
Ransomware Attacks on Banking Industry
Ransomware Attacks on Banking Industry Due to the escalating illicit pursuits of cybercriminals seeking unlawful financial gains, particular sectors and specific types of cyber attacks tend to gain pr...
Critical RCE Vulnerability in ShareFile: PoC Exploit Available
Critical RCE Vulnerability in ShareFile: PoC Exploit Available [Update] August 1, 2023: Researchers from Greynoise warn of the first attempts to exploit the vulnerability in Citrix ShareFile. Added th...

Navigating the Assets Discovery Journey with SOCRadar XTI EASM
Navigating the Assets Discovery Journey with SOCRadar XTI EASM The attack surface is the sum of all potential entry points an attacker can use to gain unauthorized access to an organization’s as...

Apple Addresses Critical Zero-Day Exploit (CVE-2023-37450) with Rapid ...
Apple Addresses Critical Zero-Day Exploit (CVE-2023-37450) with Rapid Security Response Updates Apple has released Rapid Security Response (RSR) updates to tackle a zero-day vulnerability that has bee...

Newly Emerged Ransom Threats: Big Head and Rancoz
Newly Emerged Ransom Threats: Big Head and Rancoz July is the official Ransomware Awareness Month and it serves as a poignant reminder of the ever-growing danger presented by ransomware attacks. In li...

Major Cyberattacks in Review: June 2023
Major Cyberattacks in Review: June 2023 In today’s interconnected world, cybersecurity incidents, including the entrance of major cyberattacks in June 2023, have become an unfortunate reality, a...

Fortinet and Linux Kernel Exploit Shares, iCloud Checker Tool, and Cit...
Fortinet and Linux Kernel Exploit Shares, iCloud Checker Tool, and Citrix Access Sales This week, as always, we bring you these startling narratives not to alarm but to inform and prompt action. So jo...

New Critical and High-Severity Vulnerabilities Found in MOVEit Transfe...
New Critical and High-Severity Vulnerabilities Found in MOVEit Transfer In recent security disclosures, a total number of three critical and high-severity vulnerabilities have been identified in Progr...

Threads and BlueSky Could Be a New Playground for Scammers
Threads and BlueSky Could Be a New Playground for Scammers In today’s digital landscape, social media has become essential for businesses to connect with their audience and promote their brand. ...
Understanding the Type Confusion Vulnerability
Understanding the Type Confusion Vulnerability In early June 2023, a zero-day, exploited in the wild, emerged regarding Google Chrome, Microsoft Edge, and many more Chromium-based browsers, ...

Joint Advisory Warns of Truebot Malware Variants Infecting US and Cana...
Joint Advisory Warns of Truebot Malware Variants Infecting US and Canadian Networks Today, a joint Cybersecurity Advisory (CSA) was released by several organizations, including the Cybersecurity and I...
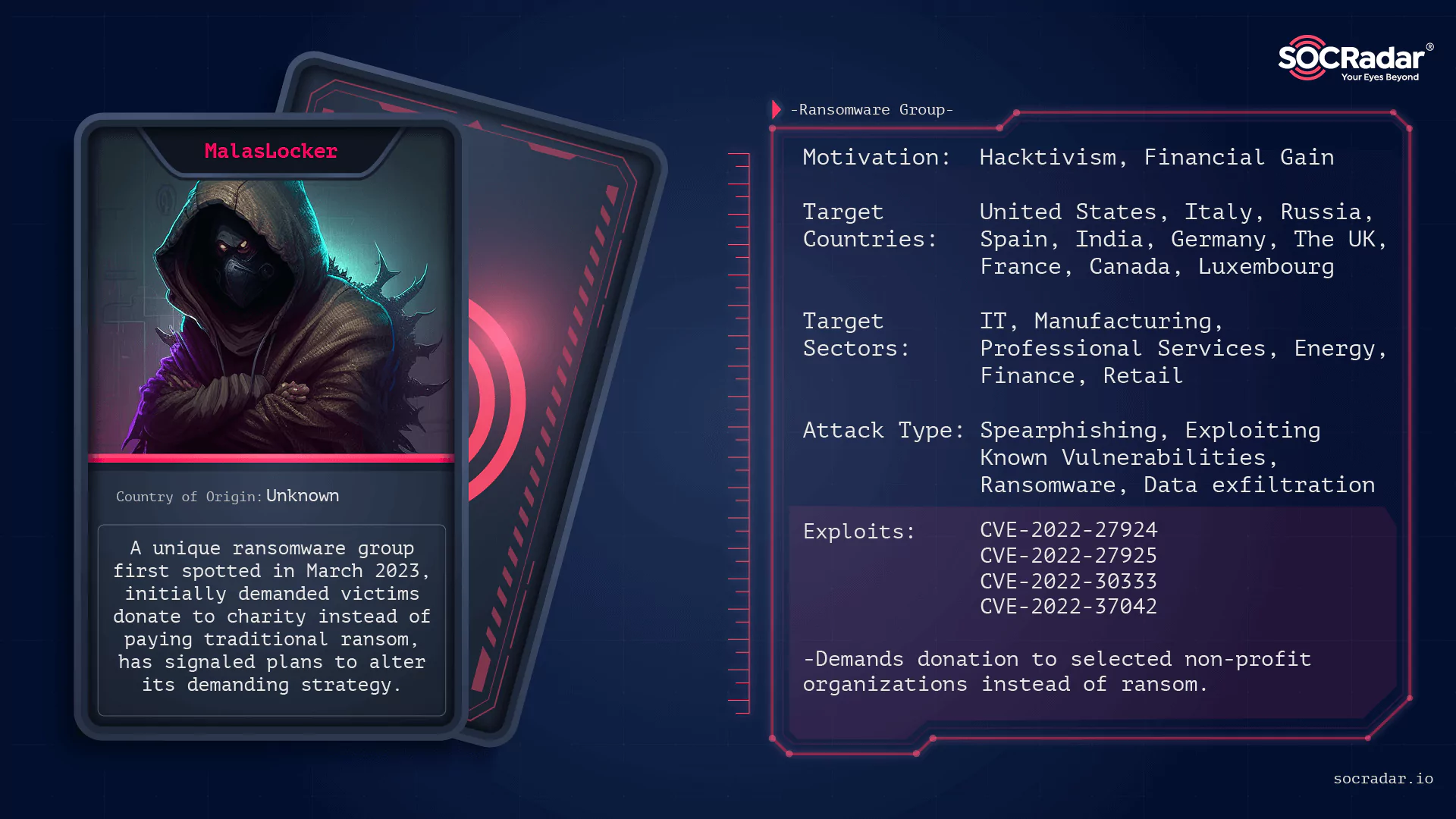
Dark Web Profile: MalasLocker Ransomware
Dark Web Profile: MalasLocker Ransomware A new player has emerged on the stage of cybercrime by announcing multiple victim announcements at the end of April. Dubbed “MalasLocker,” this ran...

Ransomware Chronicles: Unveiling the Monthly Trends in 2023
Ransomware Chronicles: Unveiling the Monthly Trends in 2023 Welcome to our “Ransomware Trends in 2023: A Live Blog of Insights and Analysis.” This live blog delves into the intricate world...

CVSS v4.0 on the Horizon
CVSS v4.0 on the Horizon [Update] November 2, 2023: See the subheading “FIRST Has Released CVSS v4.0: The Next Generation of Vulnerability Scoring” The Common Vulnerability Scoring System (CVSS) is a...

CISA's Recent Summary: Critical Vulnerabilities Impacting Apple and Ot...
CISA’s Recent Summary: Critical Vulnerabilities Impacting Apple and Other Prominent Entities CISA has recently published a Vulnerability Summary for the previous week. This summary encompasses s...

Revealing Critical SAP Vulnerabilities and Proof-of-Concept Exploit
Revealing Critical SAP Vulnerabilities and Proof-of-Concept Exploit In the world of cybersecurity, staying informed about the latest vulnerabilities is crucial for organizations, especially when it co...

US Experiences Increased DoS and DDoS Activities Across Multiple Secto...
US Experiences Increased DoS and DDoS Activities Across Multiple Sectors The United States is currently observing an upswing in targeted Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS...

Major Data Leaks on TikTok, Instagram, and Yahoo
Major Data Leaks on TikTok, Instagram, and Yahoo Welcome to this week’s dark web summary from SOCRadar. Our vigilant Dark Web Team has been working around the clock to keep you updated on the la...

APT Profile: FIN7
APT Profile: FIN7 In the world of cybercrime, a name resounds with an unsettling echo – FIN7. This notorious cyber gang has left its mark on the globe, causing digital chaos wherever they g...

The Mindset Behind Phishing Campaigns
The Mindset Behind Phishing Campaigns Phishing attacks are cybercrimes that target individuals, businesses, and organizations. These attacks use deception and manipulation techniques to trick victims ...



































