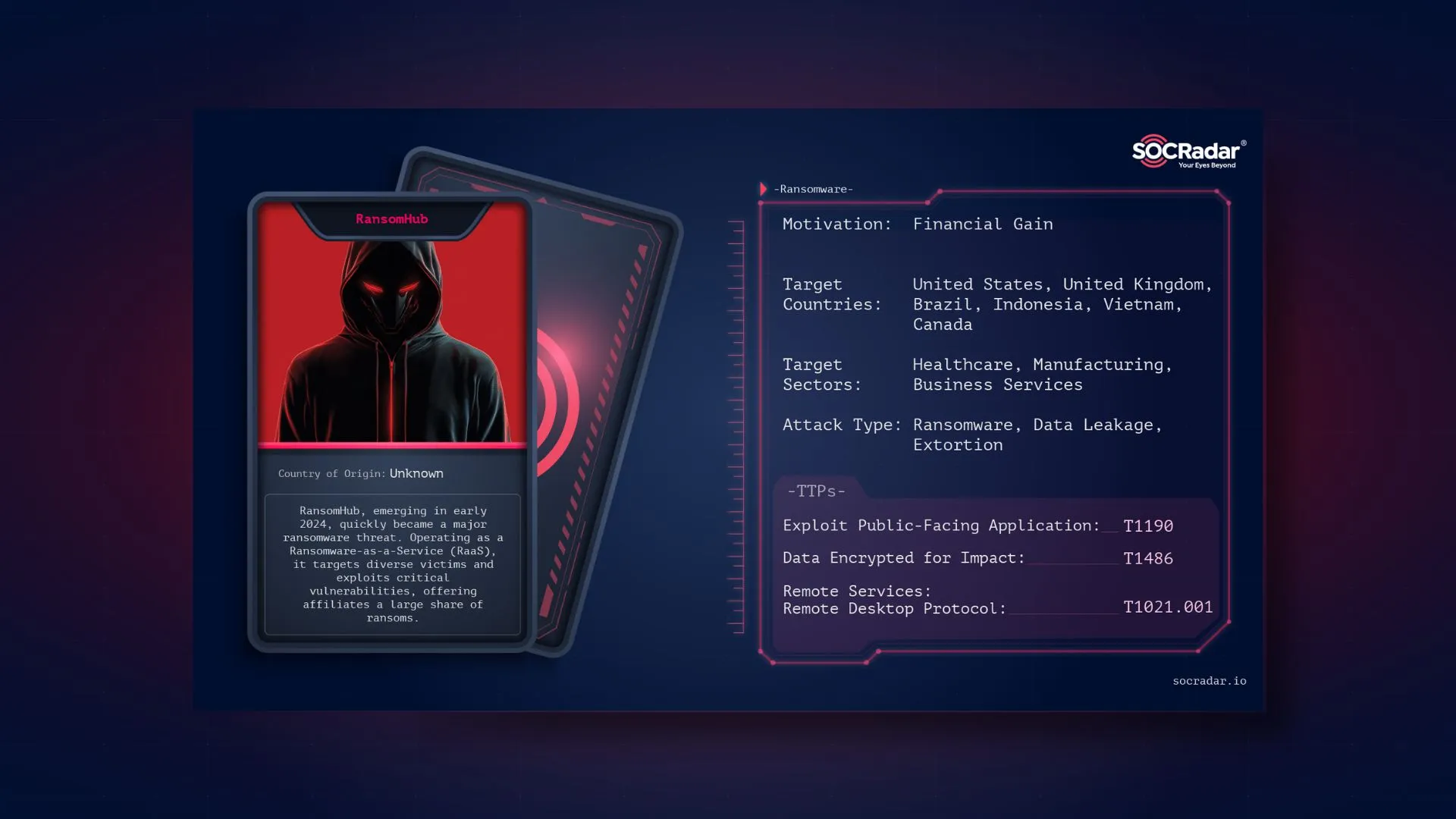
Dark Web Profile: RansomHub
Dark Web Profile: RansomHub [Update] January 22, 2025: “What Has Changed In A Year?” [Update] June 6, 2024: “RansomHub Adds ZeroLogon Vulnerability to Its Arsenal” [Update] April 8, 2024: “From ALPHV...

Cybersecurity in the Skies: SOCRadar Aviation Industry Threat Landscap...
Cybersecurity in the Skies: SOCRadar Aviation Industry Threat Landscape Report The digital age has brought many wonders, including making air travel easier and more efficient than ever before. But, ju...

Critical RCEs: Ivanti Standalone Sentry (CVE-2023-41724), Neurons for ...
Critical RCEs: Ivanti Standalone Sentry (CVE-2023-41724), Neurons for ITSM (CVE-2023-46808), Telerik Report Server (CVE-2024-1800) [Update] March 22, 2024: “CISA Warns for the Vulnerabilities in Ivant...

Executive Interview: Mr. Miroslav on Mastering the Dynamic Cybersecuri...
Executive Interview: Mr. Miroslav on Mastering the Dynamic Cybersecurity Landscape In the fast-paced and ever-evolving cybersecurity realm, staying ahead with the latest trends and technologies is cru...

Top 5 Russian-Speaking Dark Web Forums
Top 5 Russian-Speaking Dark Web Forums The dark web, a hidden corner of the internet, is a habitat for cybercrime. Among its labyrinthine networks, certain platforms stand out for their influence and ...

Dark Web Profile: ShinyHunters
Dark Web Profile: ShinyHunters Within the obscured world of the Deep/Dark Web, where cybercrime flourishes amidst databases, initial access brokers, and a plethora of illegal activities, there exists ...

Binance Stealer Logs, Exodus Botnet, Instagram 0-day Exploit, and Data...
Binance Stealer Logs, Exodus Botnet, Instagram 0-day Exploit, and Database Sales Explore the most recent dark web threats identified by SOCRadar’s Dark Web Team. From the exposure of Binance us...

Analysis of Stealer Logs within the Entertainment Industry
Analysis of Stealer Logs within the Entertainment Industry Stealer logs – databases of stolen information that vividly depict compromised security – are one of the many pieces that hold together the d...

Critical RCE Vulnerability in Fortra FileCatalyst Workflow Threatens F...
Critical RCE Vulnerability in Fortra FileCatalyst Workflow Threatens File Transfer Security (CVE-2024-25153) Fortra FileCatalyst Workflow, a trusted enterprise file transfer solution, is under severe ...

SOCRadar’s Latest Report Illuminates Cyber Threats in Switzerland's Di...
SOCRadar’s Latest Report Illuminates Cyber Threats in Switzerland’s Digital Landscape Imagine Switzerland, a place known for its stunning mountains, delicious chocolates, and top-notch watches. ...

Critical Update for Spring Framework: CVE-2024-22259 Exposes Applicati...
Critical Update for Spring Framework: CVE-2024-22259 Exposes Applications to Open Redirect, SSRF Attacks Spring Framework faces a critical security challenge with the emergence of CVE-2024-22259. This...

Major Cyber Attacks in Review: February 2024
Major Cyber Attacks in Review: February 2024 February 2024 witnessed significant cyber attacks across industries like healthcare, energy, and cryptocurrency, highlighting the persistent threats organi...
































